IBM Cognos Real-time Monitoring Developer v6.0
Question 1
A user is creating a new dashboard in Business Insight. The user chooses a Real-time
Monitoring dashboard object which is built on a cube and adds it to this dashboard.
Theuser then maximizes it. Using the toolbar icons available in the maximized mode, which two actions can the user perform? (Choose two.)
- A. Create watch points.
- B. Create dimension filters.
- C. Change the category.
- D. Create thresholds.
Answer : BC
Question 2
Auser wants to set up an escalation rule for an alert which was still in an exception condition for more than two hours. Which function should be used in the rule?
- A. HOLDS_FOR
- B. IS_RAISED
- C. IS_ACKED
- D. ESCALATE
Answer : B
Question 3
A Real-time Monitoring object has dependent objects. What will happen if this object is deleted with the "Delete Only This Object" option?
- A. The object will not be deleted because itwill invalidate the dependent objects.
- B. The object will be deleted and all its dependents will become dependents of its parent.
- C. The object will be deleted, and the user will be prompted to change the definitions of the dependents.
- D. The object will be deleted and all its dependents will be marked as invalid and disabled.
Answer : D
Question 4
A user wants to build a dashboard for an operations manager who wants to monitor the number of unsatisfied customer calls which were not resolved by thecall center representative and had to be escalated. The operations manager wants to monitor this over five minute intervals, over one day, and compare them with a similar trend over the last ten years. Daily transactional data is stored in a database, andis loaded into a data warehouse nightly for historical analysis and purged weekly. Which two actions achieve this using the
Cognos suite of products? (Choose two.)
- A. Use Real-time Monitoring (RTM) to model both a five minute and a 10-year trend chart using the temporal windows functionality based on the database data only.
- B. Use Business Intelligence to model a 10-year trend chart based on the data warehouse and RTM to model a five minute trend chart based on the database and display them together in the Business Insight workspace.
- C. Use Business Intelligence to model both the 10-year trending and the five-minute trend chart based on the data warehouse and display them in the Business Insight workspace.
- D. Use RTM to model both a five minute and a 10-year trend chart using the temporal windows functionality based on the database data for data streams and the data warehouse for a lookup table.
Answer : BD
Question 5
Which two statements about a public watch point are true? (Choosetwo.)
- A. An e-mail notification can be sent from a public watch point.
- B. Public watch points are visible to all users.
- C. By default, watch points are public.
- D. You cannot change the availability of a watch point after you have saved it.
Answer : BD
Question 6
A customer wants to build a real-time application where streaming data mustbe pushed into
Real-time Monitoring as it changes. Which two agent types accomplish this? (Choose two.)
- A. JDBC
- B. Web Services
- C. JMS
- D. ERP
Answer : BD
Question 7
A customerswitches from internal authentication to external LDAP authentication. They have an existing internal user "Bob" with a password "internal". They have another user named "Bob" in the external LDAP server with password "external". They synchronize the usersfrom the external LDAP server to Real-time Monitoring. Why is the customer unable to login with the username and password "Bob/external"?
- A. Synchronization succeeded and the external user Bob replaced the existing internal user Bob.
- B. Synchronization failed as there was an existing internal user Bob in the metadata, so no new external user was imported.
- C. Synchronization succeeded and the external user Bob was skipped because there was an existing internal user Bob in the metadata.
- D. Synchronization failed but the internal user Bob was deleted and no new external user was imported.
Answer : C
Question 8
An event stream consists of a data stream, a view, and a cube. After each record in the event is processed and updates are applied to the aggregate measures in the cube, what happens to the record andevent information?
- A. A complete history of each record and the processing event it was associated with is maintained.
- B. Only the data record is maintained.
- C. The record and event data are discarded.
- D. The event information is discarded, but the data values are maintained.
Answer : C
Question 9
In an event stream, the data stream query returns 100 total rows on the first polling, 200 rows on the second polling, and 50 rows on the third polling. The "Treat all rows in the result set as a single event" property is selected. If a stateless view is created (with all settings set to default) based on this data stream, how many rows will exist in that view after the third polling?
- A. 1
- B. 50
- C. 200
- D. 350
Answer : B
Question 10
A user wants to analyze a call center's call volume in four regions for each hour over the previous five days. Which three steps allow you to do this? (Choose three.)
- A. Create a stateful view on the data stream which is streaming the call center call data records.
