Specialist Infrastructure Security Exam v1.0
Question 1
Your organization has tasked you with collecting information on all the data, personnel, devices, systems, and facilities that enable the organization to achieve its business purposes.
Which part of the NIST Cybersecurity Framework would you consult first?
- A. ID.SC
- B. DE.DP
- C. PR.AC
- D. ID.AM
Answer : D
Reference:
https://www.phe.gov/Preparedness/planning/405d/Documents/resources-templates-508.pdf
(27)
Question 2
What is concerned with availability, reliability, and recoverability of business processes and functions?
- A. Business Impact Analysis
- B. Business Continuity Plan
- C. Recovery Strategy
- D. Disaster Recovery Plan
Answer : B
Question 3
A security engineer is responsible for monitoring company software, firmware, system OS, and applications for known vulnerabilities. How should they stay current on exploits and information security?
- A. Implement security awareness training
- B. Update company policies and procedures
- C. Revise vulnerability management plan
- D. Subscribe to security mailing lists
Answer : D
Question 4
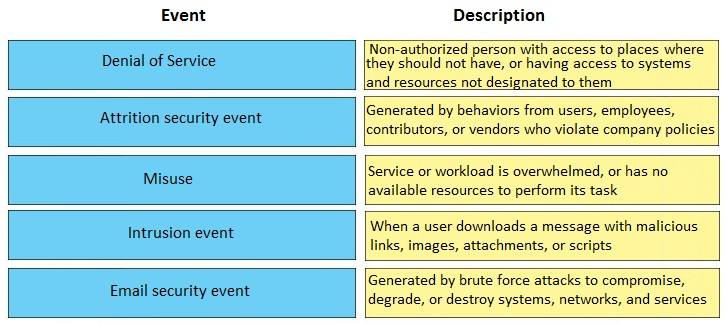
DRAG DROP -
Match the security event to its description.
Select and Place:
Answer : 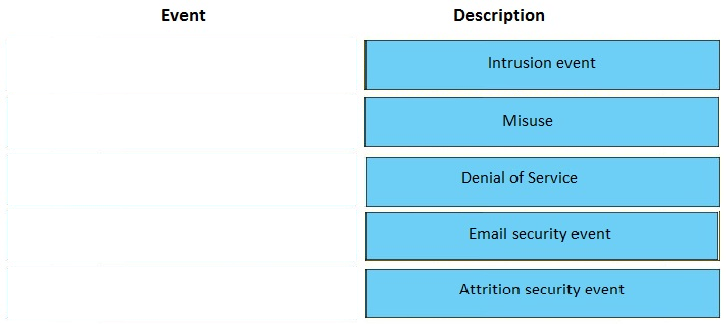
Question 5
The project manager of a data center has a budget of $1,500,000 to install critical infrastructure systems. The project will take 24 months to complete.
The project manager is working with the project management team, security experts, and stakeholders to identify cyber risks. After reviewing the project plan, the
CIO wants to know why so many risk identification meetings are requested.
What a valid reason for the repeated risk identification meetings?
- A. Identify new risks
- B. Update the company risk register
- C. Transfer risk to other project team members
- D. Prevent all risk
Answer : B
Question 6
A company suffers a data breach and determines that the threat actors stole or compromised 10,000 user profiles. The company had planned for such a breach and determined the loss would be around $2 million. Soon after restoration, the company stock suffered a 30% drop and the loss was nearly $20 million. In addition, the company received negative press.
Which area of risk did the business forget to account for?
- A. Litigation or Legal Risk
- B. Reputational Risk
- C. Vulnerability risk
- D. Business Operational Risk
Answer : A
Question 7
A company implemented an intrusion detection system. They notice the system generates a very large number of false alarms.
What steps should the company take to rectify this situation?
- A. Re-evaluate the Baseline and make necessary adjustments to the detection rules
- B. Replace the intrusion detection system with an intrusion protection system
- C. Define how to identify and disregard the false alarms
- D. Consider evaluating a system from another vendor
Answer : A
Question 8
Assume that a DDoS attack has been occurring for 72 minutes. What determines who talks to external stakeholders?
- A. Business Continuity Plan
- B. Communication Plan
- C. Business Impact Analysis
- D. Incident Response Plan
Answer : B
Question 9
What is considered outside the scope of a BIA?
- A. Estimated probability of the identified threats actually occurring
- B. Selection of full, incremental, or differential backups
- C. Efficiency and effectiveness of existing risk mitigation controls
- D. Determination of capacity requirements for backups
Answer : B
Question 10
What are the five functions of the NIST Framework Core?
- A. Identify, Protect, Detect, Respond, and Recover
- B. Governance, Identify, Recover, Respond, and Recover
- C. Protect, Detect, Respond, Governance, and Recover
- D. Identify, Respond, Protect, Detect, and Governance
Answer : A
Reference -
https://www.nist.gov/cyberframework/online-learning/five-functions
Question 11
Which NIST Cybersecurity Framework category ensures that organizational communication and data flows are mapped?
- A. ID.AM
- B. ID.GV
- C. ID.RA
- D. ID.SC
Answer : A
Reference -
https://1path.com/blog/overview-of-the-nist-cybersecurity-framework/
Question 12
The Backup Recovery Plan is dependent on what effort?
- A. PR.DS
- B. RTO
- C. BIA
- D. SDLC
Answer : B
Reference -
https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-34r1.pdf
Question 13
What must be done before returning a compromised laptop to normal operations in the environment?
- A. Perform a virus scan
- B. Eliminate the root cause of the compromise
- C. Re-image the device
- D. Device cannot be returned to the environment
Answer : C
Question 14
An incident has occurred. You restore backups onto mission/business critical assets. After restoration of the backups your services are still inaccessible on numerous assets.
What could be the cause of the issue?
- A. Unverified backups
- B. Incorrect backup strategy
- C. Hardware failure
- D. Network failure
Answer : B
Question 15
A new employee is starting work at your company. When should they be informed of the company"™s security policy?
- A. Based on human resource policy
- B. After the first security infraction
- C. Annual security policy review
- D. During regular security awareness sessions
Answer : D