Fortinet NSE4 - FortiOS 6.2 v1.0
Question 1
Which two statements correctly describe how FortiGate performs route lookup, when searching for a suitable gateway? (Choose two.)
- A. Lookup is done on the first packet from the session originator
- B. Lookup is done on the last packet sent from the responder
- C. Lookup is done on every packet, regardless of direction
- D. Lookup is done on the first reply packet from the responder
Answer : AD
Question 2
A FortiGate is operating in NAT mode and configured with two virtual LAN (VLAN) subinterfaces added to the physical interface.
In this scenario, which statement about the VLAN IDs is true?
- A. The two VLAN sub interfaces can have the same VLAN ID, only if they have IP addresses in different subnets.
- B. The two VLAN sub interfaces must have different VLAN IDs.
- C. The two VLAN sub interfaces can have the same VLAN ID, only if they belong to different VDOMs.
- D. The two VLAN sub interfaces can have the same VLAN ID, only if they have IP addresses in the same subnet.
Answer : B
Question 3
Refer to the exhibit.
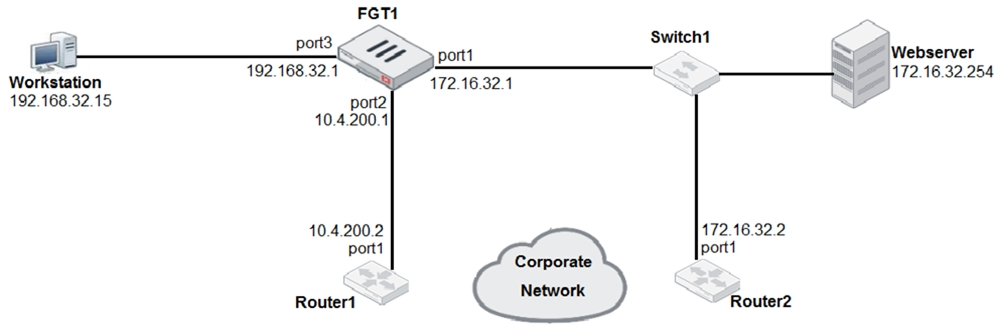
Given the network diagram shown in the exhibit, which route is the best candidate route for FGT1 to route traffic from the workstation to the webserver?
- A. 172.16.32.0/24 is directly connected, port1
- B. 172.16.0.0/16 [50/0] via 10.4.200.2, port2 [5/0]
- C. 10.4.200.0/30 is directly connected, port2
- D. 0.0.0.0/0 [20/0] via 10.4.200.2, port2
Answer : A
Question 4
Which two statements about central NAT are true? (Choose two.)
- A. SNAT using central NAT does not require a central SNAT policy.
- B. Central NAT can be enabled or disabled from the CLI only.
- C. IP pool references must be removed from existing firewall policies, before enabling central NAT.
- D. DNAT using central NAT requires a VIP object as the destination address in a firewall policy.
Answer : BC
Question 5
Which condition must be met in order for a web browser to trust a web server certificate signed by a third-party CA?
- A. The private key of the CA certificate that is signed the browser certificate must be installed on the browser.
- B. The CA certificate that signed the web server certificate must be installed on the browser.
- C. The public key of the web server certificate must be installed on the web browser.
- D. The web-server certificate must be installed on the browser.
Answer : B
Question 6
Refer to the exhibit.
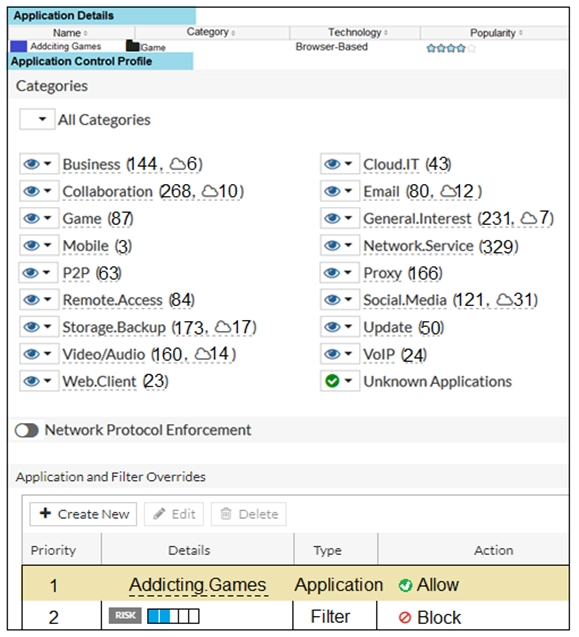
A user located behind the FortiGate device is trying to go to http://www.addictinggames.com (Addicting.Games). The exhibit shows the application detains and application control profile.
Based on this configuration, which statement is true?
- A. Addicting.Games will be blocked, based on the Filter Overrides configuration.
- B. Addicting.Games will be allowed only if the Filter Overrides action is set to Learn.
- C. Addicting.Games will be allowed, based on the Categories configuration.
- D. Addicting.Games will be allowed, based on the Application Overrides configuration.
Answer : D
Question 7
Refer to the exhibit.
