Data Domain Specialist Exam for Storage Administrators v1.0
Question 1
A company using Dell EMC Data Domain systems with Extended Retention Tier is facing an issue. The retention unit is completely lost and there is no secondary
DR system available.
Which characteristic of Fault Isolation would enable the company to be operational as soon as possible?
- A. Fault isolation automatically fixes the issue and system becomes operational
- B. File system can be removed and system can continue to operate beyond the fault
- C. New archive unit can be added to the existing unit
- D. New file system can be added to the retention tier
Answer : B
Explanation:
For fault isolation purposes, deduplication occurs entirely within the retention unit for DD Extended Retention-enabled DD systems. There is no cross- deduplication between active and retention tiers, or between different retention units (if applicable).
Ensure that the system continues to operate in the event of a failure by sealing data into a self-contained storage unit.
Incorrect Answers:
A: If there is loss of data and a replica is available, try to recover the data from the replica. If a replica is not available, limit any loss of data by leveraging the fault isolation features of DD Extended Retention through Support.
References:
https://www.emc.com/data-protection/data-domain/data-domain-extended-retention.htm
Question 2
An organization wants to back up their data from multiple locations onto a single Dell EMC Data Domain system. They also need to replicate the backup data onto multiple Data Domain systems to meet their Disaster Recovery policies.
Which replication topology suits the organization"™s needs?
- A. Many-to-one
- B. One-to-many
- C. Cascaded one-to-many
- D. Cascaded
Answer : B
Explanation:
DD Replicator supports five replication topologies (one-to-one, one-to-one bidirectional, one-to-many, many-to-one, and cascaded).
In one-to-many replication, data flows from a source directory or MTree on one DD system to several destination DD systems.
Incorrect Answers:
A: In many-to-one replication, whether with MTree or directory, replication data flows from several source DD systems to a single destination DD system. This type of replication can be used to provide data recovery protection for several branch offices on a corporate headquarter"™s IT system.
D: In a cascaded replication topology, a source directory or MTree is chained among three DD systems. The last hop in the chain can be configured as collection.
References:
Dell EMC Data Domain Operating System Version 6.1, Administration Guide, page 397
Question 3
Which software license is required to store and manage archive data on a single Dell EMC Data Domain system to comply with requirements of regulatory standards?
- A. Retention Lock Compliance
- B. Retention Lock Governance
- C. Extended Retention
- D. Encryption
Answer : A
Explanation:
Data Domain Retention Lock Compliance Edition meets the strictest data retention requirements from regulatory standards such as SEC17a-4.
Incorrect Answers:
B: Data Domain Retention Lock Governance Edition protects selected files from modification and deletion before a specified retention period expires.
References:
Dell EMC Data Domain Operating System Version 6.1, Administration Guide, page 26
Question 4
In a DD Boost environment, which storage is supported when using a Dell EMC ProtectPoint solution?
- A. Unity
- B. VMAX
- C. VMAX3
- D. VNX
Answer : C
Explanation:
The direct connection between the primary storage and Data Domain requires Dell EMC storage "" specifically VMAX All Flash, VMAX3 or XtremIO.
References:
https://community.emc.com/community/products/data-domain/blog/2016/10/19/dell-emc-kept-the-app-owner-in-mind-with-these-new-updates
Question 5
A company is using AWS as a cloud provider and is trying to create a cloud unit. Which certificate must be imported to the Dell EMC Data Domain system?
- A. Baltimore CyberTrust Root CA certificate
- B. Digicert High Assurance Root CA certificate
- C. Load Balancer Root CA certificate
- D. Dell EMC Root certificate
Answer : B
Explanation:
For AWS and Azure download root CA certificates from https://www.digicert.com/digicert-rootcertificates.htm.
References:
https://www.emc.com/collateral/TechnicalDocument/docu85188.pdf, page 29
Question 6
A backup administrator has enabled encryption on a Dell EMC Data Domain system. They are currently trying to change the encryption passphrase.
What is a consideration when changing the encryption passphrase?
- A. User with Admin role is sufficient to change the passphrase
- B. Passphrase can be only changed from the command line
- C. Encryption must be disabled to change the passphrase
- D. File system must be disabled before changing the passphrase
Answer : A
Explanation:
The file system must be disabled to change the passphrase. If the file system is running, you are prompted to disable it.
