IBM Information Management Data Security & Privacy Sales Mastery v1 v6.0
Question 1
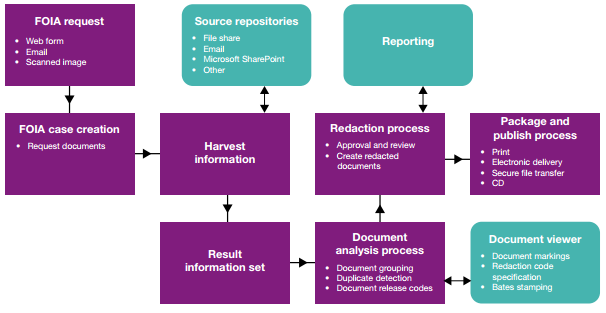
Your customer deals with a lot of FOIA (Freedom of Information Act) requests and need to keep some information confidential. Which solution should you immediately recommend to him/her?
- A. Guardium Data Activity Monitor
- B. Optim Data Masking
- C. Guardium Data Redaction
- D. Guardium Encryption Expert
Answer : C
Explanation: * InfoSphere Guardium Data Redaction is a product aimed at achieving a balance between openness and privacy. Often, the same regulations require organizations to share their documents with regulators, business partners, or customers, and at the same time to protect sensitive information which may be buried in these documents
*
Question 2
Which of the following regulations does Guardium NOT help address?
- A. PCI-DSS
- B. SOX
- C. Volker Rule
- D. HIPAA
Answer : C
Explanation: InfoSphere Guardium is used by over 400 organizations world-wide to automate the controls associated with a variety of mandates including:
Financial regulations, such as the Sarbanes-Oxley Act (SOX), FIEL and C-SOX
Data Privacy regulations including the EU Data Privacy Directive, PIPEDA, Garante della
Privacy and the German Federal Data Protection Act
PCI DSS (Payment Card Industry Data Security Standard), providing support for capabilities specified in sections 2,3,6,7, 8,10, 11 and 12
HIPAA -
Question 3
Which of the following is qualifying question you should ask the first time you speak to a new prospect/client about IBM's Infosphere Privacy and Security Solutions?
- A. Have you worked with S-TAPs before?
- B. Do you know where does your sensitive or privacy data reside across and outside the enterprise? If so, where?
- C. How fast are your Production databases growing?
- D. What has your organization done to speed application development?
Answer : B
Explanation: * IBM InfoSphere Data Privacy and Security for Data Warehousing enables organizations to reduce risk and cost associated with protecting sensitive data. The solution provides a complete set of capabilities to mask or redact data, monitor and audit data activity and maintain sensitive data definitions within select data warehousing environments.
Question 4
An S-TAP is:
- A. A hardware probe
- B. A software probe installed on the database server.
- C. A software probe sitting on the network
- D. An appliance.
Answer : B
Explanation: You must install InfoSphere Guardium S-TAP on each database server that you plan to use for capturing or replaying workloads. InfoSphere Guardium S-TAP is a lightweight software agent that monitors database traffic and forwards information about that traffic to an InfoSphere Guardium appliance.
Question 5
Which is a benefit of using Guardium DAM instead of Database Logging?
- A. Guardium DAM is less expensive that Database logging
- B. Turning Database Logging on will cause a performance hit to the Database
- C. Database Logging is used for providing results in real time
- D. There is no benefit
Answer : B
Explanation: IBM InfoSphere Guardium Data Activity Monitor (DAM) prevents unauthorized data access, alerts on changes or leaks to help ensure data integrity, automates compliance controls and protects against internal and external threats.
Continuous monitoring and real time security policies protect data across the enterprise without changes to databases or applications or performance impact.
Question 6
The customer needs to provide PCI compliance controls to encrypt the PCI PAN data inside of DB2, Oracle and SQL Server. Which product do you recommend to the customer?
- A. Guardium Data Encryption
- B. Guardium Database Activity Monitoring
- C. Guardium Vulnerability Assessment
- D. Guardium Data Redaction
Answer : B
Explanation: The need:
Prevent users from inappropriately accessing or jeopardizing the integrity of enterprise data. Protect financial and transactional data including: payment card primary account numbers (PAN data), automatic cleansing house (ACH) transaction data and human resources (HR) data. Comply with Sarbanes-Oxley,
Payment Card Industry Data Security Standard (PCI-DSS) and other financial privacy and audit regulations.
The solution: Implement BIM InfoSphere Guardium Database Activity Monitor.
Question 7
When is data masking in the test environment NOT an important consideration?
