Cloud, Specialist (JNCIS-Cloud) v1.0
Question 1
Two virtual machines that belong to the same virtual network are not able to communicate with each other.
Which statement is true in this scenario?
- A. A floating IP address is assigned to the virtual machine.
- B. Images used to spawn the two virtual machines have different flavors.
- C. A security group is blocking the communication.
- D. The two virtual machines are in different availability zones.
Answer : C
Question 2
What are three functions of an SDN controller? (Choose three.)
- A. An SDN controller uses federated routes between BGP autonomous systems.
- B. An SDN controller uses northbound APIs to manage applications and business logic.
- C. An SDN controller uses southbound APIs to manage flow control to the switches and routes in the network.
- D. An SDN controller uses federated data between SDN controller domains.
- E. An SDN controller functions as a gateway for the virtual machines in the SDN.
Answer : ABC
Question 3
You are configuring a Contrail Security firewall policy rule and need to specify an exact port.
Which two statements describe how to accomplish this task? (Choose two.)
- A. You should create a tag and specify it in the firewall policy rule.
- B. You should create an address group and specify it in the firewall policy rule.
- C. You should create a service group and specify it in the firewall policy rule.
- D. You should specify the service in the firewall policy rule.
Answer : AB
Reference:
https://www.juniper.net/documentation/en_US/contrail20/information-products/pathway-pages/contrail-networking-security-user-guide.pdf
Question 4
Click the Exhibit button.
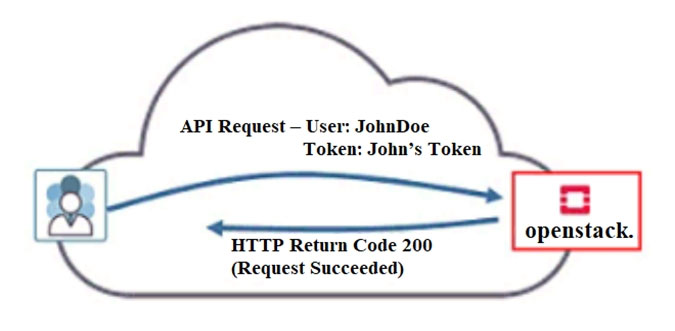
Referring to the exhibit, what must have occurred prior to JohnDoe sending the request?
- A. JohnDoe must have obtained a valid token from Horizon.
- B. JohnDoe must have successfully authenticated using OpenStackג€™s Web user interface.
- C. JohnDoe must have obtained a valid token from Keystone.
- D. JonnDoe must have obtained a valid token from the Contrail control node.
Answer : A
Question 5
Which Kubernetes resource defines the traffic allowed to reach the pod?
- A. SecurityGroup
- B. NetworkPolicy
- C. Ingress
- D. IPAM
Answer : B
Reference:
https://www.juniper.net/documentation/en_US/contrail19/topics/concept/k8s-network-policy.html
Question 6
Which ETSI NFV function is responsible for the management of virtual network functions (VNF) and element management systems (EMS)?
- A. Virtual Network Function Manager (VNFM)
- B. OpenStack
- C. Contrail Command
- D. Analytics Database
Answer : A
Question 7
Your development team asks you to provision twenty exact copies of a three-tier application containing three VMs. Each copy of the application must be on their own isolated network. The development team also wants to deploy more copies in the future from a self-service portal.
What will accomplish this task?
- A. Create a Heat orchestration template for the application and then launch twenty stacks using the Horizon dashboard or OpenStack CLI.
- B. Use the Contrail fabric manager to define and launch all twenty stacks using an intent-driven automation feature.
- C. Create all twenty networks and launch each instance using the Horizon instance creation wizard.
- D. Create a Heat orchestration template for the application and then launch twenty stacks using the AppFormix user interface.
Answer : A
Question 8
What are two supported methods to add a new Contrail compute node using Contrail Command? (Choose two.)
- A. From the Web UI, add a new server and assign it as a compute node to the existing cluster.
- B. From the CLI on the Contrail Command server, edit the instances.yml file and add the new node information.
- C. From the CLI on the Contrail Command server, edit the command_servers.yml file and add the new node information.
- D. From the CLI on the Contrail Command server, edit the testbed.py file and add the new node information.
Answer : AB
Reference:
https://www.juniper.net/documentation/en_US/contrail19/topics/task/configuration/adding-new-compute-node-cc.html
Question 9
Which two interfaces are active in the Contrail analyzer-vm-console-two-if.qcow2 traffic analyzer image? (Choose two.)
- A. left
- B. right
- C. monitor
- D. management
Answer : AD
Reference:
https://www.juniper.net/documentation/en_US/contrail19/topics/task/configuration/configure-traffic-analyzer-vnc.html
Question 10
You are creating an AppFormix dynamic alarm definition with a dynamic threshold.
In this scenario, which three parameters are available? (Choose three.)
- A. baseline analysis algorithm
- B. state
- C. owner
- D. sensitivity
- E. learning period duration
Answer : ADE
Reference:
https://www.juniper.net/documentation/en_US/appformix/topics/concept/appformix-alarms.html
Question 11
Which three encapsulations does Contrail support for overlay networking? (Choose three.)
- A. MPLS over GRE
- B. EVPN
- C. VXLAN
- D. MPLS over UDP
- E. MPLS over IPsec
Answer : ACD
Reference:
https://www.juniper.net/us/en/local/pdf/whitepapers/2000535-en.pdf
Question 12
A vRouter includes which two containers? (Choose two.)
- A. nodemgr
- B. dns
- C. api
- D. agent
Answer : AD
Reference:
https://docs.mirantis.com/mcp/q4-18/mcp-ref-arch/opencontrail-plan/contrail-components/contrail-components-4.html
Question 13
You are asked to create a connection between a VM and two ports on a QFX leaf device in the fabric.
Which Contrail feature must you configure to accomplish this task?
- A. virtual network policy
- B. floating IP
- C. virtual port group
- D. virtual network with route leaking
Answer : C
Reference:
https://www.juniper.net/documentation/en_US/contrail19/information-products/pathway-pages/contrail-fabric-lifecycle-management-feature- guide.pdf#page=113&zoom=100,100,712
Question 14
Which two nodes are part of the Contrail controller role? (Choose two.)
- A. config
- B. control
- C. analytics
- D. load balancer
Answer : AB
Reference:
https://www.juniper.net/documentation/en_US/nfv2.1/topics/concept/ccpe-architecture.html#:~:text=Contrail%20controller%20node%2C%20which%
20hosts,virtualized%20network%20functions%20(VNFs)
.
http://juniper.github.io/contrail-vnc/architecture.html
Question 15
Which statements correct about Contrail security?
- A. Contrail security is used to control access into Junos devices.
- B. Contrail security is used to apply security features and segment traffic flows.
- C. Contrail security is used to analyze network performance and learn traffic patterns.
- D. Contrail security is used to control management access to VNFs.
Answer : B