Juniper Networks Certified Support Professional Security (JNCSP-SEC) v1.0
Question 1
-- Exhibit --
Apr 27 19:11:09 company-fw init: low_mem_signal_processes: send signal 16 to routing
Apr 27 19:11:09 company-fw /kernel: KERNEL_MEMORY_CRITICAL: System low on free memory, notifying init (#4).
Apr 27 19:11:09 company-fw rpd[1268]: Processing low memory signal
Apr 27 19:11:09 company-fw init: low_mem_signal_processes: send signal 16 to idp-policy
Apr 27 19:11:09 company-fw idpd[1295]: Processing low memory signal
Apr 27 19:11:10 company-fw idpd[1987]: IDP_SECURITY_INSTALL_RESULT: security package install result
Done;Install aborted due to system reaching low memory condition!)
-- Exhibit --
Click the Exhibit button.
You are troubleshooting a problem where the IDP signature database update on your Junos device has failed.
Referring to the exhibit, which action will resolve this problem?
- A. Perform a manual update of the IDP signature database by issuing the command request security idp security-package download.
- B. Clear the control plane memory used by IDP by issuing the command clear security idp status.
- C. Increase the amount of control plane memory by issuing the command set security advanced-services data-plane memory low.
- D. Download the IDP signature database on the control plane without updating the data plane detector engine by issuing the command request security idp security-package install update-attack-database-only.
Answer : C
References: http://kb.juniper.net/InfoCenter/index?page=content&id=KB27082
Question 2
-- Exhibit --
[edit security utm]
user@host# show
custom-objects {
url-pattern {
blocklist {
value [ http://badsite.com http://blocksite.com ];
}
acceptlist {
value http://juniper.net;
}
}
custom-url-category {
blacklist {
value blocklist;
}
whitelist {
value acceptlist;
}
}
}
feature-profile {
web-filtering {
url-whitelist whitelist;
url-blacklist blacklist;
type juniper-local;
juniper-local {
profile web-filter {
custom-block-message "Site is not allowed";
fallback-settings {
default log-and-permit;
}
}
}
}
}
utm-policy utm1 {
web-filtering {
http-profile web-filter;
}
}
-- Exhibit --
Click the Exhibit button.
You set up Web filtering to allow employees to only access your internal website. You notice that employees are still able to reach websites outside of the blacklists.
Referring the exhibit, which parameter must be changed?
- A. You must define all sites you want to block using the mime-pattern parameter.
- B. You must change the fallback-settings parameter to default block.
- C. You must use integrated or redirect Web filtering instead of local list filtering.
- D. You must define all sites you want to block using the protocol-command parameter.
Answer : C
Incorrect:
A, D: These are options for content filtering as opposed to web filtering.
B: Fallback is for error conditions.
Question 3
-- Exhibit --
user@host> show configuration security utm
custom-objects {
url-pattern {
block-juniper {
value *.spammer.com;
}
}
custom-url-category {
blacklist {
value block-juniper;
}
}
}
feature-profile {
anti-spam {
address-blacklist block-juniper;
sbl {
profile myprofile {
no-sbl-default-server;
spam-action block;
}
}
}
}
utm-policy wildcard-policy {
anti-spam {
smtp-profile myprofile;
}
}
-- Exhibit --
Click the Exhibit button.
You added a blacklist to your antispam policy to block any e-mails from the spammer.com domain. However, your users are complaining that they are still receiving spam e-mails from that domain. You run the utm test-string test and confirm that the blacklist is not working.
Referring to the exhibit, what is causing this problem?
- A. The wildcard character * cannot be used for the e-mail pattern match.
- B. The protocol-command smtp value sender: needs to be added under custom-objects.
- C. url-pattern is not supported for antispam.
- D. The pattern needs to be preceded by an @ symbol.
Answer : A
You can configure entries on either list by IP address, e-mail address, or domain name. You can use asterisk * orquestion mark ? wildcards on the local lists. You must precede all wildcard URLs with http://. You can only use the asterisk * wildcard character if it is at the beginning of the URL and is followed by a period. You can only use the question mark ? wildcard character at the end of the URL. The following wildcard syntax is supported: http://*.juniper.net. The following wildcard syntax is not supported: http://*.
