Fortinet NSE4 - FortiOS 6.0 v1.0
Question 1
Examine the network diagram and the existing FGTI routing table shown in the exhibit, and then answer the following question:
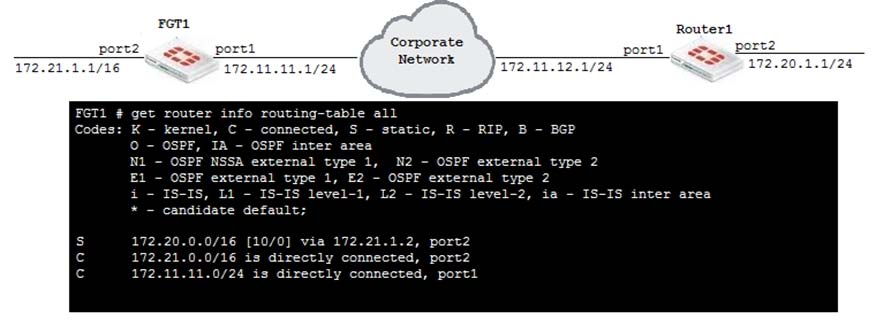
An administrator has added the following static route on FGTI.
Since the change, the new static route is not showing up in the routing table. Given the information provided, which of the following describes the cause of this problem?
- A. The new route"™s destination subnet overlaps an existing route.
- B. The new route"™s Distance value should be higher than 10.
- C. The Gateway IP address is not in the same subnet as port1.
- D. The Priority is 0, which means that this route will remain inactive.
Answer : C
Question 2
Which configuration objects can be selected for the Source field of a firewall policy? (Choose two.)
- A. Firewall service
- B. User or user group
- C. IP Pool
- D. FQDN address
Answer : BC
Question 3
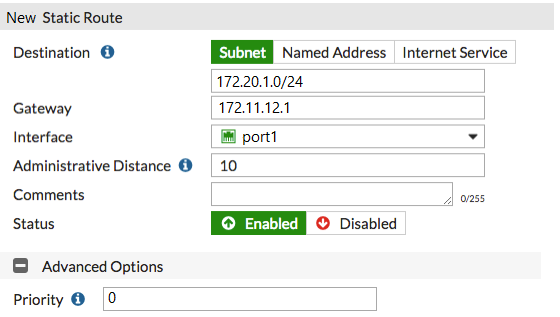
View the exhibit.
Which users and user groups are allowed access to the network through captive portal?
- A. Users and groups defined in the firewall policy.
- B. Only individual users "" not groups "" defined in the captive portal configuration
- C. Groups defined in the captive portal configuration
- D. All users
Answer : C
Question 4
NGFW mode allows policy-based configuration for most inspection rules. Which security profile"™s configuration does not change when you enable policy-based inspection?
- A. Web filtering
- B. Antivirus
- C. Web proxy
- D. Application control
Answer : C
Question 5
During the digital verification process, comparing the original and fresh hash results satisfies which security requirement?
- A. Authentication.
- B. Data integrity.
- C. Non-repudiation.
- D. Signature verification.
Answer : D
Question 6
An administration wants to throttle the total volume of SMTP sessions to their email server. Which of the following DoS sensors can be used to achieve this?
- A. tcp_port_scan
- B. ip_dst_session
- C. udp_flood
- D. ip_src_session
Answer : A
Question 7
Why must you use aggressive mode when a local FortiGate IPSec gateway hosts multiple dialup tunnels?
- A. In aggressive mode, the remote peers are able to provide their peer IDs in the first message.
- B. FortiGate is able to handle NATed connections only in aggressive mode.
- C. FortiClient only supports aggressive mode.
- D. Main mode does not support XAuth for user authentication.
Answer : A
Question 8
Examine this output from a debug flow:
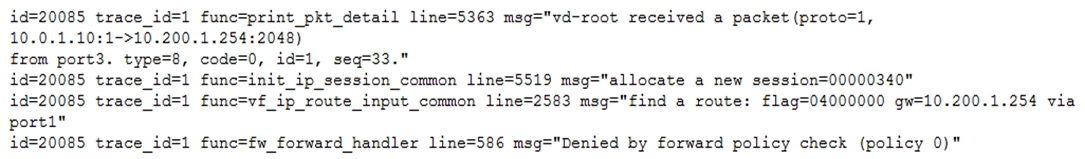
Why did the FortiGate drop the packet?
- A. The next-hop IP address is unreachable.
- B. It failed the RPF check.
- C. It matched an explicitly configured firewall policy with the action DENY.
- D. It matched the default implicit firewall policy.
