IBM WebSphere Application Server Network Deployment V8.5.5 and Liberty Profile, System Administration v7.0
Question 1
A system administrator has added a server cluster as a member of a service integration bus (SIB). The administrator needs to configure one messaging engine for each server in this cluster and to have a failover location for each messaging engine.
What should the administrator do to achieve the required design?
- A. Configure a new messaging engine in each server to support failover.
- B. Configure the data store for each messaging engine for each server in the cluster.
- C. Select scalability with high availability as the messaging engine policy.
- D. Create a core group policy to restrict each messaging engine to a particular server.
Answer : C
Explanation: The scalability with high availability configuration ensures that there is a messaging engine for each server in a cluster, and that each messaging engine has a failover location.
Reference:http://www-
01.ibm.com/support/knowledgecenter/SSCKBL_8.5.5/com.ibm.websphere.nd.doc/ae/cjt10
04_.html(second paragraph)
Question 2
A system administrator was asked by the development team to inform them of any warning message which contains a string "Connection" on a WebSphere Application Server with
High Performance Extensible Logging (HPEL) enabled.
What should the administrator do to continuously monitor logs for the required message?
- A. Configure log detail levels to include filter on "Connection" string.
- B. Use the Log Viewer in the administrative console with filter on "Connection" string.
- C. Use the logviewer.sh or logviewer.bat command with appropriate options.
- D. Use the Log Viewer in the administrative console with filter on "Connection" string and enable the 'Refresh automatically' feature.
Answer : C
Reference:http://www-
01.ibm.com/support/knowledgecenter/SSD28V_8.5.5/com.ibm.websphere.base.doc/ae/rtrb
_logviewer.html
Question 3
A system administrator has created a Python script called globalScript. py.
What should the administrator do to ensure globalScript. py is loaded when the wsadmin shell is used?
- A. Compile globalScript.py to a Java class in the bin directory.
- B. Invoke wsadmin with the argument-profileName globalScript.py.
- C. Modify the configureCustomProperty script to import globalScript. py. Set the script profiles in the wsadmin.properties file to load globalScript .py.
Answer : D
Question 4
An organization updated their LDAP directories and modified user roles. The roles that were configured to have access to a highly secured enterprise application were deleted and new roles with new names were created. The application then had security related exceptions.
How can a system administrator resolve the exceptions and restore security for the application?
- A. Modify the mapping of security roles of the application to the new LDAP roles.
- B. Modify the application and remove all security constraints and redeploy the application.
- C. Modify the application to have a run as role for each new LDAP role and redeploy the application.
- D. Create an administrative authorization group with administrator privileges scoped for the application with an administrative group role for the new LDAP roles.
Answer : D
Reference:http://www.novell.com/documentation/idmrbpm36/install/data/bb1zmw0.html(Se e the Role of Administrator).
Question 5
A system administrator,Admin1, with Administrator privileges has archived full repository checkpoints. Another administrator,Configurator1,with Configurator privileges has copied the checkpoint contents directory from one of the archived check points to its original location.Configurator1tries to restore the configuration using the copied archived checkpoint contents and the restore fails.
How canConfigurator1restore the configuration using the copied archived full repository checkpoint?
- A. Copy the archived checkpoint metadata directory to its original location.
- B. Increase the Automatic checkpoint depth to keep all the delta checkpoints.
- C. Delete the delta checkpoints taken after the full repository checkpoint was taken.
- D. Ask an administrator to update the privileges for Configurator1 to matchAdmin1.
Answer : A
Reference:http://www-
01.ibm.com/support/knowledgecenter/SSCKBL_8.5.5///com.ibm.websphere.zseries.doc/ae/ twve_xdappedcfg.html
Question 6
In a test environment, a system administrator has configured an external HTTP server in the DMZ that is routing to a cluster of application servers. The administrator wants to achieve higher performance when routing and prioritizing incoming requests to the back- end cluster.
How can the system administrator achieve this task?