References:
http://www.juniper.net/techpubs/en_US/nsm2012.2/topics/task/configuration/threat-mitigation-local-list-antispam-configuring-nsm.html
Question 4
-- Exhibit --
{hold:node0}
user@host1> show chassis cluster status
Cluster ID. 1 -
Node Priority Status Preempt Manual failover
Redundancy group: 0 , Failover count: 0
node0 1 hold no no node1 0 lost n/a n/a
{hold:node0}
user@host1> show configuration | no-more
system {
host-name host1;
root-authentication {
encrypted-password "$1$KI99zGk6$MbYFuBbpLffu9tn2.sI7l1"; ## SECRET-DATA
}
name-server {
172.16.10.100;
}
services {
ssh;
telnet;
web-management {
http;
}
}
syslog {
user * {
any emergency;
}
file messages {
any any;
authorization info;
}
file interactive-commands {
interactive-commands any;
}
}
}
interfaces {
ge-0/0/0 {
unit 0 {
family inet {
address 10.210.14.131/26;
}
}
}
ge-0/0/8 {
unit 0 {
family inet {
address 172.16.1.1/24;
}
}
}
ge-0/0/9 {
unit 0 {
family inet {
address 172.16.10.1/24;
}
}
}
}
security {
policies {
default-policy {
permit-all;
}
}
zones {
functional-zone management {
interfaces {
ge-0/0/0.0;
}
host-inbound-traffic {
system-services {
ssh;
telnet;
ping;
traceroute;
http;
snmp;
}
}
}
security-zone Trust {
host-inbound-traffic {
system-services {
any-service;
}
}
interfaces {
ge-0/0/9.0;
}
}
security-zone Untrust {
host-inbound-traffic {
system-services {
any-service;
}
}
interfaces {
ge-0/0/8.0;
}
}
}
}
----------------
{hold:node1}
user@host2> show chassis cluster status
Cluster ID. 1 -
Node Priority Status Preempt Manual failover
Redundancy group: 0 , Failover count: 0
node0 0 lost n/a n/a node1 1 hold no no
{hold:node1}
user@host2> show configuration | no-more
system {
host-name host2;
root-authentication {
encrypted-password "$1$KI99zGk6$MbYFuBbpLffu9tn2.sI7l1"; ## SECRET-DATA
}
name-server {
172.16.10.100;
}
services {
ssh;
telnet;
web-management {
http;
}
}
syslog {
user * {
any emergency;
}
file messages {
any any;
authorization info;
}
file interactive-commands {
interactive-commands any;
}
}
}
interfaces {
ge-0/0/0 {
unit 0 {
family inet {
address 10.210.14.132/26;
}
}
}
ge-0/0/8 {
unit 0 {
family inet {
address 172.16.1.1/24;
}
}
}
ge-0/0/9 {
unit 0 {
family inet {
address 172.16.10.1/24;
}
}
}
}
security {
policies {
default-policy {
permit-all;
}
}
zones {
functional-zone management {
interfaces {
ge-0/0/0.0;
}
host-inbound-traffic {
system-services {
ssh;
telnet;
ping;
traceroute;
http;
snmp;
}
}
}
security-zone Trust {
host-inbound-traffic {
system-services {
any-service;
}
}
interfaces {
ge-0/0/9.0;
}
}
security-zone Untrust {
host-inbound-traffic {
system-services {
any-service;
}
}
interfaces {
ge-0/0/8.0;
}
}
}
}
-- Exhibit --
Click the Exhibit button.
A user attempted to form a chassis cluster on an SRX240; however, the cluster did not form. While investigating the problem, you see the output shown in the exhibit.
What is causing the problem?
- A. The cluster IDs do not match.
- B. The configurations are not identical.
- C. The fxp0 interface is not configured.
- D. The ge-0/0/0 interface is configured.
Answer : D
Before we enable the SRX chassis, we need delete the configuration under ge-0/0/0 /. ge-0/0/0 will be fxp0.
