Fortinet Network Security Expert 8 Written Exam (NSE8 810 - FortiOS 5.6) v1.0
Question 1
You configured an outgoing firewall policy with a Web filter profile for accessing the Internet. The access to URL https://www.it-acme.com and all Web sites belonging to the same category should be blocked. You notice that the Web server presents a certificate with CN=www.acme.com site is categorized as "Information Technology" and the www.acme.com site is categorized as "Business".
Which statement is correct in this scenario?
- A. Category "Information technology" needs to be blocked, the FortiGate is able to inspect the URL with HTTPS sessions.
- B. Category "Business" needs to be blocked, the certificate name takes precedence over the SNI.
- C. SSL inspection must be configured to deep-inspection, the category "Information Technology" needs to be blocked.
- D. Category "Information Technology" needs to be blocked, the SNI takes precedence over the certificate name.
Answer : C
Question 2
Click the Exhibit button. A customer has just finished their Azure deployment to secure a Web application behind a FortiGate and a FortiWeb. Now they want to add components to protect against advanced threats (zero day attacks), centrally manage the entire environment, and centrally monitor Fortinet and non-Fortinet products.
Which Fortinet solutions will satisfy these requirements?
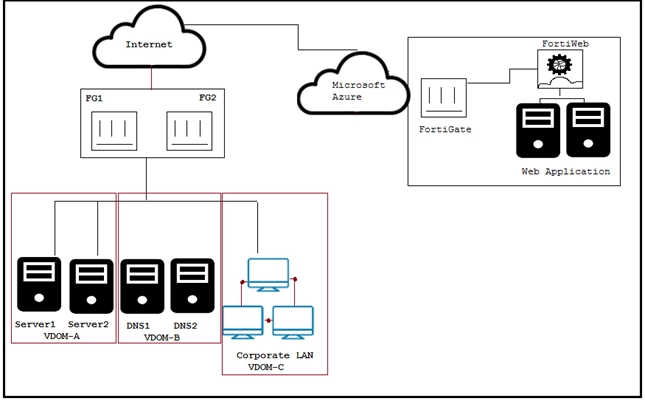
- A. Use FortiAnalyzer for monitoring in Azure, FortiSIEM for management, and FortiSandbox for zero day attacks on their local network.
- B. Use FortiAnalyzer for monitoring in Azure, FortiSIEM for management, and FortiGate for zero day attacks on their local network.
- C. Use FortiManager for management in Azure, FortiSIEM for monitoring, and FortiSandbox for zero day attacks on their local network.
- D. Use FortiSIEM for monitoring in Azure, FortiManager for management, and FortiGate for zero day attacks on their local network.
Answer : C
Question 3
Click the Exhibit button.
Referring to the exhibit, what will happen if FortiSandbox categorizes an e-mail attachment submitted by FortiMail as a high risk?
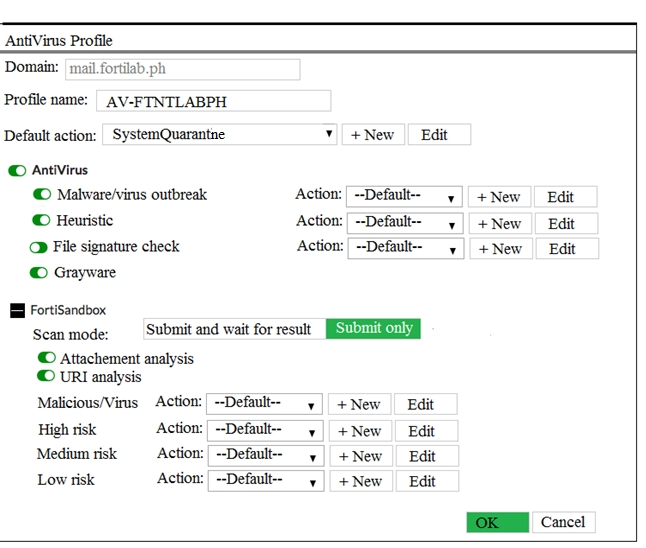
- A. The high-risk file will be discarded by attachment analysis.
