FortiMail 5.3.8 Specialist v1.0
Question 1
Examine the FortiMail session profile and protected domain configuration shown in the exhibit; then answer the question below.
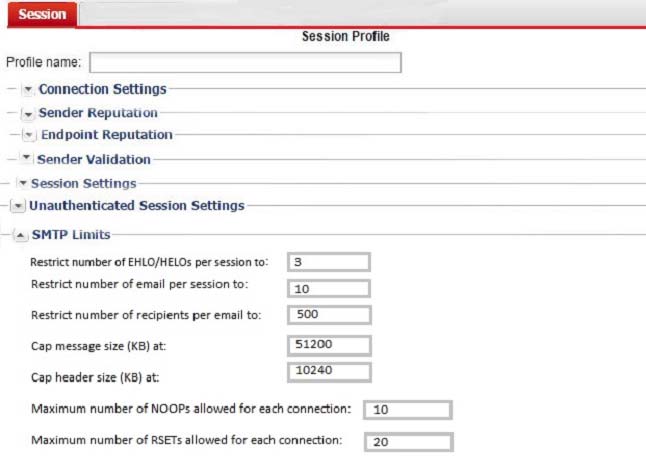
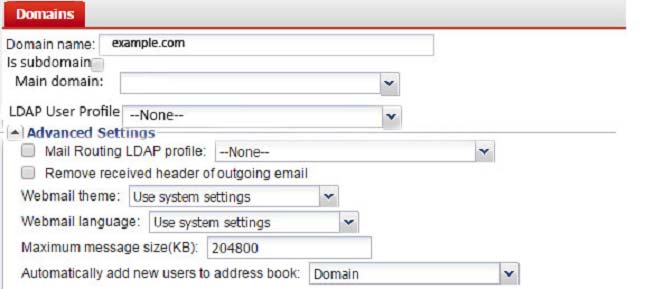
Which size limit will FortiMail apply to outbound email?
- A. 204800
- B. 51200
- C. 1024
- D. 10240
Answer : A
Question 2
Examine the FortiMail antivirus action profile shown in the exhibit; then answer the question below.
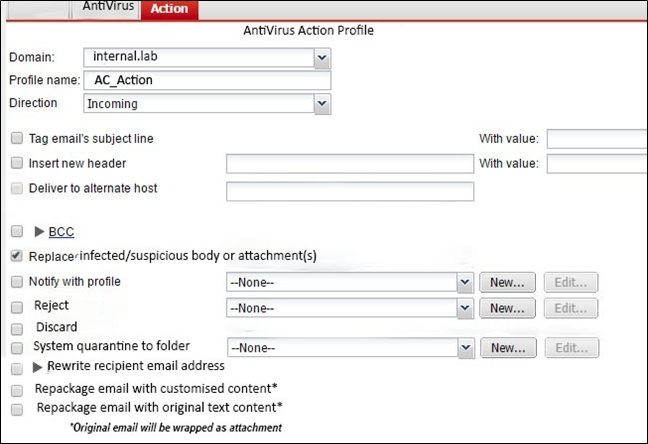
What is the expected outcome if FortiMail applies this action profile to an email? (Choose two.)
- A. The sanitized email will be sent to the recipient"™s personal quarantine
- B. A replacement message will be added to the email
- C. Virus content will be removed from the email
- D. The administrator will be notified of the virus detection
Answer : BC
Question 3
Examine the FortiMail recipient-based policy shown in the exhibit; then answer the question below.
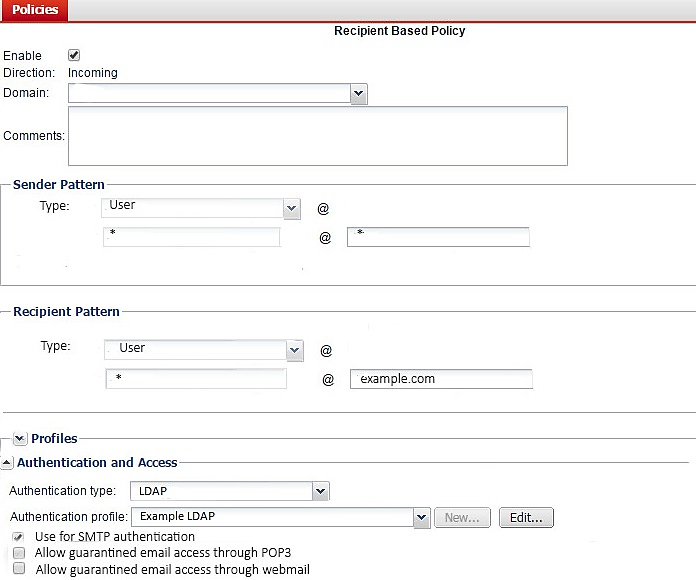
After creating the policy, an administrator discovered that clients are able to send unauthenticated email using SMTP. What must be done to ensure clients cannot send unauthenticated email?
