Fortinet Network Security Expert 8 Written Exam v8.0
Question 1
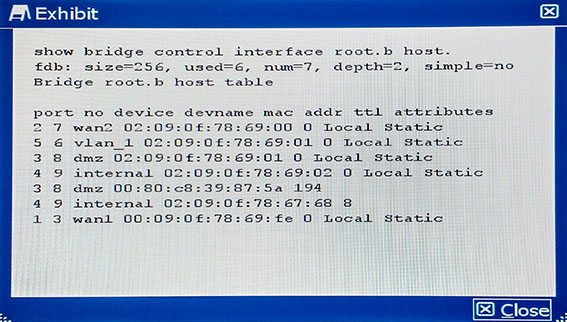
Referring to the command output shown in the exhibit, how many hosts are connected to the FortiGate?
- A. 7
- B. 6
- C. 2
- D. 256
Answer : B
Explanation:
References:
http://cookbook.fortinet.com/troubleshooting-fortigate-installation/
Question 2
FortiGate1 has a gateway-to-gateway IPsec VPN to FortiGate2. The entire IKE negotiation between FortiGate1 and FortiGate2 is on UDP port 500. A PC on FortuGate2s local area network is sending continuous ping requests over the VPN tunnel to a PC of FortiGate1s local area network. No other traffic is sent over the tunnel.
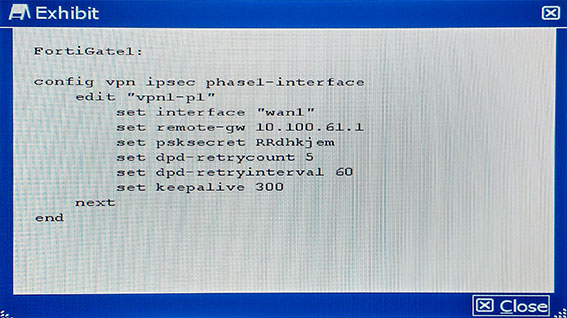
Which statement is true on this scenario?
- A. FortiGate1 sends an R-U-THERE packet every 300 seconds while ping traffic is flowing.
- B. FortiGate1 sends an R-U-THERE packet if pings stop for 300 seconds and no IKE packet is received during this period.
- C. FortiGate1 sends an R-U-THERE packet if pings stop for 60 seconds and no IKE packet is received during this period.
- D. FortiGate1 sends an R-U-THERE packet every 60 seconds while ping traffic is flowing.
Answer : C
Explanation:
References:
http://kb.fortinet.com/kb/documentLink.do?externalID=FD35337
Question 3
The SECOPS team in your company has started a new project to store all logging data in a disaster recovery center. All FortiGates will log to a secondary FortiAnalyzer and establish a TCP session to send logs to the syslog server.
Which two configurations will achieve this goal? (Choose two.)
- A.
- B.
- C.
- D.
Answer : AC
Explanation:
https://forum.fortinet.com/tm.aspx?m=122848
Question 4
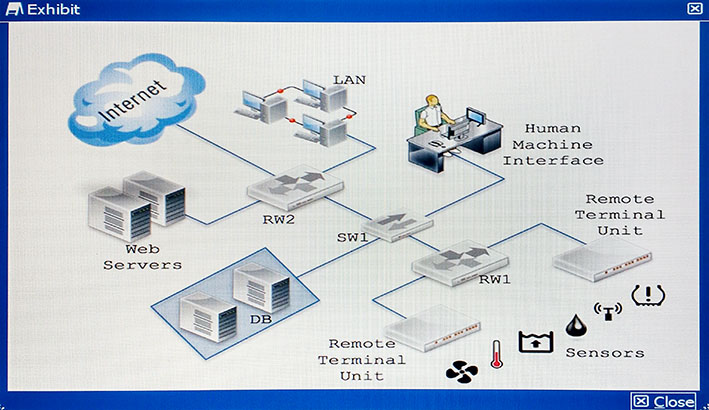
How would you apply security to the network shown in the exhibit?
- A. Replace RW1 with a ruggedized FortiGate and RW2 with a normal FortiGate. Enable industrial category on the application control. Place a FortiGate to secure Web servers. Configure IPsec to secure sensors data. Place a ruggedized FortiAP to provide Wi-Fi to the sensors.
