Security, Professional v1.0
Question 1
Click the Exhibit button.
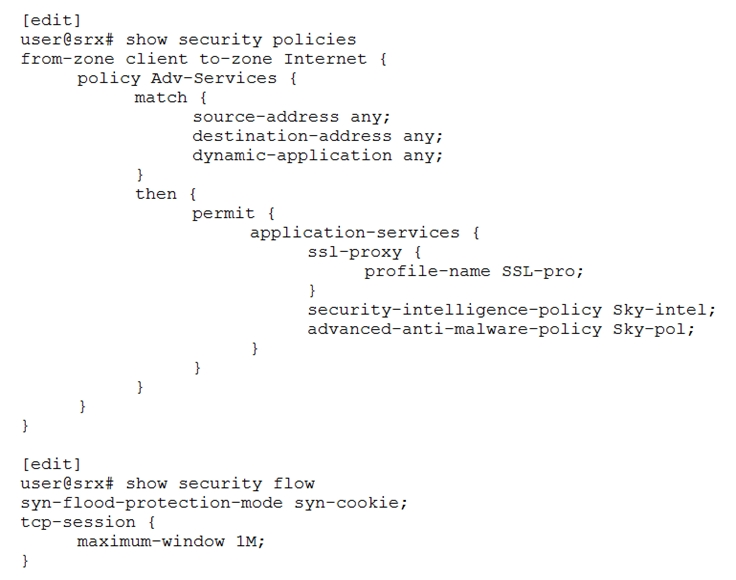
You deployed a site-to-site IPsec VPN connecting two data centers together using SRX5800s. After examining the performance of the IPsec VPN, you decide to enable IPsec performance acceleration to increase the rate of traffic that can be sent through the tunnel.
Referring to the exhibit, which two statements should you add to the configuration to accomplish this task? (Choose two.)
- A. [edit security flow] user@srx# set tcp-mss ipsec-vpn mss 65535
- B. [edit security flow] user@srx# set ipsec-performance-acceleration
- C. [edit security flow] user@srx# set power-mode-ipsec
- D. [edit security flow] user@srx# set load-distribution session-affinity ipsec
Answer : BD
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-improving-ipsec-vpn-traffic-performance.html
Question 2
Click the Exhibit button.
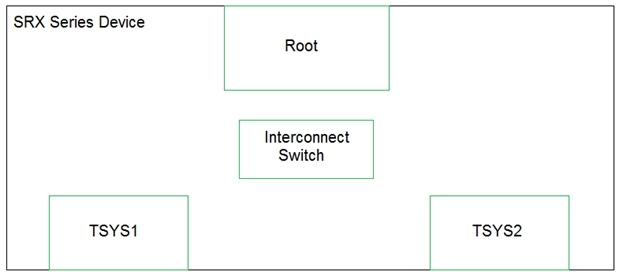
You have configured tenant systems on your SRX Series device.
Referring to the exhibit, which two actions should you take to facilitate inter-TSYS communication? (Choose two.)
- A. Place the logical tunnel interfaces in a virtual router routing instance in the interconnect switch
- B. Place the logical tunnel interfaces in a VPLS routing instance in the interconnect switch
- C. Connect each TSYS with the interconnect switch by configuring INET configured logical tunnel interfaces in the interconnect switch
- D. Connect each TSYS with the interconnect switch by configuring Ethernet VPLS configured logical tunnel interfaces in the interconnect switch
Answer : AC
Question 3
Click the Exhibit button.
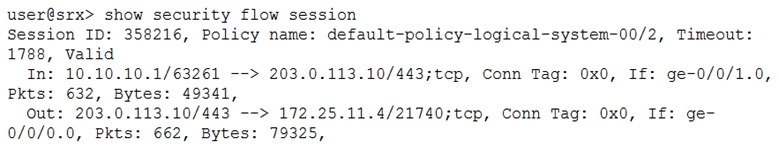
Referring to the exhibit, which statement is true?
- A. Source NAT with PAT is occurring
- B. Destination NAT is occurring
- C. Static NAT without PAT is occurring
- D. Source NAT without PAT is occurring
Answer : A
Question 4
Click the Exhibit button.
