Mobility and Devices Fundamentals v1.0
Question 1
What are two ways to lower the risk of a virus or malware infection? Choose two.
- A. Enable the Windows firewall
- B. Use only HTTPS while web surfing
- C. Keep the system updated
- D. Install a download manager
Answer : AC
Question 2
DRAG DROP -
You are setting up the networking for a single-site motel. For three different classes of users, you need to specify the most privileged network segment each can access.
Match each network to the class of users that cam access it.
Instructions: To answer, drag the appropriate network from the column of the left to the class of users on the right. Each network may be used once, more than once, or not at all. Each correct match is worth one point.
Select and Place:
Answer : 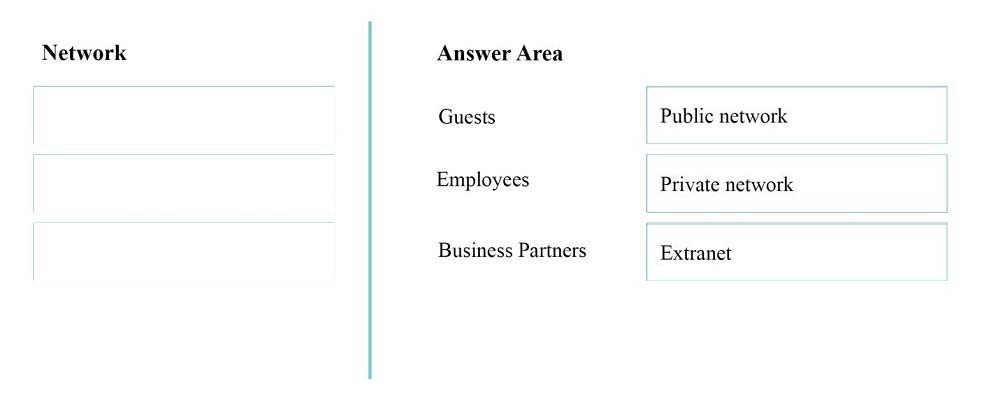
* Guest have only public access.
* Only the Employees have access to the private network.
* An extranet is a private network that uses Internet technology and the public telecommunication system to securely share part of a business's information or operations with suppliers, vendors, partners, customers, or other businesses.
Reference:
http://en.wikipedia.org/wiki/Extranet
Question 3
What is an example of the way in which a Trojan horse commonly spreads to other computers?
- A. It inserts copies of itself into other computer programs
- B. It traverses a network by exploiting a vulnerability
- C. It pretends to be a document from a friend
- D. It downloads from an infected web page
Answer : D
Trojan horses are commonly found on websites that offer free software, such as shareware programs. These communal gathering spots on the Web give Trojan horse writers a degree of anonymity along with the chance of attacking as many random victims as possible. Since website operators rarely have time to thoroughly examine every file posted, an occasional Trojan horse can slip through the checking procedures unnoticed. -
Reference: HOW TROJAN HORSES SPREAD
http://etutorials.org/Misc/computer+book/Part+2+Dangerous+Threats+on+the+Internet/Chapter+8+Trojan+Horses-+Beware+of+Geeks+Bearing+Gifts/HOW
+TROJAN+HORSES+SPREAD/
Question 4
When you copy a file from one NTFS file system partition to a different NTFS partition, what happens to the file permissions of the copied file?
- A. They are the combined permissions of the original file and destination folder
- B. They inherit the permissions of the destination folder
- C. They remain the same as the original
- D. They are removed, and only the creator is given full control
Answer : B
When you copy a protected file to a folder on the same, or a different volume, it inherits the permissions of the target directory.
Reference:
http://www.ntfs.com/ntfs-permissions-files-moving.htm
Question 5
Which type of information about users does biometrics evaluate?
- A. phrases a user has memorized
- B. where a user is located
- C. physical characteristics of a user
- D. objects a user carries with him or her
Answer : C
Biometrics refers to authentication techniques that rely on measurable physical characteristics that can be automatically checked.
Note: There are several types of biometric identification schemes: face: the analysis of facial characteristics fingerprint: the analysis of an individual's unique fingerprints hand geometry: the analysis of the shape of the hand and the length of the fingers retina: the analysis of the capillary vessels located at the back of the eye iris: the analysis of the colored ring that surrounds the eye's pupil signature: the analysis of the way a person signs his name. vein: the analysis of pattern of veins in the back if the hand and the wrist voice: the analysis of the tone, pitch, cadence and frequency of a person's voice.
Reference:
http://www.webopedia.com/TERM/B/biometrics.html
Question 6
This question requires that you evaluate the underlined text to determine if it is correct.
When you access a file located on a shared resource, the "most restrictive" permissions take precedence.
Instructions: Review the underlined text. If it makes the statement correct, select "No change is needed". If the statement is incorrect, select the answer choice than makes the statement correct.
- A. No change is needed.
- B. ACL
- C. NTFS
- D. share
Answer : A
When using share permissions and NTFS permissions together, if there is a conflict in the configuration, the most restrictive permission prevails.
Reference:
http://www.ntfs.com/ntfs-permissions-combined.htm
Question 7
Which is a feature Active Directory Rights Management Services (AD RMS)?
