Cloud Infrastructure and Services v2 Exam v6.0
Question 1
What is a function of the control layer of a cloud infrastructure?
- A. Configuring resource pools
- B. Pooling resources
- C. Communicating across computer systems
- D. Providing workflows for executing tasks
Answer : A
Question 2
Refer to the Exhibit.
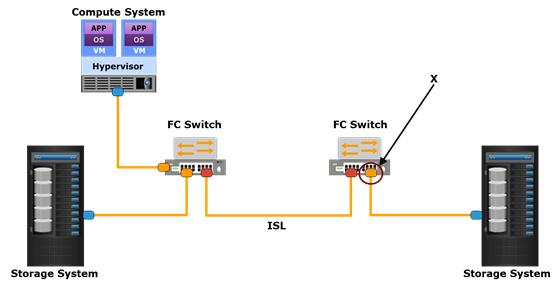
Which type of Fibre Channel SAN port is referenced by the letter X?
- A. F_Port
- B. E_Port
- C. G_Port
- D. N_Port
Answer : A
Question 3
What is enabled by cache tiering?
- A. Tiering between DRAM cache and solid state drives
- B. Creation of a large capacity secondary cache using hard disk drives
- C. Creation of a large capacity secondary cache only using DRAM cache
- D. Tiering between hard disk drives and DRAM cache
Answer : A
Question 4
Which document specifies the quality and reliability of Cloud services?
- A. Service Level Agreement
- B. Regulatory Compliance Document
- C. Service Charge Rate Specification
- D. Service Termination Agreement
Answer : C
Question 5
An organization is using a shared file system to manage virtual machine (VM) files.
Which statement is true about the file system?
- A. It enables VM files to be stored on remote file servers.
- B. It is installed on the local storage of the computer system.
- C. It enables multiple hypervisors to write to a VM file concurrently.
- D. It is installed on the guest operating system of each VM.
Answer : A
Question 6
Refer to the Exhibit.
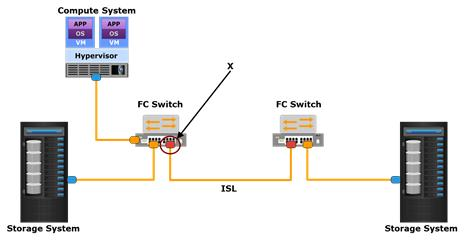
Which type of Fibre Channel SAN port is referenced by the letter X?
- A. E_Port
- B. F_Port
- C. G_Port
- D. N_Port
Answer : A
Question 7
Which mechanism in a Fibre Channel SAN prevents illegitimate host connections by rejecting WWPN logins?
- A. Port binding
- B. Fabric binding
- C. Persistent port locking
- D. Port-type locking
Answer : A
Question 8
An attacker eavesdrops on a network to capture a consumers credentials, which can be used to hijack the consumers account.
Which mechanism should the cloud service provider deploy to mitigate the risk of an account hijacking attack?
- A. Multi-factor authentication
- B. Firewall
- C. Access control list
- D. Encrypting data-at-rest
Answer : A
Question 9
What is a benefit of standardizing the cloud interface?
- A. Enhances portability and interoperability across clouds
- B. Reduces service provisioning time and operating expenditures
- C. Provides flexibility and scalability to configure resources
- D. Personalizes the functional and management interfaces of a cloud
Answer : A
Question 10
Which image represents the correct sequence of steps in a Kerberos mechanism?
A)
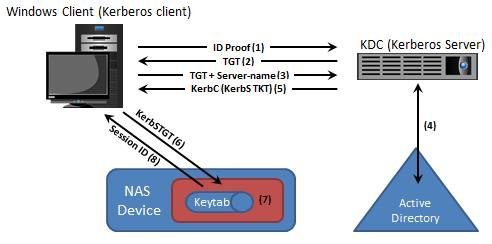
B)
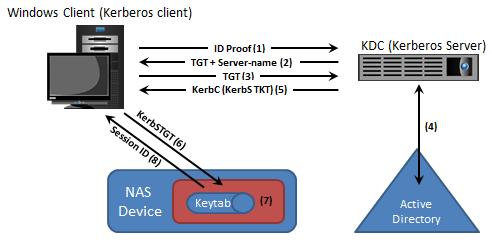
C)
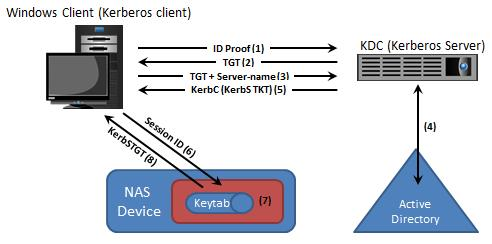
D)
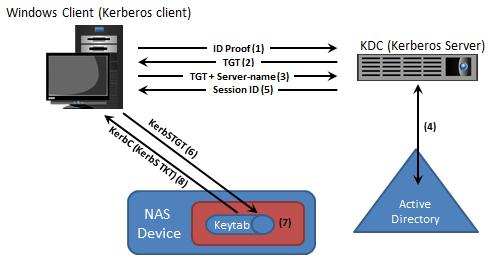
- A. Exhibit A
- B. Exhibit B
- C. Exhibit C
- D. Exhibit D
Answer : A
Question 11
What is the role of a proxy server in an image-based backup solution?
- A. Performs backup operations by using the virtual machine snapshot
- B. Stores backup media for a virtual machine backup
- C. Creates the snapshot for the virtual machine to be backed up
- D. Transfers data directly from the guest OS to the backup device
Answer : A
Question 12
What is a function of financial management?
- A. Provide necessary business cases for investment
- B. Evaluate quality and cost of supplied products against the SLA
- C. Procure capacity in the most cost-effective manner
- D. Meet availability needs with a justifiable return on investment
Answer : A
Question 13
A cloud service provider is concerned about the security risks due to velocity-of-attack.
What can the cloud service provider deploy to mitigate the impact of this attack?
- A. Containment mechanisms
- B. Role-based access control
- C. Multi-factor authentication
- D. Shredding data-at-rest
Answer : A
Question 14
An organization has a private cloud infrastructure. They want to leverage the capabilities of a public cloud by using the hybrid cloud model.
Which virtual private network (VPN) connection method will enable them to establish a secure connection to the public cloud?
- A. Site-to-site VPN connection
- B. Remote access VPN connection
- C. User access VPN connection
- D. Global access VPN connection
Answer : A
Question 15
When using a memory page sharing technique, what happens when a virtual machine tries to update the shared memory page?
- A. A private copy of the page is created.
- B. A new shared memory page is created.
- C. The page is overwritten.
- D. The page is partially updated.
Answer : A