IBM WebSphere Application Server Network Deployment V9.0 Core Administration v1.0
Question 1
In addition to logging changes, what can Cross Component Trace capture?
- A. The user agent of the browser that has initiated the request.
- B. The last time that the component was updated by a code deploy.
- C. The time that the component was started in the application server.
- D. Data snapshots that store entire request and response bodies on the file system.
Answer : C
Explanation:
Cross Component Trace (XCT) annotates the logs so that log entries that are related to a request that is serviced by more than one thread, process, or even server are identified as belonging to the same unit of work.
XCT log records are typically added to the logs to:
-> demarcate the beginning and ending of work for a particular request on a particular thread.
-> demarcate when work is about to be transferred to another thread or process, or to indicate when work returned from another thread or process.
-> demarcate when work moves from major component to major component, even if work continues on the same thread; for example to show transfer of control from application server code to application code.
Reference:
https://www.ibm.com/support/knowledgecenter/en/SSAW57_8.5.5/com.ibm.websphere.nd.doc/ae/ctrb_XCTOverview.html
Question 2
Which type of fix would typically be downloaded to address a specific problem?
- A. Interim fix
- B. Cumulative fix
- C. Product fix pack
- D. Cumulative interim fix
Answer : A
Explanation:
A WebSphere Commerce interim fix (iFix) is a software patch that contains fixes for one or more APARs. A WebSphere Commerce cumulative iFix is a comprehensive collection of interim fixes for a specific release. Both types of fixes are installed with the WebSphere Commerce Update Installer (UPDI).
Note: An Authorized Program Analysis Report, or APAR, is a formal report from IBM development to customers that have notified IBM of a problem or suspected defect. If IBM development is able to confirm the existence of the issue they will create an APAR with any known work around and perhaps an indication of which future release, if any, of the IBM program they intend to target for a formal fix to the defect and whether or not a Program Temporary Fix (PTF) is planned. The
APAR will then be published so that it is visible to supported customers.
Reference:
https://www.ibm.com/support/knowledgecenter/en/SSZLC2_7.0.0/com.ibm.commerce.install.doc/concepts/cig_install_ifixes.htm
Question 3
What determines which On Demand Routers (ODRs) a Web server forwards requests to?
- A. The default order in the ODR_Module_Routing_Policy.xml.
- B. The configuration scope determines which ODRs are included in httpd.conf.
- C. The configuration scope determines which ODRs are included in plugin-cfg.xml.
- D. The configuration scope determines which ODRs are included in HTTPplugin-cfg.xml.
Answer : C
Explanation:
In a topology with a web server which forwards requests to an on demand router (ODR), the ODR can be set to dynamically generate and update the web server plug-in configuration file plugin-cfg.xml. By configuring an ODR to dynamically update plugin-cfg.xml, you avoid manually updating the file during administrative actions, which can affect the content.
Reference:
https://www.ibm.com/support/knowledgecenter/en/SSAW57_8.5.5/com.ibm.websphere.nd.doc/ae/twve_odr.html
Question 4
When enabling SSL directives in the IBM HTTP Server configuration file, which parameter is required?
- A. The name of the key file
- B. The AllowOverride statement
- C. The IP address of the VirtualHost
- D. The DocumentRoot directory path
Answer : A
Explanation:
Enable SSL and define a key file to use. Uncomment the following lines to enable SSL and define a key file to use:
-> SSLEnable
-> SSLServerCert default
-> Keyfile "C:/Program Files/IBM/HTTPServer5/conf/admin.kdb"
Reference:
https://www.ibm.com/support/knowledgecenter/en/SSAW57_8.5.5/com.ibm.websphere.ihs.doc/ihs/tihs_setupsslwithwas.html
Question 5
Which of the following is a prerequisite for configuring single sign-on for authentication using LTPA cookies?
- A. All servers must use the same IBM HTTP Server.
- B. All servers must be configured as part of the same DNS domain.
- C. All servers must use an IBM Domino Directory that is configured for LDAP access.
- D. All servers must be managed by the same IBM WebSphere Application Server Deployment Manager.
