SOA Security Lab v6.0
Question 1
Service Consumer A sends a request message with an authentication token to Service A, but before the message reaches Service A, it is intercepted by Service Agent A (1). Service
Agent A validates the security credentials and also validates whether the message is
- A. The parts of Security Policy A and Security Policy SIB that are redundant with Security Policy SIA are removed so that there is no overlap among these three security policies. A new service agent is introduced into Service Inventory A to validate compliance to the new Security Policy SIA prior to messages being validated by Service Agent A. Another new service agent is introduced into Service Inventory B to validate compliance to the new Security Policy SIA prior to messages being validated by S
- B. The parts of Security Policy A that are redundant with Security Policy SIA are removed so that there is no overlap between these two security policies. A new service agent is introduced into Service Inventory A to validate compliance to the new Security Policy SIA prior to messages being validated by Service Agent A.
- C. The parts of Security Policy A and Security Policy SIB that are redundant with Security Policy SIA are removed so that there is no overlap among these three security policies. Service Agent A is updated so that it can validate messages for compliance with both Security Policy A and Security Policy SIA. Service Agent B is updated so that it can validate messages for compliance with both Security Policy SIA and Security Policy SIB. Service Agent C remains unchanged.
- D. Due to the amount of overlap among Security Policy A, Security Policy SIA, and Security Policy SIB, the Policy Centralization pattern cannot be correctly applied without changing the message exchange requirements of the service composition.
Answer : B
Question 2
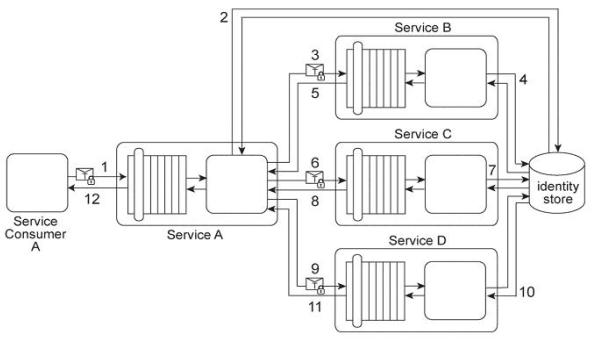
Service Consumer A sends a request message with a Username token to Service A (1).
Service B authenticates the request by verifying the security credentials from the
Username token with a shared identity store (2), To process Service Consumer A's request message. Service A must use Services B, C, and D. Each of these three services also requires the Username token (3. 6, 9) in order to authenticate Service Consumer A by using the same shared identity store (4, 7, 10). Upon each successful authentication, each of the three services (B, C, and D) issues a response message back to Service A (5, 8, 11).
Upon receiving and processing the data in all three response messages, Service A sends its own response message to Service Consumer A (12).
There are plans implement a single sign-on security mechanism in this service composition architecture. The service contracts for Services A, C, and D can be modified with minimal impact in order to provide support for the additional messaging requirements of the single sign-on mechanism. However, Service B's service contract is tightly coupled to its implementation and, as a result, this type of change to its service contract is not possible as it would require too many modifications to the underlying service implementation.
Given the fact that Service B's service contract cannot be changed to support single sign- on, how can a single sign-on mechanism still be implemented across all services?
- A. Apply the Brokered Authentication pattern so that Service A acts as an authentication broker that issues a SAML token on behalf of Service Consumer A, and forwards this token to Services C and D. Create a new utility service is positioned between Service A and Service B. This utility service perform a conversion of the SAML token to a Username token, and then forwards the Username token to Service B so that Service B can still perform authentication of incoming requests using its own security me
- B. Apply the Brokered Authentication pattern to establish Service A as an authentication broker that issues a SAML token for Service Consumer A and forwards Service Consumer A's token to other services. Apply the Trusted Subsystem pattern to create a utility service that acts as a trusted subsystem for Service B. This utility service is able to perform authentication using the SAML token from Service A and can then generate a Username token by embedding its own credentials when accessing Service B.
