Ethical Hacking and Countermeasures V8 v5.1
Question 1
What type of Trojan is this?
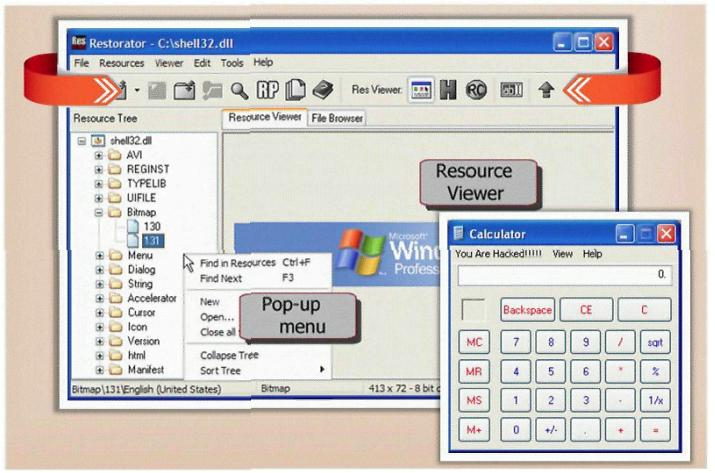
- A. RAT Trojan
- B. E-Mail Trojan
- C. Defacement Trojan
- D. Destructing Trojan
- E. Denial of Service Trojan
Answer : C
Question 2
In the context of Trojans, what is the definition of a Wrapper?
- A. An encryption tool to protect the Trojan
- B. A tool used to bind the Trojan with a legitimate file
- C. A tool used to calculate bandwidth and CPU cycles wasted by the Trojan
- D. A tool used to encapsulate packets within a new header and footer
Answer : B
Explanation:
Wrapper does not change header or footer of any packets but it mix between legitimate file and Trojan file.
Question 3
Lori is a Certified Ethical Hacker as well as a Certified Hacking Forensics Investigator working as an IT security consultant. Lori has been hired on by Kiley Innovators, a large marketing firm that recently underwent a string of thefts and corporate espionage incidents.
Lori is told that a rival marketing company came out with an exact duplicate product right before Kiley Innovators was about to release it. The executive team believes that an employee is leaking information to the rival company. Lori questions all employees, reviews server logs, and firewall logs; after which she finds nothing. Lori is then given permission to search through the corporate email system. She searches by email being sent to and sent from the rival marketing company.
She finds one employee that appears to be sending very large email to this other marketing company, even though they should have no reason to be communicating with them. Lori tracks down the actual emails sent and upon opening them, only finds picture files attached to them. These files seem perfectly harmless, usually containing some kind of joke. Lori decides to use some special software to further examine the pictures and finds that each one had hidden text that was stored in each picture.
What technique was used by the Kiley Innovators employee to send information to the rival marketing company?
- A. The Kiley Innovators employee used cryptography to hide the information in the emails sent
- B. The method used by the employee to hide the information was logical watermarking
- C. The employee used steganography to hide information in the picture attachments
- D. By using the pictures to hide information, the employee utilized picture fuzzing
Answer : C
Question 4
How do you defend against Privilege Escalation?
- A. Use encryption to protect sensitive data
- B. Restrict the interactive logon privileges
- C. Run services as unprivileged accounts
- D. Allow security settings of IE to zero or Low
- E. Run users and applications on the least privileges
Answer : A,B,C,E
Question 5
One of the effective DoS/DDoS countermeasures is 'Throttling'. Which statement correctly defines this term?
- A. Set up routers that access a server with logic to adjust incoming traffic to levels that will be safe for the server to process
- B. Providers can increase the bandwidth on critical connections to prevent them from going down in the event of an attack
- C. Replicating servers that can provide additional failsafe protection
- D. Load balance each server in a multiple-server architecture
Answer : A
Question 6
What does FIN in TCP flag define?
- A. Used to abort a TCP connection abruptly
- B. Used to close a TCP connection
- C. Used to acknowledge receipt of a previous packet or transmission
- D. Used to indicate the beginning of a TCP connection
Answer : B
Question 7
While performing a ping sweep of a local subnet you receive an ICMP reply of Code 3/Type
13 for all the pings you have sent out. What is the most likely cause of this?
- A. The firewall is dropping the packets
- B. An in-line IDS is dropping the packets
- C. A router is blocking ICMP
- D. The host does not respond to ICMP packets
Answer : C
Question 8
Shayla is an IT security consultant, specializing in social engineering and external penetration tests. Shayla has been hired on by Treks Avionics, a subcontractor for the
Department of Defense. Shayla has been given authority to perform any and all tests necessary to audit the company's network security.
