CompTIA Network+ Certification v13.0
Question 1
An F-connector is used on which of the following types of cabling?
- A. CAT3
- B. Single mode fiber
- C. CAT5
- D. RG6
Answer : D
Explanation:
An F connector is a coaxial RF connector commonly used for terrestrial television, cable television and universally forsatellite television and cable modems, usually with RG-6/U cable or, in older installations, with RG-59/U cable.
Question 2
Which of the following network topologies has a central, single point of failure?
- A. Ring
- B. Star
- C. Hybrid
- D. Mesh
Answer : B
Explanation:
A Star network is the most common network in use today. Ethernet networks with computers connected to a switch (or a less commonly a hub) form a star network.
The switch forms the central component of the star. All network devices connect to the switch. A network switch has a MAC address table which it populates with the MAC address of every device connected to the switch. When the switch receives data on one of its ports from a computer, it looks in the MAC address table to discover which port the destination computer is connected to. The switch then unicasts the data out through the port that the destination computer is connected to.
The switch that forms thecentral component of a star network is a single point of failure. If the switch fails, no computers will be able to communicate with each other.
Question 3
Which of the following network devices use ACLs to prevent unauthorized access into company systems?
- A. IDS
- B. Firewall
- C. Content filter
- D. Load balancer
Answer : B
Explanation:
A firewall is a system designed to prevent unauthorized access to or from a private network. Firewalls arefrequently used to prevent unauthorized Internet users from accessing privatenetworks connected to the Internet, especially intranets. Firewalls use
ACLs (access control lists) to determine which traffic is allowed through the firewall. All traffic entering or leaving the intranet passes through the firewall, which examines each message and blocks or allows the message depending on rules specified in the ACL. The rules in the ACL specify which combinations of source IP address, destination address in
IP port numbers are allowed.
Question 4
Which of the following network elements enables unified communication devices to connect to and traverse traffic onto the PSTN?
- A. Access switch
- B. UC gateway
- C. UC server
- D. Edge router
Answer : B
Explanation:
People use many methods of communication nowadays such as voice, email, video and instant messaging. People also use many different devices to communicate such as smart phones, PDAs, computers etc.Unified Communications (UC) enables people using different modes of communication, different media, and different devices to communicate with anyone, anywhere, at any time.
Many communication methods use digital signals. To send a digital signal over the analog
PSTN, you need a gateway (in this case a UC Gateway) to convert the digital signals into an analog format that can be sent over the PSTN.
Question 5
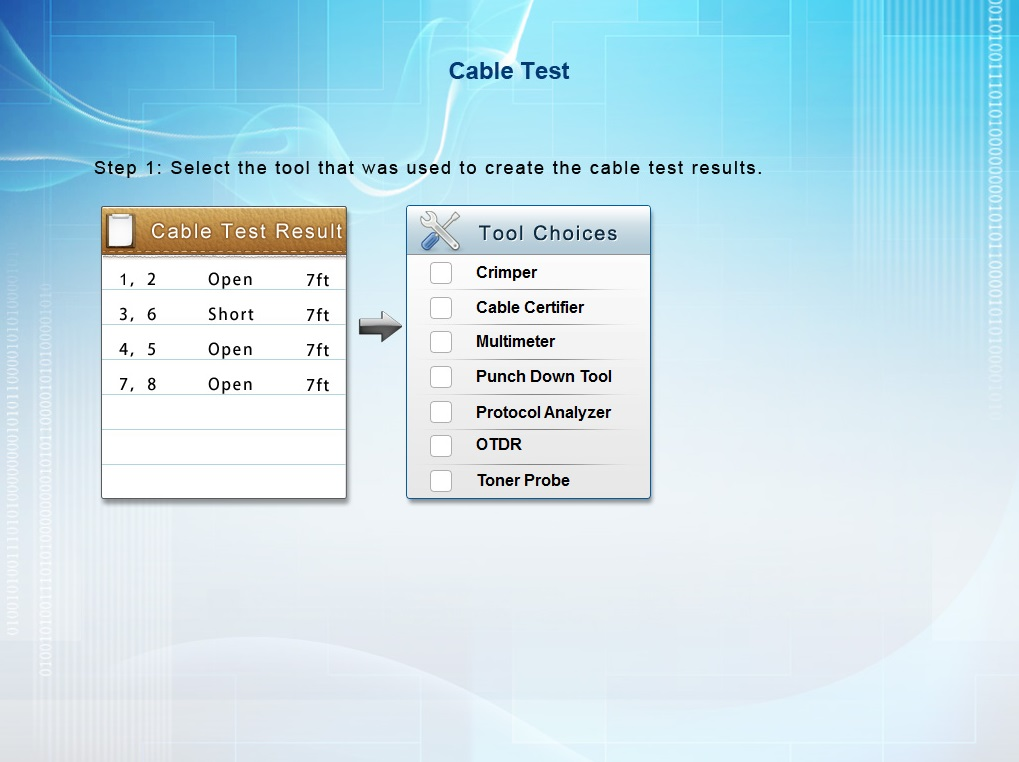
You have been tasked with testing a CAT5e cable. A summary of the test results can be found on the screen.
