Security, Professional (JNCIP-SEC) v7.0
Question 1
Click the Exhibit button.
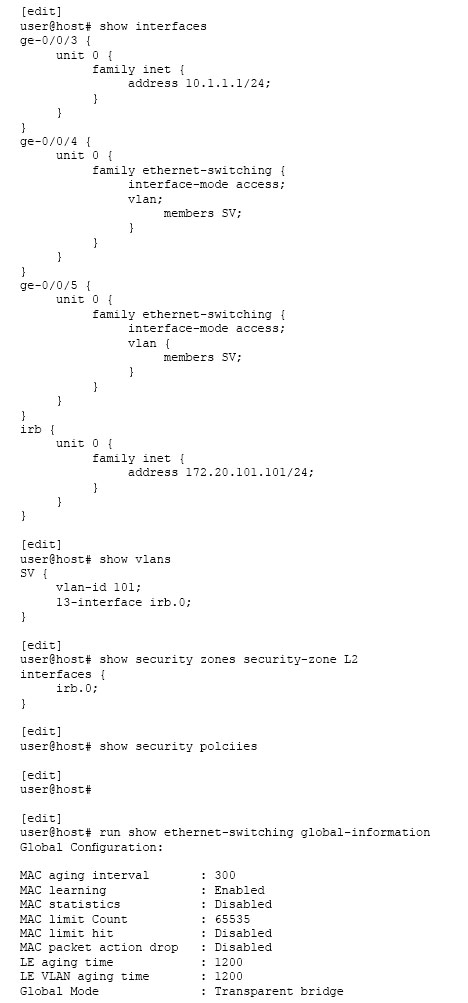
Two hosts on the same subnet are connected to an SRX340 using interfaces ge-0/0/4 and ge-0/0/5. The two hosts can communicate with each other, but they cannot communicate with hosts outside of their subnet.
Referring to the exhibit, which three actions would you take to solve this problem? (Choose three.)
- A. Add the ge-0/0/4 and ge-0/0/5 interfaces to the L2 zone.
- B. Remove the irb.0 interface from the L2 zone.
- C. Set the SRX340 to Ethernet switching mode.
- D. Configure a security policy to permit the traffic.
- E. Reboot the SRX340.
Answer : C,D,E
Question 2
You are creating an IPS policy with multiple rules. You want traffic that matches rule 5 to silently be dropped, along with any future packets that match the appropriate attributes of the incoming traffic.
In this scenario, which ip-action parameter should you use?
- A. ip-block
- B. ip-close
- C. log-create
- D. timeout
Answer : A
Question 3
Click the Exhibit button.
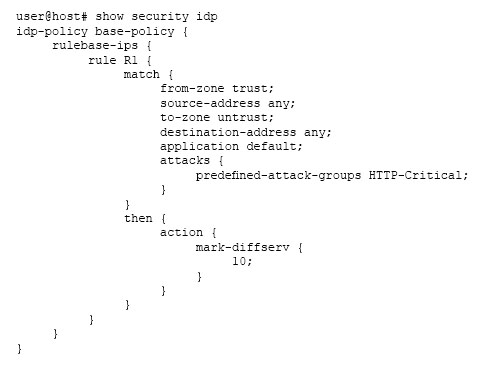
Referring to the security policy shown in the exhibit, which two actions will happen as the packet is processed? (Choose two.)
- A. It passes unmatched traffic after modifying the DSCP priority.
- B. It marks and passes matched traffic with a high DSCP priority.
- C. It marks and passes matched traffic with a low DSCP priority.
- D. It passes unmatched traffic without modifying DSCP priority.
Answer : BD
Question 4
Click the Exhibit button.
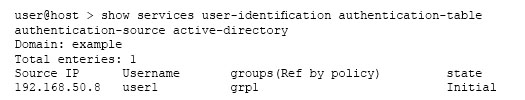
Which statement explains the current state value of the command output shown in the exhibit?
- A. A valid response was received from a domain PC probe, and the user is a valid domain user programmed in the PFE.
- B. An invalid response was received from a domain PC probe, and the user is an invalid domain user.
- C. A probe event generated an entry in the authentication table, but no probe response has been received from the domain PC.
- D. The user-to-address mapping was successfully read from the domain controller event logs, and an entry was added to the authentication table witch currently resides on the Routing Engine.
Answer : A
Question 5
Click the Exhibit button.