No employees for the company, other than the IT director, know about Shayla's work she will be doing. Shayla's first step is to obtain a list of employees through company website contact pages. Then she befriends a female employee of the company through an online chat website. After meeting with the female employee numerous times, Shayla is able to gain her trust and they become friends. One day, Shayla steals the employee's access badge and uses it to gain unauthorized access to the Treks Avionics offices.
What type of insider threat would Shayla be considered?
- A. She would be considered an Insider Affiliate
- B. Because she does not have any legal access herself, Shayla would be considered an Outside Affiliate
- C. Shayla is an Insider Associate since she has befriended an actual employee
- D. Since Shayla obtained access with a legitimate company badge; she would be considered a Pure Insider
Answer : A
Question 9
Maintaining a secure Web server requires constant effort, resources, and vigilance from an organization. Securely administering a Web server on a daily basis is an essential aspect of Web server security.
Maintaining the security of a Web server will usually involve the following steps:
1. Configuring, protecting, and analyzing log files
2. Backing up critical information frequently
3. Maintaining a protected authoritative copy of the organization's Web content
4. Establishing and following procedures for recovering from compromise
5. Testing and applying patches in a timely manner
6. Testing security periodically.
In which step would you engage a forensic investigator?
- A. 1
- B. 2
- C. 3
- D. 4
- E. 5
- F. 6
Answer : D
Question 10
This attack technique is used when a Web application is vulnerable to an SQL Injection but the results of the Injection are not visible to the attacker.
- A. Unique SQL Injection
- B. Blind SQL Injection
- C. Generic SQL Injection
- D. Double SQL Injection
Answer : B
Question 11
You just purchased the latest DELL computer, which comes pre-installed with Windows 7,
McAfee antivirus software and a host of other applications. You want to connect Ethernet wire to your cable modem and start using the computer immediately. Windows is dangerously insecure when unpacked from the box, and there are a few things that you must do before you use it.
- A. New installation of Windows should be patched by installing the latest service packs and hotfixes
- B. Key applications such as Adobe Acrobat, Macromedia Flash, Java, Winzip etc., must have the latest security patches installed
- C. Install a personal firewall and lock down unused ports from connecting to your computer
- D. Install the latest signatures for Antivirus software
- E. Configure "Windows Update" to automatic
- F. Create a non-admin user with a complex password and logon to this account
- G. You can start using your computer as vendors such as DELL, HP and IBM would have already installed the latest service packs.
Answer : A,C,D,E,F
Question 12
Which type of scan does NOT open a full TCP connection?
- A. Stealth Scan
- B. XMAS Scan
- C. Null Scan
- D. FIN Scan
Answer : A
Question 13
How do you defend against ARP Spoofing? Select three.
- A. Use ARPWALL system and block ARP spoofing attacks
- B. Tune IDS Sensors to look for large amount of ARP traffic on local subnets
- C. Use private VLANS
- D. Place static ARP entries on servers, workstation and routers
Answer : ACD
Explanation:
ARPwall is used in protecting against ARP spoofing.
Incorrect answer:
IDS option may works fine in case of monitoring the traffic from outside the network but not from internal hosts.
Question 14
Which of the following statements would NOT be a proper definition for a Trojan Horse?
- A. An authorized program that has been designed to capture keyboard keystroke while the user is unaware of such activity being performed
- B. An unauthorized program contained within a legitimate program. This unauthorized program performs functions unknown (and probably unwanted) by the user
- C. A legitimate program that has been altered by the placement of unauthorized code within it; this code performs functions unknown (and probably unwanted) by the user
- D. Any program that appears to perform a desirable and necessary function but that (because of unauthorized code within it that is unknown to the user) performs functions unknown (and definitely unwanted) by the user
Answer : A
Question 15
More sophisticated IDSs look for common shellcode signatures. But even these systems can be bypassed, by using polymorphic shellcode. This is a technique common among virus writers ?it basically hides the true nature of the shellcode in different disguises.
How does a polymorphic shellcode work?
- A. They encrypt the shellcode by XORing values over the shellcode, using loader code to decrypt the shellcode, and then executing the decrypted shellcode
- B. They convert the shellcode into Unicode, using loader to convert back to machine code then executing them
- C. They reverse the working instructions into opposite order by masking the IDS signatures
- D. They compress shellcode into normal instructions, uncompress the shellcode using loader code and then executing the shellcode
Answer : A