References:
Dell EMC Data Domain Operating System Version 6.1, Administration Guide, page 86
Question 7
What needs to be configured when implementing LACP on a Dell EMC Data Domain System to gain access to the underlying aggregated link connection?
- A. IP alias
- B. Virtual interface
- C. VLAN
- D. Physical network interface
Answer : B
Explanation:
Creating a virtual interface for link aggregation.
Create a virtual interface for link aggregation to serve as a container to associate the links that participate in aggregation.
A link aggregation interface must specify a link bonding mode and may require a hash selection. For example, you might enable link aggregation on virtual interface veth1 to physical interfaces eth1 and eth2 in mode LACP (Link Aggregation Control Protocol) and hash XOR-L2L3.
Procedure -
1. Select Hardware > Ethernet > Interfaces.
2. In the Interfaces table, disable the physical interface where the virtual interface is to be added by clicking No in the Enabled column.
3. From the Create menu, select Virtual Interface.
4. In the Create Virtual Interface dialog, specify a virtual interface name in the veth box.
Etc.
References:
Dell EMC Data Domain Operating System Version 6.1, Administration Guide, page 72
Question 8
An organization has Secure Multi-Tenancy and DD Boost enabled on a Dell EMC Data Domain system. Using a Dell EMC NetWorker server, they back up their data to a DD Boost storage unit named "payroll" on the Data Domain system.
Where is the backup data stored on the Data Domain system?
- A. /data/col1/payroll
- B. /data/col1/<tenantname>/su/payroll
- C. /data/col1/<tenantname>/payroll
- D. /data/col1/su/payroll
Answer : A
Question 9
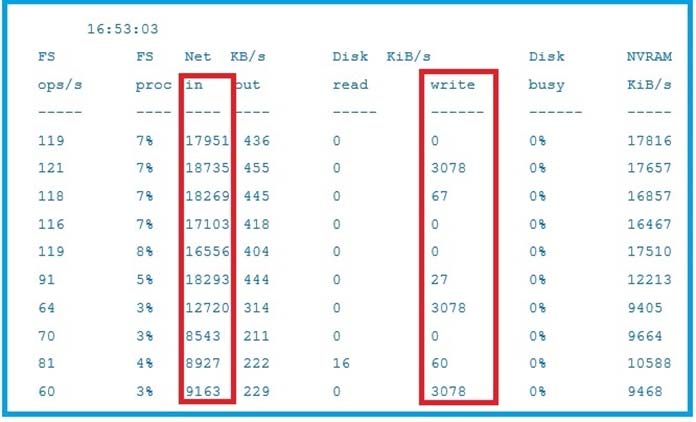
Based on the exhibit, what does the difference between the inbound network rate and writes to disk indicate on the Dell EMC Data Domain system?
- A. Much of the data is redundant and being deduplicated
- B. Much of the data is unique and being stored to disk
- C. A problem exists with the Data Domain system
- D. Data Domain system is deduplicating data faster than the backup server can send it
Answer : A
Question 10
What is the default compression type of the active tier after Extended Retention has been enabled on a Dell EMC Data Domain system?
- A. gzfast
- B. gz
- C. No compression
- D. lz
Answer : B
Explanation:
The Configuration Tab lets you configure your system.
Selecting the Options Edit button displays the Modify Settings dialog, where you can change Local Compression Type [options are none, lz (the default), gz, and gzfast] and Retention Tier Local Comp(ression) [options are none, lz, gz (the default), and gzfast], as well as enable Report Replica Writable.
References:
Dell EMC Data Domain Operating System Version 6.1, Administration Guide, page 479
Question 11
Which command can be used on a Dell EMC Data Domain system to list the UID and GID of Active Directory users so that authentication issues can be diagnosed?
- A. user show detailed
- B. cifs troubleshooting list-users
- C. cifs troubleshooting list-groups
- D. user show list
Answer : B
Explanation:
The cifs troubleshooting commands provide detailed information about CIFS users and groups. cifs troubleshooting list-users
List all CIFS users -
Incorrect Answers:
C: cifs troubleshooting list-groups
List all CIFS groups.