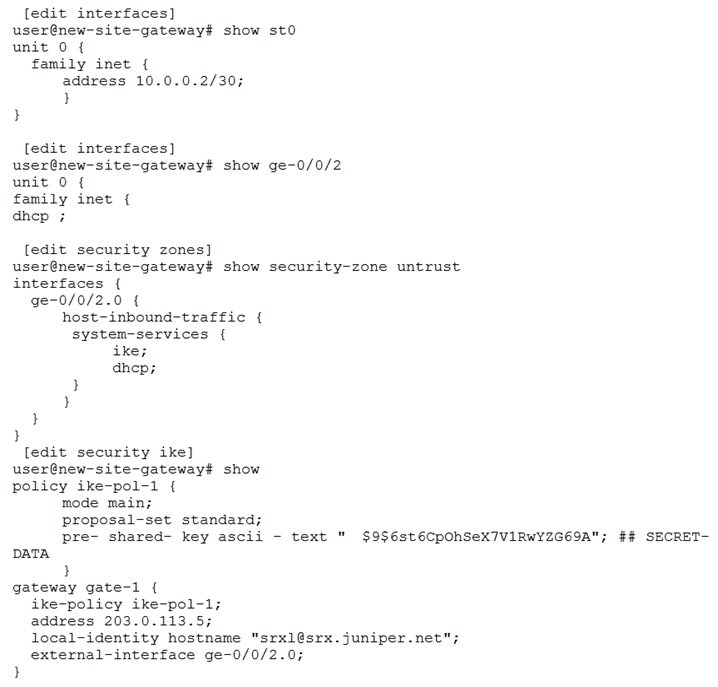
Your company has purchased a competitor and now must connect the new network to the existing one. The competitorג€™s gateway device is receiving its ISP address using DHCP. Communication between the two sites must be secured; however, obtaining a static public IP address for the new site gateway is not an option at this time. The company has several requirements for this solution:
✑ A site-to-site IPsec VPN must be used to secure traffic between the two sites;
✑ The IKE identity on the new site gateway device must use the hostname option; and
✑ Internet traffic from each site should exit through its local Internet connection.
The configuration shown in the exhibit has been applied to the new siteג€™s SRX, but the secure tunnel is not working.
In this scenario, what configuration change is needed for the tunnel to come up?
- A. Remove the quotes around the hostname
- B. Bind interface st0 to the gateway
- C. Change the IKE policy mode to aggressive
- D. Apply a static address to ge-0/0/2
Answer : A
Question 5
Click the Exhibit button.

Referring to the exhibit, which two statements are true? (Choose two.)
- A. You can secure intra-VLAN traffic with a security policy on this device
- B. You can secure inter-VLAN traffic with a security policy on this device
- C. The device can pass Layer 2 and Layer 3 traffic at the same time
- D. The device cannot pass Layer 2 and Layer 3 traffic at the same time
Answer : AD
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/ethernet-port-switching-modes.html
Question 6
Click the Exhibit button.
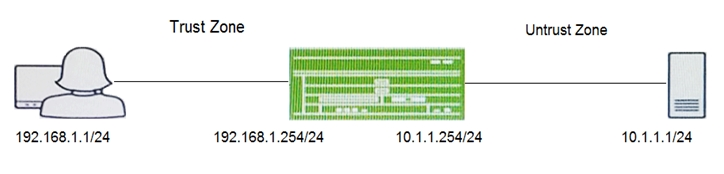
A user reports trouble when using SSH to a server outside your organization. The traffic traverses an SRX Series device that is performing NAT and applying security policies.
Referring to the exhibit, which configuration will allow you to see the bidirectional flow through the SRX Series device?
A.
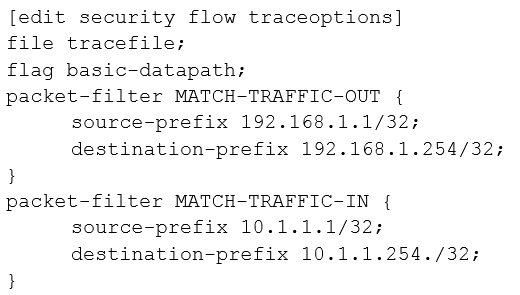
B.
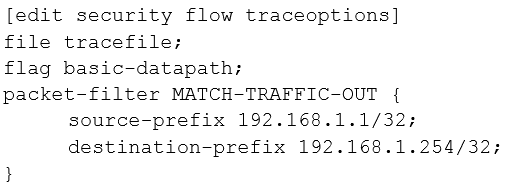
C.