- B. Create a stateless view on the data stream which is streaming the call center call data records.
- C. Group by the column region and timestamp (truncated to an hour) in the view.
- D. Add a windows clause to the view to slide one hour over five days.
- E. Set "maintain in view" to be "120" (24 hours * 5 days = 120).
Answer : ACD
Question 11
A small banking customer is using Real-time Monitoring (RTM) to monitor and notify customers if they are over drafting their checking accounts. Customer information like name and e-mail address are in a DB2database and joined to the data based on the account ID. The customers all have accounts in RTM and are members of the "Customers" role. The alert should only be sent to the primary e-mail account and not shown on the
RTM dashboard. What must you do to accomplish this goal?
- A. Choose the "Account ID" column for a data-driven subscription.
- B. Choose the "Email" column for a data-driven subscription.
- C. Subscribe the "Customers" role to the alert as a mandatory subscriber.
- D. Subscribe each user fromthe "Customers" role to the alert as an optional subscriber.
Answer : B
Question 12
An analyst has been asked to build a rule, alert, and reportlet in Real-time Monitoring
(RTM). The rule that triggers the alert fires when: ord_qty>1000. Areportlet should be attached to the alert containing relevant and supplemental information based on the exception information that the rule detected. The view on which the reportlet is based is grouped by product and defines Average_Quantity as: AVERAGE(ord_qty). When attaching the reportlet the analyst created a rule filter based on the data in the data stream.
The rule filter is defined as: ord_qty > 3000.When attaching a reportlet to an alert, which two descriptions are true? (Choose two.)
- A. The reportlet may include a row where an ord_qty column included in the average is between 1000 and 3000.
- B. The reportlet will never include rows where the Average_Quantity is less than 3000.
- C. The reportlet may be attached without any rows of data.
- D. The reportlet will always include a row for the product that was in the event that triggered the alert.
Answer : BC
Question 13
An organization is using Real-time Monitoring for monitoring business transactions that happen in the previous 24 hours only. The users are only interested in alertswhich are received in the last 24 hours. They also want to see the recent 100 alerts in an Alert
Manager list. Which two include the settings needed to accomplish this? (Choose two.)
- A. Set Maximum alerts to Display to 100.
- B. Set Maximum alerts tobe fired per interval to 100.
- C. Set the Alert Expiration Interval to 1 day.
- D. Set Interval Size to 1440 and Interval Unit to Minutes
Answer : AC
Question 14
Click the Exhibit button.
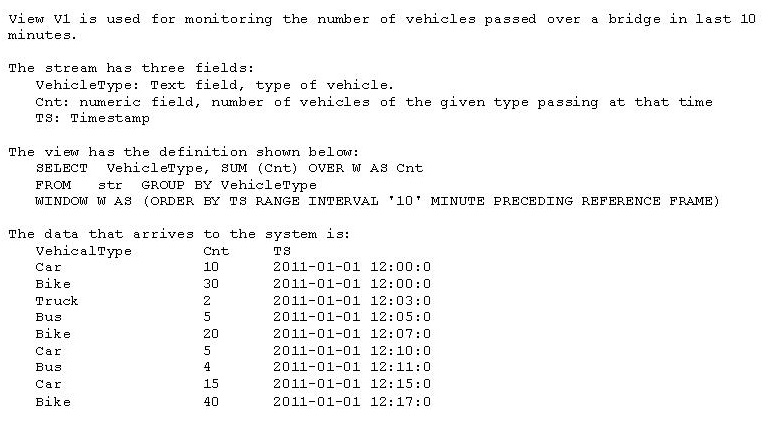
Referring to the exhibit, what will be the contents of view V1?
- A. Bus 9 Truck 2 Bike 40 Car 20
- B. Bus 4Car 40 Bike 20
- C. Bus 4 Car 40 Bike 60
- D. Bus 9Truck 2 Bike 60 Car 20
Answer : D
Question 15
A customer currently has the username and password specified in clear text on the JDBC
URL for their JDBC agent. Their security team has identified this configuration as a security risk for their company. What do you tell the customer?
- A. Specifythe username and password in the corresponding username and password fields.
- B. Use database supported encryption to encode the username and password in the URL.
- C. Use an appserver configured data source instead of the JDBC URL.
- D. Create a separate database user account with limited access.
Answer : C