GIAC Penetration Tester v8.0
Question 1
You have been contracted to map me network and try to compromise the servers for a client. Which of the following would be an example of scope creep' with respect to this penetration testing project?
- A. Disclosing information forbidden in the NDA
- B. Compromising a server then escalating privileges
- C. Being asked to compromise workstations
- D. Scanning network systems slowly so you are not detected
Answer : B
Question 2
Which of the following modes describes a wireless interface that is configured to passively grab wireless frames from one wireless channel and pass them to the operating system?
- A. Monitor Mode
- B. Promiscuous Mode
- C. Managed Mode
- D. Master Mode
Answer : C
Reference:
http://www.willhackforsushi.com/books/377_eth_2e_06.pdf
Question 3
Your company has decided that the risk of performing a penetration test Is too great. You would like to figure out other ways to find vulnerabilities on their systems, which of the following is MOST likely to be a valid alternative?
- A. Network scope Analysis
- B. Baseline Data Reviews
- C. Patch Policy Review
- D. Configuration Reviews
Answer : A
Question 4
A customer has asked for a scan or vulnerable SSH servers. What is the penetration tester attempting to accomplish using the following Nmap command?
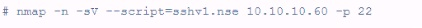
- A. Checking operating system version
- B. Running an exploit against the target
- C. Checking configuration
- D. Checking protocol version
Answer : D
Question 5
All of the following are advantages of using the Metasploitpriv module for dumping hashes from a local Windows machine EXCEPT:
- A. Doesn't require SMB or NetBIOS access to the target machine
- B. Can run inside of a process owned by any user
- C. Provides less evidence for forensics Investigators to recover
- D. LSASS related reboot problems aren't an Issue
Answer : B
Reference:
http://www.vita.virginia.gov/uploadedFiles/VITA_Main_Public/Security/Meetings/ISOAG/20
12/2012_Jan_ISOAG.pdf
Question 6
During a penetration test we determine that TCP port 22 is listening on a target host.
Knowing that SSHD is the typical service that listens on that port we attempt to validate that assumption with an SSH client but our effort Is unsuccessful. It turns out that it is actually an Apache webserver listening on the port, which type of scan would have helped us to determine what service was listening on port 22?
- A. Version scanning
- B. Port scanning
- C. Network sweeping
- D. OS fingerprinting
Answer : C
Question 7
A junior penetration tester at your firm is using a non-transparent proxy for the first time to test a web server. He sees the web site In his browser but nothing shows up In the proxy.
He tells you that he just installed the non-transparent proxy on his computer and didn't change any defaults. After verifying the proxy is running, you ask him to open up his browser configuration, as shown in the figure, which of the following recommendations will correctly allow him to use the transparent proxy with his browser?
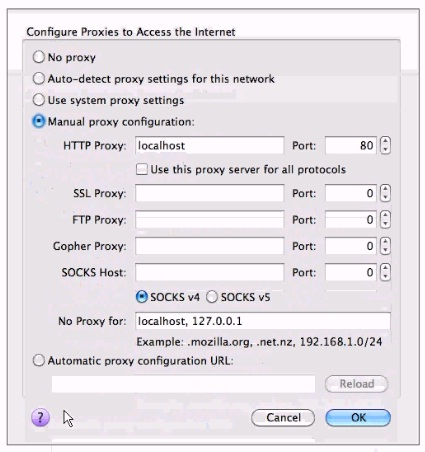
- A. He should change the PORT: value to match the port used by the non-transparentproxy.
- B. He should select the checkbox "use this proxy server for all protocols" for theproxy to function correctly.
- C. He should change the HTTP PROXY value to 127.0.0.1 since the non-transparentproxy is running on the same machine as the browser.
- D. He should select NO PROXY instead of MANUAL PROXY CONFIGURATION as thissetting is only necessary to access the Internet behind protected networks.
Answer : C
Question 8
You have been contracted to perform a black box pen test against the Internet facing servers for a company. They want to know, with a high level of confidence, if their servers are vulnerable to external attacks. Your contract states that you can use all tools available to you to pen test the systems. What course of action would you use to generate a report with the lowest false positive rate?
- A. Use a port scanner to find open service ports and generate a report listing allvulnerabilities associated with those listening services.