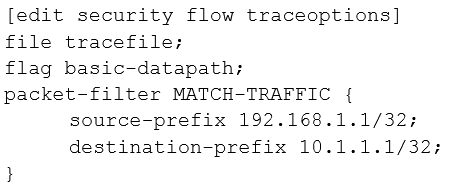
D.
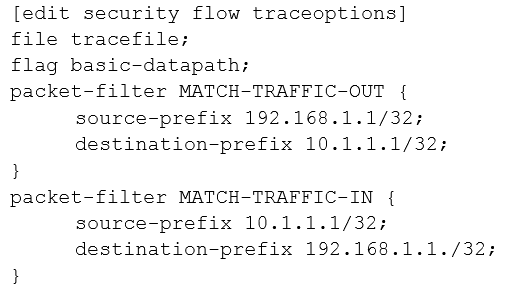
Answer : D
Question 7
Click the Exhibit button.
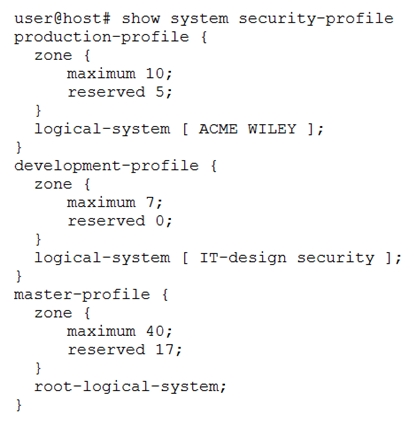
Referring to the exhibit, what is the maximum number of zones that are able to be created within all logical systems?
- A. 74
- B. 34
- C. 40
- D. 17
Answer : C
Question 8
Click the Exhibit button.
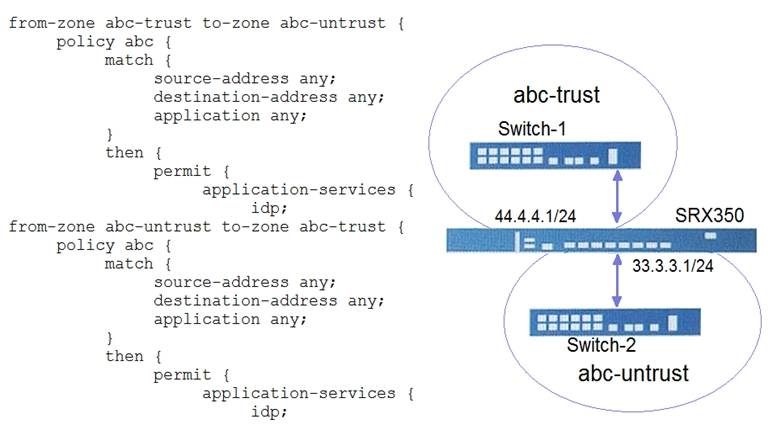
Referring to the exhibit, which three types of traffic would be examined by the IPS policy between Switch-1 and Switch-2? (Choose three.)
- A. TCP
- B. LLDP
- C. ARP
- D. ICMP
- E. UDP
Answer : ADE
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-idp-policy-rules-and-rulebases.html
Question 9
Click the Exhibit button.
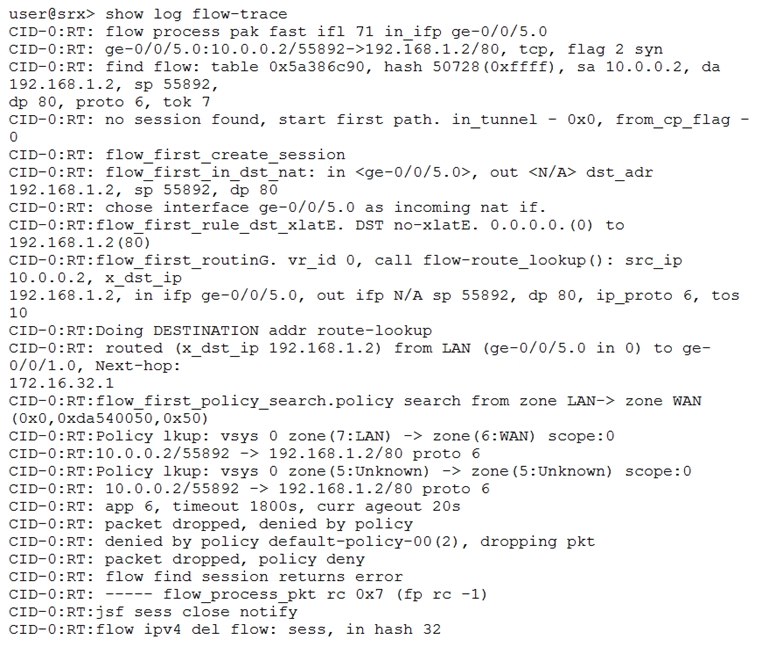
A host is unable to communicate with a webserver.
