EC-Council Certified Security Analyst (ECSA) v10.3
Question 1
DMZ is a network designed to give the public access to the specific internal resources and you might want to do the same thing for guests visiting organizations without compromising the integrity of the internal resources. In general, attacks on the wireless networks fall into four basic categories. Identify the attacks that fall under Passive attacks category.(Select all that apply)
- A. Wardriving
- B. Spoofing
- C. Sniffing
- D. Network Hijacking
Answer : A
Question 2
The IP protocol was designed for use on a wide variety of transmission links. Although the maximum length of an IP datagram is 64K, most transmission links enforce a smaller maximum packet length limit, called a MTU.
The value of the MTU depends on the type of the transmission link. The design of IP accommodates MTU differences by allowing routers to fragment IP datagrams as necessary. The receiving station is responsible for reassembling the fragments back into the original full size IP datagram.
IP fragmentation involves breaking a datagram into a number of pieces that can be reassembled later. The IP source, destination, identification, total length, and fragment offset fields in the IP header, are used for IP fragmentation and reassembly.
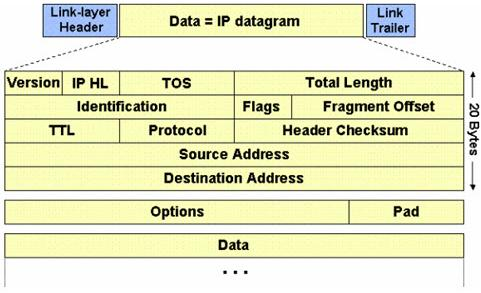
The fragment offset is 13 bits and indicates where a fragment belongs in the original IP datagram. This value is a:
- A. Multiple of four bytes
- B. Multiple of two bytes
- C. Multiple of eight bytes
- D. Multiple of six bytes
Answer : C
Reference: http://www.freesoft.org/CIE/Course/Section3/7.htm (fragment offset: 13 bits)
Question 3
Traffic on which port is unusual for both the TCP and UDP ports?
- A. Port 81
- B. Port 443
- C. Port 0
- D. Port21
Answer : C
Question 4
What is a goal of the penetration testing report?

- A. The penetration testing report helps you comply with local laws and regulations related to environmental conditions in the organization.
- B. The penetration testing report allows you to sleep better at night thinking your organization is protected
- C. The pen testing report helps executive management to make decisions on implementing security controls in the organization and helps the security team implement security controls and patch any flaws discovered during testing.
- D. The penetration testing report allows you to increase sales performance by effectively communicating with the internal security team.
Answer : C
Question 5
A penetration tester performs OS fingerprinting on the target server to identify the operating system used on the target server with the help of ICMP packets.
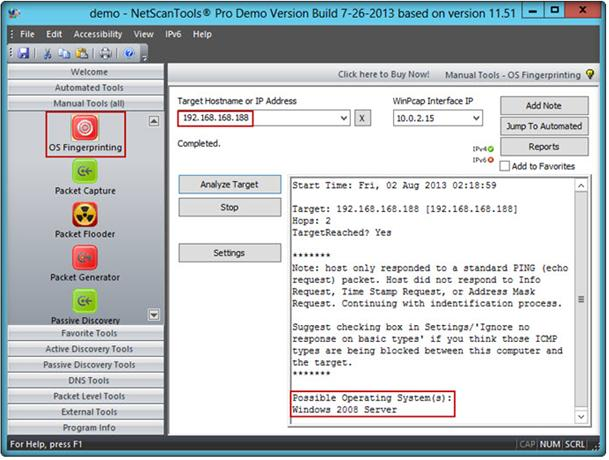
While performing ICMP scanning using Nmap tool, message received/type displays 3
Destination Unreachable[5] and code 3.
Which of the following is an appropriate description of this response?
- A. Destination port unreachable
- B. Destination host unavailable
- C. Destination host unreachable
- D. Destination protocol unreachable
Answer : A
Question 6
Which of the following attacks does a hacker perform in order to obtain UDDI information such as businessEntity, businesService, bindingTemplate, and tModel?
- A. Web Services Footprinting Attack
- B. Service Level Configuration Attacks
- C. URL Tampering Attacks
- D. Inside Attacks
Answer : A
Reference: http://www.scribd.com/doc/184891017/CEHv8-Module-13-Hacking-Web-
Applications-pdf (page 99)
Question 7
The framework primarily designed to fulfill a methodical and organized way of addressing five threat classes to network and that can be used to access, plan, manage, and maintain secure computers and communication networks is:
- A. Nortells Unified Security Framework
- B. The IBM Security Framework
- C. Bell Labs Network Security Framework
- D. Microsoft Internet Security Framework
Answer : C
Question 8
In the TCP/IP model, the transport layer is responsible for reliability and flow control from source to the destination. TCP provides the mechanism for flow control by allowing the sending and receiving hosts to communicate. A flow control mechanism avoids the problem with a transmitting host overflowing the buffers in the receiving host.
