Configuring Windows Devices v1.0
Question 1
You have a computer named Client1. Client1 is joined to an Active Directory domain.
You need to join Client1 to an Azure Active Directory (Azure AD) tenant.
What should you do?
- A. From the Local Group Policy Editor, modify the Add workstations to domain policy.
- B. From the network adapter properties, modify the DNS suffix.
- C. From the System in the Settings app, modify the sign-in options.
- D. From System in Control Panel, configure the computer to be a member of a workgroup.
Answer : C
Question 2
Your network contains an Azure AD domain. You have a subscription to Microsoft Office 365.
Users discover that they must change their Azure AD password more frequently than their Office 365 password.
You need to ensure that the password policies for Office 365 and for Active Directory are the same.
What should you do?
- A. From the Microsoft Azure Active Directory Module for Windows PowerShell, run . Set-MsolDomainAuthentication
- B. From the Office 365 Admin center, in Settings, click Security & privacy.
- C. From the Office 365 portal, under Billing, click Subscriptions.
- D. From the Microsoft Azure Active Directory Module for Windows PowerShell, run . Set-MsolCompanySettings
Answer : D
Explanation:
Directory Synchronization must be enabled. This can be performed using the Set-MsolCompanySettings cmdlet.
Question 3
You are the desktop administrator for a small company.
Your workgroup environment consists of Windows 10 Enterprise computers. You want to prevent 10 help desk computers from sleeping. However, you want the screens to shut off after a certain period of time if the computers are not being used.
You need to configure and apply a standard power configuration scheme for the 10 help desk computers on your network.
Which two actions should you perform? Each correct answer presents part of the solution.
- A. Import the power scheme by using POWERCFG /IMPORT on each of the remaining help desk computers. Set the power scheme to Active by using POWERCFG /S.
- B. Use POWERCFG /X on one help desk computer to modify the power scheme to meet the requirements. Export the power scheme by using POWERCFG / EXPORT.
- C. Use POWERCFG /S on one help desk computer to modify the power scheme to meet the requirements. Export the power scheme by using POWERCFG / EXPORT.
- D. Import the power scheme by using POWERCFG /IMPORT on each of the remaining help desk computers. Set the power scheme to Active by using POWERCFG /X.
Answer : AB
Explanation:
You can use the Powercfg.exe tool to control power settings and configure computers to default to Hibernate or Standby modes.
In this question, we use POWERCFG /X on one help desk computer to modify the power scheme to meet our requirements. After configuring the required settings, we can export the power scheme settings to a file by using POWERCFG /EXPORT.
We can then import the power scheme from the file on each of the remaining help desk computers by using POWERCFG /IMPORT. After importing the power scheme on the remaining computers, we need to set the new power scheme to be the active power scheme by using POWERCFG /S.
References:
https://docs.microsoft.com/en-us/windows-hardware/design/device-experiences/powercfg-command-line-options
Question 4
A company has an Active Directory Domain Services (AD DS) domain. All client computers run Windows 10 Enterprise. Some computers have a Trusted Platform
Module (TPM) chip.
You need to configure a single Group Policy object (GPO) that will allow Windows BitLocker Drive Encryption on all client computers.
Which two actions should you perform? Each correct answer presents part of the solution.
- A. Enable the Require additional authentication at startup policy setting.
- B. Enable the Enforce drive encryption type on operating system drives policy setting.
- C. Enable the option to allow BitLocker without a compatible TPM.
- D. Configure the TPM validation profile to enable Platform Configuration Register indices (PCRs) 0, 2, 4, and 11.
Answer : AC
Explanation:
We need to allow Windows BitLocker Drive Encryption on all client computers (including client computers that do not have Trusted Platform Module (TPM) chip).
We can do this by enabling the option to allow BitLocker without a compatible TPM in the group policy. The "˜Allow BitLocker without a compatible TPM"™ option is a checkbox in the "˜Require additional authentication at startup"™ group policy setting. To access the "˜Allow BitLocker without a compatible TPM"™ checkbox, you need to first select Enabled on the "˜Require additional authentication at startup"™ policy setting.
References:
http://www.howtogeek.com/howto/6229/how-to-use-bitlocker-on-drives-without-tpm/
Question 5
Employees are permitted to bring personally owned portable Windows 10 Enterprise computers to the office. They are permitted to install corporate applications by using the management infrastructure agent and access corporate email by using the Mail app.
