Designing Blue Prism Process Solutions v1.0
Question 1
ProSafe credit reference agency retrieves data from bank and other credit providers where customers have missed payments or gone into default. The data is very sensitive and fed directly into a Blue Prism work queue via a web service. Blue Prism process must process the data within 4 hours. The Blue Prism solution runs continuously and each case takes approximately 30 seconds to process. It is expected that an average of 10,000 cases per day will be required and up to 10
Blue Prism robots are available.
The Blue Prism solution is sown below:
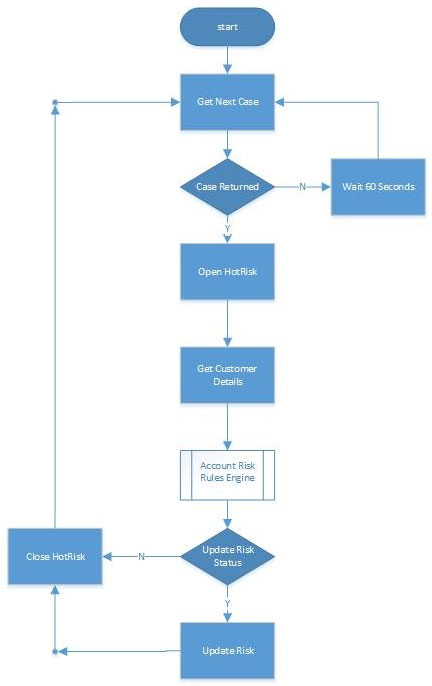
For each case of the process will access the customer account in the HotRisk system and, where an account exists, harvest the data which will be fed along with the Work Queue data into a rules engine. The rules engine is a Blue Prism process that does not interact with any target system. It merely consumes data and, via a complicated series of decision and choice stages, determines the new customer risk factor.
There is to be no scheduler used. Instead the Process Controllers who work in shifts to provide 24 hour support will stop and start process instances in line with
Work Queue volumes.
As a Blue Prism process solution designer, who is reviewing the solution, which of the following would concern you? (Choose three.)
- A. The solution is not scalable.
- B. The process does not have an end stage.
- C. The rules engine has been built in a process not an object.
- D. The process opens and closes the HotRisk system for each case.
- E. The data is too sensitive for automated processing.
- F. There is no scheduler.
Answer : ADF
Question 2
MedBank have recently introduced a new Credit Card platform Cred+. There is a requirement to migrate account and card details from the existing banking platform PCBS on to Cred+.
Account IDs of the cases requiring data transfer will be held on a SQL database. The requirement is that, for each account ID specified on the SQL database, the following data must be read from the PCBS application and input into the Cred+ application:
-> Account ID
-> Product Type
-> Name
-> Address
-> Date of Birth
-> Card PAN (Primary Account Number or credit card number)
-> Card Issue Date
-> Card Expiry Date
Once the data has been successfully input into Cred+ the correct record on the SQL database will be updated to indicate data transfer is complete. All work queues will be encrypted, however due to the sensitivity of the data, MedBank insist that a single robot account does not have access to both PCBS and CRED+ systems.
The following high level design has been proposed:
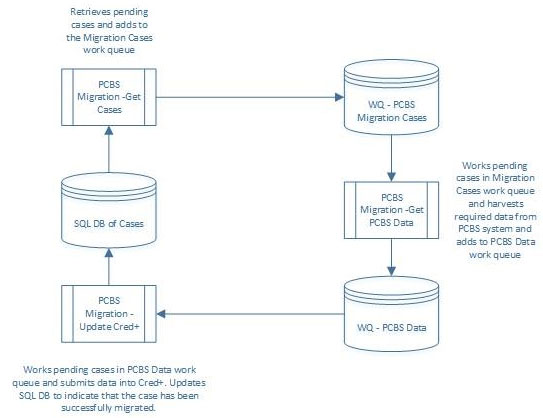
Which of the following statements about the solution design are correct? (Choose two.)
- A. If the PCBS application suffers an outage, all Blue Prism processes specified in this design must stop processing immediately.
- B. The solution enables multiple instances of the Get PCBS Data and Update Cred+ processes to run without risk of collision.
- C. There is a risk that the outcome of a data transfer will not be recorded in the SQL database.