Question 5
-- Exhibit ""
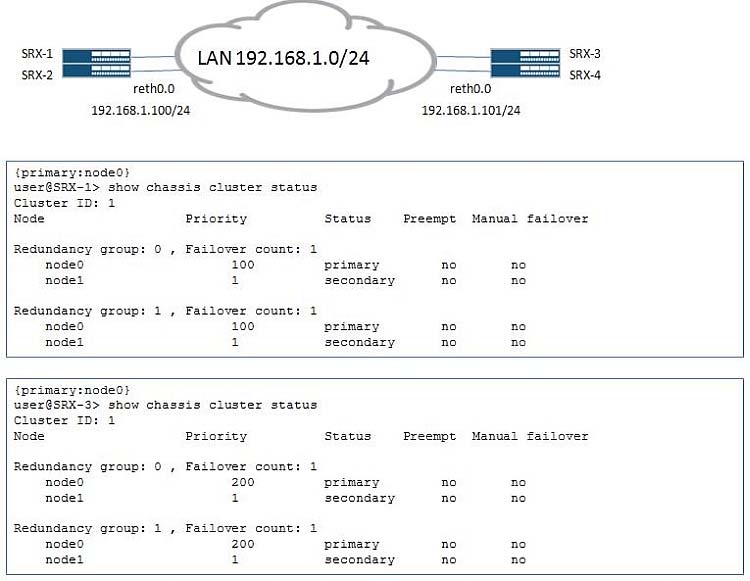
-- Exhibit --
Click the Exhibit button.
There is an existing chassis cluster connected to the corporate network 192.168.1.0/24. You are asked to connect another department to this VLAN. To achieve this, you add a new chassis cluster to the network. After connecting to the network, the cluster experiences traffic problems. You have verified that the addresses and VLAN IDs are configured correctly.
Referring to the exhibit, which configuration would resolve this problem?
- A. user@SRX-3> set chassis cluster cluster-id 1 node 0 reboot user@SRX-4> set chassis cluster cluster-id 1 node 1 reboot
- B. user@SRX-3# set chassis cluster redundancy-group 1 node 0 priority 100 user@SRX-3# commit
- C. user@SRX-3# set chassis cluster redundancy-group 1 preempt user@SRX-3# commit
- D. user@SRX-3> set chassis cluster cluster-id 2 node 0 reboot user@SRX-4> set chassis cluster cluster-id 2 node 1 reboot
Answer : D
The reth MAC addresses are calculated based on the cluster IDs and two similar cluster IDs in the same network might cause a network impact due to overlapping virtual MAC entries.
Question 6
-- Exhibit --
{primary:node0}
user@host> show configuration chassis | display inheritance
cluster {
redundancy-group 1 {
node 0 priority 200;
node 1 priority 100;
interface-monitor {
ge-0/0/12 weight 255;
ge-5/0/12 weight 255;
}
}
}
-- Exhibit --
Click the Exhibit button.
A customer reports that their SRX failover is not working as expected. They expected node1 to become the primary node for the control plane when interface ge-
0/0/12 failed. However, when ge-0/0/12 failed, node0 remained the primary node. They send you the output shown in the exhibit.
What is causing this problem?
- A. The interface-monitor configuration should be applied to redundancy-group 0.
- B. The redundancy-group configuration should include the preempt parameter.
- C. The weight parameter applied to ge-5/0/12 is too high.
- D. The weight parameter applied to ge-0/0/12 is too low.
Answer : A
Node 0 remains the master for the routing engine and therefore the "control plane", because the configuration applies to RG1 not RG0. The data plane or the forwarding for RG1 would failover in this instance which might mean nothing for the customer.
Question 7
Click the Exhibit Button.
