Security, Specialist v1.0
Question 1
You must configure JSA to accept events from an unsupported third-party log source.
In this scenario, what should you do?
- A. Separate event collection and flow collection on separate collectors.
- B. Configure an RPM for a third-party device service module.
- C. Configure JSA to silently discard unsupported log types.
- D. Configure a universal device service module.
Answer : D
Question 2
Which two solutions provide a sandboxing feature for finding zero-day malware threats? (Choose two.)
- A. Sky ATP
- B. UTM
- C. JATP
- D. IPS
Answer : AC
Question 3
Click the Exhibit button.
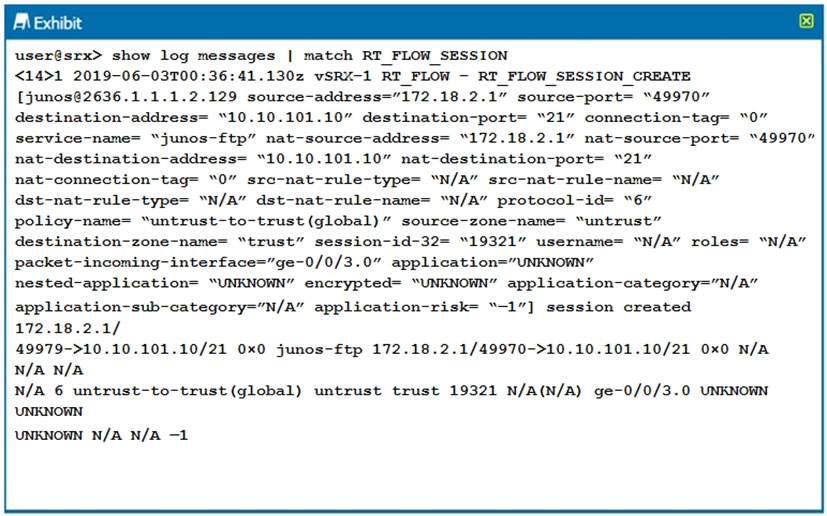
The output shown in the exhibit is displayed in which format?
- A. syslog
- B. WELF
- C. binary
- D. sd-syslog
Answer : D
Question 4
You are using the JIMS Administrator user interface to add multiple SRX client devices. You must share common configuration attributes across the SRX clients without having to re-enter those attributes for each SRX client instance.
Which JIMS Administrator feature would be used to accomplish this task?
- A. JIMS automation
- B. JIMS templates
- C. JIMS client profiles
- D. JIMS client defaults
Answer : B
Question 5
In an Active/Active chassis cluster deployment, which chassis cluster component is responsible for RG0 traffic?
- A. the backup routing engine of the primary node
- B. the master routing engine of the secondary node
- C. the primary node
- D. the secondary node
Answer : C
Question 6
Your manager asks you to find employees that are watching YouTube during office hours.
Which AppSecure component would you configure to accomplish this task?
- A. AppQoE
- B. AppFW
- C. AppTrack
- D. AppQoS
Answer : C
Question 7
What are two types of collectors for the JATP core engine? (Choose two.)
- A. SNMP
- B. e-mail
- C. Web
- D. telemetry
Answer : BC
Question 8
Click the Exhibit button.
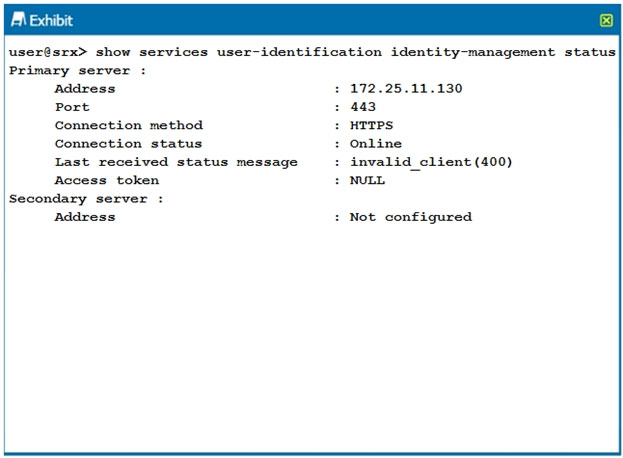
You have configured your SRX Series device to receive authentication information from a JIMS server. However, the SRX is not receiving any authentication information.