- D. To reduce the elapsed time of the end to end process, the Get Cases process should be run across multiple machines.
- E. The Process Get PCBS Data should be stopped if the Cred+ application suffers an outage to prevent a backlog of cases in the PCBS Data work queue.
- F. Such sensitive data should not be stored in a Blue Prism work queue.
Answer : BE
Question 3
Pacific West Banking has a payments process that automatically receives pending payments from multiple regions into their payment system (Paytex).
Paytex contains a queue of cases awaiting payment. When processing the case manually an agent must use two other systems, the core banking system
(DataPlus) and online account checker (FireWire).
The manual processing must perform the following steps:
-> Open the next case where the status is null in Paytex
-> Set the status to "In Progress" in Paytex
-> Validate source account in DataPlus
-> Confirm source funds in DataPlus
-> Check for fraud flags in Paytex
-> Confirm recipient IBAN details in Firewire
-> Perform payment in Paytex
-> Update case in Paytex queue. Add payment confirmation number to case and set status to "Completed"
-> Where cases cannot be fulfilled due to validation errors (e.g. invalid account details, insufficient funds, suspected fraud etc.) the customers will be contacted by the agent to resolve.
A proposed Blue Prism solution with the following properties has been created to automate the payment processing:
-> There will be one Blue Prism process that will perform the steps described above.
-> Where a case is an exception the status will be set in Paytex to "Manual Review" in order that the manual team can pick up the case from Paytex and contact the customer and conclude the case.
-> It is anticipated that to meet the SLAs of the expected volumes up to 5 instances of the Blue Prism process will be required to run concurrently.
-> A Blue Prism work queue will be used to host the payments. The queue will be configured for only 1 attempt per case and the key will be (region) & {source account number}.
The process will be started by the scheduler at 06:00 and will stop at 05:50.

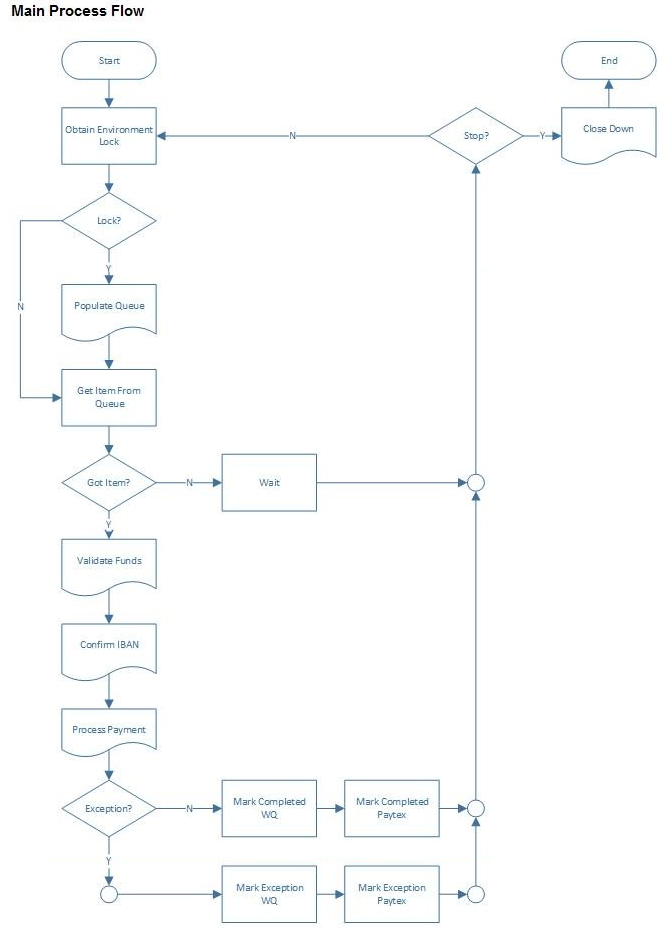
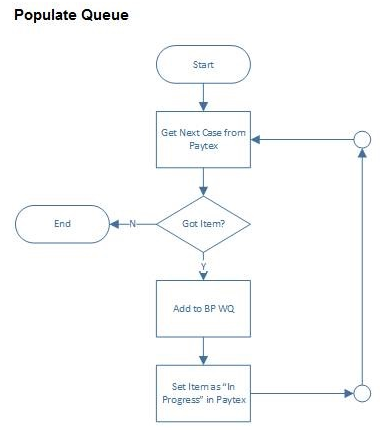
Which of the following are correct? (Choose three.)
