CompTIA Security+ Certification v36.0
Question 1
It is MOST important to make sure that the firewall is configured to do which of the following?
- A. Alert management of a possible intrusion.
- B. Deny all traffic and only permit by exception.
- C. Deny all traffic based on known signatures.
- D. Alert the administrator of a possible intrusion.
Answer : B
Explanation:
Firewalls manage traffic using filters, which is just a rule or set of rules. A recommended guideline for firewall rules is, deny by default; allow by exception.
Question 2
Sara, the security administrator, must configure the corporate firewall to allow all public IP addresses on the internal interface of the firewall to be translated to one public IP address on the external interface of the same firewall. Which of the following should Sara configure?
- A. PAT
- B. NAP
- C. DNAT
- D. NAC
Answer : A
Explanation:
Port Address Translation (PAT), is an extension to network address translation (NAT) that permits multiple devices on a local area network (LAN) to be mapped to a single public IP address. The goal of PAT is to conserve IP addresses.
Most home networks use PAT. In such a scenario, the Internet Service Provider (ISP) assigns a single IP address to the home network's router. When Computer X logs on the
Internet, the router assigns the client a port number, which is appended to the internal IP address. This, in effect, gives Computer X a unique address. If Computer Z logs on the
Internet at the same time, the router assigns it the same local IP address with a different port number. Although both computers are sharing the same public IP address and accessing the Internet at the same time, the router knows exactly which computer to send specific packets to because each computer has a unique internal address.
Question 3
Which of the following IP addresses would be hosts on the same subnet given the subnet mask 255.255.255.224? (Select TWO).
- A. 10.4.4.125
- B. 10.4.4.158
- C. 10.4.4.165
- D. 10.4.4.189
- E. 10.4.4.199
Answer : CD
Explanation:
With the given subnet mask, a maximum number of 30 hosts between IP addresses
10.4.4.161 and 10.4.4.190 are allowed. Therefore, option C and D would be hosts on the same subnet, and the other options would not.
References:
http://www.subnetonline.com/pages/subnet-calculators/ip-subnet-calculator.php
Question 4
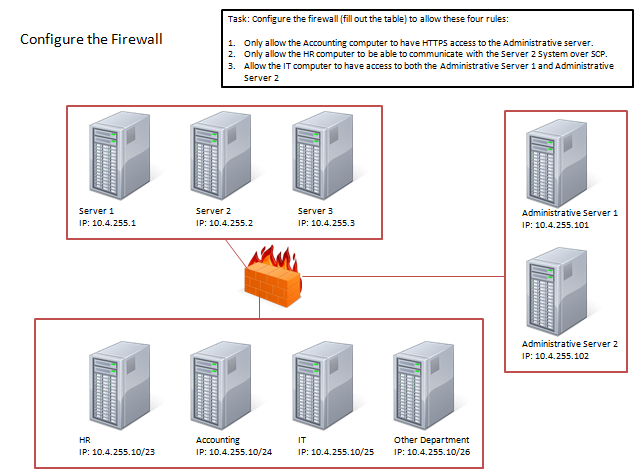
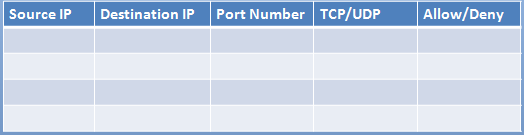
Answer : Use the following answer for this simulation task. Source IP Destination IP Port number TCP/UDP Allow/Deny 10.4.255.10/24 10.4.255.101 TCP Allow 10.4.255.10/23 10.4.255.2 TCP Allow 10.4.255.10/25 10.4.255.101 Any Any Allow 10.4.255.10/25 10.4.255.102 Any Any Allow
Explanation:
Firewall rules act like ACLs, and they are used to dictate what traffic can pass between the firewall and the internal network. Three possible actions can be taken based on the rules criteria:
Block the connection -
Allow the connection -
Allow the connection only if it is secured
TCP is responsible for providing a reliable, one-to-one, connection-oriented session. TCP establishes a connection and ensures that the other end receives any packets sent. Two hosts communicate packet results with each other. TCP also ensures that packets are decoded and sequenced properly. This connection is persistent during the session. When the session ends, the connection is torn down.
