CompTIA Strata IT Fundamentals v6.0
Question 1
Which of the following devices contains no moving parts and stores data in a digital format?
- A. Solid-state drive
- B. Cartridgetape drive
- C. Floppy disk drive
- D. Hard disk drive
Answer : A
Explanation:
Solid-state drive contains no moving parts and stores data in a digital format.
A solid-state drive (SSD) is a data storage device that uses solid-state memory to store persistentdata. An SSD emulates a hard disk drive interface, thus easily replacing it in most applications. It is also known as solid-state hard disk drive. SSDs have no moving parts; hence, they are less fragile and silent than hard disks. As there are no mechanical delays,
SSDs usually enjoy low access time and latency. An SSD using SRAM or DRAM (instead of flash memory) is often called a RAM-drive, which should not be confused with a RAM disk.
Answer options D, C, and B are incorrect. Hard disk drive, floppy diskdrive, and cartridge tape drive contain moving parts.
Reference. "http.//en.wikipedia.org/wiki/Computer_hardware"
Question 2
What is the difference between the USB 2.0 and IEEE1394 bus standards?
- A. IEEE 1394 is faster than USB 2.0.
- B. IEEE 1394 supports hot swapping.
- C. IEEE 1394 is slower than USB 2.0.
- D. USB 2.0 supports Plug and Play feature.
Answer : C
Explanation:
IEEE is a standard that defines the specifications for highspeed serial bus. IEEE 1394 is also known as Firewire. Like USB, IEEE 1394 also supports hot swapping and Plug and
Play feature. However, an -
IEEE 1394 bus runs at a speed of 400 Mbps, which is slower than that of a USB 2.0 bus.
The IEEE -
1394 standard defines two types of connectors, 4-pin and 6-pin. 6-pin connectors are commonly used on PC adapters. 4-pin connectors are used on Macintosh systems.
What is USB?
Universal Serial Bus (USB) is a high speed bus standard developed by Compaq, IBM,
DEC, Intel, Microsoft, NEC, and Northern Telecom. It provides the Plug and Play capability of Windows to external hardware devices. USB supports hot plugging, which means that a
USB device can be installed or removed while the computer is running. A single USB port can beused to connect up to
127 peripheral devices, such as CD-ROM drives, tape drives, keyboards, scanners etc.
USB 1.1 has a maximum data transfer rate of 12 Mbps, whereas USB 2.0 has a maximum data transfer rate of
480 Mbps. USB 2.0 is fully backward compatible with USB 1.1.
Question 3
You are selecting RAM for a new PC. You are very concerned about making sure errors are handled. Which of the following types of RAM should you select?
- A. RamBus
- B. Non Parity RAM
- C. ECC RAM
- D. Logic Parity RAM
Answer : C
Explanation:
Parity RAM can indeed handle error correction, however is not supported in most new computers.
ECC is supported. What is ECC memory module?
An Error Correcting Code (ECC) memory moduledetects and corrects single-bit errors in memory. It helps a computer to continue working without interruption and data corruption.
Although ECC can detect both single-bit and double-bit errors, it can only correct single-bit errors. As most memory errorsare of a single-bit nature, ECC provides high system reliability and attendant availability. An ECC-based computer is a good choice for servers.
Answer option B is incorrect. Non parity RAM offers no error checking at all. Answer option
D is incorrect. Logic Parity is a mechanism whereby a non parity RAM chip can simulate parity. Answer option A is incorrect. Rambus is unrelated to the issue of parity. What is
RIMM? Rambus Inline Memory Module (RIMM) is a type of memory that has 184 pins. It was developed by Rambus, Intel, and Kingston. This module only supports Rambus memory and fits on its own slot.
Reference: RAM Parityhttp://www.Answers.com/topic/non-parity-memory
Question 4
Which of the following is a technology that allows you to hear and watch video clips as soon as they start downloading from the Web site, instead of waiting for the download to complete?
- A. Session Initiation Protocol
- B. Streaming media
- C. HTTP streaming
- D. Slipstreaming
Answer : B
Explanation:
Streaming media is a technology that allows you to hear and watch video clips as soon as they start downloading from the Web site, instead of waiting for the download to complete.