- A. There is a risk that a payment can be duplicated.
- B. The process should not be designed to use a Blue Prism Work Queue but use Paytex as the work queue.
- C. The process will not scale i.e. you cannot run multiple instances at the same time.
- D. The solution exposes sensitive personal information.
- E. The process should not be automated as it uses a third party web application.
- F. There is a risk that a payment can be orphaned.
Answer : BCD
Question 4
VivaBank have an account closure process that can take up to three days to close an account. All requests within the bank"™s core system to close an account take place overnight during batch processing. There are two scenarios:
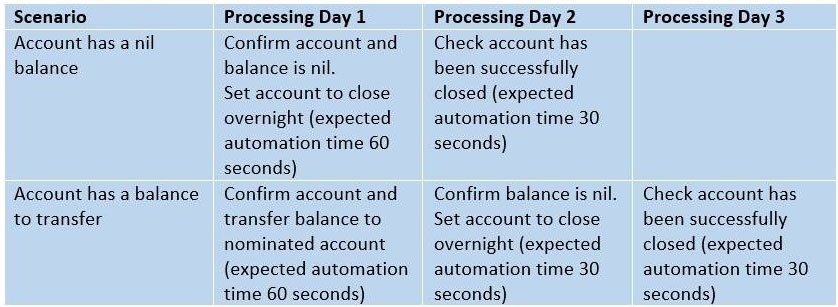
The timings relate to the expected automation time.
All requests will arrive in a Blue Prism work queue from multiple channels using either web services or other Blue Prism processes.
The following detail from the Functional Requirement Questionnaire must be considered:
-> Cases must be processed on the same day if they come in between 08:00 and 22:00 Monday to Friday
-> Exception cases are to be emailed to the manual team during processing as and when they occur.
-> It is expected that up to 200 cases can be expected per day.
The Blue Prism solution consists of four processes and four Blue Prism Work Queues.
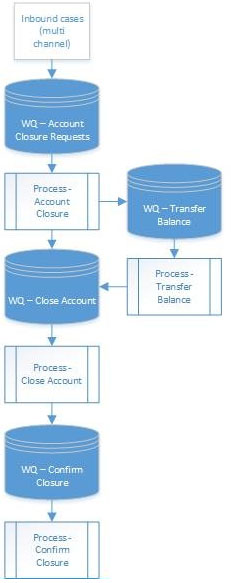
Cases come into the Account Closures Work Queue and are processed by the Account Closure process which determines if they are "Nil Balance" or "Balance to
Transfer" scenarios. Before adding the case to the relevant work queue, a check is made to see if an identical key has been added to the work queue today. If so the case is not added.
The Transfer Balance process work its queue and, for each successfully processed case, adds case to the Close Account queue.
The Close Account process works its queue and, for each successfully processed case, adds a case to the Confirm Closure queue with the case deferred to
08:00 the next day.
The Confirm Closure process completes the sequence by confirming that the account is finally closed.
A scheduler has been created to start all four processes at 08:00. Each process shall be configured to finish accordingly:
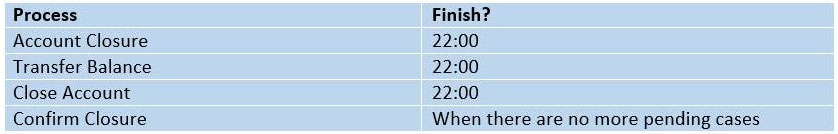
Please select from the statements below the ones you consider to be correct. (Choose two.)
- A. All processes should be merged into one process to optimize licenses.
- B. Exception cases should not be distributed whilst the processes are running and instead should be distributed when each process has completed.
- C. There should be a separate work queue for each channel feeding the process.
- D. The Confirm Closure process should work until 22:00.
- E. As an alternative the solution could use just one queue instead of four.
Answer : CD
Question 5
The following Object Design has been created for a mainframe banking application.
