VMware Certified Associate– Network Virtualization v6.0
Question 1
Which NSX service or feature provides optimized management of virtual machine broadcast (ARP) traffic?
- A. NSX Controller
- B. NSX Manager
- C. Edge Services Gateway
- D. VTEP
Answer : A
Question 2
Which Virtual Machine cannot be protected by the Distributed Firewall?
- A. A Virtual Machine connected to a vDS Portgroup running on an ESXi 5.1 host.
- B. A Virtual Machine connected to a vSS Portgroup running on an ESXi 5.5 host.
- C. A Virtual Machine connected to a vDS Portgroup running on an ESXi 5.5 host.
- D. A Virtual Machine connected to a logical switch running on an ESXi 5.1 host.
Answer : D
Question 3
-- Exhibit
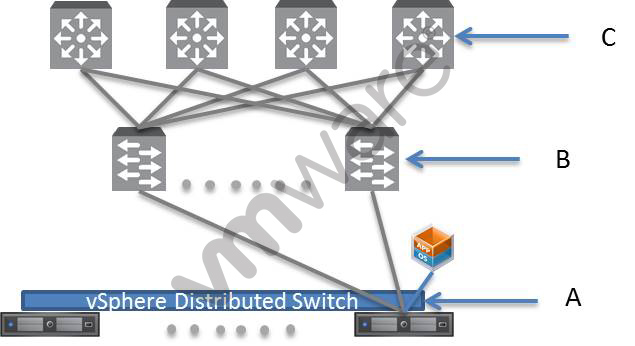
-- Exhibit --
You are designing a network for NSX and your customer has stated that virtual machine tra ffic needs to span the virtual and physical space.
Based on the diagram, where should this requirement be configured?
- A. Location A
- B. Location B
- C. Location C
- D. Locations B and C
Answer : B
Question 4
Where is the layer 2 bridge instance deployed when configuring a bridge connection between a logical switch and a VLAN?
- A. On the ESXi host running the logical router
- B. On the ESXi host running the logical switch
- C. On both ESXi hosts that make up the layer 2 bridge
- D. On each virtual machine that will utilize the layer 2 bridge
Answer : A
Question 5
A NSX administrator attempts to create a Logical Switch, but assigns it a name of an existing Logical Switch. What will be the result?
- A. The Logical Switch is created with the name assigned by the NSX Administrator.
- B. NSX Manager will append a two digit number to the Logical Switch name, starting with 01.
- C. The Logical Switch can't be attached to a Redistributed Router until it's name is changed.
- D. An error message is displayeD. Unable to allocate an available resource.
Answer : A
Question 6
What are two advantages for using NSX for vSphere's Logical Switching? (Choose two.)
- A. Expands the number of available VLANs.
- B. Allows for Layer 2 switching over Layer 3 infrastructure.
- C. Distributes Layer 3 data across multiple hypervisors.
- D. Provides for 10,000 logical segments.
Answer : BD
Question 7
Which two IPv6 connections are supported by the NSX Edge Load Balancer in Transparent mode? (Choose two.)
- A. IPv4 to IPv6
- B. IPv6 to IPv6
- C. IPv6 to IPv4
- D. IPv4 to IPv4
Answer : A,D
Question 8
Which action is not an option for adding Virtual Machines to a Security Group?
- A. Adding Virtual Machines to a Security Group and nesting it within another Security Group.
- B. Defining Dynamic Membership in the Security Group.
- C. Adding Virtual Machines to a Security Policy and associating it with a Security Group.
- D. Selecting objects to include within a Security Group.
Answer : C
Question 9
Which two statements are true regarding Layer 2 VPNs? (Choose two.)
- A. Layer 2 VPNs are used to securely extend Ethernet segments over an untrusted medium.
- B. The NSX Edge Service Gateway can form a Layer 2 VPN with a standards-compliant physical appliance.
- C. The Distributed Router can form a Layer 2 VPN to another Distributed Router or NSX Edge Service Gateway.
- D. Layer 2 VPNs require the two VPN endpoints be in the same Layer 2 segment.