- B. The high-risk file will go to the system quarantine.
- C. The high-risk file will be received by the recipient.
- D. The high-risk file will be discarded by malware/virus outbreak protection.
Answer : B
Question 4
Click the Exhibit button. Referring to the exhibit, which two statements are true? (Choose two.)
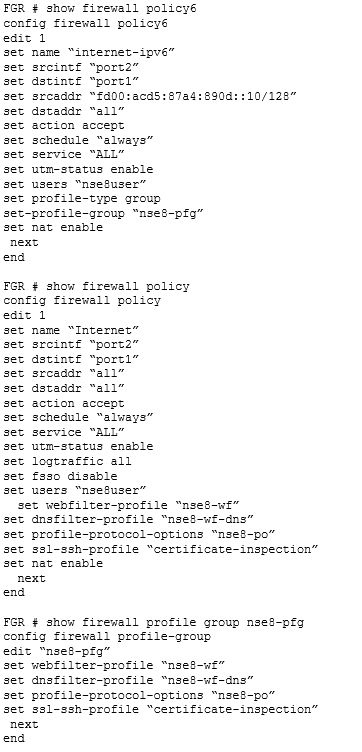
- A. The IPv4 traffic for nse8user is filtered using the DNS profile.
- B. The IPv6 traffic for nse8user is filtered using the DNS profile.
- C. The IPv4 policy is allowing security profile groups.
- D. The Web traffic for nse8user is being filtered differently in IPv4 and IPv6.
Answer : AD
Question 5
Click the Exhibit button.
You configured AV and Web filtering for your outgoing Internet connections. You later noticed that not all Web sessions are being inspected and you start troubleshooting the problem.
Referring to the exhibit, what would cause this problem?
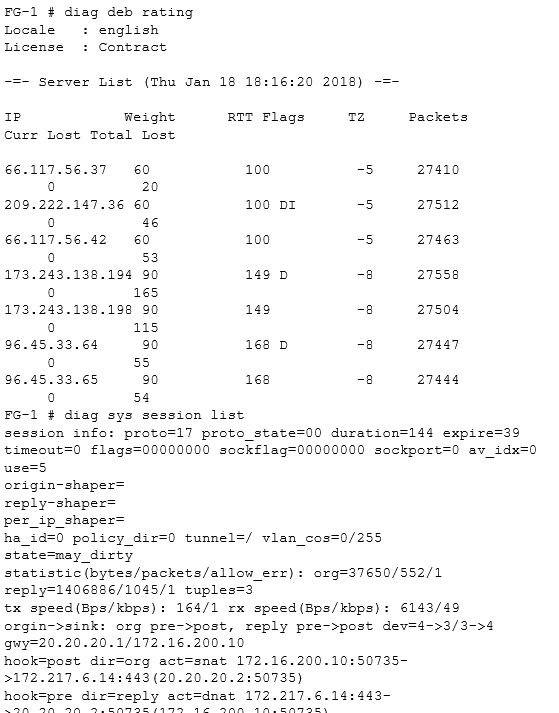
- A. The web session is using QUIC which is not inspected by the FortiGate.
- B. There are problems with the connection to the Web filter servers, therefore the Web session cannot be categorized.
- C. The SSL inspection options are not set to deep inspection.
- D. Web filtering is not licensed; therefore, no inspection occurs.
Answer : C
Question 6
Click the Exhibit button.
You have two data centers a FortiGate 7000-series chassis connected by VPN, and all traffic flows over an established generic routing encapsulation (GRE) tunnel between them. You are troubleshooting traffic that is traversing between Server VLAN A and Server VLAN B. The performance is lower than expected and all traffic is only on the FPM module in slot 3.
