Fortinet NSE 4 - FortiOS 7.0 v1.0
Question 1
Refer to the exhibit.
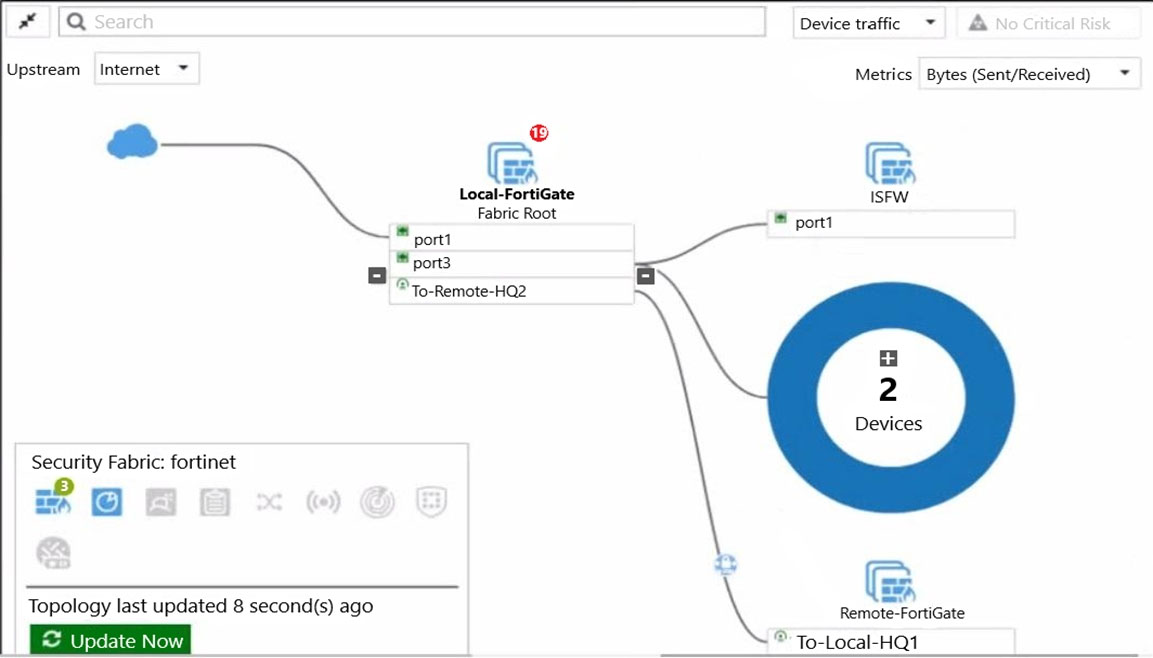
Given the security fabric topology shown in the exhibit, which two statements are true? (Choose two.)
- A. There are five devices that are part of the security fabric.
- B. There are 19 security recommendations for the security fabric.
- C. Device detection is disabled on all FortiGate devices.
- D. This security fabric topology is a logical topology view.
Answer : BD
References:
https://docs.fortinet.com/document/fortigate/5.6.0/cookbook/761085/results https://docs.fortinet.com/document/fortimanager/6.2.0/new-features/736125/security-fabric-topology
Question 2
A network administrator is configuring a new IPsec VPN tunnel on FortiGate. The remote peer IP address is dynamic. In addition, the remote peer does not support a dynamic DNS update service.
What type of remote gateway should the administrator configure on FortiGate for the new IPsec VPN tunnel to work?
- A. Dialup User
- B. Static IP Address
- C. Pre-shared Key
- D. Dynamic DNS
Answer : A
Explanation:
Dialup user is used when the remote peer's IP address is unknown. The remote peer whose IP address is unknown acts as the dialup clien and this is often the case for branch offices and mobile VPN clients that use dynamic IP address and no dynamic DNS
Question 3
An administrator wants to configure Dead Peer Detection (DPD) on IPSEC VPN for detecting dead tunnels. The requirement is that FortiGate sends DPD probes only when no traffic is observed in the tunnel.
Which DPD mode on FortiGate will meet the above requirement?
- A. On Demand
- B. Disabled
- C. On Idle
- D. Enabled
Answer : C
Reference:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD40813
Question 4
Which three statements about a flow-based antivirus profile are correct? (Choose three.)
- A. IPS engine handles the process as a standalone
- B. Flow-based inspection uses a hybrid of scanning modes available in proxy-based inspection.
