Fortinet Network Security Expert - FortiOS 5.4 v1.0
Question 1
Which statements about application control are true? (Choose two.)
- A. Enabling application control profile in a security profile enables application control for all the traffic flowing through the FortiGate.
- B. It cannot take an action on unknown applications.
- C. It can inspect encrypted traffic.
- D. It can identify traffic from known applications, even when they are using non-standard TCP/UDP ports.
Answer : CD
Question 2
View the exhibit.
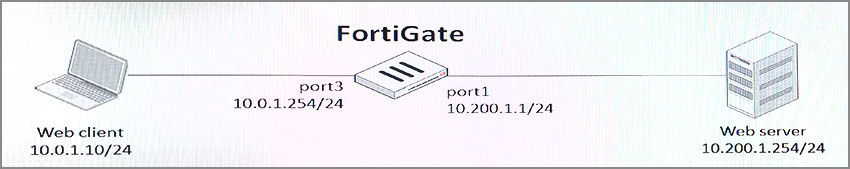
The client cannot connect to the HTTP web server. The administrator run the FortiGate built-in sniffer and got the following output:
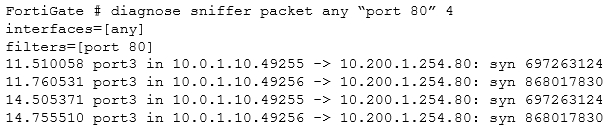
What should be done next to troubleshoot the problem?
- A. Execute another sniffer in the FortiGate, this time with the filter ג€host 10.0.1.10ג€.
- B. Run a sniffer in the web server.
- C. Capture the traffic using an external sniffer connected to port1.
- D. Execute a debug flow.
Answer : B
Question 3
Which of the following statements about NTLM authentication are correct? (Choose two.)
- A. It is useful when users log in to DCs that are not monitored by a collector agent.
- B. It takes over as the primary authentication method when configured alongside FSSO.
- C. Multi-domain environments require DC agents on every domain controller.
- D. NTLM-enabled web browsers are required.
Answer : AD
Question 4
What FortiGate feature can be used to allow IPv6 clients to connect to IPv4 servers?
- A. IPv6-over-IPv4 IPsec
- B. NAT64
- C. IPv4-over-IPv6 IPsec
- D. NAT66
Answer : B
Reference:
http://help.fortinet.com/fos50hlp/52data/Content/FortiOS/fortigate-firewall-52/Concepts/NAT%2064%20and%20NAT46.htm
Question 5
Which statements best describe auto discovery VPN (ADVPN). (Choose two.)
- A. It requires the use of dynamic routing protocols so that spokes can learn the routes to other spokes.
- B. ADVPN is only supported with IKEv2.
- C. Tunnels are negotiated dynamically between spokes.
- D. Every spoke requires a static tunnel to be configured to other spokes so that phase 1 and phase 2 proposals are defined in advance.
Answer : AC
Question 6
View the exhibit.
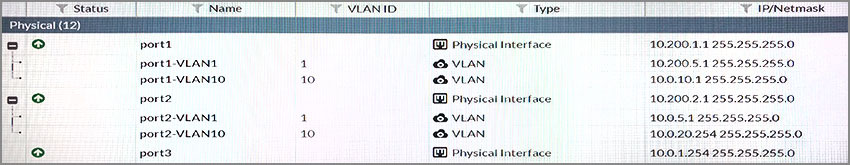
Which statements about the exhibit are true? (Choose two.)
- A. port1-VLAN10 and port2-VLAN10 can be assigned to different VDOMs.
- B. port1-VLAN1 is the native VLAN for the port1 physical interface.
- C. Traffic between port1-VLAN1 and port2-VLAN1 is allowed by default.
- D. Broadcast traffic received in port1-VLAN10 will not be forwarded to port2-VLAN10.
Answer : AD
Question 7
Which statement about the firewall policy authentication timeout is true?
- A. It is a hard timeout. The FortiGate removes the temporary policy for a userג€™s source IP address after this times expires.