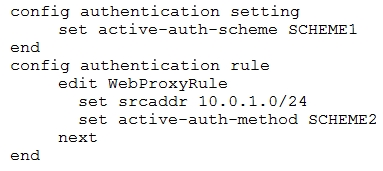
The exhibit shows a FortiGate configuration.
How does FortiGate handle web proxy traffic coming from the IP address 10.2.1.200, that requires authorization?
- A. It always authorizes the traffic without requiring authentication.
- B. It drops the traffic
- C. It authenticates the traffic using the authentication scheme SCHEME2.
- D. It authenticates the traffic using the authentication scheme SCHEME1.
Answer : D
Question 8
Which statement about the IP authentication header (AH) used by IPsec is true?
- A. AH does not support perfect forward secrecy.
- B. AH provides strong data integrity but weak encryption.
- C. AH provides data integrity but no encryption.
- D. AH does not provide any data integrity or encryption.
Answer : C
Question 9
Refer to the exhibits.
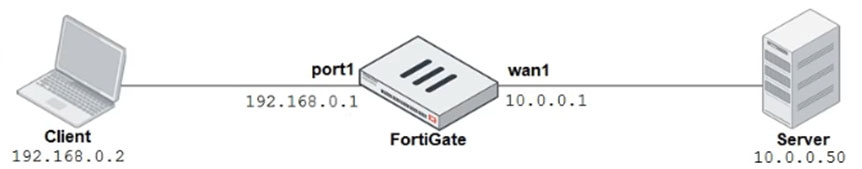
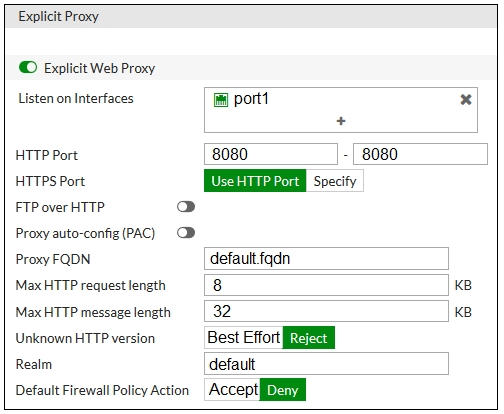
The exhibits show a network diagram and the explicit web proxy configuration.
In the command diagnose sniffer packet, what filter can you use to capture the traffic between the client and the explicit web proxy?
- A. "˜host 192.168.0.2 and port 8080"™
- B. "˜host 10.0.0.50 and port 80"™
- C. "˜host 192.168.0.1 and port 80"™
- D. "˜host 10.0.0.50 and port 8080"™
Answer : A
Question 10
How do you format the FortiGate flash disk?
- A. Execute the CLI command execute formatlogdisk.
- B. Select the format boot device option from the BIOS menu.
- C. Load the hardware test (HQIP) image.
- D. Load a debug FortiOS image.
Answer : B
Question 11
If the Services field is configured in a Virtual IP (VIP), which statement is true when central NAT is used?
- A. The Services field prevents SNAT and DNAT from being combined in the same policy.
- B. The Services field is used when you need to bundle several VIPs into VIP groups.
- C. The Services field removes the requirement to create multiple VIPs for different services.
- D. The Services field prevents multiple sources of traffic from using multiple services to connect to a single computer.
Answer : C
Question 12
Which three types of traffic and attacks can be blocked by a web application firewall (WAF) profile? (Choose three.)
- A. Server information disclosure attacks
- B. Traffic to botnet servers
- C. Credit card data leaks
- D. Traffic to inappropriate web sites
- E. SQL injection attacks
Answer : ACE
Reference:
https://help.fortinet.com/fweb/570/Content/FortiWeb/fortiweb-admin/web_protection.htm
Question 13
Why does FortiGate keep TCP sessions in the session table for several seconds, even after both sides (client and server) have terminated the session?
- A. To generate logs
- B. To remove the NAT operation
- C. To finish any inspection operations
- D. To allow for out-of-order packets that could arrive after the FIN/ACK packets
Answer : D
Question 14
Examine this PAC file configuration.
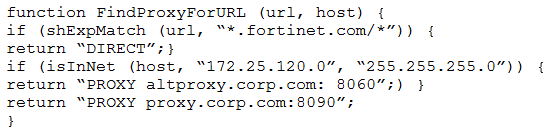
Which of the following statements are true? (Choose two.)
- A. Browsers can be configured to retrieve this PAC file from FortiGate.
- B. Any web request sent to the 172.25.120.0/24 subnet is allowed to bypass the proxy.
- C. All requests not sent to fortinet.com or the 172.25.120.0/24 subnet, have to go through altproxy.corp.com: 8060.
- D. Any web request sent to fortinet.com is allowed to bypass the proxy.
Answer : AD
Question 15
Which two statements correctly describe auto discovery VPN (ADVPN)? (Choose two.)
- A. IPSec tunnels are negotiated dynamically between spokes.
- B. ADVPN is supported only with IKEv2.
- C. It recommends the use of dynamic routing protocols, so that spokes can learn the routes to other spokes.
- D. Every spoke requires a static tunnel to be configured to other spokes, so that phase 1 and phase 2 proposals are defined in advance.
Answer : AC