Fortinet NSE 4 - FortiOS 6.4 v1.0
Question 1
An administrator must disable RPF check to investigate an issue.
Which method is best suited to disable RPF without affecting features like antivirus and intrusion prevention system?
- A. Enable asymmetric routing, so the RPF check will be bypassed.
- B. Disable the RPF check at the FortiGate interface level for the source check.
- C. Disable the RPF check at the FortiGate interface level for the reply check.
- D. Enable asymmetric routing at the interface level.
Answer : D
Reference:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD33955
Question 2
A network administrator wants to set up redundant IPsec VPN tunnels on FortiGate by using two IPsec VPN tunnels and static routes.
✑ All traffic must be routed through the primary tunnel when both tunnels are up.
✑ The secondary tunnel must be used only if the primary tunnel goes down.
✑ In addition, FortiGate should be able to detect a dead tunnel to speed up tunnel failover.
Which two key configuration changes are needed on FortiGate to meet the design requirements? (Choose two.)
- A. Configure a higher distance on the static route for the primary tunnel, and a lower distance on the static route for the secondary tunnel.
- B. Enable Dead Peer Detection.
- C. Configure a lower distance on the static route for the primary tunnel, and a higher distance on the static route for the secondary tunnel.
- D. Enable Auto-negotiate and Autokey Keep Alive on the phase 2 configuration of both tunnels.
Answer : BC
Question 3
Refer to the exhibit.
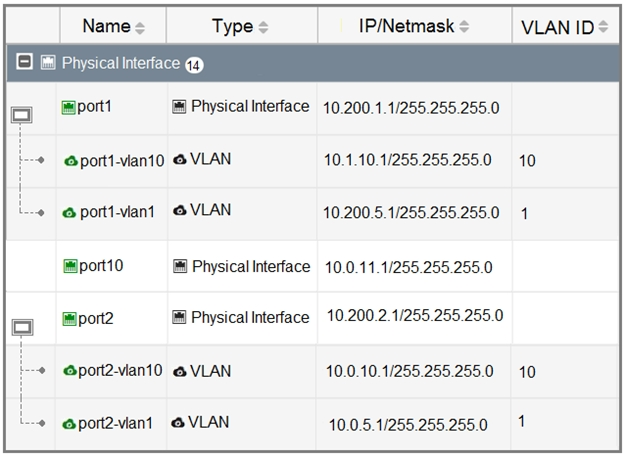
Given the interfaces shown in the exhibit, which two statements are true? (Choose two.)
- A. Traffic between port2 and port2-vlan1 is allowed by default.
- B. port1-vlan10 and port2-vlan10 are part of the same broadcast domain.
- C. port1 is a native VLAN.
- D. port1-vlan1 and port2-vlan1 can be assigned in the same VDOM or to different VDOMs.
Answer : AD
Question 4
Which two statements are correct about SLA targets? (Choose two.)
- A. You can configure only two SLA targets per one Performance SLA.
- B. SLA targets are optional.
- C. SLA targets are required for SD-WAN rules with a Best Quality strategy.
- D. SLA targets are used only when referenced by an SD-WAN rule.
Answer : AC
Question 5
Refer to the web filter raw logs.
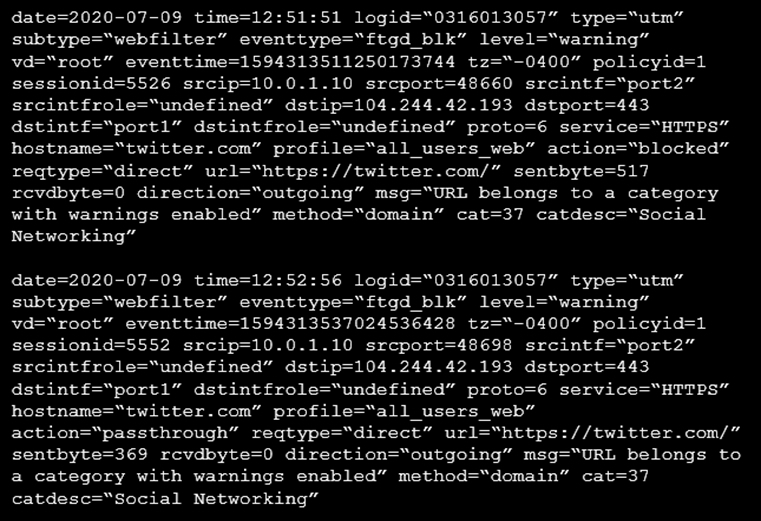
Based on the raw logs shown in the exhibit, which statement is correct?
