SCNP Strategic Infrastructure Security v6.0
Question 1
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
- A. Nmap Scan
- B. Port Scan
- C. Trojan Scan
- D. Ping Request
- E. Ping Sweep
Answer : E
Question 2
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
- A. NetBus Scan
- B. Trojan Scan
- C. Ping Sweep
- D. Port Scan
- E. Ping Sweep
Answer : D
Question 3
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
- A. Port Scan
- B. Trojan Scan
- C. Back Orifice Scan
- D. NetBus Scan
- E. Ping Sweep
Answer : B
Question 4
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
- A. Linux Ping Reply
- B. Windows 2000 Ping Reply
- C. Windows NT 4.0 Ping Request
- D. Linux Ping Request
- E. Windows 2000 Ping Request
Answer : E
Question 5
It has come to your attention that some machine has tried to send a packet to your DNS server containing both a DNS query and an answer that is false. What type of attack was used against your network?
- A. DNS overflow
- B. DNS poisoning through sequence prediction
- C. Statd overflow
- D. DNS cache poisoning
- E. DNS parse corruption
Answer : D
Question 6
What type of an attack would someone be using if they sent a packet to their target with identical source and destination IP address and port (which is the address of the target machine) which can cause a system to go into an infinite loop trying to complete a connection?
- A. SYN loop
- B. WinNuke
- C. SYN flood
- D. Ping of death
- E. Land attack
Answer : E
Question 7
You are examining a packet from an unknown host that was trying to ping one of your protected servers and notice that the packets it sent had an IPLen of 20 byes and DgmLen set to 60 bytes. What type of operating system should you believe this packet came from?
- A. Linux
- B. SCO
- C. Windows
- D. Mac OSX
- E. Netware
Answer : C
Question 8
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
- A. Trojan Horse Scan
- B. Back Orifice Scan
- C. NetBus Scan
- D. Port Scan
- E. Ping Sweep
Answer : B
Question 9
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
- A. Linux Ping Response
- B. Linux Ping Request
- C. Windows 2000 Ping Request
- D. Windows 2000 Ping Response
- E. Windows NT 4.0 Ping Request
Answer : B
Question 10
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
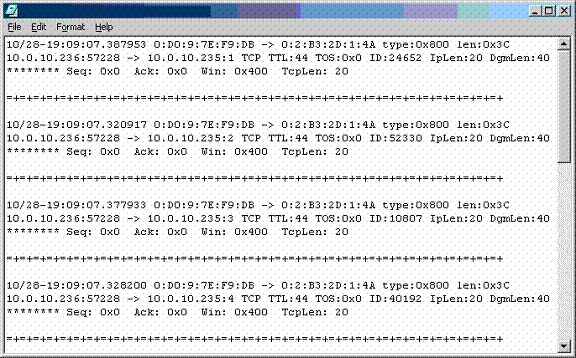
- A. Nmap SYN/FIN Scan
- B. Nmap ACK Scan
- C. Nmap NULL Scan
- D. Nmap XMAS Scan
- E. Nmap SYN Scan
Answer : C
Question 11
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
- A. Nmap SYN/FIN Scan
- B. Nmap NULL Scan
- C. Nmap ACK Scan
- D. Nmap SYN Scan
- E. Nmap XMAS Scan
Answer : D
Question 12
Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
- A. Nmap XMAS Scan
- B. Nmap NULL Scan
- C. Nmap SYN Scan
- D. Nmap ACK Scan
- E. Nmap SYN/FIN Scan
Answer : A
Question 13
Recently you have had meetings with an organization to design their security policy. There has been some resistance on their board concerning the need for a security policy. To help remove the resistance, you describe the many benefits to having a security policy. Which of the following are the benefits of a security policy?
- A. Help to prevent misuse of resources
- B. Help to decrease the legal liability
- C. Help to protect proprietary information
- D. Help to lower bandwidth usage
- E. Help protect data from unauthorized access
Answer : A,B,C,E
Question 14
You are forming the security policy for your organization. You have identified those in the organization who will participate in the creation of the policy. Several of the people you have contacted wish to know what will be on the agenda during the first meeting. During the very first policy design meeting, which of the following issues will you tell those in the policy committee to discuss?
- A. Identification of the critical business resources
- B. Identification of the infrastructure architecture
- C. Determination of the type of policy to create
- D. Identification of the critical business policies
- E. Determination of the critical policies of key connected business partners
Answer : ACD
Question 15
You are creating the User Account section of your organizational security policy. From the following options, select the questions to use for the formation of this section?
- A. Are users allowed to make copies of any operating system files (including, but not limited to /etc/passwd or the SAM)?
- B. Who in the organization has the right to approve the request for new user accounts?
- C. Are users allowed to have multiple accounts on a computer?
- D. Are users allowed to share their user account with coworkers?
- E. Are users required to use password-protected screensavers?
- F. Are users allowed to modify files they do not own, but have write abilities?
Answer : B,C,D