- C. If the virus is detected, the last packet is delivered to the client.
- D. Optimized performance compared to proxy-based inspection.
- E. FortiGate buffers the whole file but transmits to the client simultaneously.
Answer : BDE
Reference:
https://forum.fortinet.com/tm.aspx?m=192309
Question 5
An administrator has configured a strict RPF check on FortiGate.
Which statement is true about the strict RPF check?
- A. The strict RPF check is run on the first sent and reply packet of any new session.
- B. Strict RPF checks the best route back to the source using the incoming interface.
- C. Strict RPF checks only for the existence of at least one active route back to the source using the incoming interface.
- D. Strict RPF allows packets back to sources with all active routes.
Answer : B
Reference:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD33955
Question 6
Refer to the exhibit.
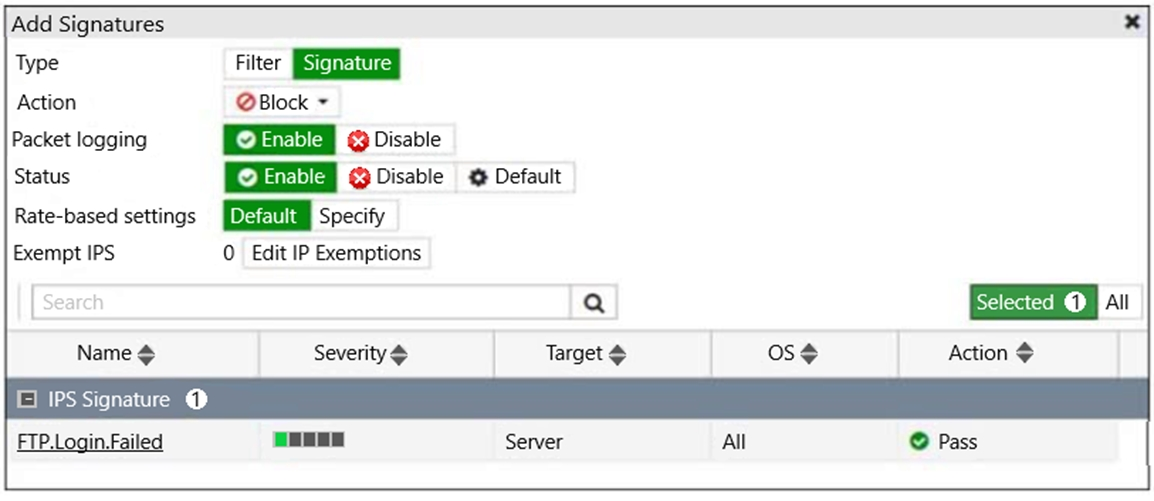
Review the Intrusion Prevention System (IPS) profile signature settings.
Which statement is correct in adding the FTP.Login.Failed signature to the IPS sensor profile?
- A. Traffic matching the signature will be silently dropped and logged.
- B. The signature setting uses a custom rating threshold.
- C. The signature setting includes a group of other signatures.
- D. Traffic matching the signature will be allowed and logged.
Answer : A
Question 7
Refer to the exhibit.
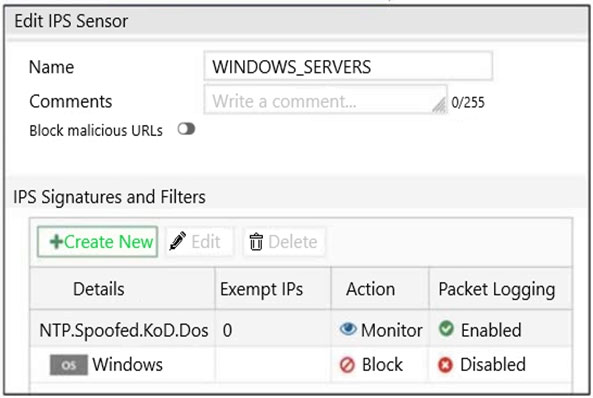
The exhibit shows the IPS sensor configuration.
If traffic matches this IPS sensor, which two actions is the sensor expected to take? (Choose two.)
- A. The sensor will block all attacks aimed at Windows servers.
- B. The sensor will gather a packet log for all matched traffic.
- C. The sensor will allow attackers matching the NTP.Spoofed.KoD.DoS signature.