Step 1: Select the tool that was used to create the cable test results.
Step 2: Interpret the test results and select the option that explains the results. After you are done with your analysis, click the 'Submit Cable Test Analysis' button.
Answer : B
Explanation:
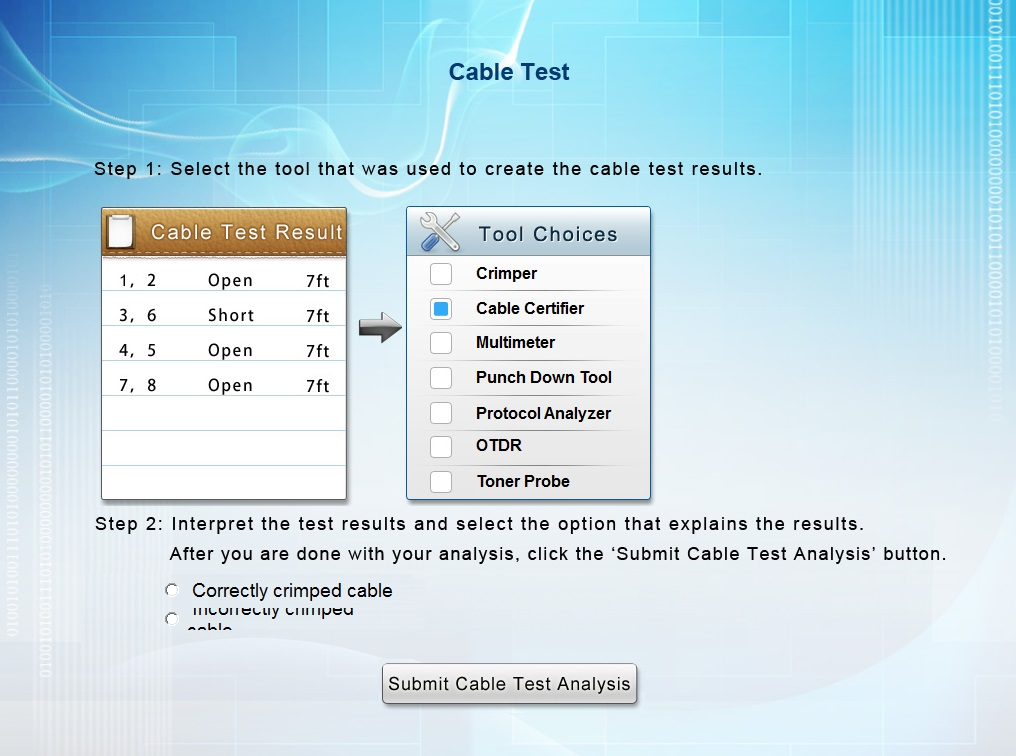
A Cable Certifier provides Pass or Fail information in accordance with industry standards but can also show detailed information when a Fail occurs. This includesshorts, the wire pairs involved and the distance to the short. When a short is identified, at the full length of the cable it means the cable has not been crimped correctly.