- C. Apply the Brokered Authentication pattern so that Service A acts as an authentication broker that issues a SAML token for Service Consumer A and forwards Service Consumer A's token to Services C and D. Create a second service contract for Service B that supports single sign-on. This way, Service B can still perform authentication of incoming requests using the old service contract while allowing for the processing of SAML tokens using the new service contract.
- D. Replace the Username tokens with X.509 digital certificates. This allows for the single sign-on mechanism to be implemented without requiring changes to any of the service contracts.
Answer : A
Question 3
Service Consumer A sends a request message with an authentication token to Service A, but before the message reaches Service A, it is intercepted by Service Agent A (1). Service
Agent A validates the security credentials and also validates whether the message is
- A. In order for Security Policy A to be centralized so that it can be shared by Service A and the new perimeter service, messages sent to the perimeter service from services in Service Inventory B will need to continue complying with Security Policy A, even if it requires that the messages contain content that does not relate to accessing the legacy system. In order to centralize Security Policy B it will need to be combined with Security Policy SIB, which means that the functionality within Servic
- B. A single centralized security policy can be created by combining Security Policy A, Security Policy B. and Security Policy SIB into a single security policy that is shared by services in both Service Inventory A and Service Inventory B. This means that the new perimeter service can share the same new security policy with Service A. This further simplifies message exchange processing because request messages sent by services in Service Inventory B to the new perimeter service need to comply to th
- C. The parts of Security Policy A that are required for access to the new perimeter service need to be removed and placed into a new security policy that is shared by Service A and the perimeter service. Messages sent by services accessing the perimeter service from Service Inventory B will need to be compliant with the new security policy. Because the perimeter service is dedicated to message exchange with services from Service Inventory B, response messages sent by the perimeter service can be de
- D. Due to the amount of overlap among Security Policy A, Security Policy B, and Security Policy SIB, the Policy Centralization pattern cannot be correctly applied to enable the described message exchange between the perimeter service in Service Inventory A and services in Service Inventory B.
Answer : C
Question 4
Service A provides a data retrieval capability that can be used by a range of service
- A. Apply the Data Origin Authentication and the Data Confidentiality patterns to ensure that request and response messages exchanged between Service A and Services B. C, and D are digitally signed and encrypted. This guarantees message integrity and confidentiality.
- B. Apply the Data Origin Authentication pattern to verily that request and response messages exchanged by Service Consumer A and Service A and exchanged by Service A and Services B, C, and D originated from the claimed sources and have not been altered prior to transmission. Also, enhance the Service A architecture so that all messages sent to its service consumers are logged.
- C. Apply the Brokered Authentication pattern to send the security credentials of Service Consumer A to Services B, C, and D. Service A can carry out the brokered authentication logic and therefore act as the intermediary security broker. Upon receiving Service Consumer A's request message, Service A can further verify the credentials against an external certificate authority, if the request is authenticated. Service A can create a signed SAML assertion containing Service Consumer A's credentials an
- D. The service contract of Service A can be extended with an ignorable WS-Policy assertion that states that all request and response messages are logged by Service A and that false complaints will be prosecuted.