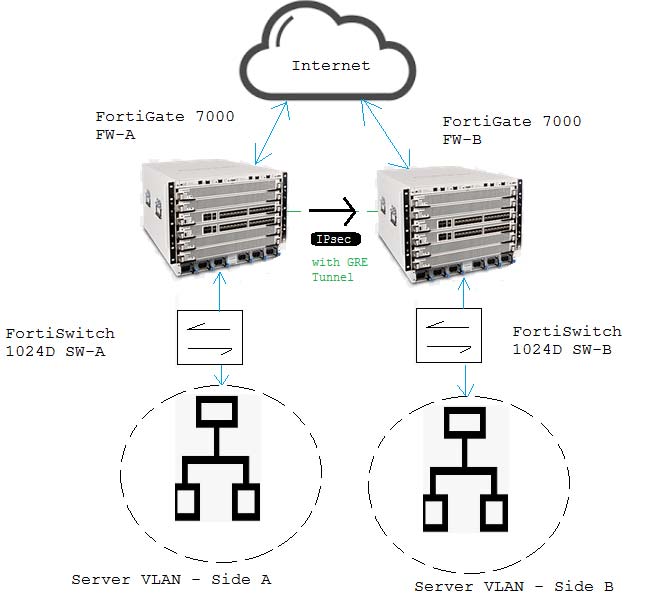
Referring to the exhibit, which action will correct the problem?
- A. Remove traffic shaping from the firewall policy allowing the traffic.
- B. No course of action enables load balancing in this scenario.
- C. Change the algorithm so it takes source IP, destination IP, and port into account.
- D. Configure a load-balance flow-rule in the CLI to enable load balancing.
Answer : C
Question 7
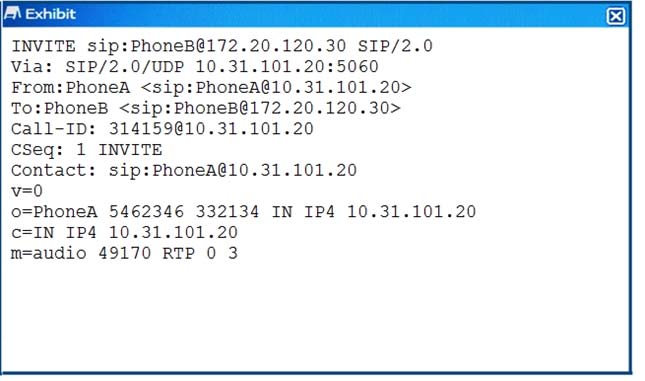
Click the Exhibit button.
A FortiGate with the default configuration is deployed between two IP phones. FortiGate receives the INVITE request shown in the exhibit form Phone A (internal) to Phone B (external). Which two actions are taken by the FortiGate after the packet is received? (Choose two.)
- A. A pinhole will be opened to accept traffic sent to FortiGate"™s WAN IP address and ports 49169 and 49170
- B. A pinhole will be opened to accept traffic sent to FortiGate"™s WAN IP address and ports 49170 and 49171.
- C. The Phone A IP address will be translated to the WAN IP address in all INVITE header fields and the m: field of the SDP statement.
- D. The Phone A IP address will be translated to the WAN IP address in all INVITE header fields and the SDP statement remains intact.
Answer : BD
Question 8
You are asked to add a FortiDDoS to the network to combat detected slow connection attacks such as Slowloris.
Which prevention mode on FortiDDoS will protect you against this specific type of attack?
- A. aggressive aging mode
- B. rate limiting mode
- C. blocking mode
- D. asymmetric mode
Answer : A
Question 9
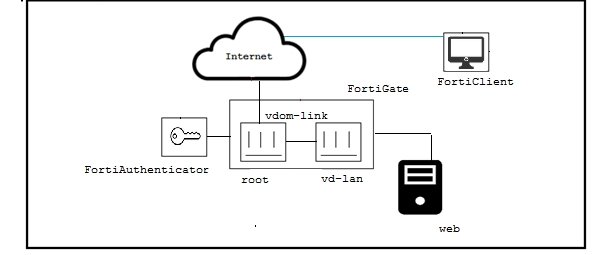
Click the Exhibit button. The exhibit shows a topology where a FortiGate is split into two VDOMs, access, where the users are authenticated by a FortiAuthenticator. The vd-lan VDOM provides internal access to a Web server. For the remote users to access the internal Web servers, there are a few requirements, which are shown below.