- B. Replace RW1 with a normal FortiGate and RW2 with a ruggedized FortiGate. Enable industrial category on the application control. Place a FortiGate to secure Web servers. Configure IPsec to secure sensors data. Place a FortiAP to provide Wi-Fi to the sensors.
- C. Replace RW1 with a normal FortiGate and RW2 with a ruggedized FortiGate. Enable industrial category on the Web filter. Place a FortiWeb to secure Web servers. Configure IPsec to secure sensors data. Place a ruggedized FortiAP to provide Wi-Fi to the sensors.
- D. Replace RW1 with a normal FortiGate and RW2 with a ruggedized FortiGate. Enable industrial category on the application control. Place a FortiWeb to secure Web servers. Configure IPsec to secure sensors data. Place a ruggedized FortiAP to provide Wi-Fi to the sensors.
Answer : D
Question 5
You want to enable traffic between 2001:db8:1::/64 and 2001:db8:2::/64 over the public
IPv4 Internet.
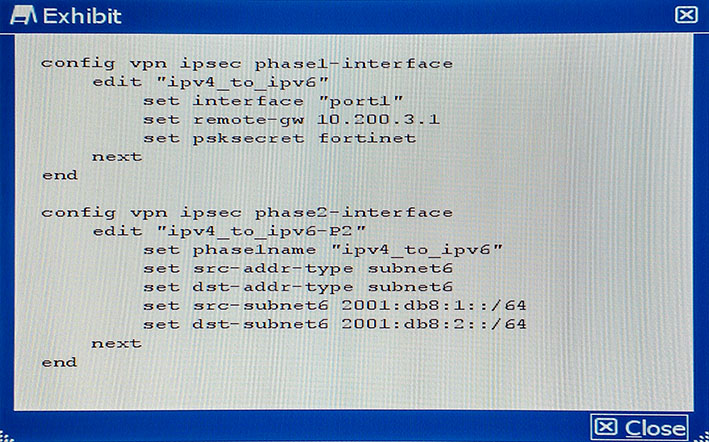
Given the CLI configuration shown in the exhibit, which two additional settings are required on this device to implement tunneling for the IPv6 transition? (Choose two.)
- A. IPv4 firewall policies to allow traffic between the local and remote IPv6 subnets.
- B. IPv6 static route to the destination phase2 destination subnet.
- C. IPv4 static route to the destination phase2 destination subnet.
- D. IPv6 firewall policies to allow traffic between the local and remote IPv6 subnets.
Answer : BD
Explanation:
References:
http://docs.fortinet.com/uploaded/files/1969/IPv6%20Handbook%20for%20FortiOS%205.2. pdf
Question 6
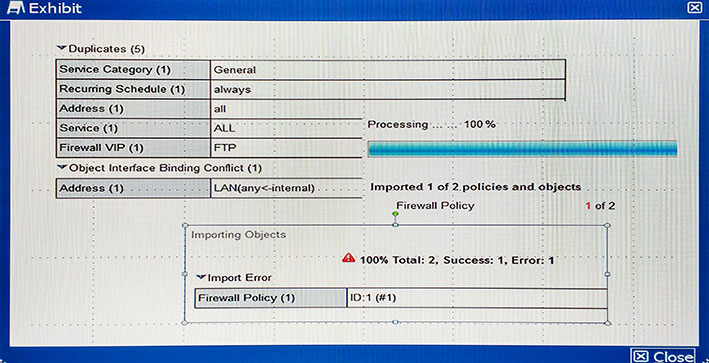
Given the following error message:
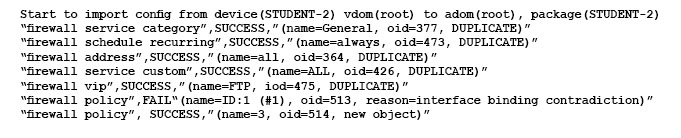
FortiManager fails to import policy ID 1.
What is the problem?
- A. FortiManager already has Address LAN which has interface mapping set to internal in its database, it is contradicting with the STUDENT-2 FortiGate device which has address LAN mapped to any.
- B. FortiManager already has address LAN which has interface mapping set to “any” in its database; this conflicts with the STUDENT-2 FortiGate device which has address “LAN” mapped to “internal”.
- C. Policy ID 1 for this managed FortiGate device already exists on the FortiManager policy package named STUDENT-2.
- D. Policy ID 1 does not have interface mapping on FortiManager.