Referring to the exhibit, which statement is correct?
- A. The webserver is not listening for traffic on port 80
- B. A policy is denying the traffic between these two hosts
- C. A session is created for this flow
- D. The session table is running out of resources
Answer : B
Question 10
Click the Exhibit button.

Which statement is correct regarding the information show in the exhibit?
- A. The tunnel binding was discovered automatically
- B. The output is for an ADVPN
- C. The tunnel gateway address was automatically discovered
- D. The tunnel is not encrypting the traffic
Answer : C
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/reference/command-summary/show-security-ipsec-next-hop-tunnels.html
Question 11
In which two ways are tenant systems different from logical systems? (Choose two.)
- A. Tenant systems have higher scalability than logical systems
- B. Tenant systems have less scalability than logical systems
- C. Tenant systems have fewer routing features than logical systems
- D. Tenant systems have more routing features than logical systems
Answer : AC
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/tenant-systems-overview.html#:~:text=Although%20similar%20to%20logical%
20systems,administrative%20domain%20for%20security%20services
Question 12
Which two statements are true about ADVPN members? (Choose two.)
- A. ADVPN members are authenticated using pre-shared keys
- B. ADVPN members are authenticated using certificates
- C. ADVPN members can use IKEv2
- D. ADVPN members can use IKEv1
Answer : BC
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-auto-discovery-vpns.html
Question 13
Which two VPN features are supported with CoS-based IPsec VPNs? (Choose two.)
- A. IKEv2
- B. VPN monitoring
- C. dead peer detection
- D. IKEv1
Answer : AC
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/secuirty-cos-based-ipsec-vpns.html
Question 14
Click the Exhibit button.
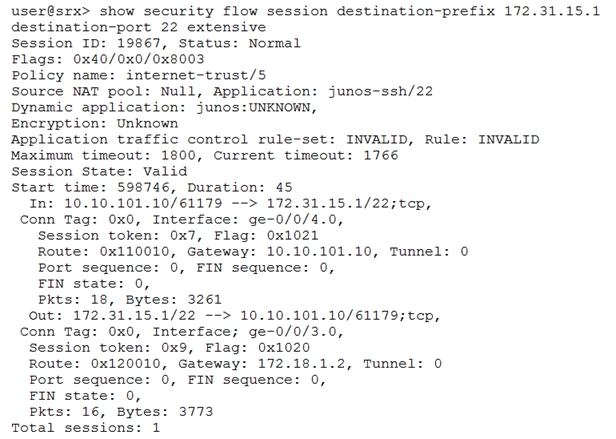
Given the command output shown in the exhibit, which two statements are true? (Choose two.)
- A. The host 172.31.15.1 is directly connected to interface ge-0/0/3.0
- B. Traffic matching this session has been received since the session was established
- C. The host 10.10.101.10 is directly connected to interface ge-0/0/4.0
- D. Network Address Translation is applied to this session
Answer : BC
Question 15
Click the Exhibit button.
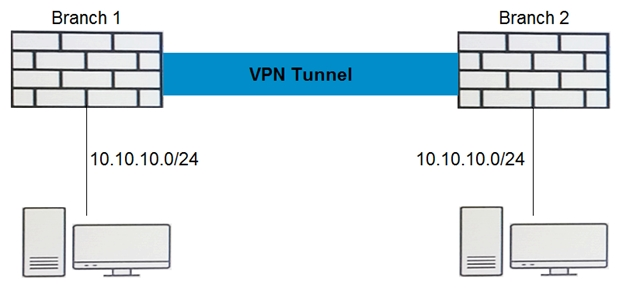
Branch 1 and Branch 2 have an active VPN tunnel configured, but internal hosts cannot communicate with each other.
Referring to the exhibit, which type of configuration should be applied to solve the problem?
- A. Configure destination NAT on both Branch 1 and Branch 2
- B. Configure source NAT on Branch 1
- C. Configure destination NAT on Branch 2 only
- D. Configure static NAT on both Branch 1 and Branch 2
Answer : D