LPIC-OT Exam 701: DevOps Tools Engineer v1.0
Question 1
Which of the following tasks are completed by docker-compose down when it is used with additional parameters? (Choose two correct answers.)
- A. Delete all volumes defined in the composer file.
- B. Delete all containers defined in the composer file.
- C. Delete all networks defined in the composer file.
- D. Delete all images used in the composer file from the Docker nodes.
- E. Delete all images built from the composer file from their registry.
Answer : AC
Reference https://docs.docker.com/compose/reference/down/
Question 2
FILL BLANK -
Which statement in a Dockerfile defines which command should be started in the container by default when it is started? (Specify ONLY the statement"™s name without any values or parameters.)
Answer : CMD
Question 3
The following command is issued on two docker nodes:
docker network create --driver bridge isolated_nw
Afterwards, one container is started at each node with the parameter --network=isolated_nw. It turns out that the containers can not interact with each other.
What must be done in order to allow the containers to interact with each other? (Choose two correct answers.)
- A. Use a host network instead of a bridged network.
- B. Add the option --inter-container to the docker network create command.
- C. Start the containers on the same node.
- D. Change the --network parameter of docker create to --network=isolated_nw,nofence.
- E. Use an overlay network instead of a bridged network.
Answer : CD
Reference https://docs.docker.com/v17.09/engine/userguide/networking/#bridge-networks
Question 4
If a Dockerfile references the container"™s base image without a specific version tag, which tag of that image is used to create the container?
- A. latest
- B. default
- C. current
- D. nightly
- E. lts
Answer : A
Reference https://docs.docker.com/engine/reference/commandline/build/
Question 5
FILL BLANK -
Which docker subcommand starts a new container? (Specify only the subcommand without any path or parameters.)
Answer : run
Question 6
Consider the following Kubernetes Deployment:

With the ReplicaSet:
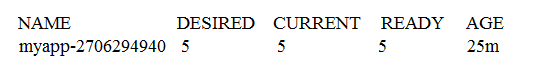
And the Pods:
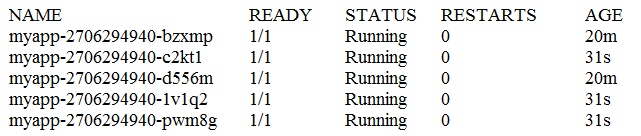
What happens if one of the Pods is terminated with the command kubect1 pod delete?
- A. The remaining Pods are stopped and the Deployment switches to the state Failed.
- B. The number of replicas in the ReplicaSet is changed to 4.
- C. The ReplicaSet immediately starts a new replacement Pod.
- D. The remaining Pods are stopped and a new ReplicaSet is started.
- E. The Deployment switches to the state Degraded.
Answer : B
Question 7
A Dockerfile contains the statements:
COPY data/ /data/
VOLUME /data -
What happens when the resulting container is started without any additional volume configuration? (Choose two correct answers.)
- A. Files existing in /data/ in the image are not available in the running container.
- B. Changes to files within /data/ affect the Docker image and all other containers derived from it.
- C. Existing files from /data/ in the image are copied to the new volume.
- D. An error is raised because /data/ already contains data when the volume is mounted.
- E. A new volume is created and mounted to /data/ within the new container.
Answer : CE
Question 8
Which section of the Prometheus configuration defines which nodes are monitored?
- A. scrape_config
- B. targets
- C. rules
- D. listener
- E. nodes
Answer : A
Reference: https://prometheus.io/docs/prometheus/latest/getting_star
Question 9
Which of the log messages below matches the following Logstash grok filter? grok { match => ["message", "%{SYSLOGBASE} new node %{IPORHOST:node}" ]
}
- A. Jun 30 00:36:49 headnode: new node 198.51.100.103 at clustermanager:12353
- B. Jun 30 00:36:49 headnode clustermanager[12353]: new node 198.51.100.103
- C. Jun 30 00:36:49 headnode clustermanager[198.51.100.103]: new node
- D. %{SYSLOG-FROM:headnode clustermanager[12353]} new node 198.51.100.103
- E. clustermanager[12353]: Jun 30 00:36:49 headnode new node 198.51.100.103
Answer : C
Question 10
A recently installed application writes log data to /opt/app/log/info.log. If Filebeat is already installed and set up for communication with a remote Logstash, what has to be done in order to submit the log data of the new application to Logstash?
- A. Add an additional input channel with the option source => "/opt/app/log/info.log" to the Logstash configuration.
- B. Configure logrotate to execute filebeat ""I /opt/app/log/info.log 0 after each rotation of /opt/app/log/info.log.
- C. Add the log file to the path option within the log prospector in the Filebeat configuration and restart Filebeat.
- D. Add a new cron job that invokes filebeat ""i /opt/app/log/info.log periodically.
- E. Replace /opt/app/log/info.log by a symbolic link to /dev/filebeat and restart the new application.
Answer : E
Question 11
Which sections can exist in a Logstash configuration file? (Choose three correct answers.)
- A. output
- B. filter
- C. input
- D. forward
- E. generate
Answer : ABC
Reference https://www.elastic.co/guide/en/logstash/current/configuration-file-structure.html
Question 12
How does Prometheus gather information about monitored hosts and services?
- A. It implements the ICMP and SNMP protocols to ping and query remote services.
- B. It opens a webhook where monitored applications have to submit various metrics.
- C. It uses HTTP to retrieve JSON encoded metrics from the monitored objects.
- D. It queries a relational database for metrics written to the database by monitored applications.
- E. It runs scripts on the Prometheus server which perform tests and return various metrics.
Answer : E
Reference https://dzone.com/articles/monitoring-with-prometheus
Question 13
A service should be provided to arbitrary clients on the Internet using HTTPS. Any standard client on the Internet should be able to consume the service without further configuration. Which of the following approaches can be used to implement these requirements? (Choose three correct answers.)
- A. Configure the web servers to not use a server certificate when serving HTTPS.
- B. Generate a self-signed certificates during the deployment of each backend server.
- C. Use a certificate issuing service to request certificates during each server deployment.
- D. Use a load balancer that decrypts incoming requests and passes them on in plain HTTP.
- E. Install a wildcard certificate and the respective private key on all the backend servers.
Answer : BCD
Question 14
Which of the following statements is true about load balancers?
- A. Load balancers are a security risk because they obfuscate the origin of connections.
- B. Load balancer help to improve the availability and scalability of a service.
- C. Load balancers are a single point of failure because they cannot be deployed redundantly.
- D. Load balancer require access to private keys in order to be able to forward HTTPS traffic.
- E. Load balancers cannot use connection content, such as HTTP cookies, to route traffic.
Answer : B
Question 15
What does the command packer validate template.json do?
- A. The command verifies that the latest build of the template can be run without downloading additional images or artifacts.
- B. The command verifies that the file template.json is a syntactically correct and complete Packer template.
- C. The command verifies that all existing artifacts generated by template.json have their original checksums.
- D. The command verifies that all source images referenced in template.json are available and have valid cryptographic signatures.
- E. The command verifies that images generated previously by template.json still use the most recent source images.
Answer : B
Reference https://www.packer.io/docs/commands/validate.html