IBM Cloud Solution Architect v4 v1.0
Question 1
When designing infrastructure for critical business applications, transactional databases, or virtual machines that require low-latency, why might you use Block storage instead of File storage?
- A. Block Storage LUNs have data at rest encryption using in-house managed keys
- B. Block Storage LUNs can be connected to authorized devices through redundant multi-path I/O (MPIO) connections
- C. Block Storage LUNs can be used for file-based NFS shares
- D. Block Storage LUNs can connect to authorized devices in another IBM Cloud datacenter
Answer : B
Reference:
https://cloud.ibm.com/docs/BlockStorage?topic=BlockStorage-getting-started
Question 2
What is IBM Cloud Functions?
- A. A polyglot functions-as-a-service (FaaS) programming platform for lightweight code that executes on demand
- B. A capability of Cloudant for triggering an action as data is updated, for example, sending data updates to systems
- C. An IBM Cloud service for implementing multi-stage business processes involving users and systems
- D. The low-code/no-code development environment for data replication and systems integration in App Connect
Answer : A
Reference:
https://www.ibm.com/cloud/functions
Question 3
A web application has been deployed in an IBM Virtual Private Cloud. In testing, itג€™s discovered that the web server is not responding to requests over the Internet.
What could be the problem?
- A. The web server is in a Security Group which is missing a rule that allows inbound traffic on port 80
- B. The VPCג€™s Vyatta Gateway does not have a NAT configuration for the web server group
- C. The VPC load balancer hasnג€™t been configured with the SSH key for the web server
- D. The subnet ACL has an ALLOW ALL inbound rule set at Priority 1 but a BLOCK ALL inbound rule set at Priority 2
Answer : A
Question 4
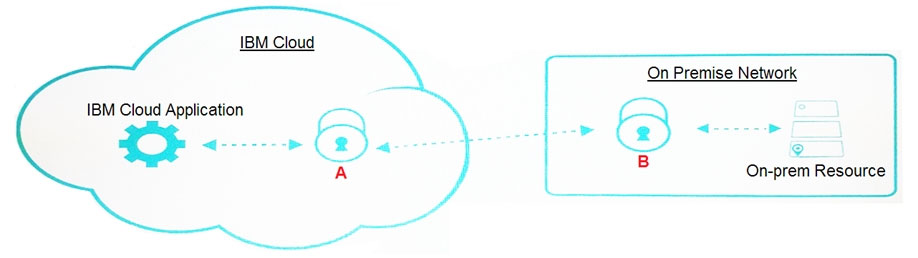
Identify the component marked as B in the Cloud Connection scenario that shows a persistent connection established between the customerג€™s environment and the IBM Cloud.
- A. Virtual Router Appliance
- B. Cloud Gateway Appliance
- C. Secure Gateway Service
- D. Secure Gateway Client
Answer : D
Reference:
https://developer.ibm.com/recipes/tutorials/how-to-integrate-ibm-secure-gateway-to-a-solution/
Question 5
With regards to disaster recover, what industry term describes ג€˜the maximum amount of time it should take to restore application or system functions following a service disruptionג€™?
- A. Restore Point Duration
- B. Recovery Point Objective
- C. Recovery Time Objective
- D. Restore Time Duration
Answer : C
Reference:
https://en.wikipedia.org/wiki/Disaster_recovery
Question 6
What does an IBM Cloud Container Registry provide?
- A. A collection of multiple zones rules that allow inbound connections to reach the cluster services
- B. Multi-tenant, highly available, and scalable private image registry that is hosted and managed by IBM
- C. A collection of multiple regions rules that allow inbound connections to reach the cluster services
- D. Single-tenant, highly available, and scalable private image registry that is hosted and managed by IBM
Answer : B
Reference:
https://cloud.ibm.com/kubernetes/catalog/registry
Question 7
IBM Cloud Activity Tracker with LogDNA service monitors which set of events?
- A. Business processes
- B. How users, applications, and services interact in an account
- C. Payment transactions
- D. Realtime performance
Answer : B
Reference:
https://logdna.com/blog/how-to-monitor-activity-in-your-ibm-cloud-with-logdna/
Question 8
Which of the following is a key features of the IBM Cloud HSM:
- A. Support for HMAC key padding for one-time authentication tokens
- B. Provides CA Issued certificates
- C. Generate, process and store keys
- D. Secure erasure using DoD 5220.22-M Data Wipe Method
Answer : C
Reference:
https://www.ibm.com/cloud/hardware-security-module
Question 9
Which IBM Cloud server also offers a Power architecture on Linux?
- A. Power Systems Virtual Servers
- B. Reserved Virtual Servers
- C. Dedicated Virtual Servers
- D. Virtual Servers for VPC
Answer : A
Reference:
https://cloud.ibm.com/docs/power-iaas?topic=power-iaas-creating-power-virtual-server
Question 10
When creating a Disaster Recovery strategy for an application, which two factors need to be determined as a starting point? (Choose two.)
- A. CSV
- B. RTO
- C. JRB
- D. RPO
- E. JCB
Answer : BD
Reference:
https://searchdisasterrecovery.techtarget.com/definition/disaster-recovery-plan
Question 11
What is the endpoint type created for IBM Cloud Databases by default?
- A. Public
- B. Private
- C. Internet
- D. Back-end
Answer : A
Reference:
https://cloud.ibm.com/docs/databases-for-mongodb?topic=cloud-databases-service-endpoints
Question 12
Which Watson Language Translator feature protects your privacy so you can own your data?
- A. Watson object store for data
- B. Ability to opt-out of any data collection
- C. Ability to stream data over HTTPS
- D. Data privacy plug-in for Watson
Answer : B
Reference:
https://www.ibm.com/watson/services/language-translator/
Question 13
What is API Gateway?
- A. A service used to create, secure, share and manage APIs
- B. A service that provides agility and speed in releasing new APIs functionalities
- C. A tool used to write automated tests, ideally before writing code
- D. A service used to create, secure, share, and manage code
Answer : A
Reference:
https://cloud.ibm.com/docs/api-gateway?topic=api-gateway-whatis_apigw
Question 14
Cloudant is an example of which type of database?
- A. Graph database
- B. Document database
- C. Key-value database
- D. Relational database
Answer : D
Reference:
https://en.wikipedia.org/wiki/Cloudant
Question 15
Which of the following statements describes Helm?
- A. Helm is an OpenStack package manager that uses Heat templates to define, install, and upgrade complex applications
- B. Helm is an open source project to connect, secure, control, and observe Kubernetes services
- C. Helm is a Kubernetes package manager that uses Helm charts to define, install, and upgrade complex Kubernetes apps in your cluster
- D. Helm is used to describe the network of microservices that make up applications in Kubernetes
Answer : C
Reference:
https://helm.sh/