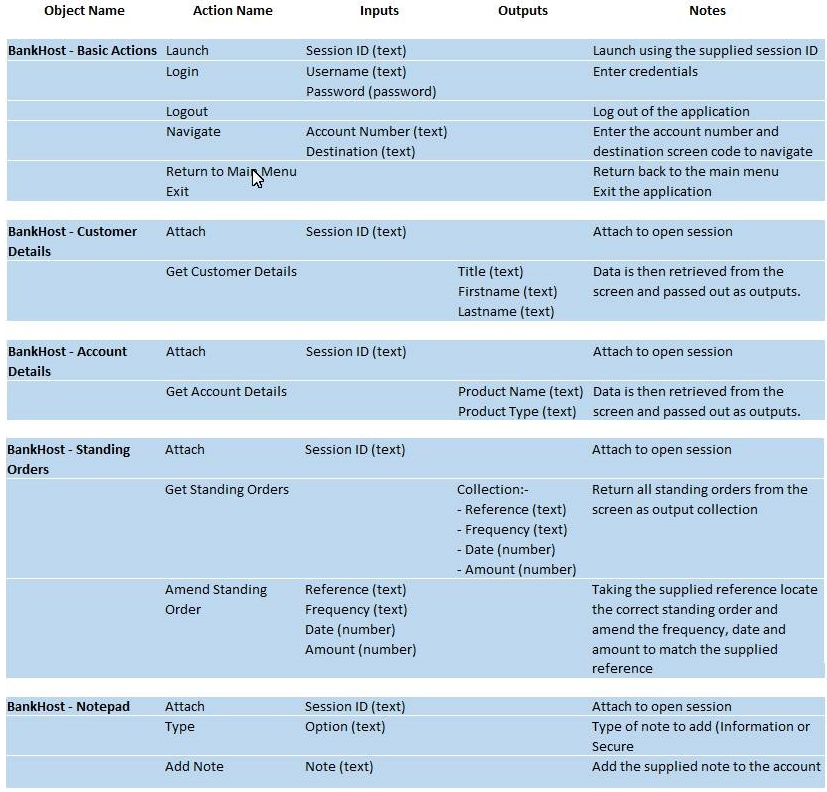
Which of the following statements about the Object design above are correct? (Choose two.)
- A. The Add Note action in the "BankHost "" Notepad" business object does not require an input for Type as the process definition document states that "˜Information"™ will always be selected for this process.
- B. The object design facilitates a scalable design that will reduce the impact of change when the object layer needs altering.
- C. The object design should be simplified by storing all BankHost actions in the same object.
- D. There is no need for attach actions to be replicated across all the objects.
- E. The design complies with Blue Prism design best practice.
Answer : BE
Question 6
Consider the following high-level design. The solution is intended to read medical data from one application in order to update another. An input file is prepared by an overnight batch run for the solution to work through each morning before patients arrive. Usually the input file is fairly small but at certain times each month the file is much larger.
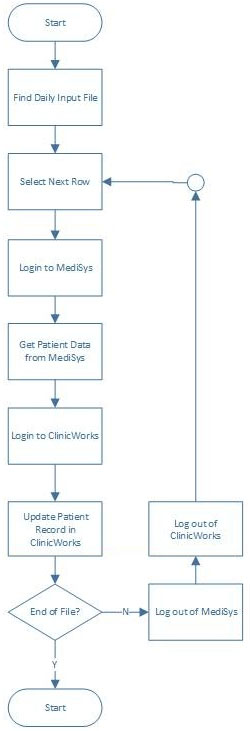
Which of these options should be considered be the process solution designer to guarantee the quality of the end-to-end solution? (Choose four.)
- A. Once in production the process controller should ensure that the process is only ever run on one Resource PC.
- B. The solution should log in to the applications before starting the case working loop.
- C. The solution should split the file into pieces to distribute to each Resource PC.
- D. The solution should log out from applications after existing working loop.
- E. Each Resource PC should be set to take a different row from the others, e.g. RPC-A works rows 1, 4, 7, 10 etc., RPC-B works 2, 5, 8 etc. and RPC-C works 3, 6, 9 etc.
- F. The solution should start by loading the file data into a work queue.
- G. The file should be updated at the start of each case to prevent other RPCs from working it.
