Fortinet Network Security Expert 4 v12.0
Question 1
In which order are firewall policies processed on a FortiGate unit?
- A. From top to bottom, according with their sequence number.
- B. From top to bottom, according with their policy ID number.
- C. Based on best match.
- D. Based on the priority value.
Answer : A
Question 2
In an IPSec gateway-to-gateway configuration, two FortiGate units create a VPN tunnel between two separate private networks. Which of the following configuration steps must be performed on both FortiGate units to support this configuration?
- A. Create firewall policies to control traffic between the IP source and destination address.
- B. Configure the appropriate user groups on the FortiGate units to allow users access to the IPSec VPN connection.
- C. Set the operating mode of the FortiGate unit to IPSec VPN mode.
- D. Define the Phase 2 parameters that the FortiGate unit needs to create a VPN tunnel with the remote peer.
- E. Define the Phase 1 parameters that the FortiGate unit needs to authenticate the remote peers.
Answer : A,D,E
Question 3
The exhibit shows two static routes to the same destinations subnet 172.20.168.0/24.
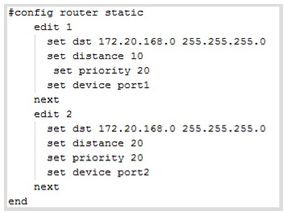
Which of the following statements correctly describes this static routing configuration?
(choose two)
- A. Both routes will show up in the routing table.
- B. The FortiGate unit will evenly share the traffic to 172.20.168.0/24 between routes.
- C. Only one route will show up in the routing table.
- D. The FortiGate will route the traffic to 172.20.168.0/24 only through one route.
Answer : CD
Question 4
Review the IKE debug output for IPsec shown in the exhibit below.
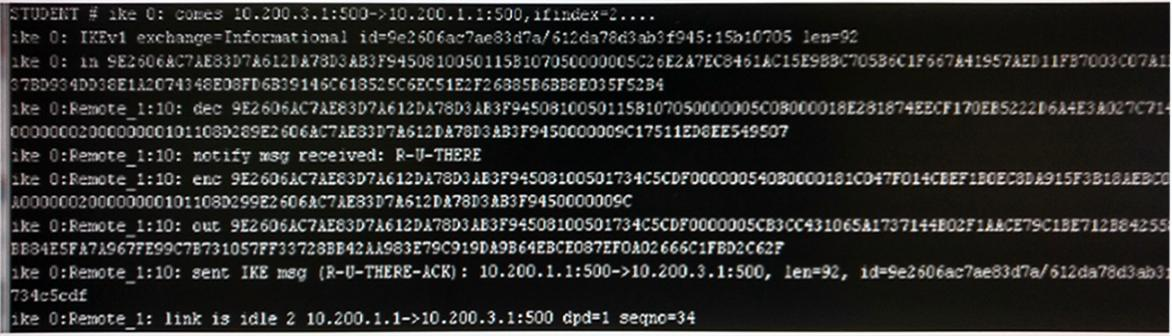
Which statements is correct regarding this output?
- A. The output is a phase 1 negotiation.
- B. The output is a phase 2 negotiation.
- C. The output captures the dead peer detection messages.
- D. The output captures the dead gateway detection packets.
Answer : C
Question 5
Files that are larger than the oversized limit are subjected to which Antivirus check?
- A. Grayware
- B. Virus
- C. Sandbox
- D. Heuristic
Answer : C
Question 6
Which statements correctly describe transparent mode operation? (Choose three.)
- A. The FortiGate acts as transparent bridge and forwards traffic at Layer-2.
- B. Ethernet packets are forwarded based on destination MAC addresses, NOT IP addresses.
- C. The transparent FortiGate is clearly visible to network hosts in an IP trace route.
- D. Permits inline traffic inspection and firewalling without changing the IP scheme of the network.
- E. All interfaces of the transparent mode FortiGate device most be on different IP subnets.
Answer : ABD
Question 7
Which statements are true regarding local user authentication? (Choose two.)
- A. Two-factor authentication can be enabled on a per user basis.
- B. Local users are for administration accounts only and cannot be used to authenticate network users.
- C. Administrators can create the user accounts in a remote server and store the user passwords locally in the FortiGate.
- D. Both the usernames and passwords can be stored locally on the FortiGate.
Answer : A,D
Question 8
Which protocols can you use for secure administrative access to a FortiGate? (Choose two)
- A. SSH
- B. Telnet
- C. NTLM
- D. HTTPS
Answer : A,D
Question 9
What is not true of configuring disclaimers on the FortiGate?
- A. Disclaimers can be used in conjunction with captive portal.
- B. Disclaimers appear before users authenticate.
- C. Disclaimers can be bypassed through security exemption lists.
- D. Disclaimers must be accepted in order to continue to the authentication login or originally intended destination.
Answer : C
Question 10
Which of the following statements are correct regarding FortiGate virtual domains
(VDOMs)? (Choose two)
- A. VDOMs divide a single FortiGate unit into two or more independent firewall.
- B. A management VDOM handles SNMP. logging, alert email and FortiGuard updates.
- C. Each VDOM can run different firmware versions.
- D. Administrative users with a 'super_admin' profile can administrate only one VDOM.
Answer : AB
Question 11
Where are most of the security events logged?
- A. Security log
- B. Forward Traffic log
- C. Event log
- D. Alert log
- E. Alert Monitoring Console
Answer : C
Question 12
What is the maximum number of FortiAnalyzer/FortiManager devices a FortiGate unit can be configured to send logs to?
- A. 1
- B. 2
- C. 3
- D. 4
Answer : C
Question 13
The exhibit shows the Disconnect Cluster Member command in a FortiGate unit that is part of a HA cluster with two HA members.
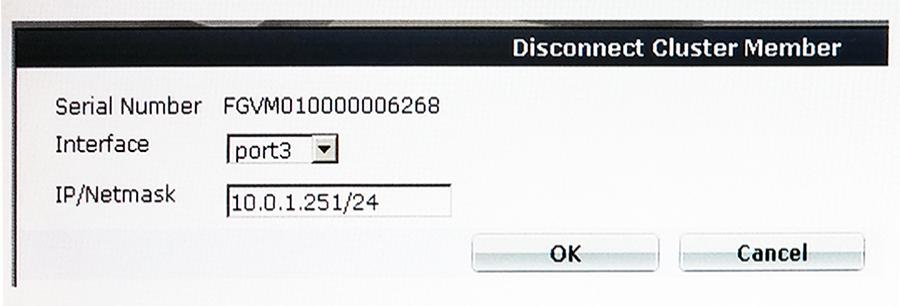
What is the effect of the Disconnect Cluster Member command as given in the exhibit.
(Choose two.)
- A. Port3 is configured with an IP address management access.
- B. The firewall rules are purged on the disconnected unit.
- C. The HA mode changes to standalone.
- D. The system hostname is set to the unit serial number.
Answer : AC
Question 14
Which statements are correct regarding an IPv6 over IPv4 IPsec configuration? (Choose two.)
- A. The source quick mode selector must be an IPv4 address.
- B. The destination quick mode selector must be an IPv6 address.
- C. The Local Gateway IP must be an IPv4 address.
- D. The remote gateway IP must be an IPv6 address.
Answer : BC
Question 15
Which IPsec configuration mode can be used for implementing GRE-over-IPsec VPNs?
- A. Policy-based only.
- B. Route-based only.
- C. Either policy-based or route-based VPN.
- D. GRE-based only.
Answer : B