References:
Dell EMC Data Domain Operating System Version 6.1, Command Reference Guide, page 80
Question 12
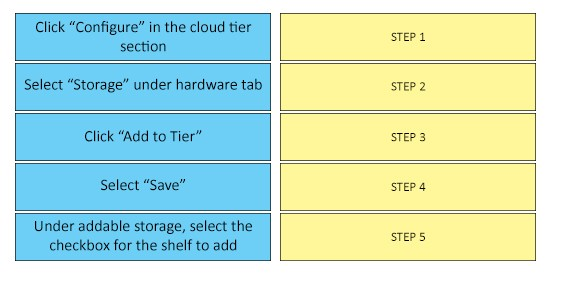
DRAG DROP -
What is the correct sequence of steps to configure storage for a Dell EMC Data Domain Cloud Tier in the System Manager GUI?
Select and Place:
Answer : 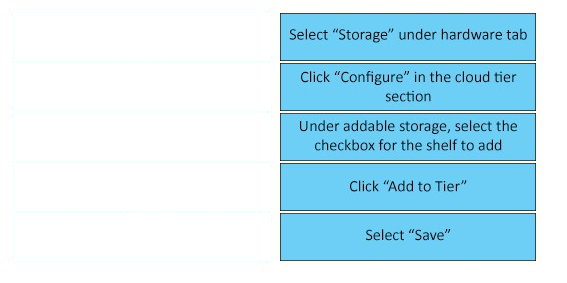
Explanation:
Procedure -
1. Select Hardware > Storage > Overview.
2. Expand the dialog for one of the available storage tiers:
-> Active Tier
-> Extended Retention Tier
-> Cache Tier
-> Cloud Tier
3. Click Configure.
4. In the Configure Storage dialog, select the storage to be added from the Addable Storage list.
5. In the Configure list, select either Active Tier or Retention Tier.
The maximum amount of storage that can be added to the active tier depends on the DD controller used.
6. Select the checkbox for the Shelf to be added.
7. Click the Add to Tier button.
8. Click OK to add the storage.
References:
Dell EMC Data Domain Operating System Version 6.1, Command Reference Guide, page 62
Question 13
What is a characteristic of Dell EMC Data Domain remote logging?
- A. Only works with Syslog servers based on Linux
- B. Communicates only through TCP ports
- C. Can only be enabled and verified through System Manager
- D. CLI command for remote logging is log host
Answer : D
Explanation:
The log host commands manage the process of sending log messages to another system.
References:
Dell EMC Data Domain Operating System Version 6.1, Administration Guide, page 136
Question 14
What is a characteristic of Dell EMC Data Domain replication with the cloud tier?
- A. Does not require that a file be recalled from the cloud on the source
- B. Requires cloud tier to be configured on source and destination systems
- C. Always takes place between the source and destination cloud tier
- D. Always takes place between the source and destination active tier
Answer : D
Explanation:
Data Domain Cloud Tier is a native feature of DD OS for moving data from the Active Tier to low-cost, high-capacity object storage in the public, private, or hybrid cloud for long-term retention.
References:
https://www.emc.com/collateral/software/white-papers/h7082-data-domain-replicator-wp.pdf, page 12
Question 15
What do Dell EMC Data Domain Retention Lock Governance and Dell EMC Retention Lock Compliance Editions have in common?
- A. Security Officer authorization is required to rename MTrees
- B. File-level retention policies
- C. Ability to change the system date is disabled
- D. Audit logging
Answer : B
Explanation:
For archive compliance storage requirements, SEC rules require that a separate copy of retention-locked data must be stored with the same retention requirements as the original. Retention-locked files can be replicated using DD Replicator to another Data Domain system. If a retention-locked file is replicated, it remains retention locked on the destination system, with the same level of protection as the source file.
Incorrect Answers:
A: Data Domain Retention Lock Compliance Edition requires a security officer for implementation of policies. The DD Retention Lock Governance Edition does not require a security officer and provides a higher degree of flexibility for archive data retention on Data Domain systems.
References:
Dell EMC Data Domain Operating System Version 6.1, Administration Guide, page 495