Answer : B
Question 5
Service Consumer A sends a request message to Service A (1) after which Service A retrieves financial data from Database A (2). Service A then sends a request message with the retrieved data to Service B (3). Service B exchanges messages with Service C (4) and
Service D (5), which perform a series of calculations on the data and return the results to
- A. A utility service is created to encapsulate Database A and to assume responsibility for authenticating all access to the database by Service A and any other service consumers. Due to the mission critical requirements of Component B, the utility service further contains logic that strictly limits the amount of concurrent requests made to Database A from outside the organizational boundary. The Data Confidentiality and Data Origin Authentication patterns are applied to all message exchanged within
- B. Service Consumer A generates a private/public key pair and sends this public key and identity information to Service A. Service A generates its own private/public key pair and sends it back to Service Consumer A. Service Consumer A uses the public key of Service A to encrypt a randomly generated session key and then sign the encrypted session key with the private key. The encrypted, signed session key is sent to Service A. Now, this session key can be used for secure message-layer communication
- C. Services B, C, and D randomly generate Session Key K, and use this key to encrypt request and response messages with symmetric encryption. Session Key K is further encrypted itself asymmetrically. When each service acts as a service consumer by invoking another service, it decrypts the encrypted Session Key K and the invoked service uses the key to decrypt the encrypted response. Database A is replicated so that only the replicated version of the database can be accessed by Service A and other e
- D. The Direct Authentication pattern is applied so that when Service Consumer A submits security credentials, Service A will be able to evaluate the credentials in order to authenticate the request message. If the request message is permitted, Service A invokes the other services and accesses Database A. Database A is replicated so that only the replicated version of the database can be accessed by Service A and other external service consumers.
Answer : A
Question 6
Service Consumer A sends a request message to Service A (1) after which Service A retrieves financial data from Database A (2). Service A then sends a request message with the retrieved data to Service B (3). Service B exchanges messages with Service C (4) and
Service D (5), which perform a series of calculations on the data and return the results to
- A. Service Consumer A generates a pair of private/public keys (Public Key E and Private Key D) and sends the public key to Service A. Service A can use this key to send confidential messages to Service Consumer A because messages encrypted by the public key of Service Consumer A can only be decrypted by Service A The Data Origin Authentication pattern can be further applied so that Service A can authenticate Service Consumer A by verifying the digital signature on request messages. The Message Scre
- B. The Brokered Authentication pattern is applied so that each service consumer generates a pair of private/public keys and sends the public key to Service A. When any service in the external service composition (Services A, B, C, and D) sends a request message to another service, the request message is signed with the private key of the requesting service (the service acting as the service consumer). The service then authenticates the request using the already established public key of the service
- C. A utility service is established to encapsulate Database A and to carry out the authentication of all access to the database by Service A and any other service consumers. To further support this functionality within the utility service, an identity store is introduced. This identity store is also used by Service A which is upgraded with its own authentication logic to avoid access by malicious service consumers pretending to be legitimate service consumers. In order to avoid redundant authentica
- D. Implement a firewall between Service Consumer A and Service A. All access to Service A is then controlled by the firewall rules. The firewall contains embedded logic that authenticates request messages and then forwards permitted messages to Service A. Moreover, the firewall can implement the Message Screening pattern so that each incoming message is screened for malicious content. This solution minimizes the security processing performed by Service A in order to maintain the performance require
Answer : C
Question 7
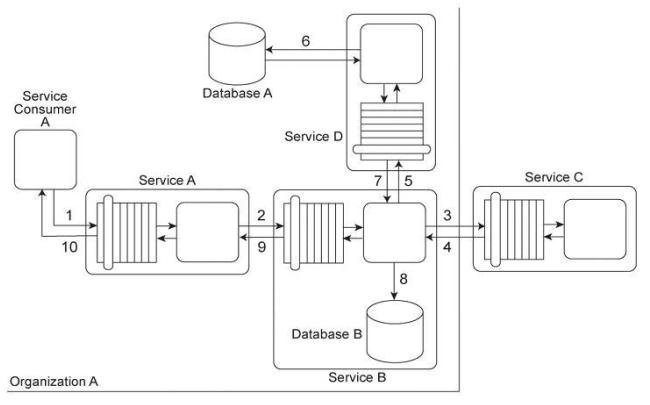
Service Consumer A sends a request message to Service A (1), after which Service A sends a request message to Service B (2). Service B forwards the message to have its contents calculated by Service C (3). After receiving the results of the calculations via a response message from Service C (4), Service B then requests additional data by sending a request message to Service D (5). Service D retrieves the necessary data from Database
A (6), formats it into an XML document, and sends the response message containing the
XML-formatted data to Service B (7). Service B appends this XML document with the calculation results received from Service C, and then records the entire contents of the
XML document into Database B (8). Finally, Service B sends a response message to
Service A (9) and Service A sends a response message to Service Consumer A (10).