Answer : B
Explanation:
To take advantage of support for SSO between WebSphere Application Servers or between WebSphere Application Server and a Domino server, applications must meet the following prerequisites and conditions:
* Verify that all servers are configured as part of the same DNS domain.
* Etc.
Reference:
https://www.ibm.com/support/knowledgecenter/en/SSAW57_8.5.5/com.ibm.websphere.nd.doc/ae/csec_sso.html
Question 6
To write a Jython script to stop a running application server, an administrator should use which administrative object?
- A. AdminApp
- B. AdminTask
- C. AdminConfig
- D. AdminControl
Answer : D
Explanation:
You can use the wsadmin tool to stop applications.
There are two ways to complete this task. Firstly, you can use the AdminControl object to stop the application. Alternatively, you can use the scripts in the
AdminApplication script library to start, stop, and administer your application configurations.
Reference:
https://www.ibm.com/support/knowledgecenter/en/SSAW57_8.0.0/com.ibm.websphere.nd.doc/info/ae/ae/txml_stopapplication.html
Question 7
Which of the following can be queried to get PMI data?
- A. Server Cell
- B. JMX Connectors
- C. MBean ObjectNames
- D. Application ServerNames
Answer : C
Explanation:
PMI data can be gathered from the J2EE managed object MBeans or the WebSphere Application Server PMI Perf MBean.
Reference:
https://www.ibm.com/support/knowledgecenter/en/SSAW57_8.5.5/com.ibm.websphere.nd.doc/ae/cprf_pmi_datacol.html
Question 8
What is the main difference between interim fixes and product fix packs as they relate to IBM WebSphere Application Server?
- A. Interim fixes typically contain new features or functionality ahead of future product fix packs.
- B. Product fix packs are a combination of interim fixes and internal fixes to make patching easier.
- C. Product fix packs are generally reserved for new features or functionality whereas interim fixes are provided only to fix known issues.
- D. Product fix packs bring WebSphere Application Server to a new product level whereas interim fixes provide corrective service for specific known problems.
Answer : D
Explanation:
Product fix packs contain bundled service to bring WebSphere Application Server up to a new product level. Interim fixes provide corrective service for specific known problems.
Reference:
https://www.ibm.com/support/knowledgecenter/en/SS7K4U_8.5.5/com.ibm.websphere.installation.zseries.doc/ae/tins_install_fixes_z.html
Question 9
Which statement is true about a request made from a browser for a jsp running in an application server?
- A. The HTTP server plug-in loaded with the embedded HTTP server within the application server forwards the request to the application server.
- B. The plug-in configuration file loaded with the embedded HTTP server within the application server forwards the request to the application server.
- C. The HTTP server plug-in loaded with the HTTP server forwards the request to the embedded HTTP server within the application server. The embedded server forwards the request into the web container.
- D. The plug-in configuration file loaded with the HTTP server forwards the request to the embedded HTTP server within the application server. The embedded server forwards the request into the web container.
Answer : A
Explanation:
When IBM HTTP Server receives a request for a JSP file, it passes the request to WebSphere Application Server - Express's servlet engine, which calls the JSP processor. The JSP processor is an internal servlet which converts a JSP file into Java source code and compiles it. The servlet that implements the JSP processor is org.apache.jasper.runtime.JspServlet.
Question 10
An administrator would like to uninstall an instance of a multiple instance installation via response file.
How does the administrator ensure that the correct instance is uninstalled?
- A. All the features must be listed.
- B. The profile ID must point to the correct instance.
- C. The offering ID must point to the correct instance.
- D. The repository location must point to the correct instance.
Answer : D
Reference:
https://www.ibm.com/support/knowledgecenter/en/SSAW57_8.5.5/com.ibm.websphere.installation.nd.doc/ae/cins_WASv85_nd_modify_Win32.html
Question 11
Which two ways are valid ways to install applications to IBM WebSphere Application Server? (Choose two.)
- A. wsadmin script
- B. JMS messaging
- C. IBM Installation Manager
- D. IBM Tivoli Access Manager
- E. Integrated Solutions Console
Answer : AE
Explanation:
Deploy an application or module using the administrative console, wsadmin, programming, or deployment tools.