An employee"™s personally owned portable computer is stolen.
You need to protect the corporate applications and email messages on the computer.
Which two actions should you perform? Each correct answer presents part of the solution.
- A. Prevent the computer from connecting to the corporate wireless network.
- B. Change the user"™s password.
- C. Disconnect the computer from the management infrastructure.
- D. Initiate a remote wipe.
Answer : BD
Explanation:
The personally owned portable Windows 10 Enterprise computers being managed by the management infrastructure agent enables the use of remote wipe. By initiating a remote wipe, we can erase all company data including email from the stolen device.
Microsoft Intune provides selective wipe, full wipe, remote lock, and passcode reset capabilities. Because mobile devices can store sensitive corporate data and provide access to many corporate resources, you can issue a remote device wipe command from the Microsoft Intune administrator console to wipe a lost or stolen device.
Changing the user"™s password should be the first step. If the stolen computer is accessed before the remote wipe happens, the malicious user could be able to access company resources if the laptop has saved passwords.
References:
https://technet.microsoft.com/en-gb/library/jj676679.aspx
Question 6
You use a Windows 8.1 tablet. The tablet receives Windows Update updates automatically from the Internet.
The tablet has Wi-Fi and is connected to a 3G mobile broadband Wi-Fi hot spot.
You need to minimize data usage while connected to this hot spot.
What should you do?
- A. Turn on Airplane Mode.
- B. Disable File and Print Sharing for mobile broadband connections.
- C. Configure the interface metric of IP settings for Wi-Fi connection as1.
- D. Edit the Inbound Rule of Windows Firewall, and then disable Internet Control Message Protocol (ICMP) traffic.
- E. Configure the broadband connection as a metered network.
Answer : E
Explanation:
You can limit the bandwidth used by the broadband connection by configuring it as a metered network. A metered network is a network where data downloaded is "˜metered"™(measured) and you are charged for the amount of data downloaded.
Setting a connection as metered prevents Windows from automatically using bandwidth in a number of ways including the following:
-> Disables automatic downloading of Windows updates: Windows won"™t automatically download updates from Windows Update on metered Internet connections. You"™ll get a "Download" button you can click whenever you want to install updates.
-> Disables automatic downloading of app updates: The Windows Store won"™t automatically download updates for your installed "Store apps" on metered connections, either. Desktop apps like Chrome, Firefox, and others will continue updating themselves normally.
-> Tiles may not update: Microsoft says that the live tiles on your Start menu or Start screen "may" stop updating on a metered connection:
References:
http://www.howtogeek.com/226722/how-when-and-why-to-set-a-connection-as-metered-on-windows-10/
Question 7
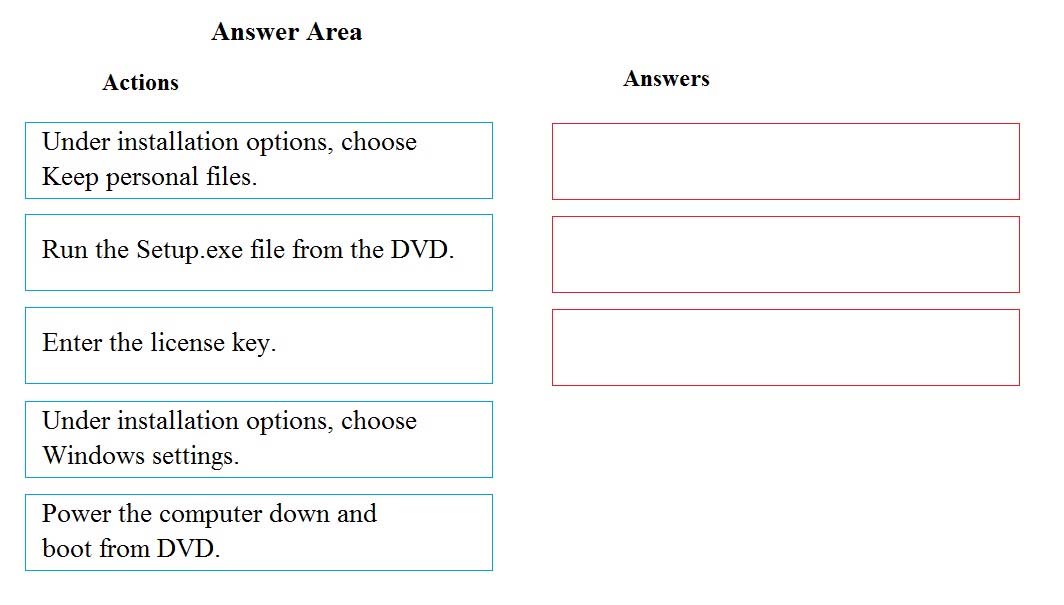
DRAG DROP -
You have a Windows 8 computer. You need to migrate from Windows 8 to Windows 10 while retaining as much data as possible. You load the Windows 10 media into the DVD drive.