- A. Access to the social networking web filter category was explicitly blocked to all users.
- B. The action on firewall policy ID 1 is set to warning.
- C. Social networking web filter category is configured with the action set to authenticate.
- D. The name of the firewall policy is all_users_web.
Answer : B
Question 6
Which two statements are true about collector agent standard access mode? (Choose two.)
- A. Standard mode uses Windows convention-NetBios: Domain\Username.
- B. Standard mode security profiles apply to organizational units (OU).
- C. Standard mode security profiles apply to user groups.
- D. Standard access mode supports nested groups.
Answer : AB
Question 7
Refer to the exhibits to view the firewall policy (Exhibit A) and the antivirus profile (Exhibit B).
Exhibit A -
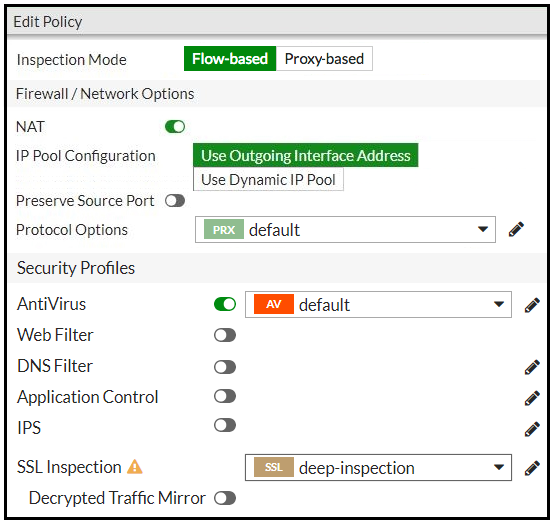
Exhibit B -
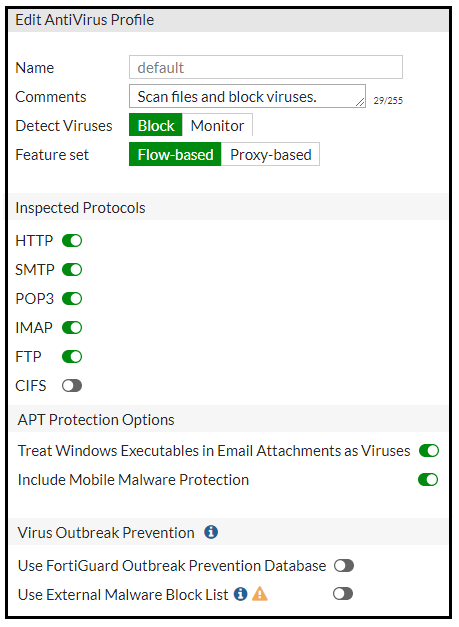
Which statement is correct if a user is unable to receive a block replacement message when downloading an infected file for the first time?
- A. The volume of traffic being inspected is too high for this model of FortiGate.
- B. The intrusion prevention security profile needs to be enabled when using flow-based inspection mode.
- C. The firewall policy performs the full content inspection on the file.
- D. The flow-based inspection is used, which resets the last packet to the user.
Answer : C
Question 8
Refer to the exhibit.
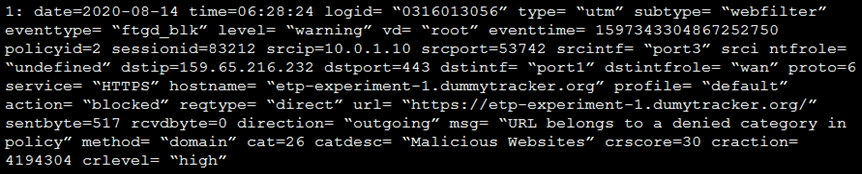
Based on the raw log, which two statements are correct? (Choose two.)
- A. Traffic is blocked because Action is set to DENY in the firewall policy.
- B. Traffic belongs to the root VDOM.
- C. This is a security log.