Answer : D
Explanation:
References:
http://kb.fortinet.com/kb/documentLink.do?externalID=FD38544
Question 7
You verified that application control is working from previous configured categories. You just added Skype on blocked signatures. However, after applying the profile to your firewall policy, clients running Skype can still connect and use the application.
What are two causes of this problem? (Choose two.)
- A. The application control database is not updated.
- B. SSL inspection is not enabled.
- C. A client on the network was already connected to the Skype network and serves as relay prior to configuration changes to block Skype
- D. The FakeSkype.botnet signature is included on your application control sensor.
Answer : AB
Question 8
Which three statements about throughput on a wireless network are true? (Choose three.)
- A. A wireless device labelled as 300 Mbps should be expected to provide a throughput of 300Mbps.
- B. Be careful to ensure the capabilities of the wireless clients match those of the access points, in order to achieve higher throughput.
- C. Reducing the duty cycles of the wireless media by generating fewer beacons may improve throughput.
- D. Because of the higher level of RF noise that is typical in the 2.4 GHz ISM band, throughput of 2.4 GHz devices will typically be less than 5 GHz devices.
- E. Because of the full-duplex nature of the medium and the minimal overhead generated by CSMA/CA, the actual aggregate throughput is typically close to the data rate.
Answer : B,C,D
Explanation:
References:
http://www.tp-link.in/faq-499.html
Question 9
You have replaced an explicit proxy Web filter with a FortiGate. The human resources department requires that all URLs be logged. Users are reporting that their browsers are now indicating certificate errors as shown in the exhibit.
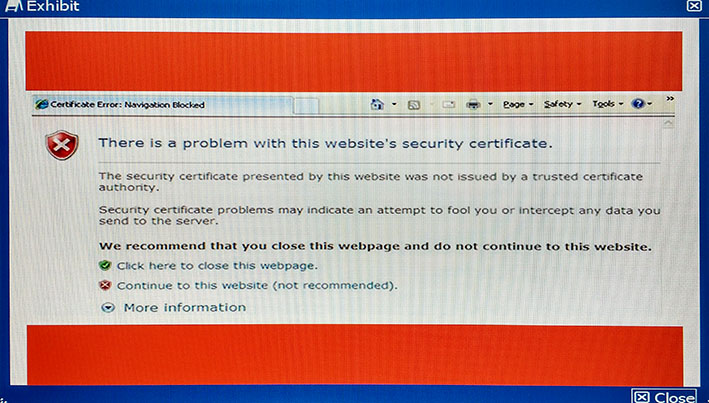
Which step is a valid solution to the problem?
- A. Make sure that the affected users’ browsers are no longer set to use the explicit proxy.
- B. Import the FortiGate’s SSL CA certificate into the Web browsers.
- C. Change the Web filter policies on the FortiGate to only do certificate inspection.
- D. Make a Group Policy to install the FortiGates SSL certificate as a trusted host certificate on the Web browser.
Answer : D
Explanation:
For https traffic inspection, client machine should install fortigates ssl certificate
Question 10
You are asked to implement a wireless network for a conference center and need to provision a high number of access points to support a large number of wireless client connections.
Which statement describes a valid solution for this requirement?
- A. Use a captive portal for guest access. Use both 2.4 GHz and 5 GHz bands. Enable frequency and access point hand-off. Use more channels, thereby supporting more clients.
- B. Use an open wireless network with no portal. Use both 2.4 GHz and 5 GHz bands. Use 802.11ac capable access points and configure channel bonding to support greater throughput for wireless clients.
- C. Use a pre-shared key only for wireless client security. Use the 5 GHz band only for greater security. Use 802.11ac capable access points and configure channel bonding to support greater throughput for wireless clients.
- D. Use a captive portal for guest access. Use both the 2.4 GHz and 5 GHz bands, and configure frequency steering. Configure rogue access point detection in order to automatically control the transmit power of each AP.
Answer : D
Question 11
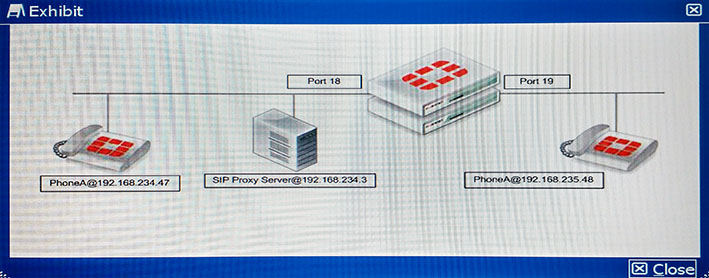
Referring to the exhibit, users are reporting that their FortiFones ring but when they pick up, the cannot hear each other. The FortiFones use SIP to communicate with the SIP Proxy
Server and RTP between the phones.
