Juniper Networks Certified Internet Specialist, SEC (JNCIS-SEC) v25.0
Question 1
A user wants to establish an HTTP session to a server behind an SRX device but is being pointed to Web page on the SRX device for additional authentication. Which type of user authentication is configured?
- A. pass-through with Web redirect
- B. WebAuth with HTTP redirect
- C. WebAuth
- D. pass-through
Answer : C
Explanation:
Web authentication is valid for all types of traffic. With Web authentication configured, users must first directly access the Junos security platform using HTTP. The user enters the address or hostname of the device into a Web browser and then receives a prompt for a username and password. If authentication is successful, the user can then access the restricted resource directly. Subsequent traffic from the same source IP address is automatically allowed access to the restricted resource, as long as security policy allows for it.
Question 2
Click the Exhibit button.
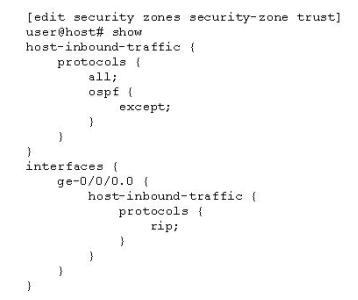
Given the configuration shown in the exhibit, which protocol(s) are allowed to communicate with the device on ge-0/0/0.0?
- A. RIP
- B. OSPF
- C. BGP and RIP
- D. RIP and PIM
Answer : A
Question 3
Which two statements about staticNAT are true? (Choose two.)
- A. Static NAT can only be used with destination NAT.
- B. Static NAT rules take precedence over overlapping dynamic NAT rules.
- C. NAT rules take precedence over overlapping static NAT rules.
- D. A reverse mapping is automatically created.
Answer : BD
Question 4
What is the proper sequence of evaluation for the SurfControl integrated Web filter solution?
- A. whitelists, blacklists, SurfControl categories
- B. blacklists, whitelists, SurfControl categories
- C. SurfControl categories, whitelists, blacklists
- D. SurfControl categories, blacklists, whitelists
Answer : B
Question 5
A system administrator detects thousands of open idle connections from the same source.Which problem can arise from this type of attack?
- A. It enables an attacker to perform an IP sweep of devices.
- B. It enables a hacker to know which operating system the system is running.
- C. It can overflow the session table to its limit, which can result in rejection of legitimate traffic.
- D. It creates a ping of death and can cause the entire network to be infected with a virus.
Answer : C
Question 6
Which three parameters are configured in the IKE policy? (Choose three.)
- A. mode
- B. preshared key
- C. external interface
- D. security proposals
- E. dead peer detection settings
Answer : ABD
Question 7
Which statementis true regarding NAT?
- A. NAT is not supported on SRX Series devices.
- B. NAT requires special hardware on SRX Series devices.
- C. NAT is processed in the control plane.
- D. NAT is processed in the data plane.
Answer : D
Explanation:
The data plane on Junos security platforms, implemented on IOCs, NPCs, and SPCs for high-end devices and on CPU cores and PIMs for branch devices, consists of Junos OS packet-handling modules compounded with a flow engine and session management like that of the ScreenOS software. Intelligent packet processing ensures that one single thread exists for packet flow processing associated with a single flow. Real-time processes enable the Junos OS to perform session-based packet forwarding.
Question 8
You have configured a UTM profile called Block-Spam, which has the appropriate antispam configuration to block undesired spam e-mails. Which configuration would protect an SMTP server in the dmz zone from spam originating in the untrust zone?
- A. set security policies from-zone dmz to-zone untrust policy anti-spam then permit application-services utm-policy Block-Spam
- B. set security policies from-zone untrust to-zone dmz policy anti-spam then permit application-services utm-policy Block-Spam
- C. set security policies from-zone untrust to-zone dmz policy anti-spam then permit application-services anti-spam-policy Block-Spam
- D. set security policies from-zone untrust to-zone dmz policy anti-spam then permit application-services Block-Spam
Answer : B
Question 9
Which two statements regarding external authentication servers for firewall user authentication are true? (Choose two.)
- A. Up to three external authentication server types can be used simultaneously.
- B. Only one external authentication server type can be used simultaneously.
- C. If the local password database is not configured in the authentication order, and the configured authentication server is unreachable, authentication is bypassed.
- D. If the local password database is not configured in the authentication order, and the configured authentication server rejects the authentication request, authentication is rejected.
Answer : BD
Question 10
Which three advanced permit actions within security policiesare valid? (Choose three.)
- A. Mark permitted traffic for firewall user authentication.
- B. Mark permitted traffic for SCREEN options.
- C. Associate permitted traffic with an IPsec tunnel.
- D. Associate permitted traffic with a NAT rule.
- E. Mark permitted traffic for IDP processing.
Answer : ACE
Question 11
Which two statements regarding firewall user authentication client groups are true?
(Choose two.)
- A. A client group is a list of clients associated with a group.
- B. A client group is a list of groups associated with a client.
- C. Client groups are referenced in security policy in the same manner in which individual clients are referenced.
- D. Client groups are used to simplify configuration by enabling firewall user authentication without security policy.
Answer : BC
Question 12
You must configure a SCREEN option that would protect your device from a session table flood. Which configurationmeets this requirement?
- A. [edit security screen] user@host# show ids-option protectFromFlood { icmp { ip-sweep threshold 5000; flood threshold 2000; } }
- B. [edit security screen] user@host# show ids-option protectFromFlood { tcp { syn-flood { attack-threshold 2000; destination-threshold 2000; } } }
- C. [edit security screen] user@host# show ids-option protectFromFlood { udp { flood threshold 5000; } }
- D. [edit security screen] user@host# show ids-option protectFromFlood { limit-session { source-ip-based 1200; destination-ip-based 1200; } }
Answer : D
Question 13
For which network anomaly does Junos provide a SCREEN?
- A. a telnet to port 80
- B. a TCP packet with the SYN and ACK flags set
- C. an SNMP getnext request
- D. an ICMP packet larger than 1024 bytes
Answer : D
Question 14
The Junos OS blocks an HTTP request due to the category of the URL. Which form of Web filtering is being used?
- A. redirect Web filtering
- B. integrated Web filtering
- C. categorized Web filtering
- D. local Web filtering
Answer : B
Question 15
Which type of Web filtering by default builds a cache of server actions associated with each
URL it has checked?
- A. Websense Redirect Web filtering
- B. integrated Web filtering
- C. local Web filtering
- D. enhanced Web filtering
Answer : B