- D. Log severity is set to error on FortiGate.
Answer : BC
Question 9
Which three methods are used by the collector agent for AD polling? (Choose three.)
- A. FortiGate polling
- B. NetAPI
- C. Novell API
- D. WMI
- E. WinSecLog
Answer : BDE
Reference:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD47732
Question 10
Refer to the exhibit.
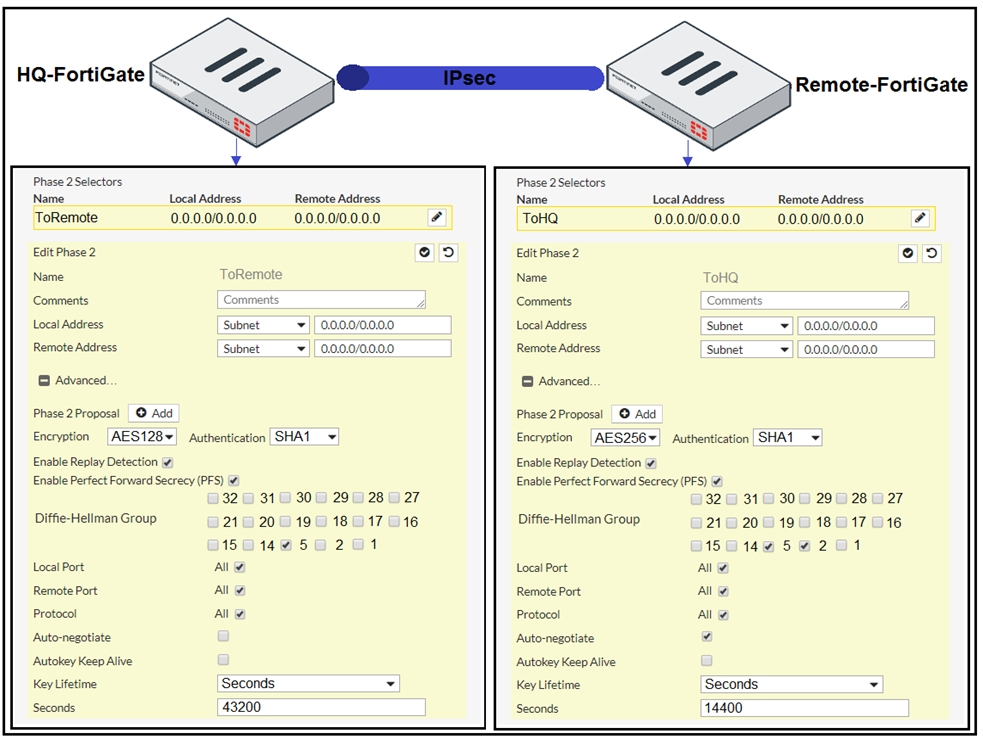
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 status is up, but phase
2 fails to come up.
Based on the phase 2 configuration shown in the exhibit, what configuration change will bring phase 2 up?
- A. On HQ-FortiGate, enable Diffie-Hellman Group 2.
- B. On HQ-FortiGate, enable Auto-negotiate.
- C. On Remote-FortiGate, set Seconds to 43200.
- D. On HQ-FortiGate, set Encryption to AES256.
Answer : A
Reference:
https://docs.fortinet.com/document/fortigate/5.4.0/cookbook/168495
Question 11
If Internet Service is already selected as Source in a firewall policy, which other configuration objects can be added to the Source field of a firewall policy?
- A. IP address
- B. Once Internet Service is selected, no other object can be added
- C. User or User Group
- D. FQDN address
Answer : C
Reference:
https://docs.fortinet.com/document/fortigate/6.2.5/cookbook/179236/using-internet-service-in-policy
Question 12
Consider the topology:
Application on a Windows machine <--{SSL VPN} -->FGT--> Telnet to Linux server.
An administrator is investigating a problem where an application establishes a Telnet session to a Linux server over the SSL VPN through FortiGate and the idle session times out after about 90 minutes. The administrator would like to increase or disable this timeout.
The administrator has already verified that the issue is not caused by the application or Linux server. This issue does not happen when the application establishes a Telnet connection to the Linux server directly on the LAN.
What two changes can the administrator make to resolve the issue without affecting services running through FortiGate? (Choose two.)