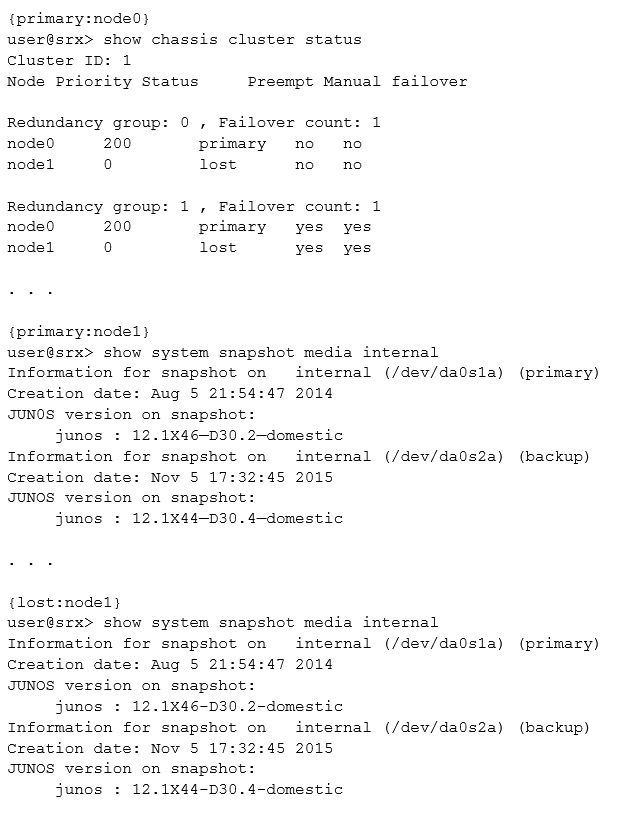
The node1 device of your chassis cluster experiences a power failure. It boots using the backup partition, while node0 remains on the primary partition.
However, the status for node1 is lost. You determine that the status of the physical links are operational, so you proceed to view the outputs shown in the exhibit.
In this scenario, what is causing the problem?
- A. The node1 device booted from a different Junos OS version.
- B. The priority in node1 was previously set to 0.
- C. A manual failover was performed after node1 boots up.
- D. The preempt configuration on node1 causes the device to change its status during the power failure.
Answer : D
Note: Preempt -
Yes: Mastership can be preempted based on priority.
No: Change in priority will not preempt the mastership.
References:
http://kb.juniper.net/InfoCenter/index?page=content&id=KB20672&actp=search http://www.juniper.net/documentation/en_US/junos12.1x44/topics/reference/command-summary/show-chassis-cluster-status.html
Question 8
Click the Exhibit button.
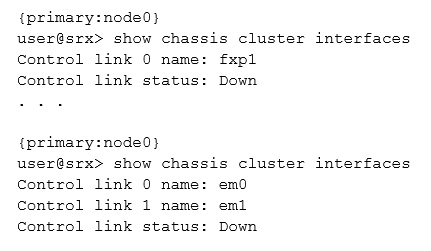
You are reviewing the status of a high-end SRX Series chassis cluster and notice that some interfaces have error messages.
Referring to the exhibit, which two steps would you use to troubleshoot the problem? (Choose two.)
- A. Verify the security policies for incoming traffic.
- B. Verify if there are Layer 1 or Layer 2 issues between the node devices.
- C. Recognize the control link port to a different Services Processing Card (SPC), move the cable, and reboot both nodes.
- D. Reconfigure the firewall filters to allow traffic.
Answer : BC
B: If the Control Link is SFP-type port, change the transceiver on both ends. Ensure that the transceivers are same type (LX, SX, etc.) and that they are Juniper- branded parts.
C: Change the cable that you are using for control link. Is the interface link light GREEN now?
Yes - Previous link cable was faulty. Recommend to now reboot both the nodes simultaneously.
References:
http://kb.juniper.net/InfoCenter/index?page=content&id=kb20698&actp=search
Question 9
Network users mention that they are having an issue downloading files. You determine that the issue began after you configured the full file-based antivirus feature on your SRX Series device. After reviewing the UTM antivirus statistics, you do not find any signs of blocked traffic because of threats.
Which configuration change solves this problem?
- A. Increase the TCP initial timeout to increase the time in the session table.
- B. Set the intelligent prescreening feature to improve antivirus scanning performance.
- C. Enable the trickling feature under the profile name set for the antivirus.
- D. Change the full file-based antivirus feature to be less CPU intensive.