Which three actions should you perform next in sequence?
Select and Place:
Answer : 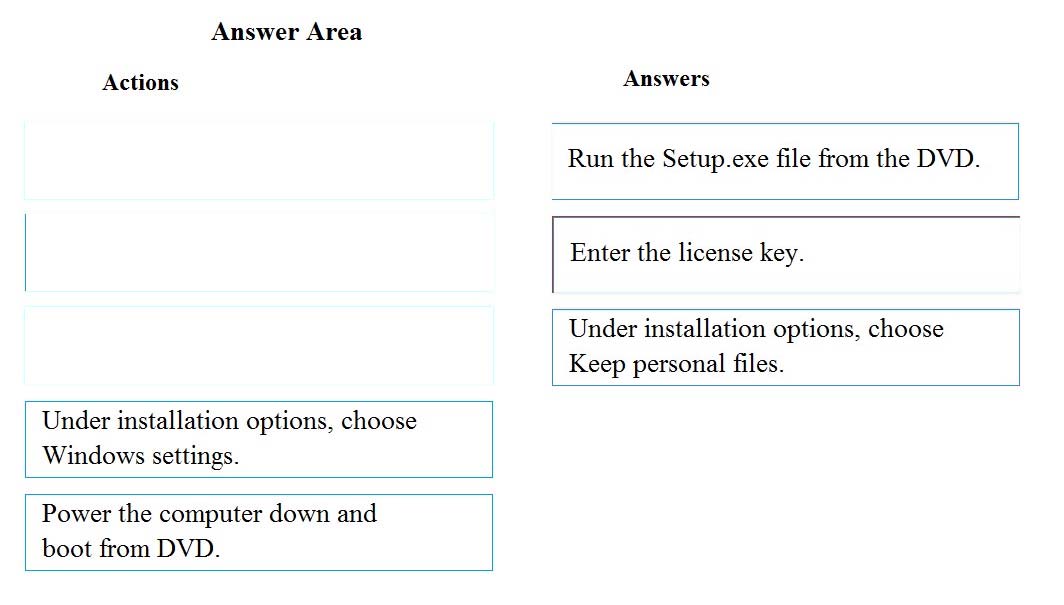
Explanation:
Box 1: Run the Setup.exe file from the DVD.
Launch setup.exe on the DVD drive to start the upgrade process.
Box 2: Enter the license key.
You will be prompted for the license key.
Box 3: Under the installation, choose Keep personal files.
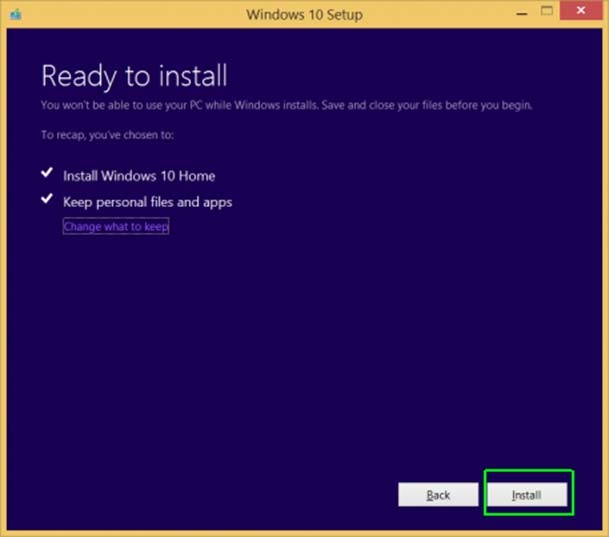
References:
http://www.laptopmag.com/articles/how-to-upgrade-windows-10
Question 8
HOTSPOT -
You plan to use a Group Policy to configure the power settings of several laptops.