- D. The sensor will reset all connections that match these signatures.
Answer : AC
Question 8
Which two attributes are required on a certificate so it can be used as a CA certificate on SSL Inspection? (Choose two.)
- A. The CA extension must be set to TRUE.
- B. The issuer must be a public CA.
- C. The common name on the subject field must use a wildcard name.
- D. The keyUsage extension must be set to keyCertSign.
Answer : AD
Reference:
https://www.reddit.com/r/fortinet/comments/c7j6jg/recommended_ssl_cert/
Question 9
A network administrator has enabled SSL certificate inspection and antivirus on FortiGate. When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the virus and the file can be downloaded.
What is the reason for the failed virus detection by FortiGate?
- A. Antivirus definitions are not up to date.
- B. SSL/SSH Inspection profile is incorrect.
- C. Antivirus profile configuration is incorrect.
- D. Application control is not enabled.
Answer : B
Question 10
Which two protocols are used to enable administrator access of a FortiGate device? (Choose two.)
- A. FortiTelemetry
- B. HTTPS
- C. SSH
- D. FTM
Answer : BC
Reference:
https://docs.fortinet.com/document/fortigate/6.4.0/hardening-your-fortigate/995103/building-security-into-fortios
Question 11
Refer to the exhibit.
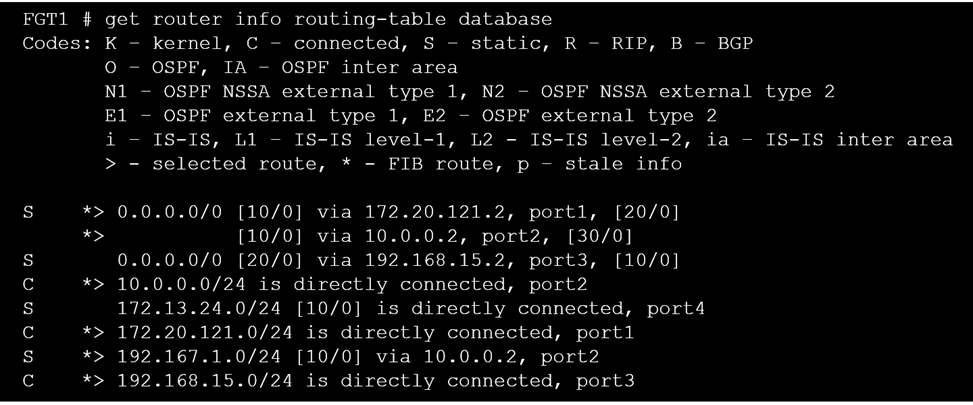
Given the routing database shown in the exhibit, which two statements are correct? (Choose two.)
- A. The port3 default route has the lowest metric.
- B. There will be eight routes active in the routing table.
- C. The port1 and port2 default routes are active in the routing table.
- D. The port3 default route has the highest distance.
Answer : CD
Question 12
Which statement about the policy ID number of a firewall policy is true?
- A. It changes when firewall policies are reordered.
- B. It defines the order in which rules are processed.
- C. It represents the number of objects used in the firewall policy.
- D. It is required to modify a firewall policy using the CLI.
Answer : D
Question 13
Which two settings can be separately configured per VDOM on a FortiGate device? (Choose two.)
- A. Operating mode
- B. NGFW mode
- C. System time
- D. FortiGuard update servers
Answer : AB
Question 14
Refer to the exhibits.
Exhibit A.