Answer option C is incorrect. HTTP streaming is a simple mechanism for sending data from a Web server to a Web browser in response to an event. Every time a seek operation is performed, the media player makes a request to the server side script with a couple of GET variables. One is the file to play and one is the start position. The server side script then starts the video from the offset given. For example, after starting the video, a user can jump directly to any part in the video without having to wait until it is loaded. Answer optionA is incorrect. Session Initiation Protocol (SIP), designed by Henning
Schulzrinne and Mark Handley in 1996, is a signaling protocol, widely used for setting up and tearing down multimedia communication sessions such as voice and video calls over the Internet
(VoIP).Answer option D is incorrect. Slipstreaming is a process of integrating service pack updates into the Windows XP Professional setup files. The slipstreaming process eliminates the need of deploying service pack update on each computer separately.
Reference: "http://en.wikipedia.org/wiki/Streaming_media"
Question 5
What are the benefits of using Universal Serial Bus (USB) 2.0 over legacy communication ports such as RS-232 and parallel ports? Each correct Answer represents a complete solution. Choose all that apply.
- A. Easy configuration of hardware devices
- B. Expansion
- C. Security
- D. Speed
Answer : ABD
Explanation:
Universal Serial Bus (USB) is a high speed bus standard developed by Compaq, IBM,
DEC, Intel,
Microsoft, NEC, and Northern Telecom. It provides the Plug and Play capability of Windows to external hardware devices. USB supports hot plugging, which means that a USB device can be installed or removed while the computer is running. A single USB port canbe used to connect up to 127 peripheral devices, such as CD-ROM drives, tape drives, keyboards, scanners etc. USB 1.1 has a maximum data transfer rate of 12 Mbps, whereas USB 2.0 has a maximum data transfer rate of
480 Mbps. USB 2.0 is fully backward compatible with USB 1.1. By connecting a USB hub to a USB port on a computer, you can connect multiple devices to the computer and therefore get the benefit of expansion using the same port.
Answer option C is incorrect. USB ports have nothing to do with security.
Reference: TechNet Technical Information CD, Topic: "Appendix C - Hardware Support"
Question 6
N NO:59 -
Which of the following types of attacks is often performed by looking surreptitiously at the keyboard or monitor of an employee's computer?
- A. Man-in-the-middle attack
- B. Denial-of-Service (DoS) attack
- C. Buffer-overflow attack
- D. Shoulder surfingattack
Answer : D
Explanation:
The Shoulder surfing attack is often performed by looking surreptitiously at the keyboard or monitor of an employee's computer.
Shoulder surfing is a type of in person attack in which an attacker gathers information about thepremises of an organization. This attack is often performed by looking surreptitiously at the keyboard or monitor screen of an employee's computer while he is typing in his password at any access point such as a terminal/Web site. An attacker can also gather information by looking at open documents on the employee's desk, posted notices on the notice boards, etc.
Answer option A is incorrect. Man-in-the-middle attacks occur when an attacker successfully inserts an intermediary software or program between two communicating hosts. The intermediary software or program allows attackers to listen to and modify the communication packetspassing between the two hosts. The software intercepts the communication packets and then sends the information to the receivinghost. The receiving host responds to the software, presuming it to be the legitimate client.
Answer option C is incorrect. A buffer-overflow attack is performed when a hacker fills a field, typically an address bar, with more characters than it can accommodate. The excess characters can be run as executable code, effectively giving the hacker control of the computer and overriding any security measures set.
Answer option B is incorrect. A Denial-of-Service (DoS) attack is mounted with the objective of causing a negative impact on the performance of a computer or network. It is also known as network saturation attack or bandwidth consumption attack. Attackers make
Denial-of-Service attacks by sending a large number of protocol packets to a network. A
DoS attack can cause the following to occur:
Saturate network resources.
Disrupt connections between two computers, thereby preventing communications between services.
Disrupt services to a specific computer.