UDP provides an unreliable connectionless communication method between hosts. UDP is considered a best-effort protocol, but its considerably faster than TCP. The sessions dont establish a synchronized session like the kind used in TCP, and UDP doesnt guarantee error-free communications. The primary purpose of UDP is to send small packets of information. The application is responsible for acknowledging the correct reception of the data.
Port 22 is used by both SSH and SCP with UDP.
Port 443 is used for secure web connections HTTPS and is a TCP port.
Thus to make sure only the Accounting computer has HTTPS access to the Administrative server you should use TCP port 443 and set the rule to allow communication between
10.4.255.10/24 (Accounting) and 10.4.255.101 (Administrative server1)
Thus to make sure that only the HR computer has access to Server2 over SCP you need use of TCP port 22 and set the rule to allow communication between 10.4.255.10/23 (HR) and 10.4.255.2 (server2)
Thus to make sure that the IT computer can access both the Administrative servers you need to use a port and accompanying port number and set the rule to allow communication between:
10.4.255.10.25 (IT computer) and 10.4.255.101 (Administrative server1)
10.4.255.10.25 (IT computer) and 10.4.255.102 (Administrative server2)
References:
Dulaney, Emmett and Chuck Eastton, CompTIA Security+ Study Guide, 6th Edition, Sybex,
Indianapolis, 2014, pp. 77, 83, 96, 157
Question 5
The Human Resources department has a parent shared folder setup on the server. There are two groups that have access, one called managers and one called staff. There are many sub folders under the parent shared folder, one is called payroll. The parent folder access control list propagates all subfolders and all subfolders inherit the parent permission. Which of the following is the quickest way to prevent the staff group from gaining access to the payroll folder?
- A. Remove the staff group from the payroll folder
- B. Implicit deny on the payroll folder for the staff group
- C. Implicit deny on the payroll folder for the managers group
- D. Remove inheritance from the payroll folder
Answer : B
Explanation: Implicit deny is the default security stance that says if you aren’t specifically granted access or privileges for a resource, you’re denied access by default.
Question 6
Drag and drop the correct protocol to its default port.
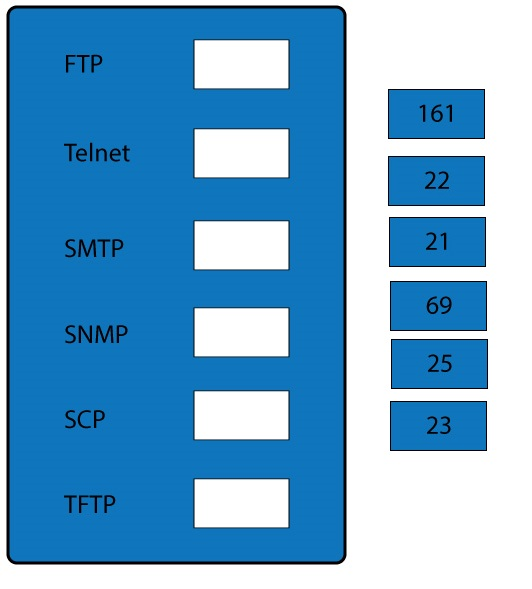
Answer : 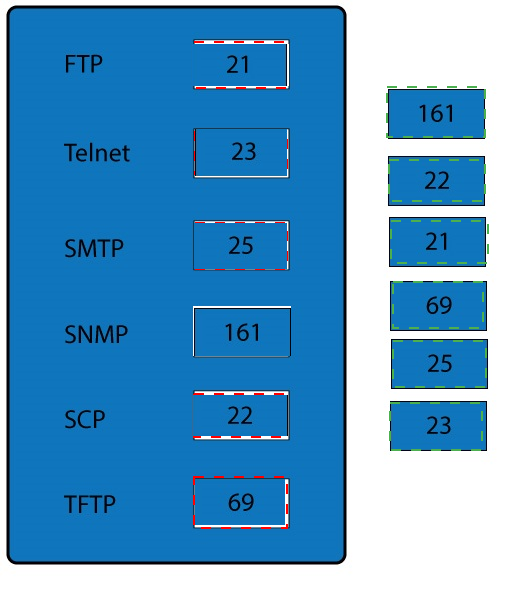
Explanation:
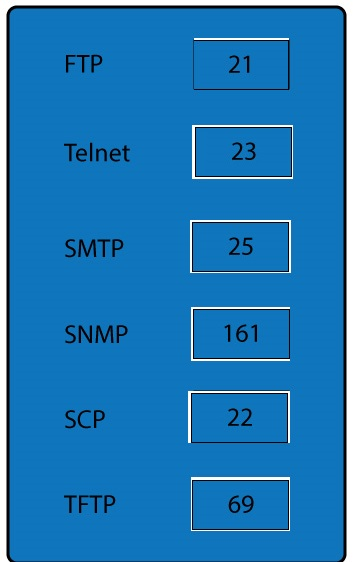
FTP uses TCP port 21.