You need to ensure that the laptops meet the following requirements:
-> Enter hibernation mode when the lid is closed.
-> Enter sleep mode when the battery level is critical.
Which two Power Management Group Policy settings should you modify? To answer, select the appropriate settings in the answer area.
Hot Area:
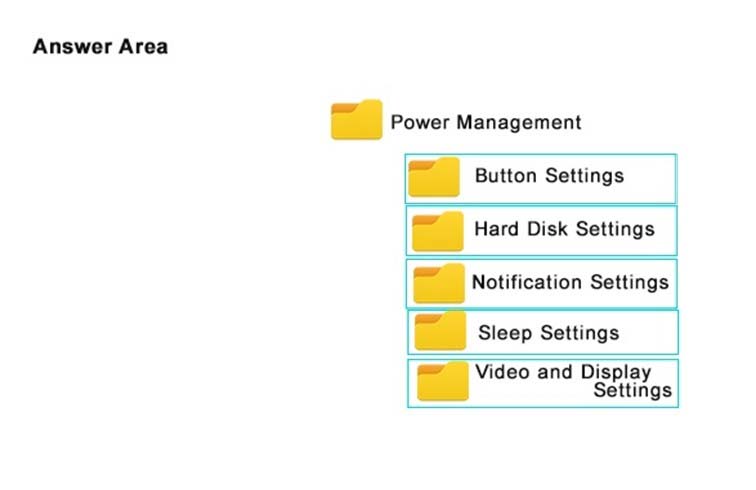
Answer : 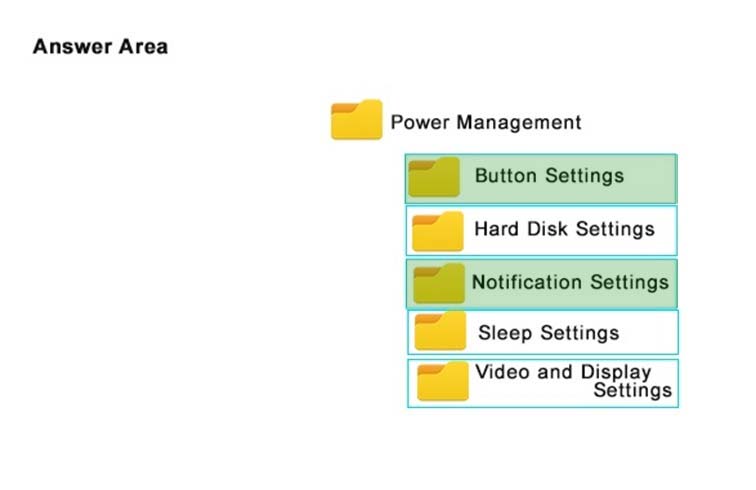
References:
http://www.thewindowsclub.com/change-critical-low-level-battery-action-windows-8-7
Question 9
Your company has a standard power scheme for the sales team. You are replacing a laptop for a sales associate.
You import the power scheme onto the new laptop.
You need to apply the power scheme.
What should you do?
- A. Modify the power scheme under Power and Sleep settings.
- B. Run the gpupdate /F command.
- C. Run the powercfg /S command.
- D. Modify the advanced power settings.
Answer : C
Explanation:
You can use the powercfg.exe tool to control power schemes (also named power plans) to use the available sleep states, to control the power states of individual devices, and to analyze the system for common energy-efficiency and battery-life problems.
The powercfg /SETACTIVE or powercfg /S commands make the specified power scheme active on the system.
Note: To Import a Power Plan -
1. Open an elevated command prompt.
2. Type the command below into the command prompt, and press Enter to export the power plan. powercfg -import "Full path of .pow file"
Note: Substitute Full path of .pow file in the command above with the actual full path of the .pow file of the power plan you exported.
3. When finished, you can close the command prompt if you like.
4. Users on the PC will now be able to select the imported power plan as their active power plan
References:
https://msdn.microsoft.com/en-us/library/dn898599(v=vs.85).aspx https://docs.microsoft.com/en-us/windows-hardware/design/device-experiences/powercfg-command-line-options
Question 10
A company has an Active Directory Domain Services (AD DS) domain with one physical domain controller. All client computers run Windows 10 Enterprise.