- A. Configure a cluster of external HTTP servers.
- B. Enable the prefer local option on the cluster members.
- C. Set up a Caching Proxy server between the external web server and the application server.
- D. Place an On Demand Router (ODR) between the external web server and the application servers.
Answer : D
Question 7
A system administrator needs to install WebSphere Application Server Network
Deployment V8.5.5 multiple times and would like to automate the task of installing the product. The administrator wants to create a response file based on an initial installation and use this for future installations.
How can the administrator accomplish this task?
- A. Use the IBM Packaging Utility.
- B. Use the Installation Manager Console mode.
- C. Complete a silent installation with the -log option.
- D. Start the Installation Manager GUI with the -record option.
Answer : D
Reference:http://setgetweb.com/p/portal80/p8/additional.html
Question 8
There are many applications deployed in a large WebSphere Application Server cluster. A system administrator is required to give Configuration role access to a developer for a single application deployed in that cluster.
How should the administrator meet this requirement and restrict Configuration role access for a single application?
- A. Create a J2C authentication alias for that developer.
- B. Create an Administrative user role and provide Configuration access to the developer.
- C. Create an Administrative group role and provide Configuration access to the developer.
- D. Create an administrative authorization group, scope it only for that application and create an Administrative user or group role to give Configuration access to the developer.
Answer : A
Question 9
An EJB application posts a request message into a JMS destination and waits for a response message on a different JMS destination. To correlate the response message to the request message, the application uses the JMS correlation ld of the message. The application waits up to five seconds for a response before timing out the request.
A Message Driven Bean (MDB) running on a different cluster is responsible for consuming the request message, process it and post a response message.
The destinations are defined in a Service Integration Bus (SIB) within the cell.
Intermittent timeout exceptions have occurred for the requester application. How can a system administrator correlate and analyze the debug information from both requester and consumer applications?
- A. Enable High Performance Extensible Logging (HPEL). Use HPEL logViewer command to see debug information.
- B. Enable a diagnostic trace in both requester and consumer servers. Use the Integrated Solutions Console (ISC) to set the admin=all trace. Analyze the trace.
- C. Enable High Performance Extensible Logging (HPEL). Enable Cross Component Trace (XCT) to include request IDs in log and trace records. Use HPEL logViewer command with appropriate filters to see debug information.
- D. Using the Integrated Solutions Console (ISC), browse the request message that has timed out and look for any key application data. Search for exceptions using the key application data in both requester and consumer in native_stderr.log and native_stdout.log.
Answer : C
Question 10
Which of the following comprises an initial Liberty profile server process?
- A. A single JVM, the Liberty kernel, and feature manager.
- B. A single JVM, an OSGI framework and an object request broker.
- C. An OSGI framework, a web container and an EJB container.
- D. An administrative agent, the Liberty kernel and shared libraries.
Answer : C
Reference:https://www-
01.ibm.com/support/knowledgecenter/was_beta_liberty/com.ibm.websphere.wlp.nd.multipl atform.doc/ae/cwlp_about.html(See the Liberty Profile Overview).
Question 11
A web application was deployed on a WebSphere Application Server cluster. While users are using the application, one of the cluster servers fails and the users lose their working data.
What can the system administrator configure to ensure users can continue to work if one of the cluster servers fails?
- A. An increased session timeout.
- B. A cluster of external HTTP servers.
- C. A load balancer to spread work between existing servers.
- D. A WebSphere extreme Scale HTTP session management.
Answer : D
Reference:http://websphere.sys-con.com/node/1299059
Question 12
A web application is hosted on an application server that receives HTTP requests from a third party application named myApp. The URlGroup mapping for this application is called default_host_myApp.
The development team asks a system administrator to configure the HTTP plug-in to prevent routing requests to any application server except serverl.
The following exhibit shows the parts of the plugin-cfg.xml file that are relevant for myApp.
The UriGroups for other applications are not shown in the exhibit.
