Palo Alto Networks Certified Cybersecurity Associate v1.0
Question 1
You discover malware has corrupted the BIOS on your laptop. Which type of malware is this?
- A. bootkit
- B. exploit
- C. rootkit
- D. vulnerability
Answer : A
Question 2
Which data security compliance standard is used to protect credit cardholder data wherever it is processed, stored, or transmitted?
- A. Property Card Industry
- B. Payment Card Industry
- C. Personal Card Industry
- D. Payment Club Industry
Answer : B
Question 3
What does Palo Alto Networks Traps do first when an endpoint is asked to run an executable?
- A. send the executable to WildFire
- B. run a static analysis
- C. run a dynamic analysis
- D. check its execution policy
Answer : D
Question 4
What is the function of a hashing protocol?
- A. encrypts data with encapsulation
- B. establishes an unencrypted tunnel
- C. establishes a secure tunnel
- D. provides data integrity
Answer : D
Question 5
Which two items operate at the network layer in the OSI network model? (Choose two.)
- A. IP address
- B. router
- C. switch
- D. MAC address
Answer : AB
Question 6
In which type of cloud computing service does an organization own and control application data, but not the application?
- A. platform as a service
- B. computing as a service
- C. infrastructure as a service
- D. software as a service
Answer : D
Question 7
You discover an infected email attachment that contains software code that attacks a known vulnerability in a popular social networking application. This type of software code belongs to which type of malware category?
- A. social engineering
- B. virus
- C. pharming
- D. exploit
Answer : D
Question 8
What is an example of a distance-vector routing protocol?
- A. OSPF
- B. BGP
- C. RIP
- D. IGRP
Answer : C
Question 9
Which type of firewall monitors traffic streams from beginning to end?
- A. circuit-level gateway
- B. stateless
- C. stateful
- D. packet filter
Answer : C
Question 10
Which option lists the correct sequence of a TCP three-way handshake?
- A. SYN, ACK, SYN
- B. SYN, SYN+ACK, ACK
- C. SYN, ACK, FIN
- D. SYN, SYN+ACK, FIN
Answer : B
Question 11
Which two types of SaaS applications are allowed by an IT department? (Choose two.)
- A. tolerated
- B. certified
- C. sanctioned
- D. unsanctioned
Answer : AC
Reference:
https://www.paloaltonetworks.com/cyberpedia/saas-security
Question 12
Which network method securely connects two sites across a public network?
- A. VPN
- B. VLAN
- C. switch
- D. router
Answer : A
Question 13
Review the exhibit and identify the type of vulnerability or attack that is commonly used against this technology.

- A. phishing
- B. denial-of-service
- C. code-injection
- D. password cracking
Answer : D
Question 14
When accessing an intranet website, a certificate error is received. What can be done to move past the certificate error and ensure that the error is not received the next time the website is accessed?
- A. install the website certificate into the web browser
- B. request trusted access from the web developer
- C. enable TLS 2.0 in the advanced options of the web browser
- D. trust the web developer for the application
Answer : A
Question 15
Assume that it is your responsibility to secure the software functioning at all layers in the exhibit.
Which cloud service model type is represented?
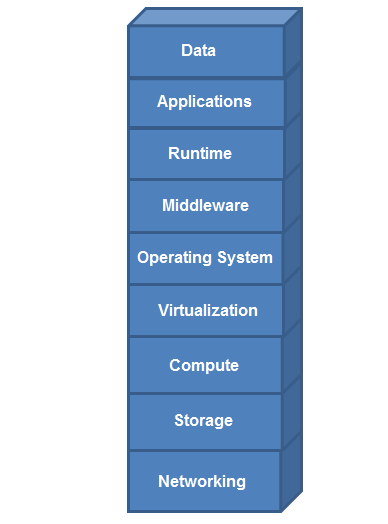
- A. software as a service
- B. platform as a service
- C. infrastructure as a service
- D. on-premises
Answer : D