Answer : B
Enable intelligent prescreening and set its timeout setting to 1800 seconds and trickling setting (applicable only to HTTP) to 600 seconds. This means that if the device receives a packet within a 600-second period during a file transfer or while performing an antivirus scan, it should not time out.
References:
http://www.juniper.net/documentation/en_US/junos12.1x46/topics/example/utm-antivirus-full-feature-profile-configuring-cli.html
Question 10
Click the Exhibit button.
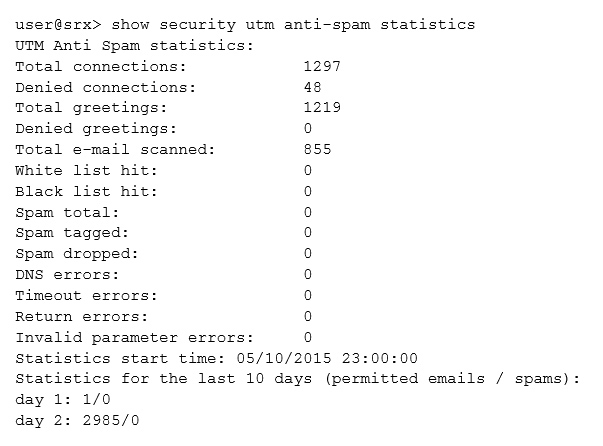
Your customer suspects that their antispam software is not functioning properly. You determine that their SRX Series device is not receiving any hits on the spam counter. You do not trust the results of the command shown in the exhibit.
In this scenario, what is happening?
- A. Traffic has been forwarded directly from a known dynamic IP range.
- B. Queries to the database are not going through.
- C. A trusted relay server in the cloud has been used.
- D. The IP address is a known spam sender.
Answer : C
Is the SMTP traffic delivered directly to you, or are you maybe using a trusted relay server in the cloud? If everything comes from a trusted server it might be a problem.
References:
https://forums.juniper.net/t5/SRX-Services-Gateway/anti-spam-no-working/m-p/272484
Question 11
A customer downloaded and installed the IDP policy template. After copying the recommended templates and creating the needed policy, the customer deleted the templates. After the commit, the templates return.
Which command will prevent the templates from appearing again?
- A. user@srx# deactivate security idp active-policy Recommended
- B. user@srx# delete security idp idp-policy Recommended
- C. user@srx# set security idp security-package automatic
- D. user@srx# deactivate system scripts commit file templates.xsl
Answer : D
Delete or deactivate the commit script file. By deleting the commit script file, you avoid the risk of overwriting modifications to the template when you commit the configuration. Run one of the following commands: user@host# delete system scripts commit file templates.xsl user@host# deactivate system scripts commit file templates.xsl
References:
http://www.juniper.net/documentation/en_US/junos12.1x47/topics/task/configuration/idp-predefined-policy-template-downloading-and-using-cli.html
Question 12
Click the exhibit button.
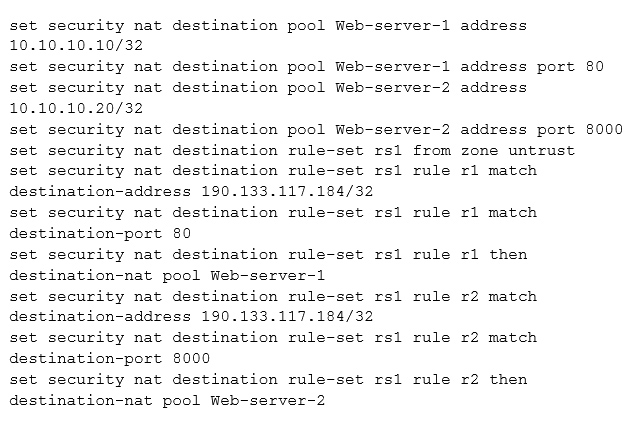
You recently installed two new internal webservers. You configure destination NAT on your SRX Series device so that external users will have access to internal
Web resources. However, the external users reported that they still do not have access to the server.
Referring to the exhibit, what should you do to solve the problem?
- A. Configure proxy ARP for the address 190.133.117.184/32.