Answer : D
Question 9
View the exhibit:
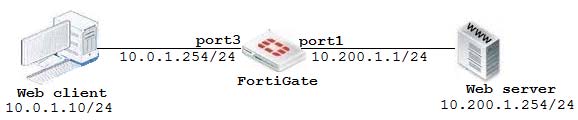
The client cannot connect to the HTTP web server. The administrator ran the FortiGate built-in sniffer and got the following output:
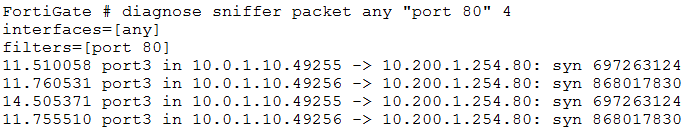
What should be done next to troubleshoot the problem?
- A. Run a sniffer in the web server.
- B. Execute another sniffer in the FortiGate, this time with the filter "host 10.0.1.10".
- C. Capture the traffic using an external sniffer connected to port1.
- D. Execute a debug flow.
Answer : C
Question 10
Which of the following statements about policy-based IPsec tunnels are true? (Choose two.)
- A. They can be configured in both NAT/Route and transparent operation modes.
- B. They support L2TP-over-IPsec.
- C. They require two firewall policies: one for each directions of traffic flow.
- D. They support GRE-over-IPsec.
Answer : AB
Question 11
An employee connects to the https://example.com on the Internet using a web browser. The web server"™s certificate was signed by a private internal CA. The
FortiGate that is inspecting this traffic is configured for full SSL inspection.
This exhibit shows the configuration settings for the SSL/SSH inspection profile that is applied to the policy that is invoked in this instance. All other settings are set to defaults. No certificates have been imported into FortiGate. View the exhibit and answer the question that follows.
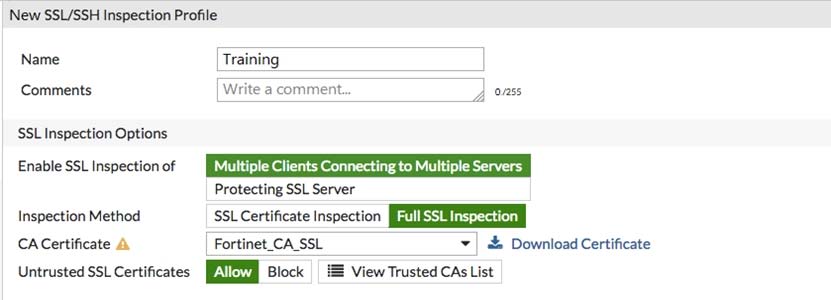
Which certificate is presented to the employee"™s web browser?
- A. The web server"™s certificate.
- B. The user"™s personal certificate signed by a private internal CA.
- C. A certificate signed by Fortinet_CA_SSL.
- D. A certificate signed by Fortinet_CA_Untrusted.
Answer : A
Question 12
Examine this FortiGate configuration:
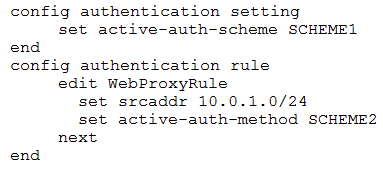
How does the FortiGate handle web proxy traffic coming from the IP address 10.2.1.200 that requires authorization?
- A. It always authorizes the traffic without requiring authentication.
- B. It drops the traffic.
- C. It authenticates the traffic using the authentication scheme SCHEME2.
- D. It authenticates the traffic using the authentication scheme SCHEME1.
Answer : C
Question 13
Examine the exhibit, which shows the output of a web filtering real time debug.
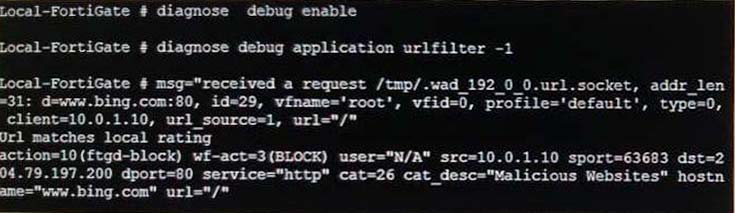
Why is the site www.bing.com being blocked?
- A. The web site www.bing.com is categorized by FortiGuard as Malicious Websites.
- B. The user has not authenticated with the FortiGate yet.
- C. The web server IP address 204.79.197.200 is categorized by FortiGuard as Malicious Websites.
- D. The rating for the web site www.bing.com has been locally overridden to a category that is being blocked.
Answer : D
Question 14
Which of the following statements are best practices for troubleshooting FSSO? (Choose two.)
- A. Include the group of guest users in a policy.
- B. Extend timeout timers.
- C. Guarantee at least 34 Kbps bandwidth between FortiGate and domain controllers.
- D. Ensure all firewalls allow the FSSO required ports.
Answer : AD
Question 15
When override is enabled, which of the following shows the process and selection criteria that are used to elect the primary FortiGate in an HA cluster?
- A. Connected monitored ports > HA uptime > priority > serial number
- B. Priority > Connected monitored ports > HA uptime > serial number
- C. Connected monitored ports > priority > HA uptime > serial number
- D. HA uptime > priority > Connected monitored ports > serial number
Answer : C