Security, Associate (JNCIA-SEC) v1.0
Question 1
What are two available methods used to authenticate users connecting to an SRX Series device? (Choose two.)
- A. Use Local authentication
- B. Use two-factor authentication
- C. Use Active-Directory authentication
- D. Use RADIUS authentication
Answer : AD
Question 2
Click the Exhibit button.
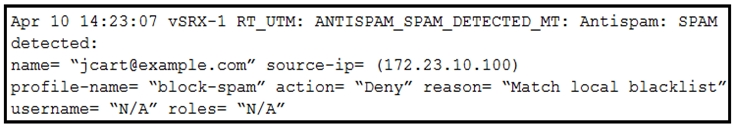
You have configured antispam to allow e-mails from example.com; however, reviewing the logs you see that [email protected] is blocked.
Referring to the exhibit, what are two ways to solve this problem? (Choose two.)
- A. Add [email protected] to the profile antispam address whitelist.
- B. Verify connectivity with the SBL server.
- C. Delete [email protected] from the profile antispam address whitelist.
- D. Delete [email protected] from the profile antispam address blacklist.
Answer : AD
Question 3
In which order are NAT types evaluated?
- A. reverse static > source > static > destination
- B. source > destination > static > reverse static
- C. static > destination > reverse static > source
- D. destination > static > reverse static > source
Answer : C
Question 4
Click the Exhibit button.
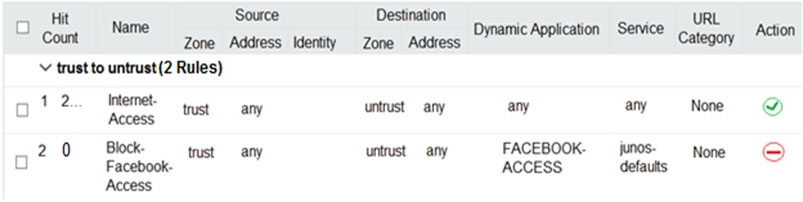
Users should not have access to Facebook, however, a recent examination of the security logs show that users are accessing Facebook.
Referring to the exhibit, what should you do to solve this problem?
- A. Change the source address for the Block-Facebook-Access rule to the prefix of the users.
- B. Change the Block-Facebook-Access rule from a zone policy to a global policy.
- C. Move the Block-Facebook-Access rule before the Internet-Access rule.
- D. Change the Internet-Access rule from a zone policy to a global policy.
Answer : C
Question 5
Which security feature is applied to traffic on an SRX Series device when the device is running in packet mode?
- A. ALGs
- B. Sky ATP
- C. firewall filters
- D. unified policies
Answer : A
Question 6
Firewall filters define which type of security?
- A. stateful
- B. stateless
- C. NGFW
- D. dynamic enforcement
Answer : B
Question 7
Users in your network are downloading files with file extensions that you consider to be unsafe for your network. You must prevent files with specific file extensions from entering your network.
Which UTM feature should be enabled on an SRX Series device to accomplish this task?
- A. content filtering
- B. antispam
- C. Web filtering
- D. URL filtering
Answer : A
Question 8
You want to automatically generate the encryption and authentication keys during IPsec VPN tunnel establishment.
What would be used to accomplish this task?
- A. main mode
- B. aggressive mode
- C. IPsec
- D. Diffie-Hellman
Answer : D
Question 9
Which two statements about security policy processing on SRX Series devices are true? (Choose two.)
- A. Zone-based security policies are processed before global policies.
- B. Traffic matching a global policy cannot be processed against a firewall filter.
- C. Traffic matching a zone-based policy is not processed against global policies.
- D. Zone-based security policies are processed after global policies.
Answer : AC
Question 10
You are asked to run a report to find the top talkers on your network in the past 48 hours.
In this scenario, the report will be in which format when the J-Web UI delivers it to you?
- A. JPG
- B. HTML
- C. xls
- D. CSV
Answer : B
Question 11
Which UTM feature should you use to protect users from visiting certain blacklisted websites?
- A. content filtering
- B. Web filtering
- C. antivirus
- D. antispam
Answer : B
Question 12
Which two statements are true about security policies in the factory-default configuration of an SRX340? (Choose two.)
- A. All traffic from the trust zone to the untrust zone is allowed.
- B. All interzone traffic is denied.
- C. All interzone traffic is allowed.
- D. All traffic from the untrust zone to the trust zone is denied.
Answer : AD
Question 13
Which two actions are performed on an incoming packet matching an existing session? (Choose two.)
- A. security policy evaluation
- B. service ALG processing
- C. screens processing
- D. zones processing
Answer : BC
Question 14
On an SRX Series device, how should you configure your IKE gateway if the remote endpoint is a branch office using a dynamic IP address?
- A. Configure the IPsec policy to use MD5 authentication.
- B. Configure the IKE policy to use aggressive mode.
- C. Configure the IPsec policy to use aggressive mode.
- D. Configure the IKE policy to use a static IP address.
Answer : B
Question 15
What must you do first to use the Monitor/Events workspace in the J-Web interface?
- A. You must enable security logging that uses the TLS transport mode.
- B. You must enable security logging that uses the SD-Syslog format.
- C. You must enable stream mode security logging on the SRX Series device.
- D. You must enable event mode security logging on the SRX Series device.
Answer : B