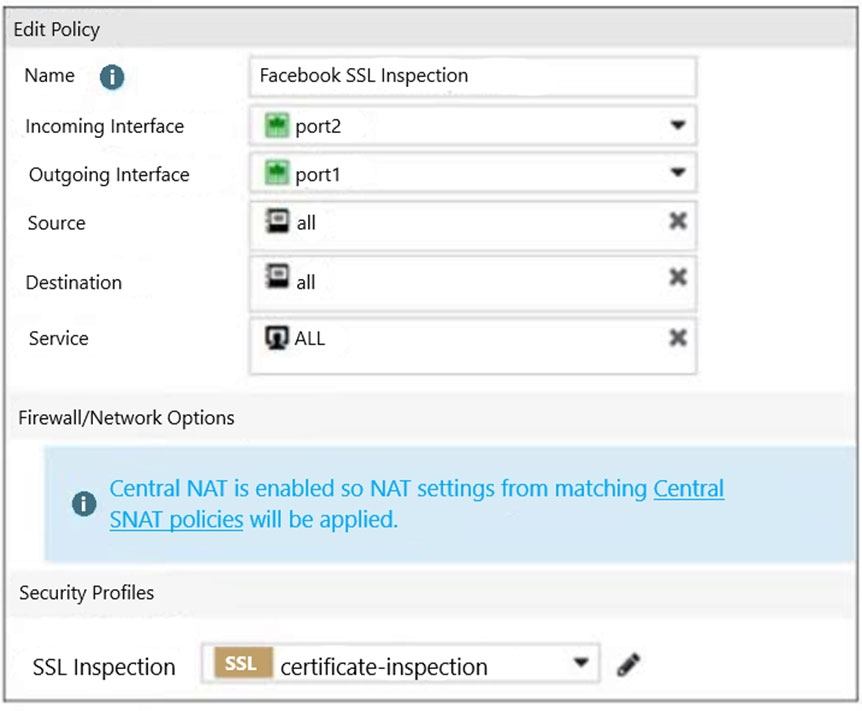
Exhibit B.
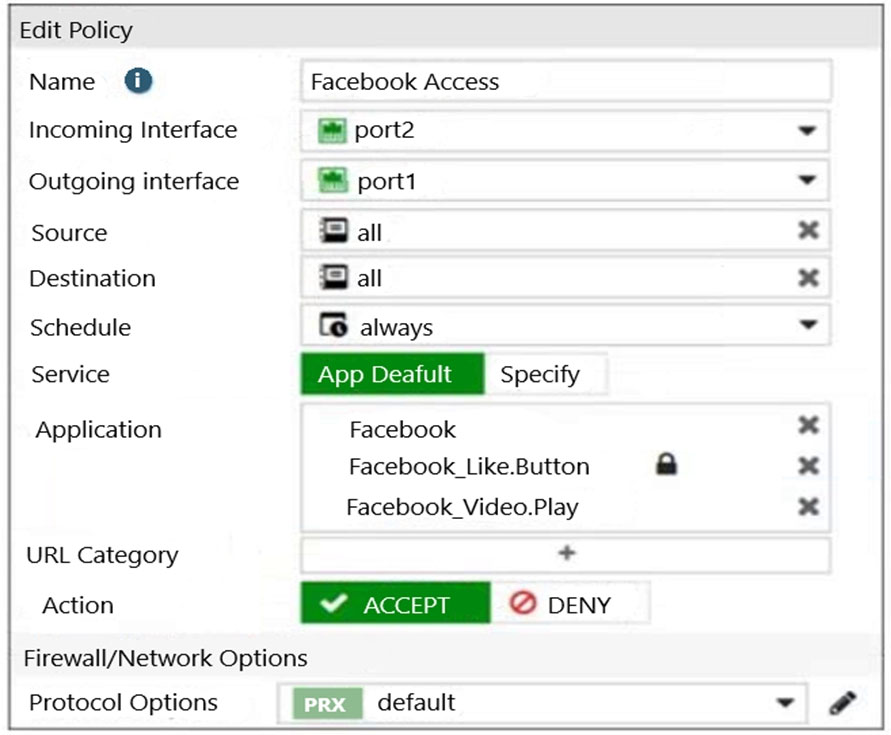
The exhibits show the SSL and authentication policy (Exhibit A) and the security policy (Exhibit B) for Facebook.
Users are given access to the Facebook web application. They can play video content hosted on Facebook but they are unable to leave reactions on videos or other types of posts.
Which part of the policy configuration must you change to resolve the issue?
- A. Add Facebook in the URL category in the security policy.
- B. Additional application signatures are required to add to the security policy.
- C. Force access to Facebook using the HTTP service.
- D. The SSL inspection needs to be a deep content inspection.
Answer : D
Explanation:
The lock logo behind Facebook_like.Button indicates that SSL Deep Inspection is Required.
Question 15
When configuring a firewall virtual wire pair policy, which following statement is true?
- A. Any number of virtual wire pairs can be included, as long as the policy traffic direction is the same.
- B. Only a single virtual wire pair can be included in each policy.
- C. Any number of virtual wire pairs can be included in each policy, regardless of the policy traffic direction settings.
- D. Exactly two virtual wire pairs need to be included in each policy.
Answer : C