- B. It is a hard timeout. The FortiGate removes the temporary policy for a userג€™s source MAC address after this times expires.
- C. It is an idle timeout. The FortiGate considers a user to be idle if it does not see any packets coming from the userג€™s source MAC address.
- D. It is an idle timeout. The FortiGate considers a user to be idle if it does not see any packets coming from the userג€™s source IP.
Answer : D
Question 8
Which of the following settings and protocols can be used to provide secure and restrictive administrative access to FortiGate? (Choose three.)
- A. Trusted host
- B. HTTPS
- C. Trusted authentication
- D. SSH
- E. FortiTelemetry
Answer : ABD
Question 9
If traffic matches a DLP filter with the action set to Quarantine IP Address, what action does the FortiGate take?
- A. It blocks all future traffic for that IP address for a configured interval.
- B. It archives the data for that IP address.
- C. It provides a DLP block replacement page with a link to download the file.
- D. It notifies the administrator by sending an email.
Answer : A
Question 10
How can a browser trust a web-server certificate signed by a third party CA?
- A. The browser must have the CA certificate that signed the web-server certificate installed.
- B. The browser must have the web-server certificate installed.
- C. The browser must have the private key of CA certificate that signed the web-browser certificate installed.
- D. The browser must have the public key of the web-server certificate installed.
Answer : A
Question 11
How does FortiGate verify the login credentials of a remote LDAP user?
- A. FortiGate sends the user entered credentials to the LDAP server for authentication.
- B. FortiGate re-generates the algorithm based on the login credentials and compares it against the algorithm stored on the LDAP server.
- C. FortiGate queries its own database for credentials.
- D. FortiGate queries the LDAP server for credentials.
Answer : A
Question 12
An administrator has enabled proxy-based antivirus scanning and configured the following settings:

Which statement about the above configuration is true?
- A. Files bigger than 10 MB are not scanned for viruses and will be blocked.
- B. FortiGate scans only the first 10 MB of any file.
- C. Files bigger than 10 MB are sent to the heuristics engine for scanning.
- D. FortiGate scans the files in chunks of 10 MB.
Answer : A
Question 13
Examine this output from the diagnose sys top command:

Which statements about the output are true? (Choose two.)
- A. sshd is the process consuming most memory
- B. sshd is the process consuming most CPU
- C. All the processes listed are in sleeping state
- D. The sshd process is using 123 pages of memory
Answer : BC
Question 14
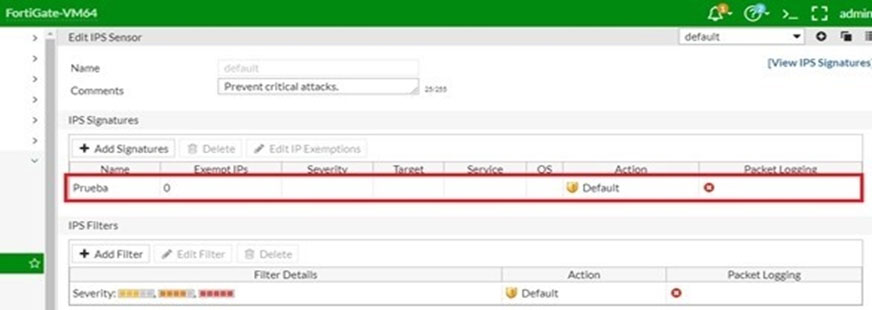
An administrator has created a custom IPS signature. Where does the custom IPS signature have to be applied?
- A. In an IPS sensor
- B. In an interface.
- C. In a DoS policy.
- D. In an application control profile.
Answer : A
Explanation:
I create a custom signature then I try to add and appear only in IPS sensor.
Question 15
An administrator wants to configure a FortiGate as a DNS server. The FortiGate must use its DNS database first, and then relay all irresolvable queries to an external DNS server. Which of the following DNS method must you use?
- A. Non-recursive
- B. Recursive
- C. Forward to primary and secondary DNS
- D. Forward to system DNS
Answer : B