A SYN attack is a common DoS technique in which an attacker sends multiple SYN packets to a target computer. For each SYN packet received, the target computer allocates resources and sends an acknowledgement (SYN-ACK) to the source IP address. Since the target computer does not receive a response from the attacking computer, it attempts to resend the SYN-ACK. This leaves TCP ports in the half-open state. When an attacker sends TCP SYNs repeatedly before the half-open connections are timed out, the target computer eventually runs out of resources and is unable to handle any more connections, thereby denying service to legitimate users.
Reference: "http://en.wikipedia.org/wiki/Shoulder_surfing_(computer_security)"
Question 7
Drag and drop the appropriate class of fire extinguisher in front of types of fires.
Answer : 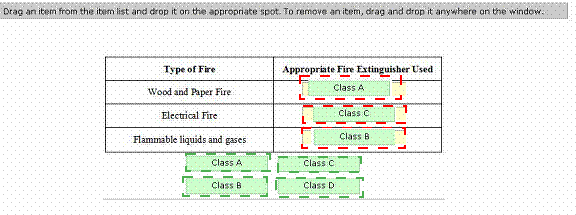
Explanation:
Class A fire extinguisher is used for wood and paper fire.
Class B fire extinguisher is used for flammable liquid and gases fire.
Class C fire extinguisher is used for electrical fire.
Class D fire extinguisher is used for combustible metals fire. Reference.
"http.//en.wikipedia.org/wiki/Fire_extinguisher"
Question 8
You are responsible for technical support at a company. One of the employees complains that his new laptop cannot connect to the company wireless network. You have verified that he is entering a valid password/passkey. What is the most likely problem?
- A. His operating system is incompatible.
- B. A firewall is blocking him.
- C. His laptop isincompatible.
- D. MAC filtering is blocking him.
Answer : D
Explanation:
The most likely problem is that, since this is a new laptop, the laptop's MAC address is not listed with the router, and is therefore blocked by MAC filtering.
What is MAC addressfiltering?
MAC address filtering is a security method that enables a device to allow only certain MAC addresses to access a network. It can be configured on a Wireless Access Point (WAP) to allow only certain system MAC addresses to communicate with the rest of the network.
MAC address filtering can be performed using either of the two policies: exclude all by default, then allow only listed clients; or include all by default, then exclude listed clients.
MAC filtering can also be used on a wireless networkto prevent certain network devices from accessing the wireless network. MAC addresses are allocated only to hardware devices, not to persons.
Answer option B is incorrect. Firewalls block certain types of traffic, but would not completely block an attemptto connect.
Answer options A and C are incorrect. Wireless networking is not operating system or hardware specific. Macintosh, Linux, Windows, all can connect to the same wireless network.
Reference: http://en.wikipedia.org/wiki/MAC_filtering
Question 9
Which of the following isthe clock speed of the Accelerated Graphics Port (AGP) 8X expansion slot?
- A. 266 MHz
- B. 133 MHz
- C. 533 MHz
- D. 633 MHz
Answer : C
Explanation:
The clock speed of the Accelerated Graphics Port (AGP) 8X expansion slot is 533 MHz.
AGP expansion slot is a highspeed 32-bit bus designed for high performance graphics and video support. It allows a video card to have direct access to a computer's RAM, which enables fast video performance. AGP provides a bandwidth of up to 2,133 MB/second.
Answer option A is incorrect. The clock speed of Accelerated Graphics Port (AGP) 4X expansion slot is
266 MHz.
Answer option B is incorrect. The clock speed of Accelerated Graphics Port (AGP) 2X expansion slot is 133 MHz.
Answer option D is incorrect. The Accelerated Graphics Port(AGP) expansion slot does not support the clock speed of 633 MHz.
Reference. "http.//en.wikipedia.org/wiki/Accelerated_Graphics_Port"
Question 10
Which of the following features are related to power management?
Each correct answer represents a complete solution. Choose two.
- A. Hot plugging
- B. Hibernate mode
- C. Standby mode
- D. Safe mode
Answer : BC
Explanation:
The Hibernate mode and Standby mode are features related to power management.