Which of the following flow control mechanism guarantees reliable delivery of data?
- A. Sliding Windows
- B. Windowing
- C. Positive Acknowledgment with Retransmission (PAR)
- D. Synchronization
Answer : C
Reference: http://condor.depaul.edu/jkristof/technotes/tcp.html (1.1.3 Reliability)
Question 9
Which of the following protocols cannot be used to filter VoIP traffic?
- A. Media Gateway Control Protocol (MGCP)
- B. Real-time Transport Control Protocol (RTCP)
- C. Session Description Protocol (SDP)
- D. Real-Time Publish Subscribe (RTPS)
Answer : D
Question 10
John, the penetration testing manager in a pen testing firm, needs to prepare a pen testing pricing report for a client.
Which of the following factors does he need to consider while preparing the pen testing pricing report?

- A. Number of employees in the client organization
- B. Complete structure of the organization
- C. Number of client computers to be tested and resources required to perform a pen test
- D. Number of servers available in the client organization
Answer : C
Question 11
Black-box testing is a method of software testing that examines the functionality of an application (e.g. what the software does) without peering into its internal structures or workings. Black-box testing is used to detect issues in SQL statements and to detect SQL injection vulnerabilities.
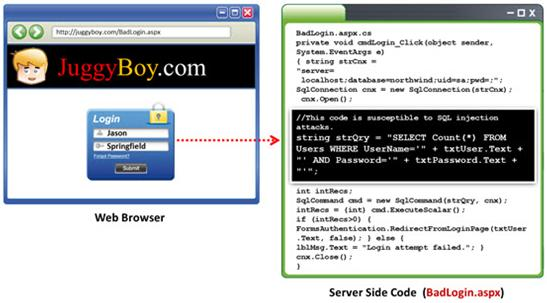
Most commonly, SQL injection vulnerabilities are a result of coding vulnerabilities during the Implementation/Development phase and will likely require code changes.
Pen testers need to perform this testing during the development phase to find and fix the
SQL injection vulnerability.
What can a pen tester do to detect input sanitization issues?
- A. Send single quotes as the input data to catch instances where the user input is not sanitized
- B. Send double quotes as the input data to catch instances where the user input is not sanitized
- C. Send long strings of junk data, just as you would send strings to detect buffer overruns
- D. Use a right square bracket (the ] character) as the input data to catch instances where the user input is used as part of a SQL identifier without any input sanitization
Answer : D
Question 12
Traceroute is a computer network diagnostic tool for displaying the route (path) and measuring transit delays of packets across an Internet Protocol (IP) network. It sends a sequence of three Internet Control Message Protocol (ICMP) echo request packets addressed to a destination host.
The time-to-live (TTL) value, also known as hop limit, is used in determining the intermediate routers being traversed towards the destination.
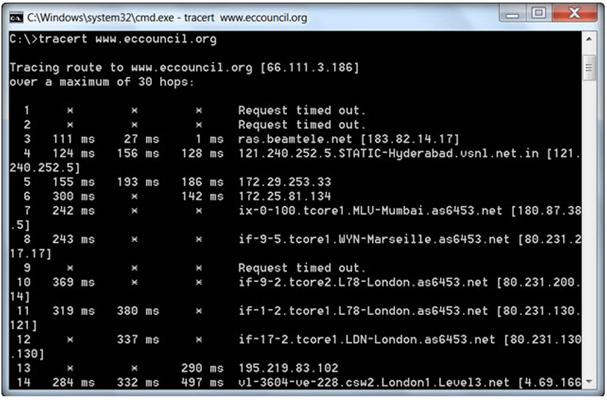
During routing, each router reduces packets' TTL value by
- A. 3
- B. 1
- C. 4
- D. 2
Answer : B
Reference: http://www.packetu.com/2009/10/09/traceroute-through-the-asa/
Question 13
Network scanning is used to identify the available network resources. Which one of the following is also known as a half-open scan, because a full TCP connection is never completed and it is used to determine which ports are open and listening on a target device?
- A. SYN Scan
- B. TCP Connect Scan
- C. XMAS Scan
- D. Null Scan
Answer : A
Question 14
Identify the person who will lead the penetration-testing project and be the client point of contact.
- A. Database Penetration Tester
- B. Policy Penetration Tester
- C. Chief Penetration Tester
- D. Application Penetration Tester
Answer : C
Reference: http://www.scribd.com/doc/133635286/LPTv4-Module-15-Pre-Penetration-
Testing-Checklist-NoRestriction (page 15)
Question 15
An antenna is a device that is designed to transmit and receive the electromagnetic waves that are generally called radio waves. Which one of the following types of antenna is developed from waveguide technology?
- A. Leaky Wave Antennas
- B. Aperture Antennas
- C. Reflector Antenna
- D. Directional Antenna
Answer : B