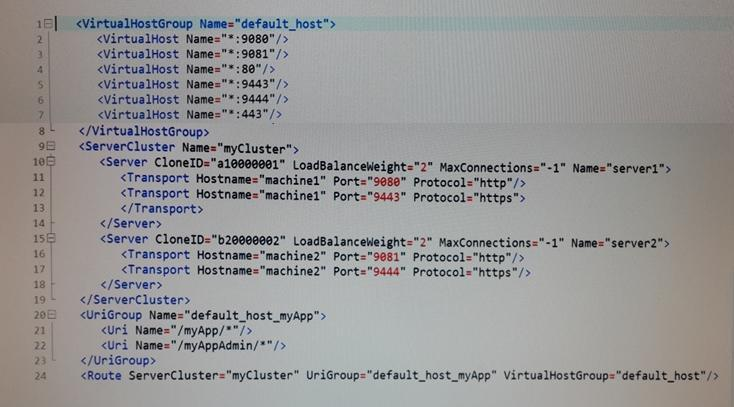
What should the administrator do to the plugin-cfg.xml file to ensure that requests for default_host_myApp URIGroup are routed only to machine1?
- A. Delete the server tag for Cloneld="b20000002" Delete all of the tags within the Server tag
- B. Delete the UriGroup tag for default_host_myApp Delete all of the tags within this UriGroup tag
- C. Delete the VirtualHostGroup tag for default_host Delete all of the tags within the VirtualHostGroup tag
- D. Edit the LoadBalanceWeight forserverl to 20 Edit the LoadBalanceWeight for server2 to 2
Answer : C
Question 13
A system administrator needs to deploy a new enterprise application which requires that application security be enabled, but, the existing applications in the cell cannot be executed with application security enabled. The cell has the global security and Java 2 security disabled.
How can the administrator handle this requirement?
- A. Enable Java 2 security for the cell. Create a security domain with application security enabled. Associate the security domain to the new application.
- B. Enable Java 2 security for the cell. Create a security domain with application security enabled. Associate the security domain to a new cluster to be used to deploy the new application,
- C. Enable administrative security for the cell. Create a security domain with application security enabled. Associate the security domain at the application level for the new application.
- D. Enable administrative security for the cell. Create a security domain with application security enabled. Associate the security domain to the new cluster where the new application is deployed.
Answer : C
Reference:http://www-
01.ibm.com/support/knowledgecenter/SSAW57_8.5.5/com.ibm.websphere.nd.doc/ae/csec
_sec_multiple_domains.html?cp=SSAW57_8.5.5%2F1-8-2-33-1-0(See the Java 2 security).
Question 14
A system administrator wants to learn some of the Python scripting commands for the administration of the environment.
Which product feature should the administrator use?
- A. The wsadmin.properties file to load a profile.
- B. The AdminTask object to generate wsadmin scripts.
- C. The guided activities panel from the Integrated Solutions Console (ISC).
- D. The "Log command assistance commands" option in the Integrated Solutions Console (ISC).
Answer : D
Question 15
A system administrator is required to monitor the application server logs for heap memory issues and determine if the heap memory usage is reaching close to 70% of the maximum heap. The application server is configured with an initial heap of 256 MB and a max heap of 1 GB.
How should the administrator determine if the application server is utilizing 70% of the max allocated heap memory?
- A. Check the System logs for Out Of Memory Errors. Trigger a heap dump from the Integrated Solutions Console (ISC). Analyze the heap dump.
- B. Configure WebSphere Application Server to enable verbose garbage collection. Analyze the garbage collection cycles in the native logs.
- C. Configure Initial heap to be equal to the max heap. Trigger a heap dump from the Integrated Solutions Console (ISC). Analyze the heap dump.
- D. Configure WebSphere Application Server to increase max heap. Trigger a heap dump from the Integrated Solutions Console (ISC). Analyze the heap dump.
Answer : A
Reference:http://www.ibm.com/developerworks/bpm/bpmjournal/1312_chan/1312_chan.ht ml