- A. Configure a matching IP policy with SMTP authentication and exclusive flag enabled
- B. Move the recipient policy to the top of the list
- C. Configure an access receive rule to verify authentication status
- D. Configure an access delivery rule to enforce authentication
Answer : A
Question 4
FortiMail is configured with the protected domain "example.com". Identify which of the following envelope addresses will require an access receive rule to relay for unauthenticated senders? (Choose two.)
- A. MAIL FROM: [email protected] RCPT TO: [email protected]
- B. MAIL FROM: [email protected] RCPT TO: [email protected]
- C. MAIL FROM: [email protected] RCPT TO: [email protected]
- D. MAIL FROM: [email protected] RCPT TO: [email protected]
Answer : CD
Question 5
Examine the nslookup output shown in the exhibit; then answer the question below.
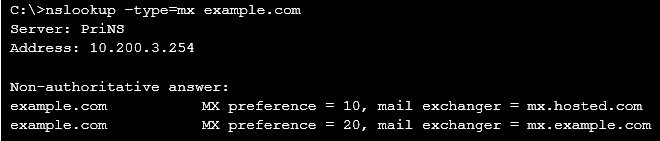
Identify which of the following statements is true regarding the example.com domain"™s MTAs. (Choose two.)
- A. External MTAs will send email to mx.example.com only if mx.hosted.com is unreachable
- B. The primary MTA for the example.com domain is mx.hosted.com
- C. The PriNS server should receive all email for the example.com domain
- D. The higher preference value is used to load balance more email to the mx.example.com MTA
Answer : CD
Question 6
What are the configuration steps to enable DKIM signing for outbound messages on FortiMail? (Choose three.)
- A. Enable DKIM signing for outgoing messages in a matching session profile
- B. Publish the public key as a TXT record in a public DNS server
- C. Enable DKIM check in a matching session profile
- D. Enable DKIM check in a matching antispam profile
- E. Generate a public/private key pair in the protected domain configuration
Answer : ACE
Question 7
Examine the FortMail mail server settings shown in the exhibit; then answer the question below.
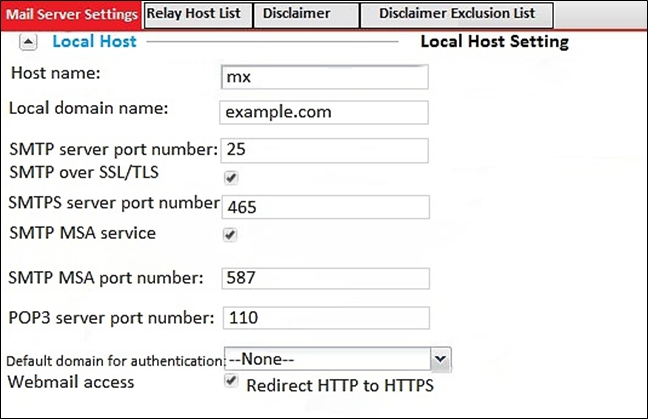
Which of the following statements are true? (Choose two.)
- A. mx.example.com will enforce SMTPS on all outbound sessions
- B. mx.example.com will display STARTTLS as one of the supported commands in SMTP sessions
- C. mx.example.com will accept SMTPS connections
- D. mx.example.com will drop any inbound plaintext SMTP connection
Answer : AC
Question 8
Examine the FortiMail active-passive cluster shown in the exhibit; then answer the question below.