- A. manages Digital Rights Media (DRM) for digital media
- B. provides a permissions system that works with any cloud-based storage solution
- C. manages share and file permissions on all servers in enterprise
- D. allow users to define who can open, modify, print, or forward a document
Answer : D
Windows Rights Management Services (also called Rights Management Services, Active Directory Rights Management Services or RMS) is a form of Information
Rights Management used on Microsoft Windows that uses encryption and a form of selective functionality denial for limiting access to documents such as corporate e-mail, Word documents, and web pages, and the operations authorized users can perform on them. Companies can use this technology to encrypt information stored in such document formats, and through policies embedded in the documents, prevent the protected content from being decrypted except by specified people or groups, in certain environments, under certain conditions, and for certain periods of time.
Reference:
http://en.wikipedia.org/wiki/Active_Directory_Rights_Management_Services
Question 8
You have an external monitor connected to a laptop computer that is running Windows 10. The monitors are configured to provide a panoramic display that continues across both monitors.
You want to move the system tray to the secondary monitor. Both monitors must continue to display screen data.
Which Display setting you select?
- A. Custom scaling
- B. Show only on 2
- C. Extend desktop to this display
- D. Make this my main display
Answer : D
References:
https://www.tenforums.com/tutorials/3871-change-main-display-windows-10-a.html
Question 9
Your parents want you to help them protect a tax return file that is on their computer. You use BitLocker to encrypt the hard drive that contains the file. You then make a backup copy of the file.
What will occur if you attempt to copy the backup copy to a USB flash drive?
- A. The backup copy will remain encrypted
- B. BitLocker will encrypt the USB flash drive
- C. BitLocker will prevent you from moving the file
- D. The backup copy will be decrypted
Answer : A
References:
https://social.technet.microsoft.com/Forums/en-US/94951675-b9ac-4ba2-880d-2da98defd560/bitlocker-does-not-decrypt-files-when-moving-file-from-hard-drive- to-another-device
Question 10
HOTSPOT -
A computer running Microsoft Windows 10 Pro includes the following disk partitions:
-> Drive C: internal hard disk formatted as NTFS.
-> Drive D: internal hard disk formatted as NTFS.
-> Drive F: USB disk formatted as FAT32.
You enable encrypting file system (EFS) encryption on a folder on drive C:.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Hot Area:
Answer : 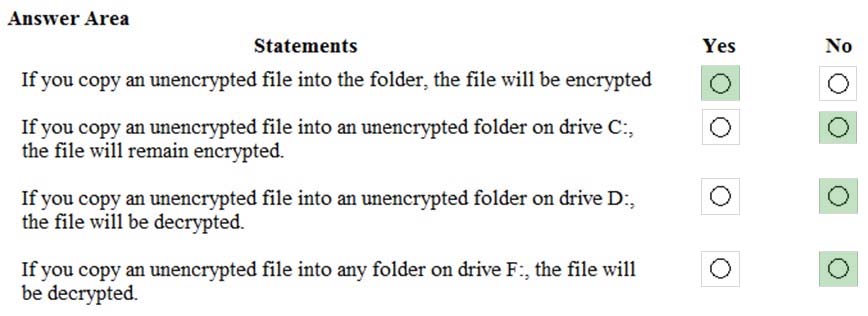
References:
https://www.tenforums.com/tutorials/77130-encrypt-files-folders-efs-windows-10-a.html
Question 11
This question requires that you evaluate the underlined text to determine if it is correct.
You have a Windows 10 computer that is part of a workgroup. To share the C:\Work folder from the computer and make it available to offline users, you need to use the public share option.
Review the underlined text, if it makes the statement correct, select "No change is needed". If the statement is incorrect, select the answer choice than makes the statement correct.
- A. No change is needed
- B. advanced
- C. HomeGroup
- D. basic
Answer : B
References:
https://www.digitalcitizen.life/how-customize-your-advanced-network-sharing-settings-windows-81
Question 12
You perform a bare metal installation of Microsoft Windows 10 Enterprise on a new computer. The computer has a single 1 TB hard disk that you configure as a single partition.
Which file system should you use to format the disk partition?
- A. NTFS
- B. ReFS
- C. FAT32
- D. exFAT
Answer : A
Question 13
Your sister is taking a video editing class at school. She purchased a 2-TB USB hard drive to store video files. She wants to connect it to her Windows 10 computer at home. Video file will exceed 5 GB in size.
You need to prepare the new hard drive by formatting it with the appropriate file system.
Which file system should you choose?
- A. FAT
- B. HFS
- C. NTFS
- D. FAT32
Answer : C
References:
https://answers.microsoft.com/en-us/windows/forum/windows_7-files/what-is-the-maximum-file-size-fat-fat32-ntfs-file/1663db6b-490e-4021-9e36-f7a6976ac0c0
Question 14
Which file system format has been adopted by the computer industry as the standard for optical media?
- A. ExFAT
- B. FAT16
- C. ReFS
- D. UDF
Answer : D
References:
https://en.wikipedia.org/wiki/Universal_Disk_Format
Question 15
Your network is configured as an Active Directory Domain Services (AD DS) domain. The company has an Azure AD premium subscription. You need to configure file access and storage to meet the following requirements:
-> Users can access files from any location with any managed devices without connecting to the corporate network.
-> Users can access local copies of files when they are not connected to the Internet.
-> Files will sync automatically when connected to the Internet.
What should you configure?
- A. Work Folders
- B. Offline folders
- C. Company Portal
- D. RemoteApp
Answer : A
References:
https://docs.microsoft.com/en-us/windows-server/storage/work-folders/work-folders-overview