Database Fundamentals v1.0
Question 1
You need to populate a table named EmployeeCopy with data from an existing table named Employee.
Which statement should you use?

- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer : D
Question 2
You execute the following statement:
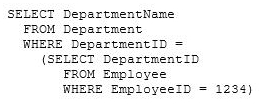
This statement is an example of a/an:
- A. Subquery
- B. Union
- C. Outer join
- D. Cartesian product
Answer : A
Question 3
Which keyword would you use in a select statement to return rows that meet a specific condition?
- A. WHERE
- B. UNION
- C. ORDER BY
- D. FROM
Answer : A
Question 4
You have a table named Employee that includes the following columns:
EmployeeID -
Smp1oyeeName -
Which statement should you use to return the number of rows in the table?

- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer : D
Question 5
The Product table contains the following data.
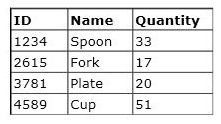
You execute the following statement:
SELECT COUNT(*)
FROM Product WHERE Quantity > 18
What is the value returned by this statement?
- A. 1
- B. 2
- C. 3
- D. 4
Answer : C
Question 6
Which command should you use to remove a table from a database?
- A. REMOVE TABLE
- B. UPDATE TABLE
- C. DROP TABLE
- D. DELETE TABLE
Answer : C
Question 7
You need to store the contact information for each student in your school database.
You should store each student's information in a:
- A. Stored procedure
- B. Function
- C. Row
- D. Variable
Answer : C
Question 8
Which category of SQL statements is used to add, remove, and modify database structures?
- A. Data access language (DAL)
- B. Data manipulation language (DML)
- C. Data control language (DCL)
- D. Data definition language (DDL)
Answer : D
Question 9
You have a Customer table and an Order table. You join the Customer table with the Order table by using the CusromerID column.
The results include:
All customers and their orders -

✑ Customers who have no orders
Which type of join do these results represent?
- A. Complete join
- B. Partial join
- C. Inner join
- D. Outer join
Answer : D
Question 10
Data in a database is stored in:
- A. Tables
- B. Queries
- C. Data types
- D. Stored procedures
Answer : A
Question 11
You have a table named Student that contains 100 rows. Some of the rows have a NULL value in the FirstName column.
You execute the following statement:
DELETE FROM Student -
What is the result?
- A. All rows in the table will be deleted.
- B. All rows containing a NULL value in the FirstName column will be deleted.
- C. You will receive an error message.
- D. All rows and the table definition will be deleted.
Answer : A
Question 12
You need to establish a set of permissions that you can routinely assign to new users.
What should you create?
- A. Resource
- B. Group
- C. List
- D. Role
Answer : D
Question 13
Which database term is used to describe the process of applying a backup to a damaged or corrupt database?
- A. Recover
- B. Restore
- C. Commit
- D. Attach
Answer : B
Question 14
You need to disable User1's access to view the data in the Customer table.
Which statement should you use?
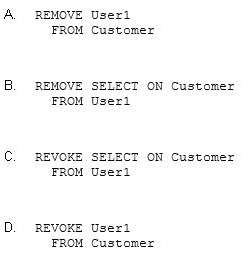
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer : C
Question 15
Denormalization is performed in order to:
- A. Reduce redundancy.
- B. Eliminate repeating groups.
- C. Create smaller tables.
- D. Improve query performance.
Answer : D