Referring to the exhibit, which statement is true?
- A. E-mails from the [email protected] address are marked with SPAM in the subject line by the spam block list server.
- B. E-mails from the [email protected] address are blocked by the spam list server.
- C. E-mails from the [email protected] address are blocked by the reject blacklist.
- D. E-mails from the [email protected] address are allowed by the allow whitelist.
Answer : D
Question 6
Click the Exhibit button.

According to the policy shown in the exhibit, which application-services traffic will be processed first?
- A. the application traffic matchings the IDP rules
- B. the application traffic matchings the utm-policy log rule set
- C. the application traffic matchings the utm-policy wf-policy_websense-home rules
- D. the application traffic matchings the application-firewall rule-set demo-tracking_1 rule
Answer : A
Question 7
Your network includes SRX Series devices at the headquarters location. The SRX Series devices at this location are part of a high availability chassis cluster and are expected to support several UTM features.
Which two statements related to this environment are true? (Choose two.)
- A. UTM features can be configured on either of the nodes within the cluster.
- B. The chassis cluster must be configured for active/active mode.
- C. UTM features must be configured on the primary node within the cluster.
- D. The chassis cluster must be configured for active/backup mode.
Answer : A,D
Question 8
The Software-Defined Secure Networks Policy Enforcer contains which two components?
(Choose two.)
- A. SRX Series device
- B. Sky ATP
- C. Policy Controller
- D. Feed Connector
Answer : CD
Question 9
A customer has recently deployed a next-generation firewall, sandboxing software, cloud access security brokers (CASB), and endpoint protection.
In this scenario, which tool would provide the customer with additional attack prevention?
- A. Junos Space Cross Provisioning Platform
- B. Contrail
- C. Security Director Policy Enforcer
- D. Network Director Inventory Manager
Answer : C
Question 10
Which two statements about enabling MACsec using static CAK security mode keys are true? (Choose two.)
- A. CAK secures the data plane traffic.
- B. SAK secures the data plane traffic.
- C. SAK secures the control plane traffic.
- D. CAK secures the control plane traffic.
Answer : BD
Question 11
After downloading the new IPS attack database, the installation of the new database fails.
What caused this condition?
- A. The new attack database no longer contained an attack entry that was in use.
- B. The new attack database was revoked between the time it was downloaded and installed.
- C. The new attack database was too large for the device on which it was being installed.
- D. Some of the new attack entries were already in use and had to be deactivated before installation.
Answer : A
Question 12
While reviewing the Log and Reporting portion of Security Director, you find that multiple objects reference the same address. You want to use a standardized name for all of the objects.
In this scenario, how would you create a standardized object name without searching the entire policy?
- A. Remove the duplicate objects.
- B. Merge the duplicate objects.
- C. Rename the duplicate objects.
- D. Replace the duplicate objects.
Answer : B
Question 13
You have configured a log collector VM and Security Director. System logging is enabled on a branch SRX Series device, but security logs do not appear in the monitor charts.
How would you solve this problem?
- A. Configure a security policy to forward logs to the collector.
- B. Configure application identification on the SRX Series device.
- C. Configure security logging on the SRX Series device.
- D. Configure J-Flow on the SRX Series device.
Answer : C
Question 14
Click the Exhibit button.

Referring to the exhibit, which two statements are true? (Choose two.)
- A. You can secure inter-VLAN traffic with a security policy on this device.
- B. You can secure intra-VLAN traffic with a security policy on this device.
- C. The device can pass Layer 2 and Layer 3 traffic at the same time.
- D. The device cannot pass Layer 2 and Layer 3 traffic at the same time.
Answer : AC
Question 15
Your manager has identified that employees are spending too much time posting on a social media site. You are asked to block user from posting on this site, but they should still be able to access any other site on the Internet.
In this scenario, which AppSecure feature will accomplish this task?
- A. AppQoS
- B. AppTrack
- C. APpFW
- D. APBR
Answer : C