HCNA-Security-CBSN (Huawei Certified Network Associate - Constructing Basic Security Network) v1.0
Question 1
What do VLAN port types include? (Choose three.)
- A. Access Port
- B. Trunk port
- C. Hybrid port
- D. Ethernet port
Answer : ABC
Question 2
Which scenarios does IPSec WEB configuration wizard not support?
- A. Gateway to Gateway
- B. Center Gateway
- C. Branch Gateway
- D. Host and Host
Answer : D
Question 3
Which of the Policy Center functional areas is wrong?
- A. Pre-authentication domain refers to the client through the identity authentication before access to the area
- B. Post-authentication domain refers to the client can access through the security certification area
- C. Isolation domain refers to the client after authenticated must have access to the area
- D. Isolation domain refers to the client security authentication failed the required access area
Answer : C
Question 4
In the firewall, detect ftp command to set in which mode? (Choose two.)
- A. System Model
- B. Interface Mode
- C. Domain Model
- D. Inter-Domain mode
Answer : CD
Question 5
In most scenarios, NAT Inbound is used to the enterprise private network users to access the Internet scenario.
- A. True
- B. False
Answer : B
Question 6
What are common hash algorithms? (Choose two.)
- A. DES
- B. AES
- C. MD5
- D. SHA-1
Answer : CD
Question 7
In the environment of GRE configuration, which of the following statements are true? (Choose three.)
- A. In order to make the ends of the tunnel forward data packets normally, the devices of both ends are configured routing which through the Tunnel interface
- B. If both ends enable the configuration of keyword verification, the keyword must be the same
- C. When the local device send data packets, by identifying the protocol field value of IP header for GRE to determine whether send the data packet to GRE module for processing
- D. When the opposite end receives data packets, by identifying the protocol field value of IP header for GRE to determine whether send the data packet to GRE module for processing
Answer : ABD
Question 8
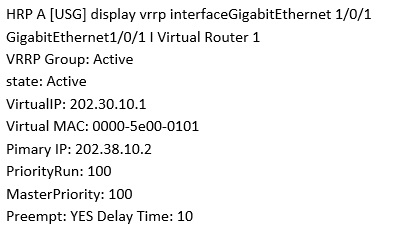
Execute the command on the Firewall and display the above information.
Which of the following description is correct? (Choose two.)
- A. This Firewall VGMP group status is Active
- B. The virtual IP address of the firewall G1/0/1 interface is 202.30.10.2
- C. The priority of the VRRP backup group of the firewall VRID 1 is 100
- D. If the master device fails, it will not switch
Answer : AC
Question 9
Which of the following are the key features of the state inspection firewall include?
- A. The processing speed is slow
- B. Follow-up packet processing performance is excellent
- C. Can only detect network layer
- D. Do the packet filtering detection to each packet
Answer : B
Question 10
In IPSEC VPN, which of the following scenarios can be applied by tunnel mode?
- A. between the host and the host
- B. between hosts and security gateways
- C. between security gateways
- D. between tunnel mode and transport mode
Answer : C
Question 11
Which of the following statement about the NAT is wrong?
- A. NAT technology can effectively hide the costs of the LAN; it is an effective network security protection technology
- B. Address Translation can follow the needs of users, providing FTP, WWW, Telnet and other services outside the LAN
- C. Some application layer protocols carry IP address information in the data, but also modify the IP address information in the data of the upper layer when they are as NAT
- D. For some non-TCP, UDP protocols (such as ICMP, PPTP), unable to do the NAT translation
Answer : D
Question 12
As shown, when configuring the point-to-multipoint scenarios, the headquarters network segment is 10.1.1.0/24, the segment of branch 1 is 10.1.2.0/24, of branch
2 is 10.1.3.0/24.
About the protected data flow configuration which defined by headquarters and branch offices, which of the following combinations can be the full matched requirements?
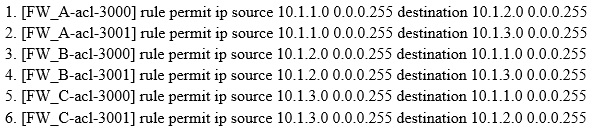
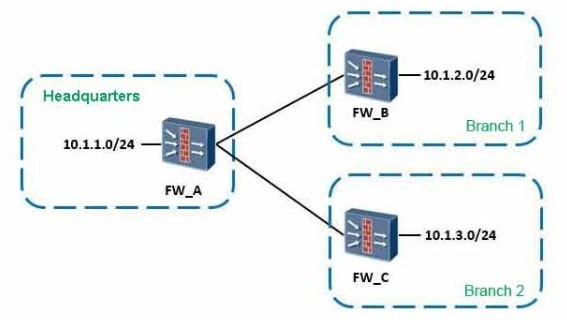
- A. 1 2
- B. 1 2 3 5
- C. 1 2 4 6
- D. 3 4 5 6
Answer : B
Question 13
Which of the following addresses can be used for web management address of USG product? (Choose three.)
- A. Interface Address
- B. Sub-interface address
- C. Slave IP address of the interface
- D. AUX interface address
Answer : ABC
Question 14
Which of the following statement about Internet user group management is wrong?
- A. Each user group can include multiple users and user group
- B. Each user group can belong to more than one parent user group
- C. There is a default user group in the system; the user group is also the default authentication domain
- D. Each user belongs to at least one user group, who can also belong to multiple user groups
Answer : B
Question 15
In SSL handshake protocol, what is the role of Server Key Exchange message?
- A. server key exchange message indicates that the server has finished sending all the information
- B. in the server key exchange message, it contains set of parameters required for completing key exchange
- C. it contains an X.509 certificate in server key exchange message, the public key is contained in the certificate, which is issued to the client to verify signatures or to encrypt messages when key exchange
- D. in the server key exchange message, it contains the negotiated CipherSuite which is copied to the state of the current connection
Answer : B