Services A, B and D are agnostic services that belong to Organization A and are also being reused in other service compositions. Service C is a publicly accessible calculation service that resides outside of the organizational boundary. Database A is a shared database used by other systems within Organization A and Database B is dedicated to exclusive access by Service B.
Recently, Service D received request messages containing improperly formatted database retrieval requests. All of these request messages contained data that originated from
Service C. There is a strong suspicion that an attacker from outside of the organization has been attempting to carry out SOL injection attacks. Furthermore, it has been decided that each service that writes data to a database must keep a separate log file that records a timestamp of each database record change. Because of a data privacy disclosure requirement used by Organization A, the service contracts of these services need to indicate that this logging activity may occur.
How can the service composition architecture be improved to avoid SQL injecti
- A. Apply the Service Perimeter Guard pattern together with the Message Screening pattern in order to establish a perimeter service with message screening logic. Position the perimeter service between Service C and Service B. The message screening logic rejects or filters out potentially harmful content in messages sent from Service C, prior to being forwarded to Service B. Secondly, update the service contracts for Services B and D with an optional WS-Policy assertion that provides service consumer
- B. Apply the Data Origin Authentication pattern to authenticate data received from Service
- C. Service C digitally signs any data sent in response messages to Service B. Service B can then verify that the data has not been modified during transit and that it originated from Service C. Secondly, update the service contracts for Services B and D with an ignorable WS-Policy assertion that communicates the possibility of the logging activity. The service contracts for Services B and D are updated with an optional WS-Policy assertion that provides service consumers with the option of complying
- D. Apply the Message Screening pattern in order to establish a service agent with message screening logic. Position the service agent between Service C and Service B. The service agent's message screening logic can reject or filter out potentially harmful content in messages sent from Service C, before being processed by Service B. Secondly, update the service contracts for Services B and D with an ignorable WS-Policy assertion that communicates the possibility of the logging activity.
Answer : D
Question 8
- A. The Data Confidentiality pattern can be applied to messages exchanged by the services in Service Inventory A. The Data Origin Authentication pattern can be applied to messages exchanged by services in Service Inventory B.
- B. The Service Perimeter Guard pattern can be applied to Service Inventory A in order to establish a perimeter service responsible for validating and filtering all incoming request messages on behalf of Service C. The Data Origin Authentication pattern can be applied to messages exchanged by services in Service Inventory B. This will ensure the integrity of messages by verifying their origins to the message recipients.
- C. WS-SecureConversation can be used to secure the communication between the authentication broker and service consumers in Service Inventory A. This ensures that Services A and B will contact Service C to request a security context token that will be used to generates a session key for the encryption of the ticket submitted to Service C. The Data Origin Authentication pattern can be applied to messages exchanged by services in Service Inventory B. This will ensure the integrity of messages try ver
- D. WS-Trust can be used to establish secure communication between the authentication broker and the service consumers. After receiving the request message and the corresponding credentials from service consumers, the authentication broker can validate their identity, and if successful, a signed SAML assertion containing all authentication information will be issued. The SAML assertion will then be used to authenticate the service consumers during subsequent communications. Because the messages are
Answer : A
Question 9
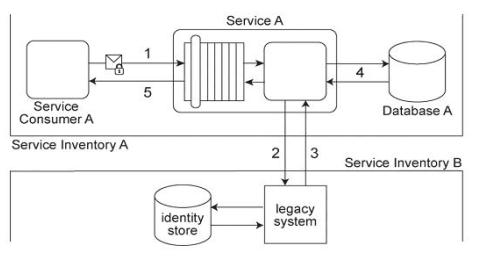
Service Consumer A submits a request message with security credentials to Service A (1).