- H. Once in production the clinic should wait until the solution has completed before admitting patients.
- I. The batch run should create multiple input files so that each Resource PC has its own file to work with.
- J. The file should be updated after each case to indicate that the case has been worked. K. The solution should use an environment lock to ensure the file can only be accessed by one Resource PC at a time.
Answer : BEGH
Question 7
Consider the following high-level design.
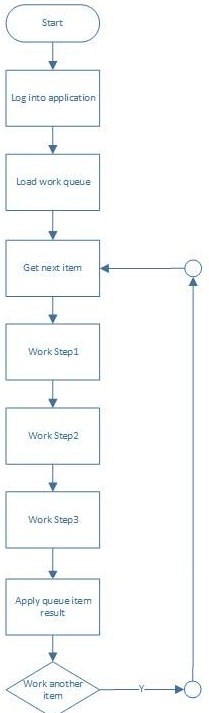
The application concerned is prone to being sluggish or even unresponsive at times. As the solution designer you should anticipate that there will be system exceptions and that after an exception case the application might not be in an ideal state.
What should you do? (Choose three.)
- A. Add "˜clean up"™ logic to get the application in the right position after Apply Queue Item Result.
- B. Kill the application after each case and log back in to ensure the next case starts in the right position.
- C. Instruct the developer to build objects capable of navigating the application back to the home position.
- D. Restart the application if attempts to navigate back to the home position fail.
- E. Move Log Into Application to be before Work Step1 and move Log Out of Application to be after Step3.
- F. Add "˜clean up"™ logic to get the application in the right position before Work Step1.
- G. Add "˜clean up"™ logic to get the application in the right position after Work Step3.
Answer : ABC
Question 8
Consider the following steps for a theoretical manual process.
-> Check in input folder any new files.
-> If there are no files check again later as files can arrive anytime, and there is no limit to the number of files that may come.
-> Open the next available file.
-> Take the first case.
-> Start System X and find the case details.
-> If the case can"™t be found, move to the next one.
-> After finding the case in System X, fetch additional case details from System Y.
-> Again if the case can"™t be found, move to the next one.
-> Analyse all the data to see if System Z should be updated.
-> If the data does not meet the requirements, add notes indicating this to System X and Y and move to the next case.
-> If the data does meet the requirements, update the case in System Z.
-> Add notes to System X and Y and move to the next case.
-> At the end of the file, go back and look for another.
-> Stop checking for new files at 16:00 and finish any remaining cases.
-> When all work is complete create a report of the day"™s exception cases.
Close down Systems X, Y and Z.

If the volume of incoming cases is such that 1 Resource PC can easily handle the workload, which of the following steps for an automated solution should be part of the "˜Preparation"™ phase of an automated process?
- A. Check input folder, wait for files.
- B. Check input folder, wait for files, read file and load queue.
- C. Log into applications.
- D. Check input folder, wait for files, read file and load queue, log into applications.
Answer : C
Question 9
Consider the following steps for a theoretical manual process.
-> Check in input folder any new files.
-> If there are no files check again later as files can arrive anytime, and there is no limit to the number of files that may come.
-> Open the next available file.
-> Take the first case.
-> Start System X and find the case details.
-> If the case can"™t be found, move to the next one.
-> After finding the case in System X, fetch additional case details from System Y.
-> Again if the case can"™t be found, move to the next one.
-> Analyse all the data to see if System Z should be updated.
-> If the data does not meet the requirements, add notes indicating this to System X and Y and move to the next case.
-> If the data does meet the requirements, update the case in System Z.
-> Add notes to System X and Y and move to the next case.
-> At the end of the file, go back and look for another.
-> Stop checking for new files at 16:00 and finish any remaining cases.
-> When all work is complete create a report of the day"™s exception cases.
-> Close down Systems X, Y and Z.
If it is possible that there are long intervals between files arriving, what are the alternatives the process should take to control System X, System Y and System Z?
(Choose two.)
- A. Nothing because they will not have been started if no files have arrived yet.
- B. Nothing, just leave them logged in until more work arrives.
- C. Minimize them to keep the desktop clear.
- D. Close Y and Z down but keep X open because it is the first application needed to work a case.
- E. Log out while waiting and log back in when a file arrives.