- A. Set the maximum session TTL value for the TELNET service object.
- B. Set the session TTL on the SSLVPN policy to maximum, so the idle session timeout will not happen after 90 minutes.
- C. Create a new service object for TELNET and set the maximum session TTL.
- D. Create a new firewall policy and place it above the existing SSLVPN policy for the SSL VPN traffic, and set the new TELNET service object in the policy.
Answer : BC
Question 13
Which Security rating scorecard helps identify configuration weakness and best practice violations in your network?
- A. Fabric Coverage
- B. Automated Response
- C. Security Posture
- D. Optimization
Answer : C
Reference:
https://www.fortinet.com/content/dam/fortinet/assets/support/fortinet-recommended-security-best-practices.pdf
Question 14
What is the primary FortiGate election process when the HA override setting is disabled?
- A. Connected monitored ports > System uptime > Priority > FortiGate Serial number
- B. Connected monitored ports > HA uptime > Priority > FortiGate Serial number
- C. Connected monitored ports > Priority > HA uptime > FortiGate Serial number
- D. Connected monitored ports > Priority > System uptime > FortiGate Serial number
Answer : B
Reference:
http://myitmicroblog.blogspot.com/2018/11/what-should-you-know-about-ha-override.html
Question 15
Refer to the exhibit.
Exhibit A -
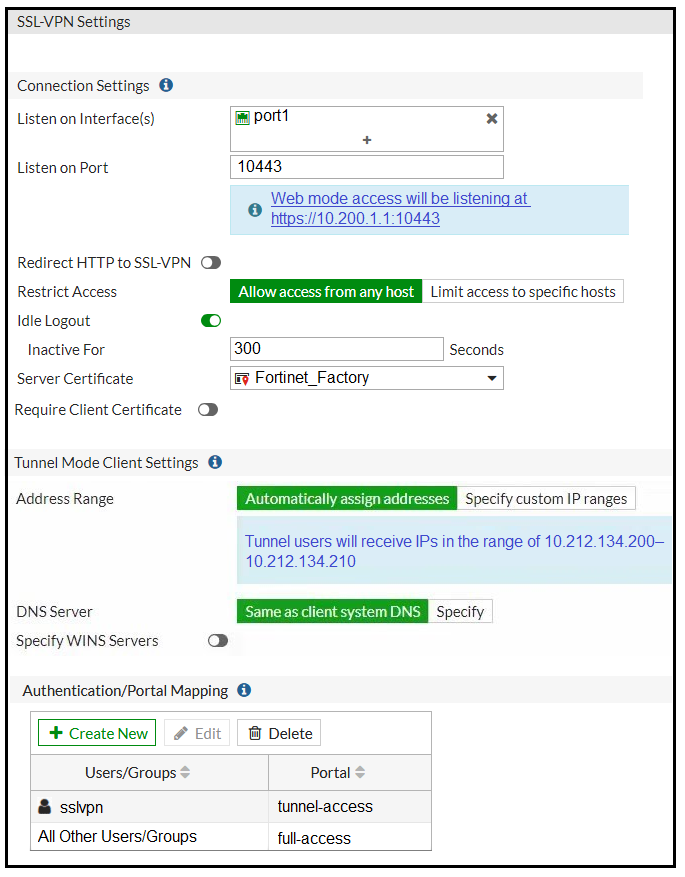
Exhibit B -
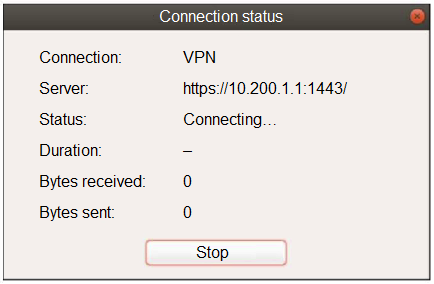
The SSL VPN connection fails when a user attempts to connect to it.
What should the user do to successfully connect to SSL VPN?
- A. Change the SSL VPN port on the client.
- B. Change the Server IP address.
- C. Change the idle-timeout.
- D. Change the SSL VPN portal to the tunnel.
Answer : A
Reference:
https://docs.fortinet.com/document/fortigate/5.4.0/cookbook/150494