Security, Specialist (JNCIS-SEC) v1.0
Question 1
What are the maximum number of redundancy groups that would be used on a chassis cluster?
- A. The maximum number of redundancy groups use is equal to the number of configured physical interfaces.
- B. The maximum number of redundancy groups use is equal to one more than the number of configured physical interfaces.
- C. The maximum number of redundancy groups use is equal to the number of configured logical interfaces.
- D. The maximum number of redundancy groups use is equal to one more than the number of configured logical interfaces.
Answer : C
Question 2
You want to ensure that any certificates used in your IPsec implementation do not expire while in use by your SRX Series devices.
In this scenario, what must be enabled on your devices?
- A. RSA
- B. TLS
- C. SCEP
- D. CRL
Answer : C
Question 3
What are two valid zones available on an SRX Series device? (Choose two.)
- A. security zones
- B. policy zones
- C. transit zones
- D. functional zones
Answer : AD
Question 4
What are three valid virtual interface types for a vSRX? (Choose three.)
- A. SR-IOV
- B. fxp0
- C. eth0
- D. VMXNET 3
- E. virtio
Answer : ADE
Question 5
Clients at a remote office are accessing a website that is against your company Internet policy. You change the action of the security policy that controls HTTP access from permit to deny on the remote office SRX Series device. After committing the policy change, you notice that new users cannot access the website but users that have existing sessions on the device still have access. You want to block all user sessions immediately.
Which change would you make on the SRX Series device to accomplish this task?
- A. Add the set security flow tcp-session rst-invalidate-session option to the configuration and commit the change.
- B. Add the set security policies policy-rematch parameter to the configuration and commit the change.
- C. Add the security flow tcp-session strict-syn-check option to the configuration and commit the change.
- D. Issue the commit full command from the top of the configuration hierarchy.
Answer : B
Question 6
Screens help prevent which three attack types? (Choose three.)
- A. SYN flood
- B. port scan
- C. NTP amplification
- D. ICMP fragmentation
- E. SQL injection
Answer : ABD
Question 7
Click the Exhibit button.
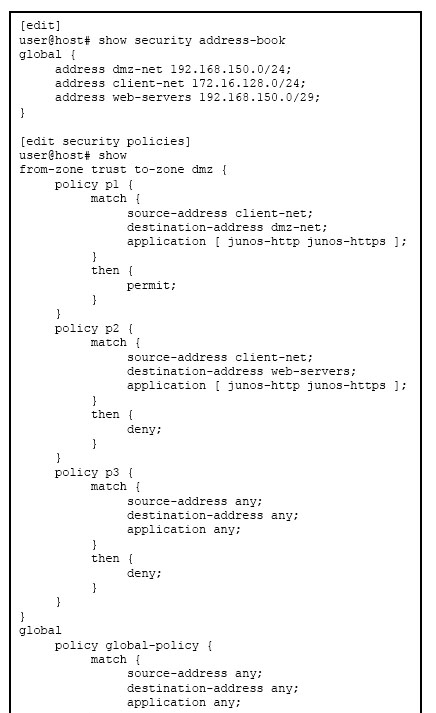
Referring to the exhibit, what will happen if client 172.16.128.50 tries to connect to destination 192.168.150.3 using HTTP?
- A. The client will be denied by policy p2.
- B. The client will be permitted by the global policy.
- C. The client will be permitted by policy p1.
- D. The client will be denied by policy p3.
Answer : C
Question 8
A link from the branch SRX Series device chassis cluster to the Internet requires more bandwidth.
In this scenario, which command would you issue to begin provisioning a second link?
- A. set chassis cluster reth-count 2
- B. set interfaces fab0 fabric-options member-interfaces ge-0/0/1
- C. set interfaces ge-0/0/1 gigether-options redundant-parent reth1
- D. set chassis cluster redundancy-group 1 node 1 priority 1
Answer : C
Question 9
Click to the Exhibit button.