- F. Stop them from timing out by keeping them active while waiting for files.
Answer : BE
Question 10
Consider the following steps for a theoretical manual process.
-> Check in input folder any new files.
-> If there are no files check again later as files can arrive anytime, and there is no limit to the number of files that may come.
-> Open the next available file.
-> Take the first case.
-> Start System X and find the case details.
-> If the case can"™t be found, move to the next one.
-> After finding the case in System X, fetch additional case details from System Y.
-> Again if the case can"™t be found, move to the next one.
-> Analyse all the data to see if System Z should be updated.
-> If the data does not meet the requirements, add notes indicating this to System X and Y and move to the next case.
-> If the data does meet the requirements, update the case in System Z.
-> Add notes to System X and Y and move to the next case.
-> At the end of the file, go back and look for another.
-> Stop checking for new files at 16:00 and finish any remaining cases.
-> When all work is complete create a report of the day"™s exception cases.
-> Close down Systems X, Y and Z.
It is imperative that notes are applied to System X and Y, regardless of whether System Z is updated or not, what could the process do? (Choose two.)
- A. Add all notes before attempting to update System Z.
- B. Create an unhappy path where notes are added as part of exception handling.
- C. Add notes before rejecting a case as a Business Exception.
- D. Create new cases for any cases not found in Systems X and Y so that notes can be added.
Answer : AD
Question 11
Imagine you are designing the application integration logic for a solution. One of the applications involved is one you have not automated before but it is widely used and the project is the first in a series for this client.
Which of the following are valid considerations when designing business objects? (Choose two.)
- A. It"™s best that objects are designed to be reusable and are not made bespoke for one process.
- B. The first Production process to automate an application should not share its integration logic with any other because there will invariably be teething problems during an initial implementation.
- C. When an application is automated for the first time a single business object should be used to isolate the first process from any that follow.
- D. Any new application should be assessed to find the appropriate integration technique and identify any potential technical issues.
- E. It"™s best that each process uses its own business objects to keep it separate from any other.
Answer : AB
Question 12
When designing business objects which of the following statements is true? (Choose three.)
- A. It"™s best practice to keep application logic in one business object so that there is a single point of reference.
- B. It"™s good practice to split application logic into multiple objects so that the process is more efficient.
- C. It"™s good practice to keep application logic in one business object so that developers know where to find.
- D. It"™s good practice to keep application logic in one business object to minimize the process dependencies.
- E. It"™s a good practice to split application logic into multiple objects to minimize the process dependencies.
- F. It"™s a good practice to split application logic into multiple objects to minimize the effect of change.
- G. It"™s a good practice to keep application logic in one business object so that the process is more efficient.
Answer : ADF
Question 13
You are the Lead Developer tasked with delivering four processes for the same client. You have enough developers in the team to develop all the processes in parallel. All the processes have one application in common, another application is used by two processes and one process uses an application that none of the others do.
Which of the following statements is true?
- A. Other than the standard utilities, there should be 3 objects.
- B. Other than the standard utilities, there should be 4 objects.
- C. Other than the standard utilities, there should be 7 objects.
- D. It"™s not possible to determine how many objects there should be.
Answer : C
Question 14
It"™s technically possible for one business object to call another. Outside of using utility objects are any of the following valid reasons why you would want to do this?
- A. No. objects should never call other objects.
- B. Yes but object calling other objects could lead to undesirable memory problems so care must be taken.
- C. Yes, to create a wrapper object as a vehicle for a reusable sequence of application logic.
- D. Yes, but only if the object is calling itself.
Answer : C
Question 15
A process is required for a client in the banking sector that involves using an application to transfer funds between accounts. A strong security model is in place to prevent any malicious activity but the client is nervous about the risk of external problems, like a power cut leaving a case in an incomplete state or a fault in the source data causing a case to be duplicated or an excessively large transfer to be made.
What should be included in the solution design? (Choose three.)
- A. A different queue for each major processing step.
- B. A different process for each major processing step.
- C. A single queue that is cleared of all worked items at the start of each day.
- D. Rules to limit transaction values.
- E. A key value that will uniquely identify queue items.
- F. A requirement that the solution is never run on more than one machine.
- G. An exception handling procedure to track manual referrals.
Answer : BDE