AWS Certified Developer - Associate 2018 v1.0
Question 1
An application has hundreds of users. Each user may use multiple devices to access the application. The Developer wants to assign unique identifiers to these users regardless of the device they use.
Which of the following methods should be used to obtain unique identifiers?
- A. Create a user table in Amazon DynamoDB as key-value pairs of users and their devices. Use these keys as unique identifiers.
- B. Use IAM-generated access key IDs for the users as the unique identifier, but do not store secret keys.
- C. Implement developer-authenticated identities by using Amazon Cognito, and get credentials for these identities.
- D. Assign IAM users and roles to the users. Use the unique IAM resource ID as the unique identifier.
Answer : D
Question 2
An application is designed to use Amazon SQS to manage messages from many independent senders. Each sender"™s messages must be processed in the order they are received.
Which SQS feature should be implemented by the Developer?
- A. Configure each sender with a unique MessageGroupId
- B. Enable MessageDeduplicationIds on the SQS queue
- C. Configure each message with unique MessageGroupIds.
- D. Enable ContentBasedDeduplication on the SQS queue
Answer : C
Reference: https://aws.amazon.com/blogs/developer/how-the-amazon-sqs-fifo-api-works/
Question 3
A deployment package uses the AWS CLI to copy files into any S3 bucket in the account, using access keys stored in environment variables. The package is running on EC2 instances, and the instances have been modified to run with an assumed IAM role and a more restrictive policy that allows access to only one bucket. After the change, the Developer logs into the host and still has the ability to write into all of the S3 buckets in that account.
What is the MOST likely cause of this situation?
- A. An IAM inline policy is being used on the IAM role
- B. An IAM managed policy is being used on the IAM role
- C. The AWS CLI is corrupt and needs to be reinstalled
- D. The AWS credential provider looks for instance profile credentials last
Answer : B
Question 4
A Developer is writing transactions into a DynamoDB table called "SystemUpdates" that has 5 write capacity units.
Which option has the highest read throughput?
- A. Eventually consistent reads of 5 read capacity units reading items that are 4 KB in size
- B. Strongly consistent reads of 5 read capacity units reading items that are 4 KB in size
- C. Eventually consistent reads of 15 read capacity units reading items that are 1 KB in size
- D. Strongly consistent reads of 15 read capacity units reading items that are 1 KB in size
Answer : B
Question 5
Where should an Elastic Beanstalk configuration file named healthcheckur1.config be placed in the application source bundle?
- A. In the root of the application
- B. In the bin folder
- C. In healthcheckur1.config.ebextension under root
- D. In the .ebextensions folder
Answer : D
Reference https://docs.aws.amazon.com/elasticbeanstalk/latest/dg/ebextensions.html
Question 6
During non-peak hours, a Developer wants to minimize the execution time of a full Amazon DynamoDB table scan without affecting normal workloads. The workloads average half of the strongly consistent read capacity units during non-peak hours.
How would the Developer optimize this scan?
- A. Use parallel scans while limiting the rate
- B. Use sequential scans
- C. Increase read capacity units during the scan operation
- D. Change consistency to eventually consistent during the scan operation
Answer : B
Question 7
A Developer is creating a Lambda function and will be using external libraries that are not included in the standard Lambda libraries.
What action would minimize the Lambda compute time consumed?
- A. Install the dependencies and external libraries at the beginning of the Lambda function.
- B. Create a Lambda deployment package that includes the external libraries.
- C. Copy the external libraries to Amazon S3, and reference the external libraries to the S3 location.
- D. Install the external libraries in Lambda to be available to all Lambda functions.
Answer : D
Question 8
A Developer is writing a Linux-based application to run on AWS Elastic Beanstalk. Application requirements state that the application must maintain full capacity during updates while minimizing cost.
Which type of Elastic Beanstalk deployment policy should the Developer specify for the environment?
- A. Immutable
- B. Rolling
- C. All at Once
- D. Rolling with additional batch
Answer : A
Reference:
https://aws.amazon.com/about-aws/whats-new/2016/04/aws-elastic-beanstalk-adds-two-new-deployment-policies-and-amazon-linux-ami-2016-03- update/
Question 9
An application under development is required to store hundreds of video files. The data must be encrypted within the application prior to storage, with a unique key for each video file.
How should the Developer code the application?
- A. Use the KMS Encrypt API to encrypt the data. Store the encrypted data key and data.
- B. Use a cryptography library to generate an encryption key for the application. Use the encryption key to encrypt the data. Store the encrypted data.