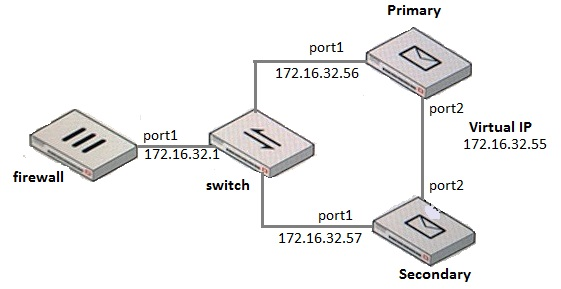
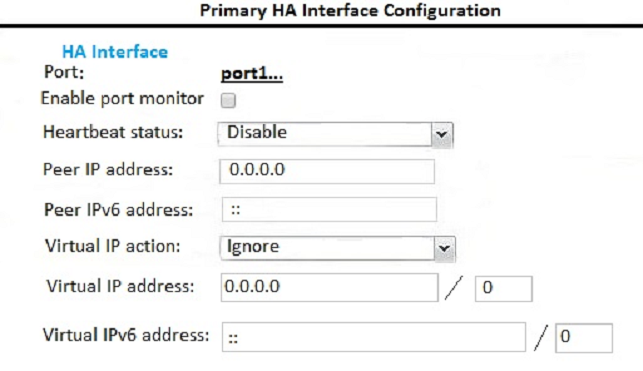
Which of the following parameters are recommended for the Primary FortiMail"™s HA interface configuration? (Choose three.)
- A. Enable port monitor: disable
- B. Peer IP address: 172.16.32.57
- C. Heartbeat status: Primary
- D. Virtual IP address: 172.16.32.55/24
- E. Virtual IP action: Use
Answer : CDE
Question 9
Which of the following CLI commands, if executed, will erase all data on the log disk partition? (Choose two.)
- A. execute formatmaildisk
- B. execute formatmaildisk_backup
- C. execute formatlogdisk
- D. execute partitionlogdisk 40
Answer : CD
Question 10
Examine the FortiMail IBE users shown in the exhibit; then answer the question below
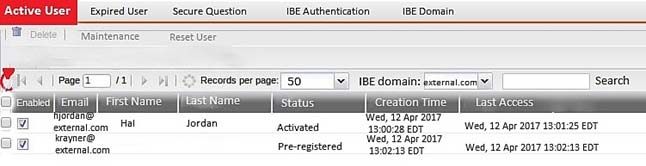
Which one of the following statements describes the Pre-registered status of the IBE user [email protected]?
- A. The user was registered by an administrator in anticipation of IBE participation
- B. The user has completed the IBE registration process but has not yet accessed their IBE email
- C. The user has received an IBE notification email, but has not accessed the HTTPS URL or attachment yet
- D. The user account has been de-activated, and the user must register again the next time they receive an IBE email
Answer : C
Question 11
Examine the access receive rule shown in the exhibit; then answer the question below.
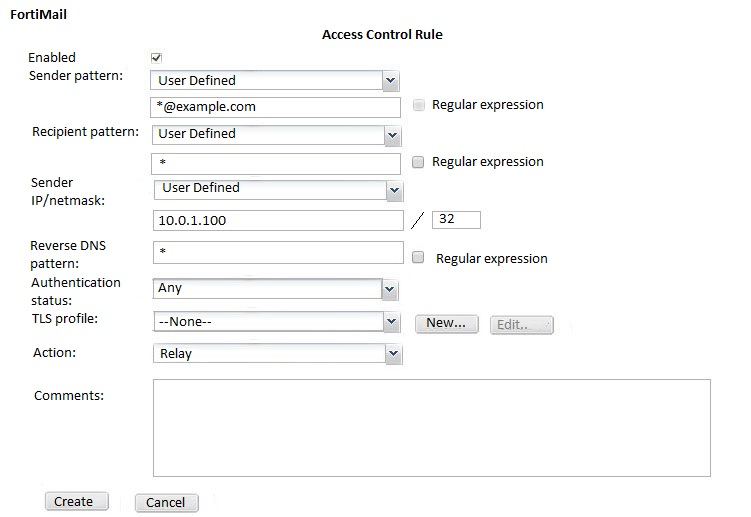
Which of the following statements are true? (Choose two.)