The identity store that Service A needs to use in order to authenticate the security credentials can only be accessed via a legacy system that resides in a different service inventory. Therefore, to authenticate Service Consumer A, Service A must first forward the security credentials to the legacy system (2). The legacy system then returns the requested identity to Service A (3). Service A authenticates Service Consumer A against the identity received from the legacy system. If the authentication is successful, Service A retrieves the requested data from Database A (4), and returns the data in a response message sent back to Service Consumer A (5).
Service A belongs to Service Inventory A which further belongs to Security Domain A and the legacy system belongs to Service Inventory B which further belongs to Security Domain
B. (The legacy system is encapsulated by other services within Service Inventory B, which are not shown in the diagram.) These two security domains trust each other.
Communication between Service A and the legacy system is kept confidential using transport-layer security.
It was recently discovered that a malicious attacker, posing as Service Consumer A, has
- A.
- B. Apply the Service Perimeter Guard pattern together with the Trusted Subsystem pattern to establish a perimeter service that can perform security functions on behalf of Service A. The utility service can verify the validity of the request messages from Service Consumer A by authenticating the request message against an identity store. If the request message is authenticated, the utility service then sends it to Service A for further processing. All communications between Service A and Service Con
- C. Apply the Service Perimeter Guard pattern to establish a perimeter service that can perform security functions on behalf of Service A. Next, apply the Data Confidentiality pattern so that the security credential information provided by Service Consumer A with the request message is encrypted with the secret key shared between the perimeter service and Service Consumer A. The perimeter service evaluates the credentials and if successfully authenticated, forwards the request message to Service A.
- D. Apply the Trusted Subsystem pattern together with the Data Origin Authentication pattern in order to establish a utility service that performs the security processing on behalf of Service A. Service Consumer A must digitally sign all request messages and encrypt the credential information using the public key of the utility service. The utility service can then verify the security credentials and the digital signature to establish the validity of the request message. If the request message is pe
Answer : A
Question 10
Service A provides a data access capability that can be used by a variety of service consumers. The database records accessed by Service A are classified as either private or public. There are two types of service consumers that use Service A: Service consumers with public access permissions (allowed to access only public data records) and service consumers with private access permissions (allowed to access all data records). For performance reasons the Service A architecture uses a single database, named Database
- A. The Exception Shielding pattern is applied to replace the error description text before a response message is returned to the service consumer. Furthermore, the ID value of all database records is appended with a code indicating whether the database record is private or public
- B. The database rules are changed so that the ID value of database records no longer needs to be unique. As a further precaution, the Service A logic is changed to disallow the update of private database records by service consumers with only public access permissions.
- C. The service consumer's request message containing the ID value can be encrypted by inserting the private key of the service consumer into the data. Because all service consumers have different private keys, this approach will lead to different encrypted values, even if the plain text ID values are the same. As a result, two data items with the same encrypted unique identifier cannot exist.
- D. When Service A detects that a service consumer with public access permissions has submitted an ID value that already exists within a private database record, it stores the service consumer's ID value in a temporary database and returns a response message indicating that the update was successful. A notification message is then sent to a human database administrator who manually contacts the owner of the service consumer in order to explain that the ID value submitted cannot be accepted because i
Answer : A
Question 11
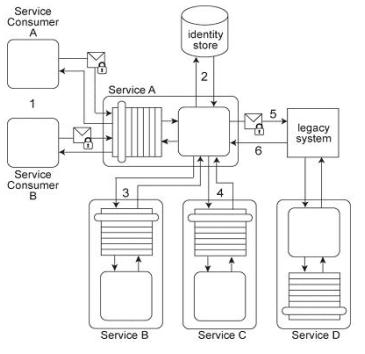
Service A has two specific service consumers, Service Consumer A and Service Consumer
B (1). Both service consumers are required to provide security credentials in order for
Service A to perform authentication using an identity store (2). If a service consumer's request message is successfully authenticated, Service A processes the request by exchanging messages with Service B (3) and then Service C (4). With each of these message exchanges, Service A collects data necessary to perform a query against historical data stored in a proprietary legacy system. Service A's request to the legacy system must be authenticated (5). The legacy system only provides access control using a single account. If the request from Service A is permitted, it will be able to access all of the data stored in the legacy system. If the request is not permitted, none of the data stored in the legacy system can be accessed. Upon successfully retrieving the requested data (6),
Service A generates a response message that is sent back to either Service Consumer A or B.