Answer : AB
Question 10
Which two are pieces of information required to perform an NSX backup? (Choose two.)
- A. Transfer protocol
- B. Default Port
- C. Number of backups retained
- D. Filename prefix
Answer : A,D
Question 11
A vSphere administrator deployed an NSX Edge Load Balancer in HA mode. What happens in the event the Load Balancer has a failure?
- A. The secondary NSX Edge Load Balancer assumes the role of primary. Existing Flows will need to have their connections reestablished.
- B. HA will start the NSX Edge Load Balancer on another ESXi host in the cluster. All existing flows will need to have their connections reestablished.
- C. HA will start the NSX Edge Load Balancer on another ESXi host in the cluster. The NSX Controller caches existing flows and hands them to the Load Balancer when it is back up.
- D. The secondary NSX Edge Load Balancer assumes the role of primary. The NSX Controller caches existing flows and hands them to the Load Balancer when it is back up.
Answer : A
Question 12
Which two are valid types of authentication for an OSPF area? (Choose two.)
- A. Password authentication
- B. MD5 authentication
- C. SHA1 authentication
- D. LDAP authentication
Answer : AB
Question 13
Which option is VMware's best practice for the deployment of NSX Manager and NSX
Controller components?
- A. Deploy the NSX Manager and NSX Controller components to a management cluster.
- B. Deploy the NSX Manager component to a management cluster and the NSX Controller components to a resource cluster.
- C. Deploy the NSX Controller components to a management cluster and the NSX Manager component to a resource cluster.
- D. Deploy the NSX Manager and NSX Controller components to a resource cluster.
Answer : A
Question 14
Which statement is correct when upgrading vShield Data Security to NSX Data Security?
- A. NSX Data Security does not support a direct upgrade.
- B. NSX Controller must be deployed before the upgrade.
- C. The vCloud Network and Security Virtual Wires must have been upgraded.
- D. vCould Network and Security must be at least version 5.1 before starting the upgrade.
Answer : A
Question 15
-- Exhibit
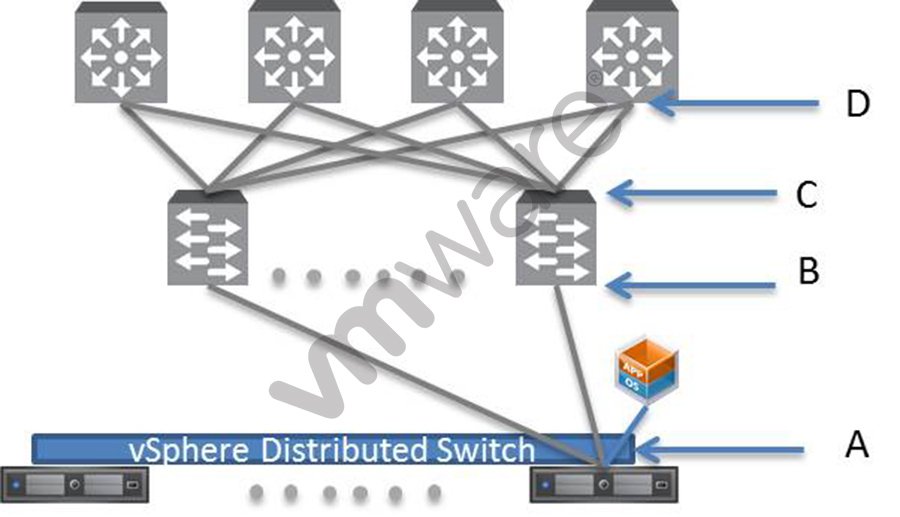
-- Exhibit --
This diagram details the network connectivity from an NSX network and the supporting phy sical network. Locations C and D may be required to process packets with QoS tags.
Based on the diagram, which statement details proper processing of packets if they are
QoS tagged?
- A. Locations C and D will trust the QoS tags of the encapsulated frame when passing packets.
- B. Location B should trust the QoS tags of the encapsulated frames that are switched.
- C. Location A will mark the inner header of the encapsulated frame.
- D. Location B should trust the QoS tags of the external header.
Answer : D