- A. Testers/Developers typically have access to live sensitive data
- B. Outsourced applications testing requires typically requires live sensitive test data being sent to outside locations/environments
- C. Testers/Developers may perform testing on laptops which can be stolen/misplaced
- D. Client does not have sensitive data
Answer : D
Explanation: * Data masking is a method of creating a structurally similar but inauthentic version of an organization's data that can be used for purposes such as software testing and user training. The purpose is to protect the actual data while having a functional substitute for occasions when the real data is not required.
Question 8
Home grown solutions are typically costly and ineffective when compared to Guardium
Database Activity Monitor. The following are all reasons for this except:
- A. No automation or enterprise-wide policies
- B. High expertise to implement and maintain
- C. No separation of duties
- D. Insufficient testing of these solutions prior to implementation
Answer : B
Question 9
What are the overall main business drivers for the Infosphere Security and Privacy
Solutions?
- A. Security, Privacy, and Compliance
- B. Audit, discovery, and Data breach
- C. Fines, penalties, and negative reputation
- D. None of the above
Answer : A
Explanation: * Database Activity Monitoring: Three Key Business Drivers
1. Prevent data breaches
Mitigate external and internal threats
2. Ensure data integrity
Prevent unauthorized
changes to sensitive data
3. Reduce cost of compliance
Automate and centralize controls
Across DBMS platforms and applications
Across SOX, PCI, SAS70,
Simplify processes
Question 10
If the customer asks an IBM sales rep if Guardium supports the following items: "Dynamic
Profiling", "User Rights Management", and "SCUBA", what is the most likely competitor is in the account?
- A. Oracle
- B. McAfee
- C. Application Security (AppSec)
- D. Imperva
Answer : D
Explanation: * Dynamic Profiling, which is the core of Imperva's dynamic white list security model, enables SecureSphere to detect any changes in application or database usage.
* Scuba: A Free Database Vulnerability Scanner
A free tool that scans leading enterprise databases for security vulnerabilities and configuration flaws, including patch levels.
Question 11
The Infosphere Data Security and Privacy Solutions Value Proposition includes:
- A. Helping to prevent data breaches
- B. Ensure the integrity of Sensitive Data
- C. CPU acceleration
- D. All of the above
Answer : B
Explanation: IBM InfoSphere Data Privacy and Security for Data Warehousing enables organizations to reduce risk and cost associated with protecting sensitive data.
Question 12
Your customer does a lot of testing and development overseas. Which solution should you immediately recommend to him/her:
- A. Guardium Data Activity Monitor
- B. Optim Data Masking
- C. Guardium Data Redaction
- D. Guardium Encryption Expert
Answer : B
Explanation: Many organizations use production data to populate their test environments.
The problem with this is that if there is sensitive data in your production environment, then you are exposing that data to software developers and testers. IBM offers the following two solutions to solve this problem: The InfoSphere Optim Data Masking option for Test
Data Management, and the InfoSphere DataStage Pack for Data Masking. Both mask data and depersonalize it while still maintaining it's realism.
Question 13
Your customer tells you that they have already have a security solution and they do not need to buy another one. What do you tell them?
- A. Other solutions are single purpose and don't scale with business growth or across databases, data types and computing models. They can't be managed centrally or build defense in depth.
- B. Other solutions are of lower quality and do not provide the premier functionality of IBM products
- C. Disengage from the client
- D. Ask them to discuss Guardium with their current security vendor
Answer : A
Question 14
Infosphere Guardium Data Encryption (GDE) addresses compliance at the files system level through?
- A. File and Volume Encryption
- B. Database Encryption
- C. Policy Based Access Control to Encrypted Data
- D. All of them
Answer : B
Explanation: InfoSphere Guardium Data Encryption encrypts databases and files in place and avoids the need to re-architect databases, files, or storage networks. Inserted above the file system and/or logical volume layers, InfoSphere Guardium Data Encryption is transparent to users, applications, databases and storage subsystems. It requires no coding, no modification to applications or databases, and consequently deployments can be managed in weeks rather than months.
Question 15
The most compromised assets of an enterprise by percent of breaches for Web/application servers and Database Servers is small, but yet remain the most important to protect. Why is that?
- A. These servers contain the companies email system
- B. These servers contain the clients most valuable information
- C. These servers contain high volumes of structured data
- D. Both B and C
Answer : BC
Explanation: Database Servers Are The Primary Source of Breached Data because:
* Database servers contain your most valuable information
Financial records
Customer information
Credit card and other account records
Personally identifiable information
* High volumes of structured data
Easy to access -