The legacy system is also used independently by Service D without requiring any authentication. Furthermore, the legacy system has no auditing feature and therefore cannot record when data access from Service A or Service D occurs. If the legacy system encounters an error when processing a request, it generates descriptive error codes.
This service composition architecture needs to be upgraded in order to fulfill the following new security requirements: 1. Service Consumers A and B have different permission levels, and therefore, response messages sent to a service consumer must only contain data for which the service consumer is authorized. 2. All data access requests made to the legacy system must be logged. 3. Services B and C must be provided with the identity of
Service A's service consumer in order to provide Service A with the requested data. 4.
Response messages generated by Service A c
- A. To correctly enforce access privileges, Services B and C must share the identity store with Service A and directly authenticate Service Consumer A or B. Furthermore, Services B and C must each maintain two policies: one for Service Consumer A and one for Service Consumer B. After receiving a request message from a Service A. Services B and C must evaluate the validity of the request by using the identity store and the appropriate policy. Service Consumers A and B are required to submit the neces
- B. Apply the Trusted Subsystem pattern by introducing a new utility service that encapsulates data access to the legacy system. After Service A authenticates a service consumer it creates a signed SAML assertion containing authentication and authorization information. The SAML assertions are used by Service A to convey the identity information of Service Consumer A or B to Services B and C. The utility service filters response messages to the service consumer based on the information in the SAML as
- C. Apply the Service Perimeter Guard pattern to provide selective access privileges to Service Consumers A and B. The resulting perimeter service shares the identity store with Service A, which it uses to authenticate each request message. If authentication is successful, the request message is forwarded to Service A. Service A then also authenticates the service consumer and retrieves the service consumer's security profile from the identity store upon successful authentication. Each service consu
- D. Apply the Trusted Subsystem pattern by introducing a new utility service that encapsulates data access to the legacy system. The utility service evaluates request messages by authenticating the service consumer against the identity store and also verifying the digital signature of each request. If the request is permitted, Service A forwards the service consumer's credentials to Services B and C, and to the legacy system. The response messages from Services B and C are returned to Service A, whi
Answer : B
Question 12
Service A provides a customized report generating capability. Due to infrastructure limitations, the number of service consumers permitted to access Service A concurrently is strictly controlled. Service A validates request messages based on the supplied credentials
(1). If the authentication of the request message is successful, Service A sends a message to Service B (2) to retrieve the required data from Database A (3). Service A stores the response from Service B (4) in memory and then issues a request message to Service C
(5). Service C retrieves a different set of data from Database A (6) and sends the result back to Service A (7). Service A consolidates the data received from Services B and C and sends the generated report in the response message to the service consumer (8).
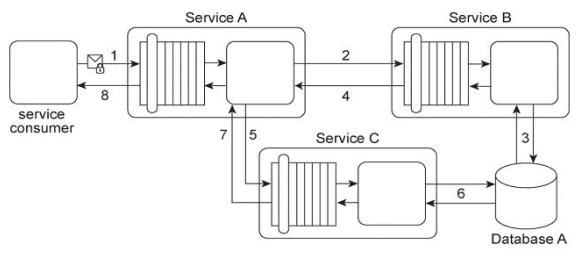
It has been discovered that attackers have been gaining access to confidential data exchanged between Service A and Service B, and between Service A and its service consumers. What changes can be made to this service composition architecture in order to counter this threat?