Telnet uses port 23.
SSH uses TCP port 22. All protocols encrypted by SSH, including SFTP, SHTTP, SCP,
SExec, and slogin, also use TCP port 22. Secure Copy Protocol (SCP) is a secure file- transfer facility based on SSH and Remote Copy Protocol (RCP). Secure FTP (SFTP) is a secured alternative to standard File Transfer Protocol (FTP).
SMTP uses TCP port 25.
Port 69 is used by TFTP.
SNMP makes use of UDP ports 161 and 162.
References:
Stewart, James Michael, CompTIA Security+ Review Guide, Sybex, Indianapolis, 2014, pp.
42, 45, 51
http://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
Question 7
When designing a new network infrastructure, a security administrator requests that the intranet web server be placed in an isolated area of the network for security purposes.
Which of the following design elements would be implemented to comply with the security administrators request?
- A. DMZ
- B. Cloud services
- C. Virtualization
- D. Sandboxing
Answer : A
Explanation:
A demilitarized zone (DMZ) is an area of a network that is designed specifically for public users to access. The DMZ is a buffer network between the public untrusted Internet and the private trusted LAN. Often a DMZ is deployed through the use of a multihomed firewall.
Question 8
A security administrator must implement a firewall rule to allow remote employees to VPN onto the company network. The VPN concentrator implements SSL VPN over the standard
HTTPS port. Which of the following is the MOST secure ACL to implement at the company's gateway firewall?
- A. PERMIT TCP FROM ANY 443 TO 199.70.5.25 443
- B. PERMIT TCP FROM ANY ANY TO 199.70.5.23 ANY
- C. PERMIT TCP FROM 199.70.5.23 ANY TO ANY ANY
- D. PERMIT TCP FROM ANY 1024-65535 TO 199.70.5.23 443
Answer : D
Explanation:
The default HTTPS port is port 443. When configuring SSL VPN you can change the default port for HTTPS to a port within the 1024-65535 range. This ACL will allow traffic from VPNs using the 1024-65535 port range to access the company network via company's gateway firewall on port 443.
Question 9
A security analyst needs to ensure all external traffic is able to access the companys front- end servers but protect all access to internal resources. Which of the following network design elements would MOST likely be recommended?
- A. DMZ
- B. Cloud computing
- C. VLAN
- D. Virtualization
Answer : A
Explanation:
A demilitarized zone (DMZ) is an area of a network that is designed specifically for public users to access. The DMZ is a buffer network between the public untrusted Internet and the private trusted LAN. Often a DMZ is deployed through the use of a multihomed firewall.
Question 10
Which of the following would satisfy wireless network implementation requirements to use mutual authentication and usernames and passwords?