Question 6
A company has a new offering to provide access to their product from a central location rather than clients internally hosting the product on the client network. The product contains sensitive corporate information that should not be accessible from one client to another.
This is an example of which of the following?
- A. Public SaaS
- B. Private SaaS
- C. Hybrid IaaS
- D. Community IaaS
Answer : B
Explanation:
SaaS stands for Software as a Service. This is a cloud model whereby a service provider provides asoftware service and makes the service available to customers over the Internet.
Examples of Saas include Microsoft Office 365, Microsoft Exchange Online, Microsoft Lync
Online etc.
Advantages of Saas include ease of administration: no need to install andconfigure local servers, no need to configure backups, no need to keep the software patched, no need to worry about system recovery, lower costs: saving on the purchase of server hardware and software; with SaaS, you lease the service paying either monthlyor yearly and compatibility by ensuring that all users are using the same version of software.
There are two types of SaaS: public and private. With public Saas, multiple customers
(usually companies) share the same servers running the software. Withprivate Saas, the servers running the software are dedicated to a single customer which provides the isolation and extra security required when dealing with sensitive information.
Question 7
Which of the following provides accounting, authorization, and authentication via a centralized privileged database, as well as, challenge/response and password encryption?
- A. Multifactor authentication
- B. ISAKMP
- C. TACACS+
- D. Network access control
Answer : C
Explanation:
TACACS+ (Terminal Access Controller Access-Control System Plus) is aprotocol that handles authentication, authorization, and accounting (AAA) services. Similar to RADIUS,
TACACS+ is a centralized authentication solution used to provide access to network resources. TACACS+ separates the authentication, authorization, and accounting services enabling you to host each service on a separate server if required.
Question 8
A technician is helping a SOHO determine where to install the server. Which of the following should be considered FIRST?
- A. Compatibility requirements
- B. Environment limitations
- C. Cable length
- D. Equipment limitations
Answer : B
Explanation:
SOHO stands for Small Office / Home Office. A SOHO network istypically a small network.
Being a small network, it is unlikely that it will have a datacenter or even a dedicated server room. Any servers installed in the network will still have the same environmental requirements as servers in a large network. The servers should be in a secure isolated area if required. The servers also need to be kept cool and dry. Therefore, the first consideration in a SOHO office is Environment limitations: where the servers and other network hardware will be located.
Question 9
Which of the following protocols uses label-switching routers and label-edge routers to forward traffic?
- A. BGP
- B. OSPF
- C. IS-IS
- D. MPLS
Answer : D
Explanation:
In an MPLS network, data packets are assigned labels. Packet-forwarding decisions are made solely on the contents of this label, without the need to examine the packet itself.
MPLS works by prefixing packets with an MPLS header, containing one or more labels.
An MPLS router that performs routing based only on the label is called a label switch router
(LSR) or transit router. This is a type of router located in the middle of a MPLS network. It is responsible for switching the labels used to route packets. When an LSR receives a packet, it uses the label included in the packet header as an index to determine the next hop on the label-switched path (LSP) and a corresponding label for the packet from a lookup table. The old label is then removed from the header and replaced with the new label before the packet is routed forward.
A label edge router (LER) is a router that operates at the edge of an MPLS network and acts as the entry and exit points for the network. LERs respectively, add an MPLS label onto an incoming packet and remove it off the outgoing packet.
When forwarding IP datagrams into the MPLS domain, an LER uses routing information to determine appropriate labels to be affixed, labels the packet accordingly, and then forwards the labelled packets into the MPLS domain. Likewise, upon receiving a labelled packet which is destined to exit the MPLS domain, the LER strips off the label and forwards the resulting IP packet using normal IP forwarding rules.
Topic 2, Network operations -
Question 10
A company has had several virus infections over the past few months. The infections were caused by vulnerabilities in the application versions that are being used. Which of the following should an administrator implement to prevent future outbreaks?
