IBM Security QRadar SIEM V7.2.6, Associate Analyst v7.0
Question 1
What is an example of the use of a flow data that provides more information than an event data?
- A. Represents a single event on the network
- B. Automatically identifies and better classifies new assets found on a network
- C. Performs near real-time comparisons of application data with logs sent from security devices
- D. Represents network activity by normalizing IP addresses ports, byte and packet counts, as well as other details
Answer : D
Explanation:
References:
http://www-01.ibm.com/support/docview.wss?uid=swg21682445
Question 2
When QRadar processes an event it extracts normalized properties and custom properties.
Which list includes only Normalized properties?
- A. Start time, Source IP, Username, Unix Filename
- B. Start time, Username, Unix Filename, RACF Profile
- C. Start time, Low Level Category, Source IP, Username
- D. Low Level Category, Source IP, Username, RACF Profile
Answer : C
Question 3
What is a common purpose for looking at flow data?
- A. To see which users logged into a remote system
- B. To see which users were accessing report data in QRadar
- C. To see application versions installed on a network endpoint
- D. To see how much information was sent from a desktop to a remote website
Answer : D
Question 4
Where can a user add a note to an offense in the user interface?
- A. Dashboard and Offenses Tab
- B. Offenses Tab and Offense Detail Window
- C. Offenses Detail Window, Dashboard, and Admin Tab
- D. Dashboard, Offenses Tab, and Offense Detail Window
Answer : B
Explanation:
References:
IBM Security QRadar SIEM Users Guide. Page: 34
Question 5
What is the default reason for closing an Offense within QRadar?
- A. Actioned
- B. Non-Issue
- C. Blocked Traffic
- D. Acceptable Traffic
Answer : B
Explanation:
References:
https://www.ibm.com/support/knowledgecenter/SS42VS_7.2.1/com.ibm.qradar.doc_7.2.1/t
_qradar_closing_offenses.html?pos=2
Question 6
What is a primary goal with the use of building blocks?
- A. A method to create reusable rule responses
- B. A reusable test stack that can be used in other rules
- C. A method to generate reference set updates without using a rule
- D. A method to create new events back into the pipeline without using a rule
Answer : B
Question 7
Which set of information is provided on the asset profile page on the assets tab in addition to ID?
- A. Asset Name, MAC Address, Magnitude, Last user
- B. IP Address, Asset Name, Vulnerabilities, Services
- C. IP Address, Operating System, MAC Address, Services
- D. Vulnerabilities, Operative System, Asset Name, Magnitude
Answer : C
Explanation:
References:
https://www.ibm.com/support/knowledgecenter/SS42VS_7.2.1/com.ibm.qradar.doc_7.2.1/c
_qradar_ug_asset_sum.html
Question 8
Which three log sources are supported by QRadar? (Choose three.)
- A. Log files via SFTP
- B. Barracuda Web Filter
- C. TLS multiline Filter
- D. Oracle Database Listener
- E. Sourcefire Defense Center
- F. Java Database Connectivity (JDBC)
Answer : DEF
Question 9
What is the primary goal of data categorization and normalization in QRadar?
- A. It allows data from different kinds of devices to be compared.
- B. It preserves original data allowing for forensic investigations.
- C. It allows for users to export data and import it into other system.
- D. It allows for full-text indexing of data to improve search performance.
Answer : A
Question 10
What is accessible from the Offenses Tab but is not used to present a sorted list of offenses?
- A. Rules
- B. Category
- C. Source IP
- D. Destination IP
Answer : A
Question 11
Given these default options for dashboards on the QRadar Dashboard Tab:
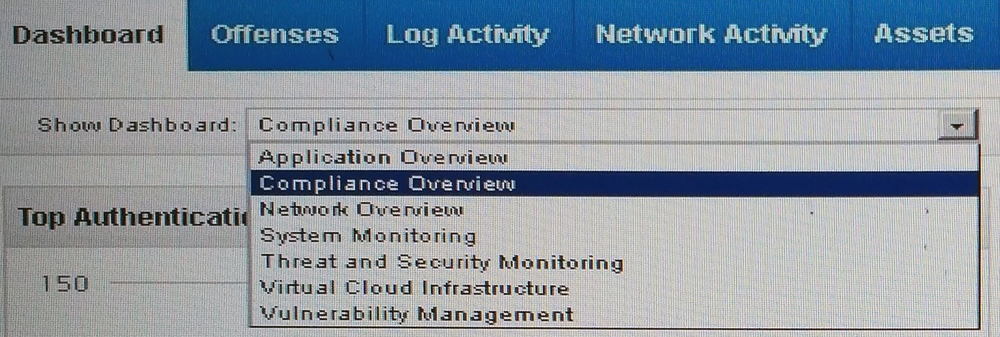
Which will display a list of offenses?
- A. Network Overview
- B. System Monitoring
- C. Vulnerability Management
- D. Threat and Security Monitoring
Answer : D
Question 12
Which QRadar add-on component can generate a list of the unencrypted protocols that can communicate from a DMZ to an internal network?
- A. QRadar Risk Manager
- B. QRadar Flow Collector
- C. QRadar Incident Forensics
- D. QRadar Vulnerability Manager
Answer : A
Question 13
What is the key difference between Rules and Building Blocks in QRadar?
- A. Rules have Actions and Responses; Building Blocks do not.
- B. The Response Limiter is available on Building Blocks but not on Rules.
- C. Building Blocks are built-in to the product; Rules are customized for each deployment.
- D. Building Blocks are Rules which are evaluated on both Flows and Events; Rules are evaluated on Offenses of Flows or Events.
Answer : A
Question 14
A Security Analyst found multiple connection attempts from suspicious remote IP addresses to a local host on the DMZ over port 80. After checking related events no successful exploits were detected.
Upon checking international documentation, this activity was part of an expected penetration test which requires no immediate investigation.
How can the Security Analyst ensure results of the penetration test are retained?
- A. Hide the offense and add a note with a reference to the penetration test findings
- B. Protect the offense to not allow it to delete automatically after the offense retention period has elapsed
- C. Close the offense and mark the source IP for Follow-Up to check if there are future events from the host
- D. Email the Offense Summary to the penetration team so they have the offense id, add a note, and close the Offense
Answer : B
Explanation:
References:
http://www.ibm.com/support/knowledgecenter/SSKMKU/com.ibm.qradar.doc/c_qradar_Off
_Retention.html
Question 15
Which type of tests are recommended to be placed first in a rule to increase efficiency?
- A. Custom property tests
- B. Normalized property tests
- C. Preference set lookup tests
- D. Payload contains regex tests
Answer : B