- B. Use a vulnerability or port scanner to find listening services and then try to exploitthose services.
- C. Use a vulnerability scanner to generate a report of vulnerable services.
- D. Log into the system and record the patch levels of each service then generate areport that lists known vulnerabilities for all the running services.
Answer : B
Question 9
Analyze the command output below. Given this information, which is the appropriate next step for the tester?
Starting Nmap4.53 (hnp://insecure.org I at2010-09-30 19:13 EDT interesting ports on
192.163.116.101:
PORT STATE SERVICE -
130/tcp filtered cisco-fna
131/tcp filtered cisco-tna
132/tcp filtered cisco-sys
133/tcp filtered statsrv
134/tcp filtered Ingres-net
135/tcp filtered msrpc
136/tcp filtered profile
137/tcp filtered netbios-ns
138/tcp filtered netbios-dgm
139/tcp open netbios-ssn
140/tcp filtered emfis-data
MAC Address: 00:30:1&:B8:14:8B (Shuttle)
warning: OSS can results may be unreliable because we could not find at least l open and l closed port
Device type, general purpose -
Running: Microsoft Windows XP -
OS details: Microsoft Windows XP SP2
Network Distance : 1 hop -
Nmap done: I IP address (I host up) scanned in l .263 seconds
- A. Determine the MAC address of the scanned host.
- B. Send a single SYN packet to port 139/tcp on the host.
- C. Send spoofed packets to attempt to evade any firewall
- D. Request a list of shares from the scanned host.
Answer : B
Question 10
What problem occurs when executing the following command from within a netcat raw shell? sudo cat /etc/shadow
- A. Sudo does not work at all from a shell
- B. Sudo works fine if the user and command are both in the /etc/sudoers file
- C. The display blanks after typing the sudo command
- D. You will not be able to type the password at the password prompt
Answer : A
Question 11
Which of the following file transfer programs will automatically convert end-of line characters between different platforms when placed in ASCII Mode?
- A. ftp
- B. nc
- C. tftp
- D. scp
Answer : A
Reference:
https://wiki.filezilla-project.org/Data_Type
Question 12
What is the most likely cause of the responses on lines 10 and 11 of the output below?
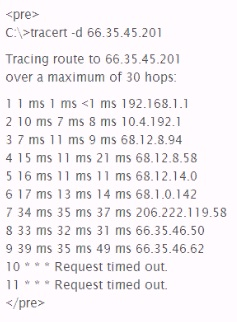
- A. The device at hop 10 silently drops UDP packets with a high destination port.
- B. The device at hop 10 is down and not forwarding any requests at all.
- C. The host running the tracer utility lost its network connection during the scan
- D. The devices at hops 10 and II did not return an "ICMP TTL Exceeded in Transit" message.
Answer : D
Question 13
Which of the following is the feature that separates the use of Rainbow Tables from other applications such as Cain or John the Ripper?
- A. Salts are used to create massive password databases for comparison.
- B. Applications take advantage of 64-bit CPU processor and multithread the crackingprocess.
- C. Data Is aligned efficiently in the rainbow tables making the search process quicker
- D. Raw hashed passwords are compared to pre-calculated hash tables.
Answer : B
Question 14
You have compromised a Windows workstation using Metasploit and have injected the
Meterpreter payload into the smss process. You want to dump the SAM database of the remote system so you can crack it offline. Which Meterpreter module would you need to load in addition to the defaults so that you can accomplish this?
- A. Core
- B. Priv
- C. Stdapi
- D. Hashdump
Answer : C
Question 15
Analyze the command output below. What information can the tester infer directly from the information shown?
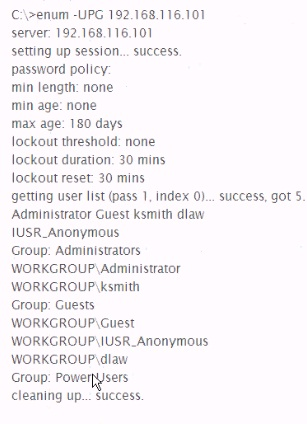
- A. The administrator account has no password
- B. Null sessions are enabled on the target
- C. The target host is running Linux with Samba services
- D. Account lockouts must be reset by the Administrator
Answer : C