Referring to the exhibit, how would you solve the problem?
- A. Use the JIMS Administrator user interface to add the SRX device as a client.
- B. Generate an access token on the SRX device that matches the access token on the JIMS server.
- C. Update the IP address of the JIMS server
- D. Change the SRX configuration to connect to the JIMS server using HTTP.
Answer : B
Question 9
After a software upgrade on an SRX5800 chassis cluster, you notice that both node0 and node1 are in the primary state, when node1 should be secondary. All control and fabric links are operating normally.
In this scenario, which step must you perform to recover the cluster?
- A. Execute the request system reboot command on node1.
- B. Execute the request system software rollback command on node0.
- C. Execute the request system software add command on node1.
- D. Execute the request system reboot command on node0.
Answer : A
Question 10
What is the default timeout period for a TCP session in the session table of a Junos security device?
- A. 1 minute
- B. 60 minutes
- C. 15 minutes
- D. 30 minutes
Answer : D
Question 11
Which security log message format reduces the consumption of CPU and storage?
- A. WELF
- B. BSD syslog
- C. binary
- D. structured syslog
Answer : B
Question 12
You must block the lateral spread of Remote Administration Tools (RATs) that use SMB to propagate within the network, using the JATP solution.
Which action would accomplish this task?
- A. Configure a new anti-virus configuration rule.
- B. Configure whitelist rules
- C. Configure YARA rules.
- D. Configure the SAML settings.
Answer : C
Question 13
Click the Exhibit button.
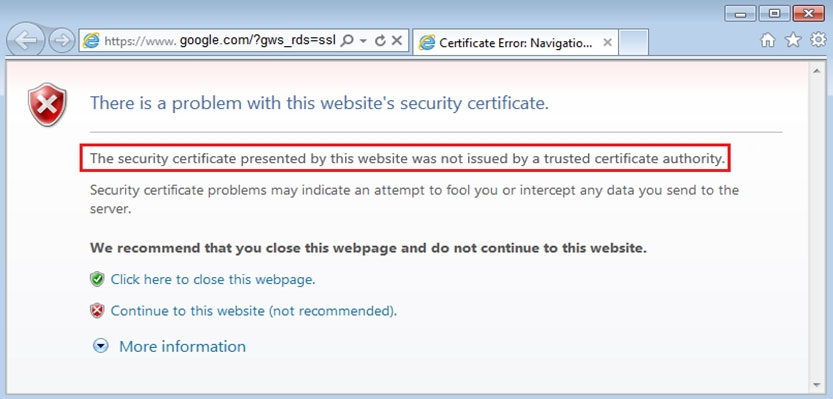
You have implemented SSL proxy client protection. After implementing this feature, your users are complaining about the warning message shown in the exhibit.
Which action must you perform to eliminate the warning message?
- A. Configure the SRX Series device as a trusted site in the client Web browsers.
- B. Regenerate the SRX self-signed CA certificate and include the correct organization name.
- C. Import the SRX self-signed CA certificate into the client Web browsers.
- D. Import the SRX self-signed CA certificate into the SRX certificate public store.
Answer : C
Question 14
You are asked to enable AppTrack to monitor application traffic from hosts in the User zone destined to hosts in the Internet zone.
In this scenario, which statement is true?
- A. You must enable the AppTrack feature within the Internet zone configuration.
- B. You must enable the AppTrack feature within the ingress interface configuration associated with the Internet zone.
- C. You must enable the AppTrack feature within the interface configuration associated with the User zone.
- D. You must enable the AppTrack feature within the User zone configuration.
Answer : D
Question 15
The DNS ALG performs which three functions? (Choose three.)
- A. The DNS ALG performs the IPv4 and IPv6 address transformations.
- B. The DNS ALG performs DNS doctoring.
- C. The DNS ALG modifies the DNS payload in NAT mode.
- D. The DNS ALG performs DNSSEC.
- E. The DNS ALG performs DNS load balancing.
Answer : ABC