- B. Contact your ISP since the packets are not reaching the SRX Series device.
- C. Configure 190.133.117.184/32 under a security zone.
- D. Configure a different IP address for the internal servers.
Answer : C
An interface for a security zone can be thought of as a doorway through which TCP/IP traffic can pass between that zone and any other zone.
Through the policies you define, you can permit traffic between zones to flow in one direction or in both. With the routes that you define, you specify the interfaces that traffic from one zone to another must use
Note: A security zone is a collection of one or more network segments requiring the regulation of inbound and outbound traffic through policies. Security zones are logical entities to which one or more interfaces are bound.
References:
http://www.juniper.net/techpubs/en_US/junos12.1x44/information-products/pathway-pages/security/security-basic-zone-interface.pdf
Question 13
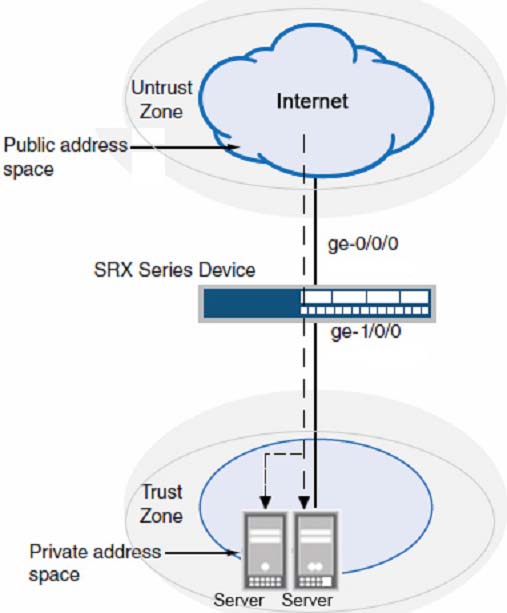
Click the Exhibit button.
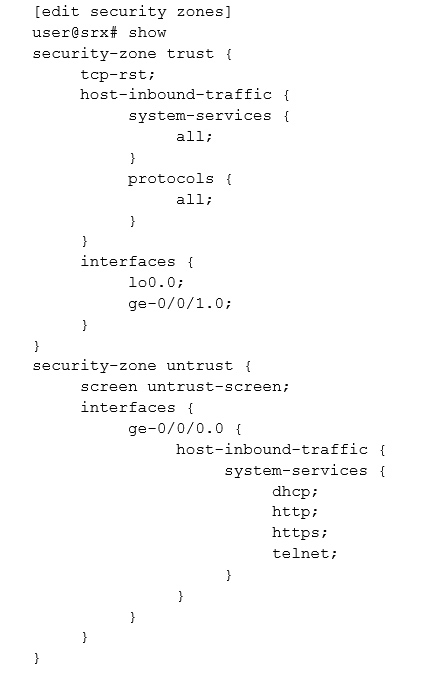
A customer has a problem connecting to an SRX Series device from the untrust zone using SSH only.
Referring to the exhibit, which action will solve the problem?
- A. Configure the ssh parameter under the [edit security zones security-zone trust interfaces ge-0/0/1.0 host inbound-traffic hierarchy. protocols]
- B. Configure the ssh parameter under the [edit security zones security-zone untrust host-inbound-traffic system-services] hierarchy.
- C. Configure the ssh parameter under the [edit security zones security-zone untrust host-inbound-traffic protocols] hierarchy.
- D. Configure the ssh parameter under the [edit security zones security-zone trust host-inbound-traffic system-services] hierarchy.
Answer : B
Assume that inbound ssh, ftp, and ping traffic should be permitted from the untrusted zone. Then you should do the following:
[edit security zones]
root# set security zone untrust host-inbound-traffic ssh
root# set security zone untrust host-inbound-traffic ftp
root# set security zone untrust host-inbound-traffic ping
Note: For SRX Series branch devices, a factory default security policy is provided that:
Allows all traffic from the trust zone to the untrust zone.
Allows all traffic between trusted zones, that is from the trust zone to intrazone trusted zones.
Denies all traffic from the untrust zone to the trust zone.
