GIACCertified Forensics Analyst v6.0
Question 1
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate the BlackBerry, which is suspected to be used to hide some important information. Which of the following is the first step taken to preserve the information in forensic investigation of the BlackBerry?
- A. Keep BlackBerry in 'ON' state.
- B. Remove the storage media.
- C. Eliminate the ability of the device to receive the push data.
- D. Turn off the BlackBerry.
Answer : C
Question 2
You are reviewing a Service Level Agreement between your company and a Web development vendor.
Which of the following are security requirements you should look for in this SLA?
Each correct answer represents a complete solution. Choose all that apply.
- A. Time to respond to bug reports
- B. Encryption standards
- C. Security Monitoring
- D. Guarantees on known security flaws
Answer : A,B,C,D
Question 3
Mark works as a Network Administrator for Net Perfect Inc. The company has a Linux- based network. Mark installs a Checkpoint Firewall NGX on a SecurePlatform device. He performs a scheduled backup of his system settings and products configuration. Where are these backup files stored?
Each correct answer represents a complete solution. Choose all that apply.
- A. SCP
- B. TFTP
- C. Locally on the SecurePlatform machine hard drive
- D. On a PC in a file named userC
Answer : ABC
Question 4
Which of the following tools can be used by a user to hide his identity?
Each correct answer represents a complete solution. Choose all that apply.
- A. Proxy server
- B. Anonymizer
- C. Rootkit
- D. IPchains
- E. War dialer
Answer : ABD
Question 5
Which of the following file systems is designed by Sun Microsystems?
- A. NTFS
- B. CIFS
- C. ext2
- D. ZFS
Answer : D
Question 6
Which of the following standard file formats is used by Apple's iPod to store contact information?
- A. HFS+
- B. hCard
- C. vCard
- D. FAT32
Answer : C
Question 7
Which of the following is the correct order of digital investigations Standard Operating
Procedure (SOP)?
- A. Initial analysis, request for service, data collection, data analysis, data reporting
- B. Initial analysis, request for service, data collection, data reporting, data analysis
- C. Request for service, initial analysis, data collection, data reporting, data analysis
- D. Request for service, initial analysis, data collection, data analysis, data reporting
Answer : D
Question 8
Which of the following types of computers is used for attracting potential intruders?
- A. Bastion host
- B. Data pot
- C. Files pot
- D. Honey pot
Answer : D
Question 9
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He receives the following e-mail:

The e-mail that John has received is an example of __________.
- A. Virus hoaxes
- B. Spambots
- C. Social engineering attacks
- D. Chain letters
Answer : D
Question 10
You work as a Network Administrator for Peach Tree Inc. The company currently has a
FAT-based Windows NT network. All client computers run Windows 98. The management wants all client computers to be able to boot in Windows XP Professional. You want to accomplish the following goals:
The file system should support file compression and file level security.
All the existing data and files can be used by the new file system.
Users should be able to dual-boot their computers.
You take the following steps to accomplish these goals:
Convert the FAT file system to NTFS using the CONVERT utility.
Install Windows XP and choose to upgrade the existing operating system during setup.
Which of the following goals will you be able to accomplish?
Each correct answer represents a complete solution. Choose all that apply.
- A. The file system supports file compression and file level security.
- B. All the existing data and files can be used by the new file system.
- C. Users are able to dual-boot their computers.
- D. None of the goals are accomplished.
Answer : AB
Question 11
Maria works as a professional Ethical Hacker. She recently got a project to test the security of www.we-are-secure.com. Arrange the three pre-test phases of the attack to test the security of weare-secure.
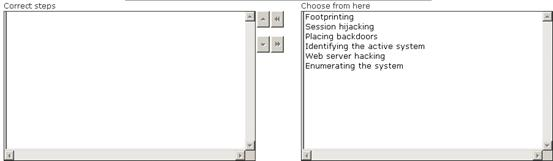
- A.
Answer : A
Question 12
Which of the following tools can be used to perform a whois query?
Each correct answer represents a complete solution. Choose all that apply.
- A. Sam Spade
- B. SuperScan
- C. Traceroute
- D. WsPingPro
Answer : ABD
Question 13
Which of the following IP addresses are private addresses?
Each correct answer represents a complete solution. Choose all that apply.
- A. 19.3.22.17
- B. 192.168.15.2
- C. 192.166.54.32
- D. 10.0.0.3
Answer : BD
Question 14
You work as the Network Administrator for McNeil Inc. The company has a Unix-based network. You want to fix partitions on a hard drive. Which of the following Unix commands can you use to accomplish the task?
- A. fdformat
- B. exportfs
- C. fsck
- D. fdisk
Answer : D
Question 15
Which of the following Acts enacted in United States allows the FBI to issue National
Security Letters (NSLs) to Internet service providers (ISPs) ordering them to disclose records about their customers?
- A. Wiretap Act
- B. Computer Fraud and Abuse Act
- C. Economic Espionage Act of 1996
- D. Electronic Communications Privacy Act of 1986
Answer : D