A client computer hosts a Windows 10 Enterprise virtual machine (VM) test environment. The VMs are connected to a private virtual switch that is configured as shown in the Virtual Switch Manager exhibit.
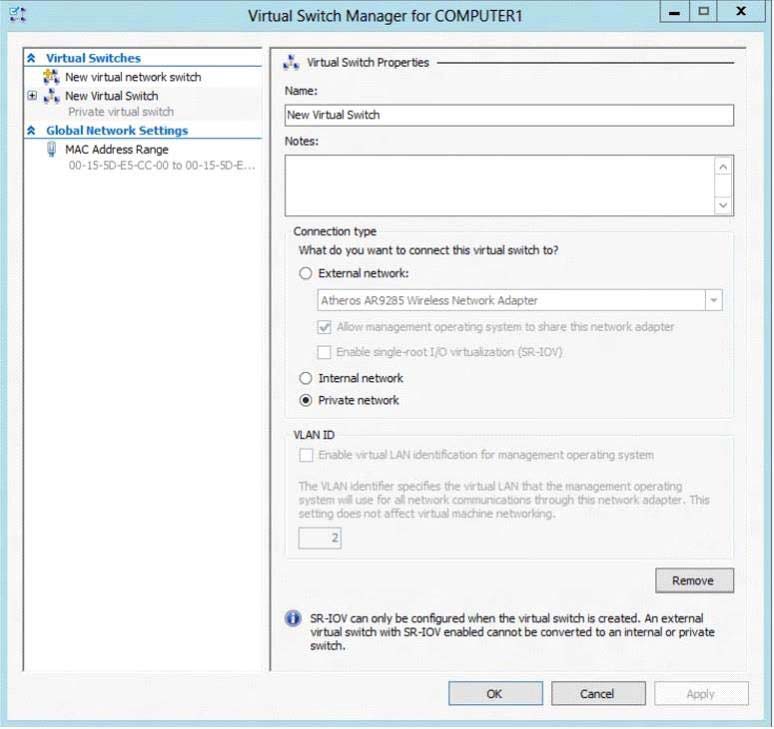
The VMs are unable to connect to the domain controller. You have the following requirements:
-> Configure the test environment to allow VMs to communicate with the domain controller.
Ensure that the VMs can communicate with other VMs in the test environment when the domain controller is unavailable.

You need to meet the requirements.
What should you do first?
- A. Create a new virtual switch with an Internal Network connection type.
- B. Change the connection type of the private virtual switch to Internal only.
- C. Create a new virtual switch with a Private Network connection type.
- D. Create a new virtual switch with an External Network connection type.
Answer : D
Question 11
HOTSPOT -
You install Windows 10 Enterprise on a new laptop that will be shipped to a remote user. You logon to the laptop with the user credentials, map network drives, and configure the network drives to be always available offline.
Company policy requires that files with a .db1 extension should be excluded from offline file synchronization.
You need to prevent the user from creating files with a .db1 extension on the mapped drives.
In the Local Group Policy Editor, which setting should you configure?
To answer, select the appropriate setting in the answer area.