Reference:
https://www.ibm.com/support/knowledgecenter/en/SSAW57_8.5.5/com.ibm.websphere.nd.doc/ae/crun_app_install.html
Question 12
How can an administrator reduce overhead when utilizing monitored directories?
- A. Increase the polling interval so that the process runs less often.
- B. Decrease the amount of time that the monitored directory is accessible by users.
- C. Decrease the size of the monitored directory so that larger files will not be able to be stored in it.
- D. Configure the monitored directory settings to not automatically synchronize the application once it is installed.
Answer : A
Explanation:
To change the standard polling interval setting, specify a number of seconds in the Polling interval field.
Figure: Configuring the monitored directory
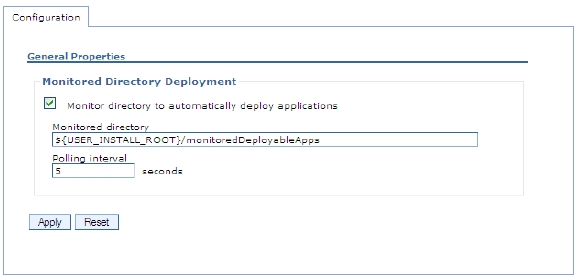
Reference: Application Server V8.5, July 2013, page 852
Question 13
An administrator has deployed an application that uses 30 unique SQL statements with a maximum data source connection pool size of 10.
What is the recommended prepared statement cache size for the application?
- A. 10
- B. 30
- C. 40
- D. 300
Answer : B
Explanation:
To determine the highest value for your cache size to avoid any cache discards, add the number of uniquely prepared statements and callable statements, as determined by the SQL string, concurrency, and the scroll type, for each application that uses this data source on a particular server. This value is the maximum number of possible statements that can be cached on a given connection over the life of the server. Setting the cache size to this value means that you never have cache discards. In general, configure a larger cache for applications with a greater number of statements.
Reference:
https://www.ibm.com/support/knowledgecenter/en/SSAW57_8.5.5/com.ibm.websphere.nd.doc/ae/udat_jdbcdatasorprops.html
Question 14
What must be done to delete one or more files from an application when using a partial application update?
- A. Manually delete the files from the file system (on all nodes if clustered).
- B. Supply the paths to the files that should be deleted in the administrative console.
- C. Include a META-INF/ibm-partialapp-delete.props in the partial application update file.
- D. Select the files that need to be deleted in the file selector section of the form for the partial application update.
Answer : C
Explanation:
If you want to delete application files when you deploy a partial application update, you must first supply a special metadata file called META-INF/ibm-partialapp- delete.props in the partial application compressed file before you continue with the following procedure.
Etc.
Reference:
https://www.ibm.com/support/knowledgecenter/en/SSZLC2_8.0.0/com.ibm.commerce.developer.doc/tasks/tdpdeploying_j2ee_assets_partial.htm
Question 15
An administrator noticed that one of the servers in the core group is experiencing OutOfMemory. As a result, other servers in the core group failed to start.
What core group custom property should the administrator tune to prevent the affected server from impacting other servers in the core group?
- A. IBM_CS_OOM_ACTION
- B. IBM_CS_DATASTACK_MEG
- C. IBM_CS_WIRE_FORMAT_VERSION
- D. IBM_CS_HAM_PROTOCOL_VERSION
Answer : A
Explanation:
Use this custom property to explicitly enable exception handlers that are specific for OutOfMemoryExceptions that occur when sending or receiving network messages. When this property is set to Isolate, if an OutOfMemoryException occurs when a network message is being sent or received, these exception handlers stop High Availability Manager communications to the Out of Memory process.
If IBM_CS_OOM_ACTION=Isolate is not added to the configuration settings for a core group, if a core group process runs out of memory, the Out of memory process might not be able to respond to all messages. This situation prevents multi-step protocols from completing, and prevents the starting server from receiving its initial view of the distributed state.
Reference:
https://www.ibm.com/support/knowledgecenter/en/SSAW57_8.0.0/com.ibm.websphere.nd.doc/info/ae/ae/urun_ha_cg_custprop.html