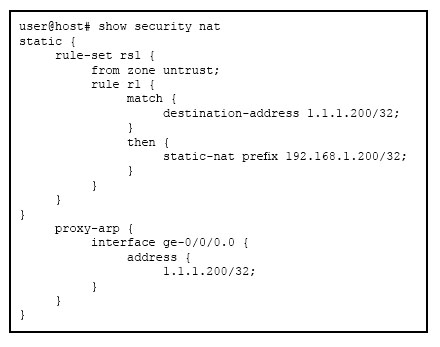
Referring to the exhibit, what does proxy ARP allow?
- A. the internal network to ARP for the internal address of the server
- B. the external network to ARP for the internal address of the server
- C. the internal network to ARP for the public address of the server
- D. the external network to ARP for the public address of the server
Answer : D
Question 10
You are asked to support source NAT for an application that requires that its original source port not be changed.
Which configuration would satisfy the requirement?
- A. Configure a source NAT rule that references an IP address pool with interface proxy ARP enabled.
- B. Configure the egress interface to source NAT fixed-port status.
- C. Configure a source NAT rule that references an IP address pool with the port no-translation parameter enabled.
- D. Configure a source NAT rule that sets the egress interface to the overload status.
Answer : C
Question 11
Click the Exhibit button.
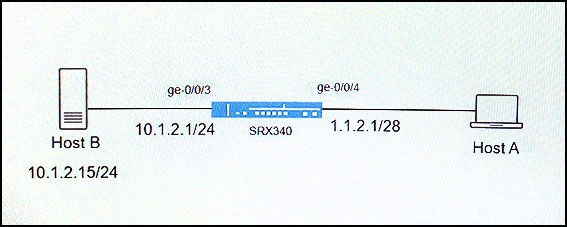
Host A is attempting to connect to Host B using the domain name, which is tied to a public IP address. All attempts to connect to Host B have failed. You have examined the configuration on your SRX340 and determined that a NAT policy is required.
Referring to the exhibit, which two NAT types will allow Host A to connect to Host B? (Choose two.)
- A. source NAT
- B. NAT-T
- C. destination NAT
- D. static NAT
Answer : CD
Question 12
Click the exhibit button.

Referring to the exhibit, which statement is true?
- A. Packets entering the interface are being dropped because of a stateless filter.
- B. Packets entering the interface matching an ALG are getting dropped.
- C. TCP packets entering the interface are failing the TCP sequence check.
- D. Packets entering the interface are getting dropped because the interface is not bound to a zone.
Answer : D
Question 13
Which three elements does AH provide in an IPsec implementation? (Choose three.)
- A. confidentiality
- B. authentication
- C. integrity
- D. availability
- E. replay attack protection
Answer : BCE
Question 14
What is the correct ordering of Junos policy evaluation from first to last?
- A. global policy > zone-based policy > default policy
- B. default policy > zone-based policy > global policy
- C. global policy > default policy > zone-based policy
- D. zone-based policy > global policy > default policy
Answer : D
Question 15
Click the Exhibit button.
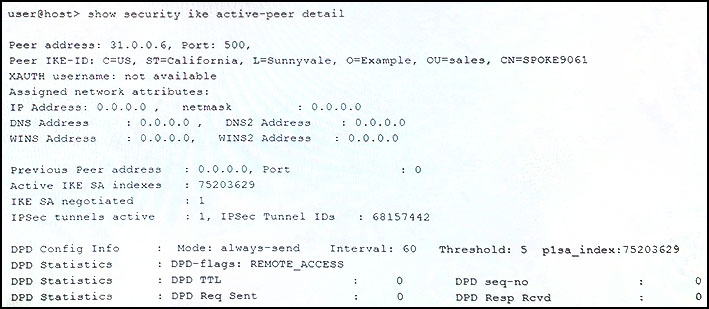
A customer would like to monitor their VPN using dead peer detection.
Referring to the exhibit, for how many minutes was the peer down before the customer was notified?
- A. 5
- B. 3
- C. 4
- D. 2
Answer : A