- A. Host-based intrusion detection systems
- B. Acceptable use policies
- C. Incident response team
- D. Patch management
Answer : D
Explanation:
As vulnerabilities are discovered, the vendors ofthe operating systems or applications often respond by releasing a patch. A patch is designed to correct a known bug or fix a known vulnerability, such as in this case to be vulnerable to virus infections, in a piece of software.
A patch differs from an update, which, in addition to fixing a known bug or vulnerability, adds one or more features to the software being updated.
Question 11
A network technician must create a wireless link between two buildings in an office park utilizing the 802.11ac standard. The antenna chosen must have a small physical footprint and minimal weight as it will be mounted on the outside of the building. Which of the following antenna types is BEST suited for this solution?
- A. Yagi
- B. Omni-directional
- C. Parabolic
- D. Patch
Answer : D
Explanation:
A patch antenna is a type of radio antenna with a low profile, which can be mounted on a flat surface. A patch antenna is typically mounted to a wall or a mast and provides coverage in a limited angle pattern.
Question 12
After a recent breach, the security technician decides the company needs to analyze and aggregate its security logs. Which of the following systems should be used?
- A. Event log
- B. Syslog
- C. SIEM
- D. SNMP
Answer : C
Explanation:
Using a Security information and event management (SIEM) product, the security logs can be analyzed andaggregated.
SIEM is a term for software products and services combining security information management (SIM) and security event management (SEM). SIEM technology provides real-time analysis of security alerts generated by network hardware and applications. SIEM is sold as software, appliances or managed services, and are also used to log security data and generate reports for compliance purposes.
SIEM capabilities include Data aggregation; Log management aggregates data from many sources, including network, security, servers, databases, applications, providing the ability to consolidate monitored data to help avoid missing crucial events.
Question 13
The RAID controller on a server failed and was replaced with a different brand. Which of the following will be needed after the server has been rebuilt and joined to the domain?
- A. Vendor documentation
- B. Recent backups
- C. Physical IP address
- D. Physical network diagram
Answer : B
Explanation:
If the RAID controller fails and is replaced with a RAID controller with a different brand the
RAID will break. We would have to rebuild a new RAID disk, access and restore the most recent backup to the new RAID disk.
Note: RAID controlleris a hardware device or software program used to manage hard disk drives (HDDs) or solid-state drives (SSDs) in a computer or storage array so they work as a logical unit. In hardware-based RAID, a physical controller is used to manage the RAID array.
Question 14
Multiple students within a networking lab are required to simultaneously access a single switch remotely. The administrator checks and confirms that the switch can be accessed using the console, but currently only one student can log in at a time. Which of the following should be done to correct this issue?
- A. Increase installed memory and install a larger flash module.
- B. Increase the number of VLANs configured on the switch.
- C. Decrease the number of VLANs configured on the switch.
- D. Increase the number of virtual terminals available.
Answer : D
Explanation:
You can set a limit of how many virtual terminals that can simultaneously be connected to a switch. Here the limit is set to one, and we should increase it.
For a Cisco network device:
You can use virtual terminal lines to connect to your Cisco NX-OS device, for example a switch. Secure Shell (SSH) and Telnet create virtual terminal sessions. You can configure an inactive session timeout and a maximum sessions limit for virtual terminals. session-limit sessions
Example:
switch(config-line)# session-limit 10
Configures the maximum number of virtual sessions for the Cisco NX-OS device. The range is from 1 to 64.
Question 15
A technician is setting up a new network and wants to create redundant paths through the network. Which of the following should be implemented to prevent performance degradation?
- A. Port mirroring
- B. Spanning tree
- C. ARP inspection
- D. VLAN
Answer : B
Explanation:
The Spanning Tree Protocol (STP) is a network protocol that ensures a loop-free topology for any bridged Ethernet local area network. The basic function of STP is to prevent bridge loops and the broadcast radiation that results from them. Spanning tree also allows a network design to include spare (redundant) links to provide automatic backup paths if an active link fails, without the danger of bridge loops, or the need for manual enabling/disabling of these backup links.