Which configuration change will resolve the problem?
- A.
- B.
- C.
- D.
Answer : C
Explanation:
References:
http://docs.fortinet.com/uploaded/files/2813/fortigate-sip-54.pdf
Question 12
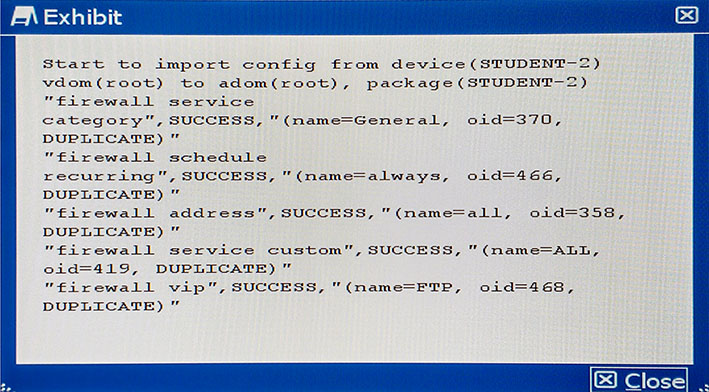
The output shown in the exhibit from FortiManager is displayed during an import of the device configuration.
Which statement describes the correct action taken for these duplicate objects?
- A. The import fails because of the duplicate entries detected which exist in the ADOM database.
- B. FortiManager installs these duplicate objects to the managed device from the ADOM database.
- C. FortiManager does not import these duplicate entries into the ADOM database because they already exist in the ADOM database.
- D. FortiManager creates indexed duplicate entries for these objects in the ADOM database.
Answer : B
Explanation:
References:
http://docs.fortinet.com/uploaded/files/2905/FortiManager-5.4.0-Administration-Guide.pdf
Question 13
Which VPN protocol is supported by FortiGate units?
- A. E-LAN
- B. PPTP
- C. DMVPN
- D. OpenVPN
Answer : BC
Question 14
You are investigating a problem related to FTP active mode. You use a test PC with IP address 10.100.60.5 to connect to the FTP server at 172.16.133.50 and transfer a large file. The FortiGate translates source address (SNAT) in network 10.100.60.0/24 to the IP address 172.16.133.1.
Which two groups of CLI commands allow you to see information related to this FTP connection (Choose two.)
- A.
- B.
- C.
- D.
Answer : A,D
Explanation:
FTP active on port 21 and passive uses port 20
Question 15
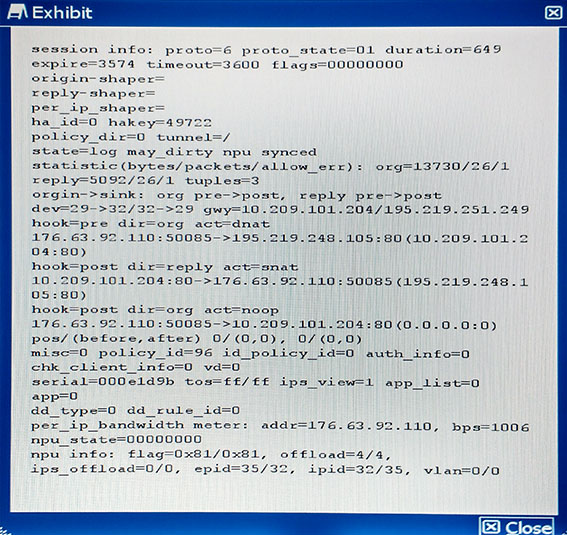
Referring to the configuration shown in the exhibit, which three statements are true?
(Choose three.)
- A. Traffic logging is disabled in policy 96.
- B. TCP handshake is completed and no FIN/RST has been forwarded.
- C. No packet has hit this session in the last five minutes.
- D. No QoS is applied to this traffic.
- E. The traffic goes through a VIP applied to policy 96.
Answer : B,C,E
Explanation:
References:
http://kb.fortinet.com/kb/viewContent.do?externalId=FD30042