- A. Apply the Service Perimeter Guard pattern in order to protect message exchanges between Service A and its service consumers. Apply the Direct Authentication pattern in order to protect message exchanges between Service A and Service B.
- B. Apply the Direct Authentication pattern in order to protect message exchanges between Service A and its service consumers and between Service A and Service B. This approach will establish a password-based authentication mechanism that relies on a local identity store and will therefore prevent access by attackers.
- C. Apply the Data Origin Authentication pattern to protect the final report sent by Service A to its service consumer. Service A can generate a message digest of the final report, after which it can sign the digest with its own private key. It then can send both the final report and the signed message digest to its service consumer. This service consumer can generate its own message digest, decrypt the signed digest using the public key of Service A (which proves that Service A sent the message), a
- D. None of the above
Answer : D
Question 13
Service Consumer A sends a request message to Service A (1), after which Service A sends a request message with security credentials to Service B (2). Service B authenticates the request and, if the authentication is successful, writes data from the request message into Database B (3). Service B then sends a request message to Service
C (4), which is not required to issue a response message. Service B then sends a response message back to Service A (5). After processing Service B's response, Service A sends another request message with security credentials to Service B (6). After successfully authenticating this second request message from Service A, Service B sends a request message to Service D (7). Service D is also not required to issue a response message. Finally, Service B sends a response message to Service A (8), after which
Service A records the response message contents in Database A (9) before sending its own response message to Service Consumer A (10).
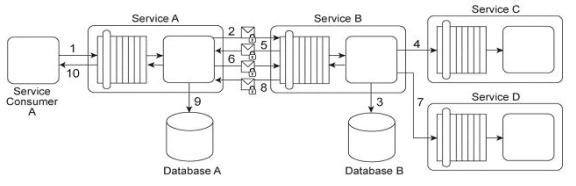
To use Service A, Service Consumer A is charged a per usage fee. The owner of Service
Consumer A has filed a complaint with the owner of Service A, stating that the bills that have been issued are for more usage of Service A than Service Consumer A actually used.
Additionally, it has been discovered that malicious intermediaries are intercepting and modifying messages being sent from Service B to Services C and D. Because Services C and D do not issue response messages, the resulting errors and problems were not reported back to Service B.
Which of the following statements describes a solution that correctly addresses these problems?
- A. The Data Confidentiality and Data Origin Authentication patterns need to be applied in order to establish message-layer confidentiality and integrity for messages sent to Services C and D. The Direct Authentication pattern can be applied to require that service consumer be authenticated in order to use Service A.
- B. Messages sent to Services C and D must be protected using transport-layer encryption in order to ensure data confidentiality. Service consumers of Service A must be authenticated using X.509 certificates because they can be reused for several request messages.
- C. Apply the Service Perimeter Guard and the Message Screening patterns together to establish a perimeter service between Service Consumer A and Service A. The perimeter service screens and authenticates incoming request messages from Service Consumer A. After successful authentication, the perimeter service generates a signed SAML assertion that is used by the subsequent services to authenticate and authorize the request message and is also carried forward as the security credential included in me
- D. Apply the Brokered Authentication to establish an authentication broker between Service Consumer A and Service A that can carry out the Kerberos authentication protocol. Before invoking Service A, Service Consumer A must request a ticket granting ticket and then it must request service granting tickets to all services in the service composition, including Services C and D. Messages sent by Service B to Services C and D must further be encrypted with the public key of Service Consumer A.
Answer : A
Question 14
Service A exchanges messages with Service B multiple times during the same runtime service activity. Communication between Services A and B has been secured using
- A. Eliminate the need to retrieve the public key from the Certificate Authority and to verify the certificate revocation information by extending the service contract of Service B to accept certificates only from pre-registered Certificate Authorities. This form of pre- registration ensures that Service B has the public key of the corresponding Certificate Authority.
