Security Design, Specialist (JNCDS-SEC) v1.0
Question 1
You are required to design a university network to meet the conditions shown below.
✑ Users connected to the university network should be able to access the Internet and the research department lab network.
✑ The research department lab network should not be able to reach the Internet.
Which three actions satisfy the design requirements? (Choose three.)
- A. Use a global permit policy for Internet traffic
- B. Use a global deny security policy for the research lab
- C. Use separate security zones for each department
- D. Use the default deny security policy for the research lab
- E. Use a static NAT rule between the internal zones for the research lab
Answer : ACD
Question 2
Click the Exhibit button.
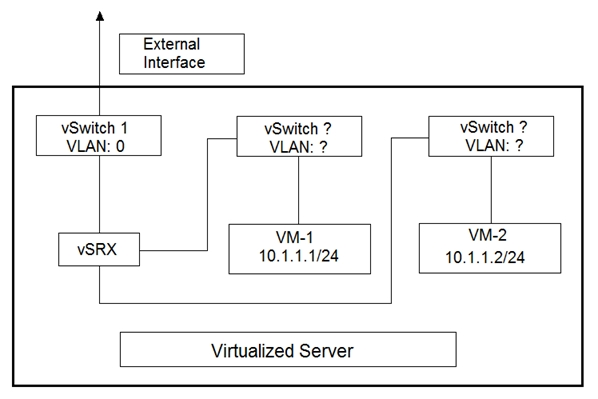
You are designing the virtualized server deployment shown in the exhibit in your data center. The vSRX device is acting as a Layer 2 firewall and the two VMs must communicate through the vSRX device.
Which two actions must you perform to accomplish this task? (Choose two.)
- A. Place both VMs in the same vSwitch
- B. Place both VMs in the same VLAN
- C. Place both VMs in different vSwitches
- D. Place both VMs in different VLANs
Answer : BC
Question 3
Which two protocols are supported natively by the Junos automation stack? (Choose two.)
- A. NETCONF
- B. PyEZ
- C. Jenkins
- D. CIP
Answer : AB
Question 4
Which solution centralizes the management of security devices in your data center?
- A. Juniper Networks Secure Analytics
- B. J-Web
- C. Junos Space Security Director
- D. Junos CLI
Answer : C
Question 5
Which solution provides a certificate based on user identity for network access?
- A. network access control
- B. user firewall
- C. IP filtering
- D. MAC filtering
Answer : A
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-user-auth-control-network-access.html
Question 6
You are concerned about users downloading malicious attachments at work while using encrypted Web mail. You want to block these malicious files using your
SRX Series device.
In this scenario, which two features should you use? (Choose two.)
- A. SSL reverse proxy
- B. SSL forward proxy
- C. Sky ATP SMTP scanning
- D. Sky ATP HTTP scanning
Answer : BC
Question 7
You are designing an enterprise WAN network that must connect multiple sites. You must provide a design proposal for the security elements needed to encrypt traffic between the remote sites.
Which feature will secure the traffic?
- A. BFD
- B. OSPF
- C. GRE
- D. IPsec
Answer : D
Question 8
You must design a small branch office firewall solution that provides application usage statistics.
In this scenario, which feature would accomplish this task?
- A. AppFW
- B. AppTrack
- C. UTM
- D. AppQoS
Answer : B
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-application-tracking.html
Question 9
You are designing a corporate WAN using SRX Series devices as a combined firewall and router at each site.
Regarding packet-mode and flow-mode operations in this scenario, which statement is true?
- A. Packet-mode on SRX Series devices is required for deep packet inspection
- B. Packet-mode is only supported on high-end SRX Series devices
- C. An SRX Series device in flow-mode cannot forward packet-mode traffic
- D. Flow-mode on SRX Series devices is required for security services
Answer : D
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-srx-devices-processing-overview.xml.html
Question 10
You are asked to include anti-malware features into an existing network design. Traffic from the infected machines must be moved to a quarantined VLAN.
Which product will provide this segregation?
- A. screens
- B. Sky ATP
- C. unified threat management
- D. Software Defined Secure Network
Answer : B
Reference:
https://www.juniper.net/documentation/en_US/release-independent/sky-atp/information-products/pathway-pages/sky-atp-admin-guide.pdf
Question 11
Policy Enforcer provides which benefit?
- A. log management
- B. command and control protection
- C. centralized management of security devices
- D. IPsec encryption
Answer : C
Question 12
Which statement about IPsec tunnels is true?
- A. They are used to provide in-depth packet inspection for traffic leaving your network
- B. They are used to prevent routing loops in a Layer 2 environment
- C. They are used to secure and encrypt traffic between tunnel endpoints
- D. They are used to combine multiple interfaces into a single bundle
Answer : C
Question 13
You work for an ISP that wants to implement remote-triggered black hole (RTBH) filters.
What are three considerations in this scenario? (Choose three.)
- A. Source RTBH can block legitimate traffic on the network
- B. BGP FlowSpec improves the RTBH model by implementing dynamic firewall filters
- C. Source RTBH requires uRPF to be implemented on the service providerג€™s network core
- D. Destination RTBH requires uRPF to be implemented on the service providerג€™s network edge
- E. Destination RTBH essentially completes the attack on the victimג€™s IP
Answer : ABC
Question 14
You are designing a DDoS solution for an ISP using BGP FlowSpec. You want to ensure that BGP FlowSpec does not overwhelm the ISPג€™s edge routers.
Which two requirements should be included in your design? (Choose two.)
- A. Specify a maximum number BGP FlowSpec prefixes per neighbor
- B. Implement a route policy to limit advertised routes to /24 subnets
- C. Implement a route policy to limit advertised routes to any public IP space
- D. Specify a maximum number of BGP FlowSpec prefixes per device
Answer : CD
Reference:
https://www.juniper.net/documentation/en_US/day-one-books/DO_BGP_FLowspec.pdf
Question 15
You are designing an SDSN security solution for a new campus network. The network will consist of Juniper Networks Policy Enforcer, Juniper Networks switches, third-party switches, and SRX Series devices. The switches and the SRX Series devices will be used as security enforcement points. The design must be able to change the VLAN mapping of the switch port of a user that is already authenticated to the network in the event that the end user device becomes compromised.
Which component satisfies this requirement?
- A. certificate server
- B. RADIUS server
- C. Security Director
- D. DHCP server
Answer : C