- C. Use the KMS GenerateDataKey API to get a data key. Encrypt the data with the data key. Store the encrypted data key and data.
- D. Upload the data to an S3 bucket using server side-encryption with an AWS KMS key.
Answer : B
Question 10
A Developer is creating an application that needs to locate the public IPv4 address of the Amazon EC2 instance on which it runs. How can the application locate this information?
- A. Get the instance metadata by retrieving http://169.254.169.254/latest/metadata/.
- B. Get the instance user data by retrieving http://169.254.169.254/latest/userdata/.
- C. Get the application to run IFCONFIG to get the public IP address.
- D. Get the application to run IPCONFIG to get the public IP address.
Answer : A
Reference: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/using-instance-addressing.html
Question 11
The Lambda function below is being called through an API using Amazon API Gateway. The average execution time for the Lambda function is about 1 second.
The pseudocode for the Lambda function is as shown in the exhibit.
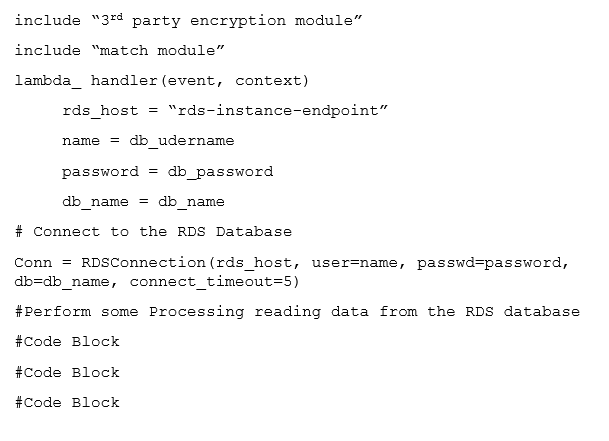
What two actions can be taken to improve the performance of this Lambda function without increasing the cost of the solution? (Select two.)
- A. Package only the modules the Lambda function requires
- B. Use Amazon DynamoDB instead of Amazon RDS
- C. Move the initialization of the variable Amazon RDS connection outside of the handler function
- D. Implement custom database connection pooling with the Lambda function
- E. Implement local caching of Amazon RDS data so Lambda can re-use the cache
Answer : AE
Question 12
An application will ingest data at a very high throughput from many sources and must store the data in an Amazon S3 bucket. Which service would BEST accomplish this task?
- A. Amazon Kinesis Firehose
- B. Amazon S3 Acceleration Transfer
- C. Amazon SQS
- D. Amazon SNS
Answer : A
Question 13
A Developer has setup an Amazon Kinesis Stream with 4 shards to ingest a maximum of 2500 records per second. A Lambda function has been configured to process these records.
In which order will these records be processed?
- A. Lambda will receive each record in the reverse order it was placed into the stream following a LIFO (last-in, first-out) method
- B. Lambda will receive each record in the exact order it was placed into the stream following a FIFO (first-in, first-out) method.
- C. Lambda will receive each record in the exact order it was placed into the shard following a FIFO (first-in, first-out) method. There is no guarantee of order across shards.
- D. The Developer can select FIFO, (first-in, first-out), LIFO (last-in, last-out), random, or request specific record using the getRecords API.
Answer : C
Question 14
A static website is hosted in an Amazon S3 bucket. Several HTML pages on the site use JavaScript to download images from another Amazon S3 bucket. These images are not displayed when users browse the site.
What is the possible cause for the issue?
- A. The referenced Amazon S3 bucket is in another region.
- B. The images must be stored in the same Amazon S3 bucket.
- C. Port 80 must be opened on the security group in which the Amazon S3 bucket is located.
- D. Cross Origin Resource Sharing must be enabled on the Amazon S3 bucket.
Answer : C
Question 15
Amazon S3 has the following structure: S3://BUCKET/FOLDERNAME/FILENAME.zip
Which S3 best practice would optimize performance with thousands of PUT request each second to a single bucket?
- A. Prefix folder names with user id; for example, s3://BUCKET/2013-FOLDERNAME/FILENAME.zip
- B. Prefix file names with timestamps; for example, s3://BUCKET/FOLDERNAME/2013-26-05-15-00-00-FILENAME.zip
- C. Prefix file names with random hex hashes; for example, s3://BUCKET/FOLDERNAME/23a6-FILENAME.zip
- D. Prefix folder names with random hex hashes; for example, s3://BUCKET/23a6-FOLDERNAME/FILENAME.zip
Answer : B
Reference:
http://jayendrapatil.com/aws-s3-best-practices/