- B. Add a service agent to screen messages sent from Service A to Service B. The service agent can reject any message containing malicious content so that only verified messages are passed through to Service B. Instead of using X.509 certificates, use WS- SecureConversation sessions. Service A can request a Security Context Token (SCT) from a Security Token Service and use the derived keys from the session key to secure communication with Service B. Service B retrieves the session key from the Secur
- C. Apply the Trusted Subsystem pattern by introducing a new utility service between Service A and Service B. When Service A sends request messages, the utility service verifies the provided credentials and creates a customized security profile for Service A. The security profile contains authentication and access control statements that are then inherited by all subsequent request messages issued by Service A. As a result, performance is improved because Service A does not need to resubmit any addi
- D. Apply the Trusted Subsystem pattern to by introducing a new utility service. Because Service B is required to limit the use of external resources. Service A must ensure that no other services can request processing from Service B in order to prevent malicious content from infiltrating messages. This is achieved by creating a dedicated replica of Service B to be used by the utility service only. Upon receiving the request message and the accompanying security credentials from Service A. the utili
Answer : B
Question 15
Service Consumer A sends a request message with a Username token to Service A (1).
Service B authenticates the request by verifying the security credentials from the
Username token with a shared identity store (2). To process Service Consumer A's request message, Service A must use Services B, C, and D. Each of these three services also requires the Username token (3. 6, 9) in order to authenticate Service Consumer A by using the same shared identity store (4, 7, 10). Upon each successful authentication, each of the three services (B, C, and D) issues a response message back to Service A (5, 8, 11).
Upon receiving and processing the data in all three response messages, Service A sends its own response message to Service Consumer A (12).
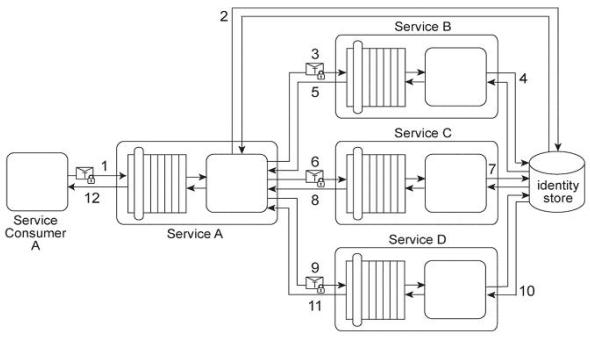
You are asked to redesign this service composition architecture so that it can still carry out the described message exchanges while requiring that Service Consumer A only be authenticated once using the identity store.
Which of the following statements describes an accurate solution?
- A. A single sign-on mechanism is implemented. The Brokered Authentication pattern is applied, resulting in Service A becoming the authentication broker. The authentication broker authenticates the security credentials received from Service Consumer A against the identity store. After successful authentication, the authentication broker issues a signed SAML token for Service Consumer A. The SAML token is subsequently provided to Services B.C. and D by Service A, on behalf of Service Consumer A.
- B. A single sign-on mechanism is implemented. The Brokered Authentication pattern is applied together with the Data Origin Authentication pattern. A separate authentication broker utility service is added in between Service Consumer A and Service A. This requires that Service A send its Username token only once to Service B. Service B then acts as a secondary authentication broker and authenticates Service Consumer A and Service A using the identity store. If the authentication is successful, Servi
- C. A single sign-on mechanism is implemented. The Brokered Authentication pattern is applied together with the Data Origin Authentication pattern. Service A is redesigned to use holder-of-key based subject confirmation SAML assertions. This way, Service A only needs to send its Username token once to Service B. Service B then acts as the authentication broker by issuing a SAML token to Service A and then further sends the SAML token to Services C and D on behalf of Service Consumer A and Service A.
- D. The Direct Authentication pattern is applied together with an authentication process that uses digital certificates and digital signatures instead of Username tokens. The digital certificate of Service Consumer A is attached to all subsequent request messages issued by Services A, B, C and D and these request messages are further signed by a private key.
Answer : A