Security Design, Specialist (JNCDS-SEC) v7.0
Question 1
Which three statements about Sky Advanced Threat Prevention are true? (Choose three.)
- A. Dynamic analysis involves unique deception techniques.
- B. Machine-learning algorithms are enabled to adapt to and identify new malware.
- C. Rapid cache lookups are used to quickly identify known files.
- D. Files are flagged for next-day analysis for certain malware types.
- E. It uses a single, best-in-class antivirus engine.
Answer : ABC
Question 2
You ate asked 10 design security policies for your corporate network where policy based
VPNs will be used In this scenario, which three statements for a traffic match are true?
(Choose three)
- A. The policy action is always permit.
- B. A VPN tunnel is indirectly referenced by a route that points to a specific tunnel interface.
- C. The security policy sets up the iPsec tunnel.
- D. Tunnels are generated when traffic matches a policy.
- E. The policy refers to the remote IKE gateway.
Answer : ABC
Question 3
You are designing a Log Director deployment that must be able to handle 9,500 sustained events per second In this scenario, what is the minimum deployment solution?
- A. one JA2500 as a Log Collector
- B. three JA2500s as Log Collectors and one JA2500 as a Log Concentrator
- C. two JA2500s as Log Collectors and one JA2500 as a Log Concentrator
- D. one JA2500 as a Log Collector and one JA2500 as a Log Concentrator
Answer : C
Question 4
Click the Exhibit button.
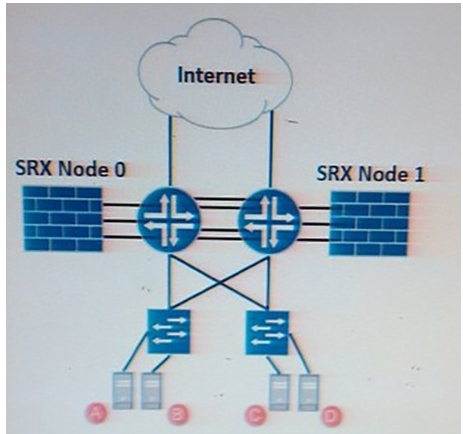
The data center shown in the exhibit is running an active/active SRX Series chassis cluster and an active/active network infrastructure Customer A needs to communicate with customer D, and customer B needs (o communicate with customer C
In this scenario Which two steps avoid Z-mode traffic? (Choose two)
- A. Associate customer A and customer D network segments in different redundancy groups.
- B. Associate customer A and customer D network segments in the same redundancy groups
- C. Associate customer B and customer C network segments in me same redundancy groups.
- D. Associate customer B and customer C network segments in different redundancy groups.
Answer : BC
Question 5
Your network design consists of two chassis clusters with the same cluster ID The reth0 interfaces of each cluster are connected to the same Layer 2 network In this scenario, what will ensure uninterrupted traffic?
- A. One of the clusters should not use reth0.
- B. One of the clusters should have a different number of physical interfaces in reth0.
- C. One of the clusters should disable LACP on all redundant interfaces
- D. One of the clusters should have reth0 configured under different redundancy groups
Answer : D
Question 6
You are designing an enterprise WAN network that must connect multiple sites. You must provide a design proposal for the security elements needed to encrypt traffic between the remote sites
Which feature will secure the traffic?
- A. BFD
- B. OSPF
- C. GRE
- D. IPsec
Answer : D
Question 7
Your customer is in the design stage for a new data center They have historically used the
SRX5600 To improve the security of the data center, you will be suggesting they deploy vSRXs and hardware-based firewalls.
- A. The SRX5600 does not support IPS.
- B. The ability to secure traffic between VMs without leaving the physical server hardware.
- C. vSRX can reside anywhere in the virtual environment.
- D. A vSRX has greater throughput than an SRX5600
Answer : BC
Question 8
Which three actions are part of an in-depth network defense strategy1? (Choose three )
- A. providing data modeling
- B. auditing for suspicious events
- C. providing security awareness training
- D. providing least privileged network access
- E. installing multiple antivirus solutions on desktop computers
Answer : B,C,D
Question 9
Which three functions are licensed UTM features? (Choose three)
- A. denial-of-service protection
- B. anti spam
- C. enhanced Web filtering
- D. intrusion prevention system
- E. antivirus
Answer : B,C,E
Question 10
Due to changes in security requirements you must place a firewall between an existing
Web server (arm and a database server farm residing in the same subnet In this scenario, why would you choose transparent mode as your operating mode?
- A. Transparent mode does not require zones to be configured.
- B. Transparent mode can be implemented with no changes to the current IP addresses.
- C. Transparent mode policies can be enforced based on MAC address ranges.
- D. Transparent mode allows only IP packets to pass through the security policies.
Answer : B
Question 11
What are the three activities in the reconnaissance phase of an attack"? (Choose three)
- A. Determine the device OS
- B. Scan for devices and ports to exploit
- C. Install malware.
- D. Propagate the virus to servers and workstations
- E. Map the network
Answer : A,B,E
Question 12
You are preparing lot the initial deployment of 100 SRX Series devices, and you want to leverage the auto installation feature Which three prerequisites are required before you begin this task? (Choose three)
- A. Create a device-specific or default configuration file, and store it on a TPTP server in the network.
- B. Confirm reach ability to an active Contrail Controller within the same Layer 2 domain.
- C. Log in to the SRX Series device as the root user and confirm the BASH shell connectivity.
- D. Physically attach the SRX Series devices to the network using a valid interface Configure a DHCP server
- E. on your network to meet your network requirements.
Answer : A,D,E
Question 13
As part of your branch office security design, you are asked to include the necessary features to address these requirements;
-stop spam and phishing,
-stop viruses, Trojans, and spyware,
-control website access, and -control content
Which security feature set meets these requirements?
- A. unified threat management
- B. intrusion prevention system
- C. stateless firewall filters
- D. services offloading
Answer : A
Explanation:
With UTM, you can Implement a comprehensive set of security features that include antispam, antivirus, Web filtering, and content filtering protection.
Question 14
Your customer is planning to secure a data center with web servers reachable through two
ISP connections terminating on each node of an active/passive SRX Series chassis cluster.
ISP-1 Is the preferred connection because it provides higher bandwidth than ISP-2.
Which two must you include in your design proposal to meet this requirement (Choose two)
- A. Use conditional BGP advertisements and use Interface monitoring for both ISP Interfaces.
- B. Use static routing and use interface monitoring for both ISP interfaces.
- C. Ensure that both ISP interfaces are in the same zone and use interface monitoring.
- D. Ensure that both the ISP interfaces are in different zones and use interface monitoring.
Answer : A,D
Question 15
Your company must enable high-speed Layer 2 connectivity between two data centers connected by private fiber Your security policy mandates that all company data is encrypted between sites
Which technology would you use to meet these requirements'?
- A. iPsec
- B. MACsec
- C. L2PT
- D. VXLAN
Answer : B