Hibernate mode is a power saving feature for computers. In hibernate mode, the current state of a computer is saved to the hard disk, and the computer shuts down. Auser will have to power on the computer to restore the previous settings. When a computer resumes from hibernate mode, it reads the saved settings from the disk and restores the system state as it was before it entered hibernate mode. By default, hibernatemode is disabled. If a computer is not ACPI-enabled or APM-enabled, users will have to enter hibernate mode manually. Users cannot set the computer to automatically hibernate after a certain time.
With ACPI-enabled and APM-enabled computers, users are able to set hibernate mode automatically.
The standby mode is a power saving feature for computers. In this mode, a computer does not shut down completely. The computer goes to low power state and, as a result, it consumes less power.
When the computer resumes from the standby mode, full power is restored to its devices.
During the standby mode, if the power supply is disconnected or interrupted, data might be lost. The standby mode is available automatically on ACPI-enabled or APM-enabled computers. Users donot need to enable this mode manually. This mode is not available in non-ACPI and non-APM based computers.
Answer option A is incorrect. Hot plugging is a feature in which a device can be installed or removed while the computer is running.
Answer option Dis incorrect. Safe Mode is a Windows feature used to start a computer with basic drivers, such as mouse, keyboard, etc. It bypasses blocking issues, such as system corruption, or installation of incompatible drivers or system services, enabling the
Administrator to resolve such issues.
Question 11
Identify the PS/2 keyboard port in the image given below.

Answer : 
Explanation:
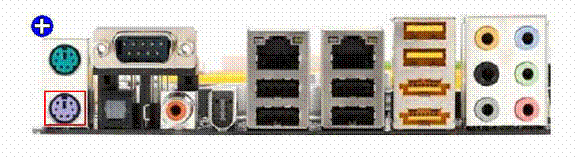
The PS/2 port is developed by IBM for connecting a mouse or keyboard to a computer.
The PS/2 port supports amini DIN plug containing 6 pins. The PS/2 keyboard port generally comes in purple color. The PS/2 mouse port generally comes in green color.
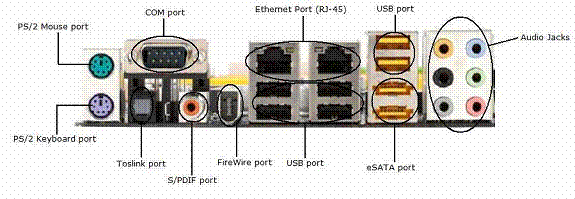
Question 12
Which of the following is the most common method used by attackers to identify wireless networks?
- A. Back door
- B. Packet sniffing
- C. Packet filtering
- D. War driving
Answer : D
Explanation:
War driving is the most common method used by attackers to identify wireless networks. In war driving, a person drives around businesses and neighborhoods attempting to locate a wireless access point (AP) by using a portable device.
Answer option Bis incorrect. Packet sniffing is a process of monitoring data packets that travel across a network. The software used for packet sniffing is known as sniffers. There are many packetsniffing programs that are available on the Internet. Some of these are unauthorized, which can be harmful for a network's security.
Answer option C is incorrect. Packet filtering is a method that allows or restricts the flow of specific types of packets to provide security. It analyzes the incoming and outgoing packets and letsthem pass or stops them at a network interface based on the source and destination addresses, ports, or protocols. Packet filtering provides a way to define precisely which type of IP traffic is allowed to cross the firewall of an intranet. IP packet filtering is important when users from private intranets connect to public networks, such as the Internet.
Answer option A is incorrect. Back door is a program or account that allows access to a system by skipping the security checks. Many vendors and developers implement back doors to save time and effort by skipping the security checks while troubleshooting. Back door is considered to be a security threat and should be kept with the highest security. If a back door becomes known to attackers and malicious users, they can use it to exploit the system.
Question 13
Which of the following Interfaces has the ability to support digital audio as well as video through a single cable?