-> All traffic must come from the SSL-VPN
-> The vd-lan VDOM only allows authenticated traffic to the Web server.
-> Users must only authenticated once, using the SSL-VPN portal.
-> SSL-VPN uses RADIUS-based authentication
Referring to the exhibit, and the requirements described above, which two statements are true? (Choose two.)
- A. vd-lan receives authentication messages from root using FSSO
- B. vd-lan connects to FortiAuthenticator as a regular FSSO client
- C. root is configured for FSSO while vd-lan is configured for RSSO
- D. root sends "RADIUS Accounting Messages" to FortiAuthenticator
Answer : BD
Question 10
Click the Exhibit button. When deploying a new FortiGate-VMX Security node, an administrator received the error message shown in the exhibit.
In this scenario, which statement is correct?
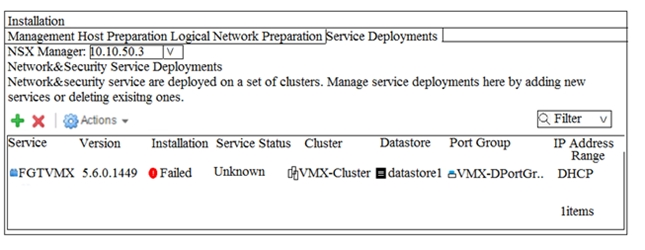
- A. The vCenter was not able locate the FortiGate-VMX"™s OVF file
- B. The vCenter could not connect to the FortiGate Service Manager.
- C. The NSX Manager was not able to connect on the FortiGate Service Manager RestAPI service.
- D. The FortiGate Service Manager did not have the proper permission to register the FortiGate ""VMX Service.
Answer : D
Question 11
Click the Exhibit button.
Your organization has a FortiGate cluster that is connected to two independent ISPs. You must configure the FortiGate failover for a single ISP failure to occur without disruption. Referring to the exhibit, which two FortiGate BGP features would be used to accomplish this task? (Choose two.)
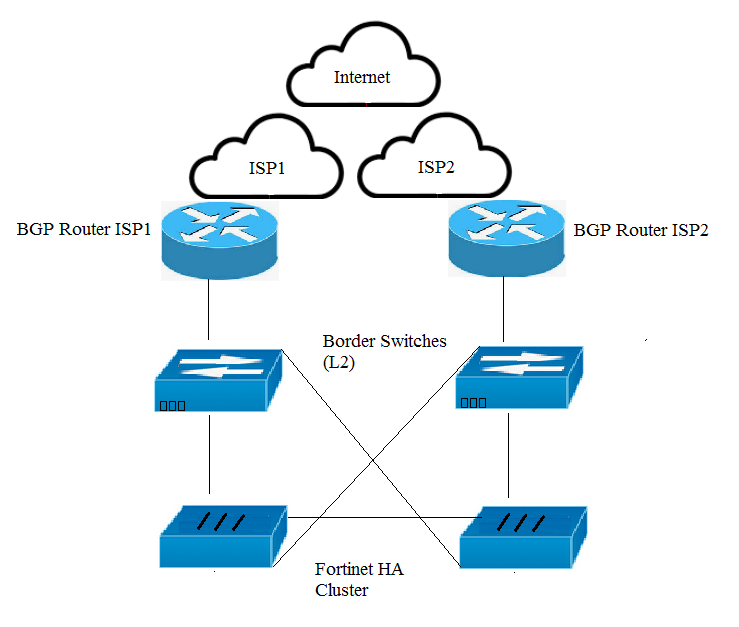
- A. Enable BFD.
