Accredited Configuration Engineer v1.0
Question 1
Which of the following is NOT a valid option for builtin CLI Admin roles?
- A. deviceadmin
- B. superuser
- C. devicereader
- D. read/write
Answer : D
Question 2
Which of the Dynamic Updates listed below are issued on a daily basis?
- A. Applications
- B. BrightCloud URL Filtering
- C. Applications and Threats
- D. Antivirus
Answer : BD
Question 3
In PANOS 6.0 and later, which of these items may be used as match criterion in a PolicyBased Forwarding Rule? (Choose three.)
- A. Source User
- B. Source Zone
- C. Destination Zone
- D. Application
Answer : ABD
Question 4
What is the maximum file size of .EXE files uploaded from the firewall to WildFire?
- A. Always 2 megabytes.
- B. Always 10 megabytes.
- C. Configurable up to 2 megabytes.
- D. Configurable up to 10 megabytes.
Answer : D
Question 5
Which of the following most accurately describes Dynamic IP in a Source NAT configuration?
- A. The next available address in the configured pool is used, and the source port number is changed.
- B. A single IP address is used, and the source port number is unchanged.
- C. A single IP address is used, and the source port number is changed.
- D. The next available IP address in the configured pool is used, but the source port number is unchanged.
Answer : A
Question 6
All of the interfaces on a Palo Alto Networks device must be of the same interface type.
- A. True
- B. False
Answer : B
Question 7
With IKE Phase 1, each device is identified to the other by a Peer ID. In most cases, the Peer ID is just the public IP address of the device. In situations where the public IP address is not static, the Peer ID can be a text value.
- A. True
- B. False
Answer : A
Question 8
Which of the following facts about dynamic updates is correct?
- A. Antivirus updates are released daily. Application and Threat updates are released weekly.
- B. Application and Antivirus updates are released weekly. Threat and "Threat and URL Filtering" updates are released weekly.
- C. Application and Threat updates are released daily. Antivirus and URL Filtering updates are released weekly.
- D. Threat and URL Filtering updates are released daily. Application and Antivirus updates are released weekly.
Answer : A
Question 9
"What is the result of an Administrator submitting a WildFire report"™s verdict back to Palo Alto Networks as "Incorrect"?
- A. The signature will be updated for False positive and False negative files in the next AV signature update.
- B. The signature will be updated for False positive and False negative files in the next Application signature update.
- C. You will receive an email to disable the signature manually.
- D. You will receive an update within 15 minutes.
Answer : A
Question 10
When configuring the firewall for UserID, what is the maximum number of Domain Controllers that can be configured?
- A. 100
- B. 50
- C. 10
- D. 150
Answer : A
Question 11
In a Palo Alto Networks firewall, every interface in use must be assigned to a zone in order to process traffic.
- A. True
- B. False
Answer : A
Question 12
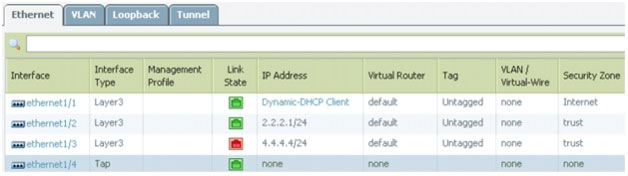
Taking into account only the information in the screenshot above, answer the following question. An administrator is pinging 4.4.4.4 and fails to receive a response. What is the most likely reason for the lack of response?
- A. The interface is down.
- B. There is a Security Policy that prevents ping.
- C. There is no Management Profile.
- D. There is no route back to the machine originating the ping.
Answer : C
Question 13
Which type of license is required to perform Decryption Port Mirroring?
- A. A free PANPADecrypt license
- B. A subscriptionbased
- C. SSL Port license
- D. A Client Decryption license
- E. A subscriptionbased PANPADecrypt license
Answer : A
Question 14
In which of the following can UserID be used to provide a match condition?
- A. Security Policies
- B. NAT Policies
- C. Zone Protection Policies
- D. Threat Profiles
Answer : A
Question 15
Which of the following are necessary components of a GlobalProtect solution?
- A. GlobalProtect Gateway, GlobalProtect Agent, GlobalProtect Portal
- B. GlobalProtect Gateway, GlobalProtect Agent, GlobalProtect Server
- C. GlobalProtect Gateway, GlobalProtect NetConnect, GlobalProtect Agent, GlobalProtect Portal, GlobalProtect Server
- D. GlobalProtect NetConnect, GlobalProtect Agent, GlobalProtect Portal, GlobalProtect Server
Answer : A