References:
http://www.dummies.com/how-to/content/how-to-configure-srx-security-zones-with-junos.html http://www.juniper.net/documentation/en_US/junos12.3x48/topics/concept/security-srx-device-zone-and-policy-understanding.html
Question 14
Click the exhibit button.
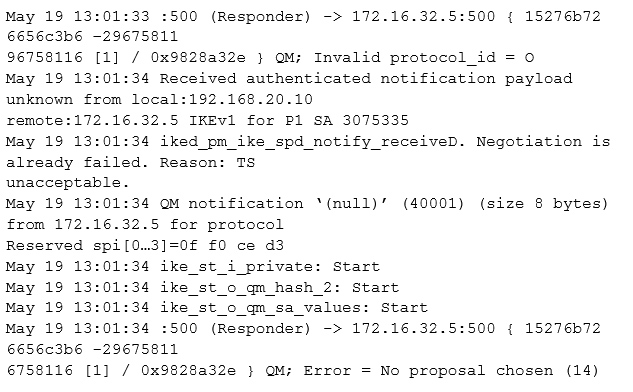
Your customer has indicated that their VPN is down.
Referring to the exhibit, what is the problem?
- A. The IKE IDs are mismatched.
- B. The proxy IDs are mismatched.
- C. The IKE Phase 2 proposals are mismatched.
- D. The IKE Phase 1 proposals are mismatched.
Answer : B
Example of IKE proxy-id mismatch (see line 11 onwards):
1 [Apr 2 10:57:34]SA-CFG lookup for Phase 2 failed for local:172.16.123.2, remote:172.16.123.1 IKEv1
2. [Apr 2 10:57:34]ikev2_fb_spd_select_qm_sa_cb: IKEv2 SA select failed with error TS unacceptable
3. [Apr 2 10:57:34]ikev2_fb_spd_select_qm_sa_cb: SA selection failed, no matching proposal (neg df6800)
.
.
.
11 [Apr 2 10:57:34]iked_pm_ike_spd_notify_received: Negotiation is already failed. Reason: TS unacceptable.
[Apr 2 10:57:34]QM notification `(null)' (40001) (size 8 bytes) from 172.16.123.1 for protocol Reserved spi[0...3]=eb 7b b2 b4
[Apr 2 10:57:34]ike_st_i_private: Start
[Apr 2 10:57:34]ike_st_o_qm_hash_2: Start
[Apr 2 10:57:34]ike_st_o_qm_sa_values: Start
Note: "A proxy-ID is used during phase 2 of Internet Key Exchange (IKE) Virtual Private Network (VPN) negotiations. Both ends of a VPN tunnel either have a proxy-ID manually configured (route-based VPN) or just use a combination of source IP, destination IP, and service in a tunnel policy. When phase 2 of IKE is negotiated, each end compares the configured local and remote proxy-ID with what is actually received. The configured proxy ID must match with what is received from the other device that is negotiating an IKE/IPsec tunnel.
References: http://www.twine-networks.com/blog/posts/5-troubleshooting-ipsec-log-messages
Question 15
Click the Exhibit button.
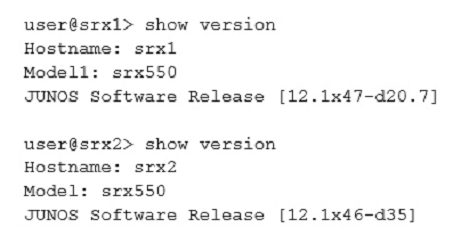
A customer wants to create a chassis cluster with the SRX Series devices shown in the exhibit. The customer is not able to create the chassis cluster. In this scenario, what would solve the problem?
- A. Both SRX Series devices need the same software version.
- B. Both SRX Series devices need the same hostname.
- C. A reboot in node1 is needed.
- D. The model must be different.
Answer : A
The SOFTWARE on both standalone devices must be the same Junos OS version.
Verify using this command on both devices:
root> show version
Model: srx220h -
JUNOS Software Release [11.4R7.5]
References: http://kb.juniper.net/InfoCenter/index?page=content&id=KB21312&actp=search