CompTIA Linux+ v1.0
Question 1
A Linux administrator has configured a Linux system to be used as a router. The administrator confirms that two network adapters are properly installed and functioning correctly. In addition, the output of the iptables ג€"L command appears to contain a complete firewall configuration.
Which of the following commands does the administrator need to issue for the router to be fully functional?
- A. echo ג€1ג€ > /proc/sys/net/ipv4/ip_forward
- B. echo ג€0ג€ > /proc/sys/net/ipv4/tcp_abort_on_overflow
- C. echo ג€0ג€ > /proc/sys/net/ipv4/max_connections
- D. echo ג€1ג€ > /proc/sys/net/ipv4/ip_default_ttl
Answer : A
Question 2
A systems administration team has decided to treat their systems as immutable instances. They keep the desired state of each of their systems in version control and apply automation whenever they provision a new instance. If there is an issue with one of their servers, instead of troubleshooting the issue, they terminate the instance and rebuild it using automation.
Which of the following is this an example of?
- A. Inventory
- B. Orchestration
- C. Infrastructure as code
- D. Agentless deployment
Answer : C
Question 3
A systems administrator wants to deploy several applications to the same server quickly. Each application should be abstracted from the host with its own dependencies and libraries and utilize a minimal footprint.
Which of the following would be BEST in this scenario?
- A. Virtual machines
- B. Type 2 hypervisor
- C. Chroot jails
- D. Containers
Answer : D
Question 4
An operator finds a user is having issues with opening certain files.
Which of the following commands would allow the security administrator to list and check the SELinux context?
- A. ls ג€"D
- B. ls ג€"a
- C. ls ג€"Z
- D. ls -l
Answer : C
Reference:
https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/6/html/security-enhanced_linux/sect-security-enhanced_linux- working_with_selinux-selinux_contexts_labeling_files
Question 5
A new corporate policy states that Bluetooth should be disabled on all company laptops. Which of the following commands would disable the use of Bluetooth?
- A. echo ג€blacklist bluetoothג€ > /etc/modprobe.d/blacklist-bluetooth
- B. echo ג€kill bluetoothג€ > /etc/modprobe.d/kill-bluetooth
- C. echo ג€modprobe bluetoothג€ > /etc/modprobe.d/modporbe-bluetooth
- D. echo ג€rmmod bluetoothג€ > /etc/modprobe.d/rmmod-bluetooth
Answer : C
Question 6
A junior Linux administrator is installing a new application with CPU architecture requirements that have the following specifications:
✑ x64 bit
✑ 3.0GHz speed
✑ Minimum quad core
The administrator wants to leverage existing equipment but is unsure whether the requirements of these systems are adequate. The administrator issues the following command cat /proc/cpuinfo. The output of the command is as follows:
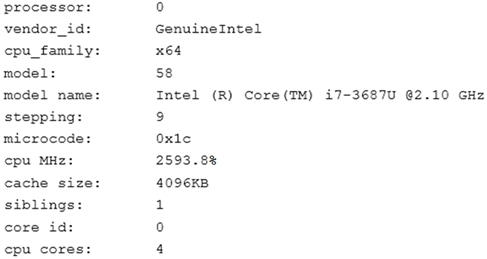
Which of the following is the recommended course of action the administrator should take based on this output?
- A. Install the application, as the system meets the application requirements
- B. Procure new equipment that matches the recommended specifications
- C. Recompile the Linux kernel to support the installation.
- D. Reconfigure lib modules to support the new application.
Answer : A
Question 7
A Linux systems administrator wants the ability to access systems remotely over SSH using RSA authentication. To which of the following files should the RSA token be added to allow this access?
- A. authorized_keys
- B. ~/.ssh/ssh_config
- C. id_rsa.pub
- D. known_hosts
Answer : C
Reference:
https://www.digitalocean.com/community/tutorials/how-to-configure-ssh-key-based-authentication-on-a-linux-server
Question 8
A Linux server needs to be accessed, but the root password is not available.
Which of the following would BEST allow an administrator to regain access and set a new known password at the same time?
- A. Boot into single-user mode and reset the password via the passwd command.
- B. Boot into single-user mode and reset the password by editing the /etc/passwd file.
- C. Boot into single-user mode and reset the password by editing the /etc/shadow file.
- D. Boot into single-user mode and reset the password via the chage command.
Answer : A
Reference:
https://phoenixnap.com/kb/how-to-change-root-password-linux
Question 9
A Linux administrator wants to fetch a Git repository from a remote Git server.
Which of the following is the BEST command to perform this task?
- A. git checkout
- B. git clone
- C. git merge
- D. git config
Answer : B
Reference:
https://git-scm.com/book/en/v2/Git-Basics-Working-with-Remotes
Question 10
An administrator needs to create a shared directory in which all users are able to read, write, and execute its content but none of the regular users are able to delete any content.
Which of the following permissions should be applied to this shared directory?
- A. rwxrwxrwt
- B. rwxrwxrws
- C. rwxrwxrwx
- D. rwxrwxrw*
Answer : A
Question 11
A systems administrator has finished building a new feature for the monitoring software in a separate Git branch.
Which of the following is the BEST method for adding the new feature to the softwareג€™s master branch?
- A. Merge the changes from the feature branch to the master branch.
- B. Save the changes to the master branch automatically with each Git commit.
- C. Clone the feature branch into the master branch.
- D. Pull the changes from the feature branch into the master branch.
Answer : A
Reference:
https://git-scm.com/book/en/v2/Git-Branching-Basic-Branching-and-Merging
Question 12
Which of the following will provide a list of all flash, external, internal, and SSD drives?
- A. lspci
- B. lsmod
- C. lsblk
- D. lsusb
Answer : C
Reference:
https://www.linux.com/learn/intro-to-linux/2017/3/how-format-storage-devices-linux
Question 13
Which of the following configuration management tools is considered agentless?
- A. Puppet
- B. Salt
- C. Ansible
- D. Chef
Answer : C
Reference:
https://www.intigua.com/blog/puppet-vs.-chef-vs.-ansible-vs.-saltstack
Question 14
An administrator reviews the following configuration file provided by a DevOps engineer:
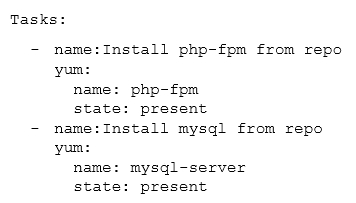
Which of the following would the application parsing this file MOST likely have to support?
- A. YAML
- B. AJAX
- C. JSON
- D. SOAP
Answer : A
Question 15
Which of the following is a difference between YAML and JSON?
- A. Users can comment in YAML but not in JSON
- B. JSON only uses curly brackets, while YAML only uses square brackets
- C. JSON is used in web development, while YAML is used solely in back-end systems.
- D. YAML has been deprecated for JSON.
Answer : A
Reference:
https://www.json2yaml.com/yaml-vs-json