- A. Email from any host in the 10.0.1.0/24 subnet can match this rule
- B. Senders must be authenticated to match this rule
- C. Email matching this rule will be relayed
- D. Email must originate from an example.com email address to match this rule
Answer : CD
Question 12
Which of the following statements are true regarding FortiMail"™s behavior when using the built-in MTA to process email in transparent mode? (Choose two.)
- A. FortiMail can queue undeliverable messages and generate DSNs
- B. If you disable the built-in MTA, FortiMail will use its transparent proxies to deliver email
- C. FortiMail ignores the destination set by the sender and uses its own MX record lookup to deliver email
- D. MUAs need to be configured to connect to the built-in MTA to send email
Answer : BC
Question 13
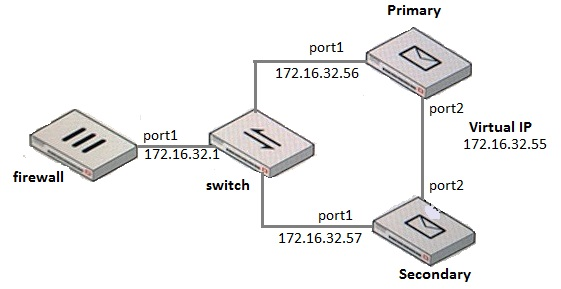
What IP address should the DNS MX record for this deployment resolve to?
- A. 172.16.32.1
- B. 172.16.32.57
- C. 172.16.32.55
- D. 172.16.32.56
Answer : C
Question 14
Examine the FortiMail topology and access receive rule shown in the exhibit; then answer the question below.
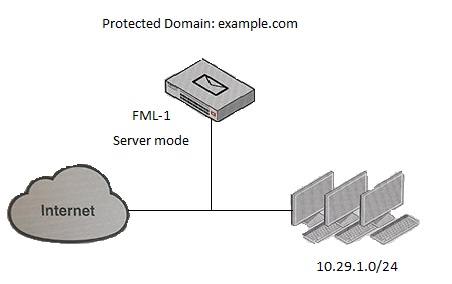
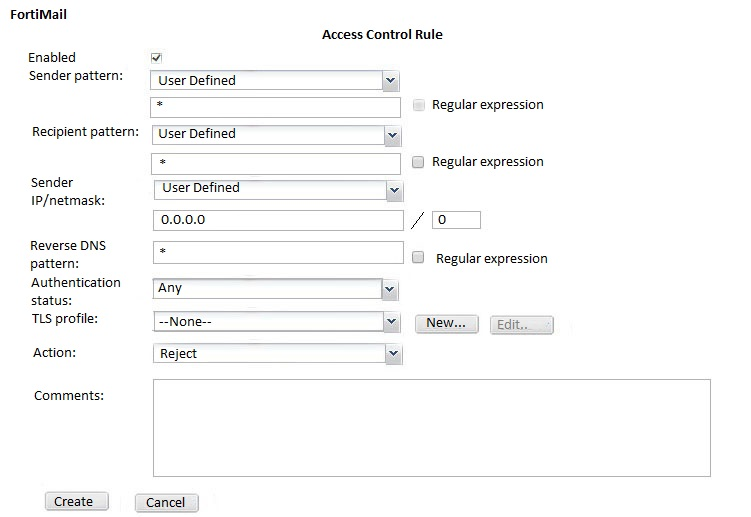
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain. Which of the following settings should be used to configure the access receive rule? (Choose two.)
- A. The Sender IP/netmask should be set to 10.29.1.0/24
- B. The Authentication status should be set to Authenticated
- C. The Recipient pattern should be set o *@example.com
- D. The Action should be set to Reject
Answer : CD
Question 15
Examine the configured routes shown in the exhibit; then answer the question below.
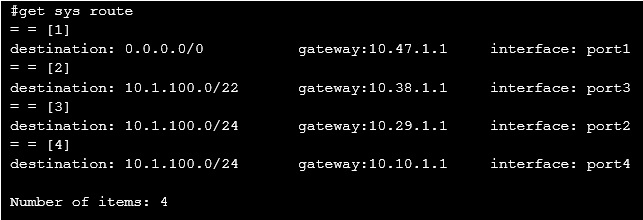
Which interface will FortiMail use to forward an email message destined for 10.1.100.252?
- A. port2
- B. port4
- C. port3
- D. port1
Answer : A