- A. EAP-MD5
- B. WEP
- C. PEAP-MSCHAPv2
- D. EAP-TLS
Answer : C
Explanation:
PEAP-MS-CHAP v2 is easier to deploy than EAP-TLS or PEAP-TLS because user authentication is accomplished via password-base credentials (user name and password) rather than digital certificates or smart cards.
Question 11
A review of the companys network traffic shows that most of the malware infections are caused by users visiting gambling and gaming websites. The security manager wants to implement a solution that will block these websites, scan all web traffic for signs of malware, and block the malware before it enters the company network. Which of the following is suited for this purpose?
- A. ACL
- B. IDS
- C. UTM
- D. Firewall
Answer : C
Explanation:
An all-in-one appliance, also known as Unified Threat Management (UTM) and Next
Generation Firewall (NGFW), is one that provides a good foundation for security. A variety is available; those that you should be familiar with for the exam fall under the categories of providing URL filtering, content inspection, or malware inspection.
Malware inspection is the use of a malware scanner to detect unwanted software content in network traffic. If malware is detected, it can be blocked or logged and/or trigger an alert.
Question 12
Which of the following is a difference between TFTP and FTP?
- A. TFTP is slower than FTP.
- B. TFTP is more secure than FTP.
- C. TFTP utilizes TCP and FTP uses UDP.
- D. TFTP utilizes UDP and FTP uses TCP.
Answer : D
Explanation:
FTP employs TCP ports 20 and 21 to establish and maintain client-to-server communications, whereas TFTP makes use of UDP port 69.
Question 13
A company has proprietary mission critical devices connected to their network which are configured remotely by both employees and approved customers. The administrator wants to monitor device security without changing their baseline configuration. Which of the following should be implemented to secure the devices without risking availability?
- A. Host-based firewall
- B. IDS
- C. IPS
- D. Honeypot
Answer : B
Explanation:
An intrusion detection system (IDS) is a device or software application that monitors network or system activities for malicious activities or policy violations and produces reports to a management station. IDS come in a variety of flavors and approach the goal of detecting suspicious traffic in different ways. There are network based (NIDS) and host based (HIDS) intrusion detection systems. Some systems may attempt to stop an intrusion attempt but this is neither required nor expected of a monitoring system. Intrusion detection and prevention systems (IDPS) are primarily focused on identifying possible incidents, logging information about them, and reporting attempts. In addition, organizations use
IDPSes for other purposes, such as identifying problems with security policies, documenting existing threats and deterring individuals from violating security policies.
IDPSes have become a necessary addition to the security infrastructure of nearly every organization.
IDPSes typically record information related to observed events, notify security administrators of important observed events and produce reports. Many IDPSes can also respond to a detected threat by attempting to prevent it from succeeding. They use several response techniques, which involve the IDPS stopping the attack itself, changing the security environment (e.g. reconfiguring a firewall) or changing the attack's content.
Question 14
An administrator wants to establish a WiFi network using a high gain directional antenna with a narrow radiation pattern to connect two buildings separated by a very long distance.
Which of the following antennas would be BEST for this situation?
- A. Dipole
- B. Yagi
- C. Sector
- D. Omni
Answer : B
Explanation:
A Yagi-Uda antenna, commonly known simply as a Yagi antenna, is a directional antenna consisting of multiple parallel dipole elements in a line, usually made of metal rods. It consists of a single driven element connected to the transmitter or receiver with a transmission line, and additional parasitic elements: a so-called reflector and one or more directors. The reflector element is slightly longer than the driven dipole, whereas the directors are a little shorter. This design achieves a very substantial increase in the antenna's directionality and gain compared to a simple dipole.
Question 15
An administrator is looking to implement a security device which will be able to not only detect network intrusions at the organization level, but help defend against them as well.
Which of the following is being described here?
- A. NIDS
- B. NIPS
- C. HIPS
- D. HIDS
Answer : B
Explanation:
Network-based intrusion prevention system (NIPS) monitors the entire network for suspicious traffic by analyzing protocol activity. The main functions of intrusion prevention systems are to identify malicious activity, log information about this activity, attempt to block/stop it, and report it