- B. Enable EDGP multipath.
- C. Enable graceful restart.
- D. Enable synchronization.
Answer : AC
Question 12
An old router has been replaced by a FortiWAN device. The FortiWAN has inherited the router"™s management IP address and now the network administrator needs to remove the old router from the FortiSIEM configuration.
Which two statements are true about this operation? (Choose two.)
- A. FortiSIEM will discover a new device for the FortiWAN with the same IP.
- B. The old router will be completely deleted from FortiSIEM"™s CMDB.
- C. FortiSIEM needs a special syslog parser for FortiWAN.
- D. FortiSIEM will move the old router device into the Decommission folder.
Answer : AB
Question 13
You have a customer experiencing problems with a legacy L3/L4 firewall device and the IPv6 SIP VoIP traffic. Their device is dropping SIP packets, consequently, it cannot process SIP voice calls. Which solution would solve the customer"™s problem?
- A. Deploy a FortiVoice and enable IPv6 SIP.
- B. Replace their legacy device with a FortiGate and configure it to extract information from the body of the IPv6 SIP packet.
- C. Deploy a FortiVoice and enable an IPv6 SIP session helper.
- D. Replace their legacy device with a FortiGate and deploy a FortiVoice to extract information from the body of the IPv6 SIP packet.
Answer : D
Question 14
Click the Exhibit button. An administrator implements a multi-chassis link aggregation (MCLAG) solution using two FortiSwitch 448Ds and one FortiGate 3700D.
As describes in the network topology shown in the exhibit, two links are connected to each FortiSwitch. What is requires to implement this solution? (Choose two.)
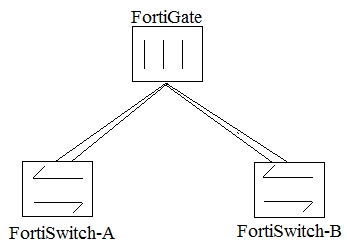
- A. A FortiGate with a hardware or a software switch
- B. an ICl link between both FortiSwitches
- C. a disabled FortiLink split interface
- D. two link aggregated (LAG) interfaces on the FortiGate side
Answer : CD
Question 15
Click the Exhibit button.
The exhibit shows a full-mesh topology between FortiGates and FortiSwitches. To deploy this configuration, two requirements must be met:
-20 Gbps full duplex connectivity is available between each FortiGate and the FortiSwitches
-The FortiGate HA must be in AP mode.
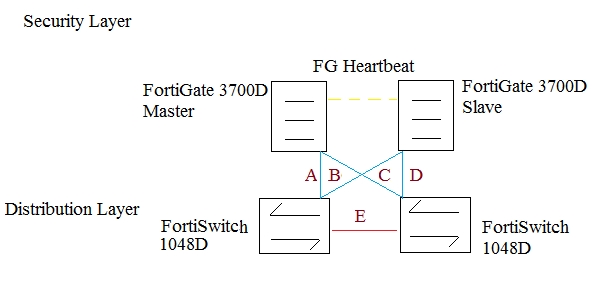
Referring to the exhibit, what are two actions that will fulfill the requirements? (Choose two.)
- A. Configure both FortiSwitches as peers with ICL over cable E, create one MCLAG on ports connected to cables A and C, and create another MCLAG on ports connected to cables B and D.
- B. Configure the master FortiGate with one LAG and FortiLink split interface disabled on ports connected to cables A and C and make sure the same ports are used for cables B and D on the slave.
- C. Configure both FortiSwitches as peers with ISL over cable E, create one MCLAG on ports connected to cables A and C, and create another MCLAG on ports connected to cables B and D.
- D. Configure the master FortiGate with one LAG and FortiLink split interface enabled on ports connected to cables A and C and make sure the same ports are used for cables B and D on the slave.
Answer : AC