- A. VGA
- B. HDMI
- C. SVGA
- D. DVI
Answer : B
Explanation:
HDMI interfacehas the ability to support digital audio as well as video through a single cable. HDMI stands for High-Definition Multimedia Interface. It is a standard, uncompressed, and all-digital audio/video interface. HDMI is capable of delivering the highest quality digital video and multichannel digital audio on a single cable. It provides an interface between any audio/video sources, such as a DVD player or a computer and a digital television (DTV) or video monitor. HDMI transmits all ATSC HDTV standards and supports 8-channel digital audio, with extra bandwidth to accommodate future enhancements. HDMI has two types of connectors. Type A and Type B. Type A and Type
B connectors use 19 pins and 29 pins, respectively. The Type B connector is designed for very high-resolution displays that are expected in near future.
Answer options C, D, and A are incorrect. SVGA, VGA, and DVI interfaces do not have capability to support digital audio as well as video through a single cable.
What is a VGA or SVGA connector?
A VGA or SVGA connector is a 15-pin, three rows, female connector, on the back of a PC used for connecting monitors.
What is DVI?
DVI stands for Digital Visual Interface. It is a standard for high speed, high resolution digital display invented by Digital
Display Working Group (DDWG). DVI accommodates analog and digital interfaces with a single connector. New video cards have DVI as well as VGA ports built into them. Most of
LCD monitors come with a 15-pin VGA connection cable, even if they are capable of handling digital signals coming from DVI connections. However, some monitors come with both types of cables. DVI has three main categories of connectors. They are. DVI-A, DVI-
D, and DVI-I. DVI-A is an analog-only connector,
DVI-D is a digital-only connector, and DVI-I is an analog/digital connector. DVI-D and DVI-I connectors are of two types. single link and dual link. DVI supports UXGA and HDTV with a single set of links. Higher resolutions such as 1920 x 1080, 2048 x 1536, or more can be supported with dual links.
Reference. "http.//en.wikipedia.org/wiki/HDMI"
Question 14
Which of the following cryptographic algorithm uses public key and private key to encrypt or decrypt data ?
- A. Hashing
- B. Symmetric
- C. Asymmetric
- D. Numeric
Answer : C
Explanation:
Asymmetric algorithm uses two keys, public key andprivate key, to encrypt and decrypt data.
What is asymmetric encryption?
Asymmetric encryption is a type of encryption that uses two keys - a public key and a private key pair for data encryption. The public key is available to everyone, while the privateor secret key is available only to the recipient of the message. For example, when a user sends a message or data to another user, the sender uses a public key to encrypt the data. The receiver uses his private key to decrypt the data.
Answer option B is incorrect. Symmetric algorithm uses a single key to encrypt and decrypt data.
Answer option A is incorrect. Hashing encryption algorithm uses a process of converting a message, or data, into a numeric value to encrypt data. Secure Hash Algorithm (SHA) and
Message Digest Algorithm (MDA) are two standards that use the hashing process for encryption.
Answer option D is incorrect. There is no such cryptographic algorithm as Numeric.
Reference. TechNet, Contents. "Description of Symmetric and Asymmetric Encryption"
Question 15
Which of the following are types of social engineering attacks?
Each correct Answer represents a complete solution. Choose two.
- A. An unauthorized persongains entrance to the building where the company's database server resides and accesses the server by pretending to be an employee.
- B. An unauthorized person inserts an intermediary software or program between two communicating hosts to listen to and modify the communication packets passing between the two hosts.
- C. An unauthorized person calls a user and pretends to be a system administrator in order to get the user's password.
- D. An unauthorized person modifies packet headers by using someone else's IP address to his identity.
Answer : AC
Explanation:
Following are the types of social engineering attacks: 1.An unauthorized person calls a user and pretends to be a system administrator in order to get the user's password.
2.An unauthorized person gainsentrance to the building where the company's database server resides and accesses the server by pretending to be an employee.
A social engineering attack is based on misleading users or administrators at the target site. Social engineering attacks are usually carried out by telephoning users or operators and pretending to be an authorized user in order to gain unauthorized access to systems.
Answer option D is incorrect.
Spoofing is a technique that makes a transmission appear to have come from an authenticsource by forging the IP address, email address, caller ID, etc. In IP spoofing, a hacker modifies packet headers by using someone else's IP address to his identity.
However, spoofing cannot be used while surfing the
Internet, chatting on-line, etc. because forging the source IP address causes the responses to be misdirected.