Hot Area:
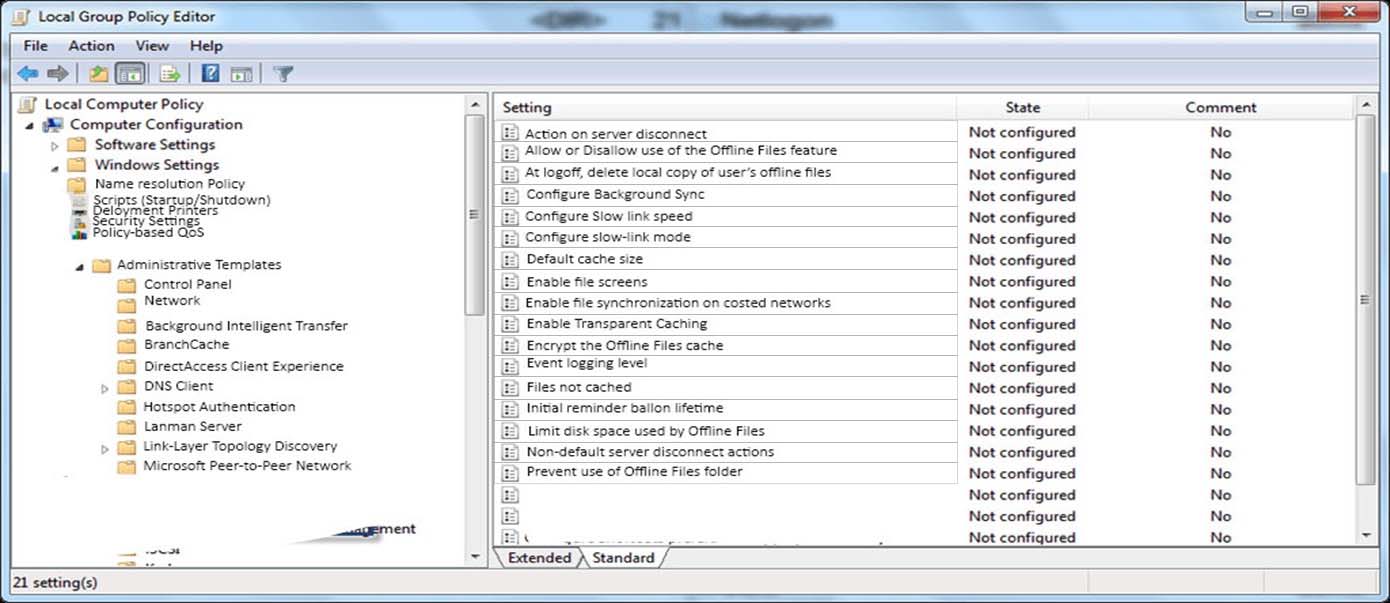
Answer : 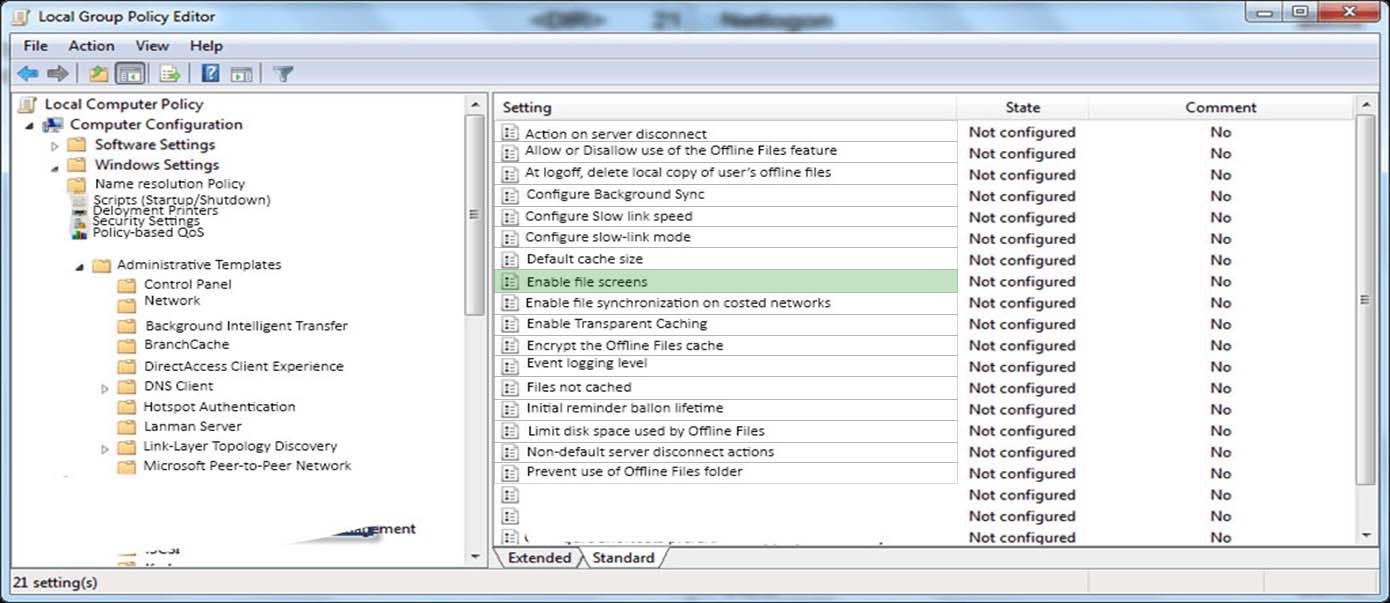
References:
https://www.windows-security.org/1941654bad9040dfcb8ffaba2724b014/enable-file-screens
Question 12
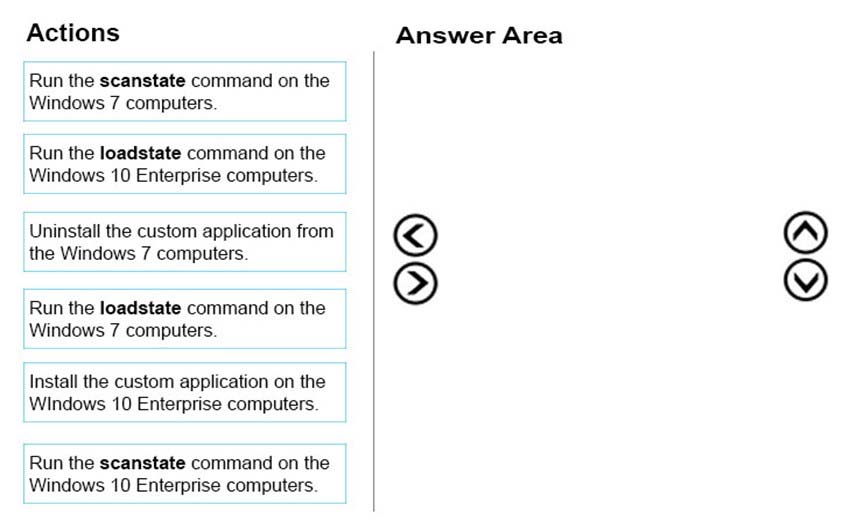
DRAG DROP -
Ten client computers run Windows 7 and a custom application. The custom application is compatible with Windows 10 Enterprise.
You purchase 10 new computers that have Windows 10 Enterprise pre-installed. You plan to migrate user settings and data from the Windows 7 computers to the
Windows 10 Enterprise computers. You add the User State Migration Toolkit (USMT) on a USB flash drive.
You need to ensure that the custom application settings are applied to the Windows 10 Enterprise computers after the migration is complete.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
Answer : 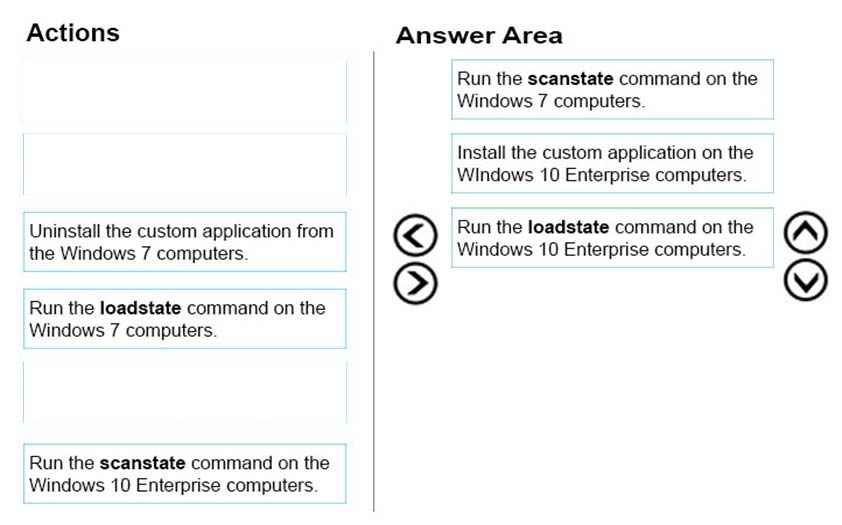
Question 13
DRAG DROP -
You administer Windows 7 and Windows 8 client computers in your company network.
You add 100 new client computers that have Windows 10 Enterprise installed.
You need to migrate user profiles, local groups membership, and network mapped drives to the new client computers. You download and copy User State
Migration Tool (USMT) files to a network share.
Which three actions should you perform next, in sequence? To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
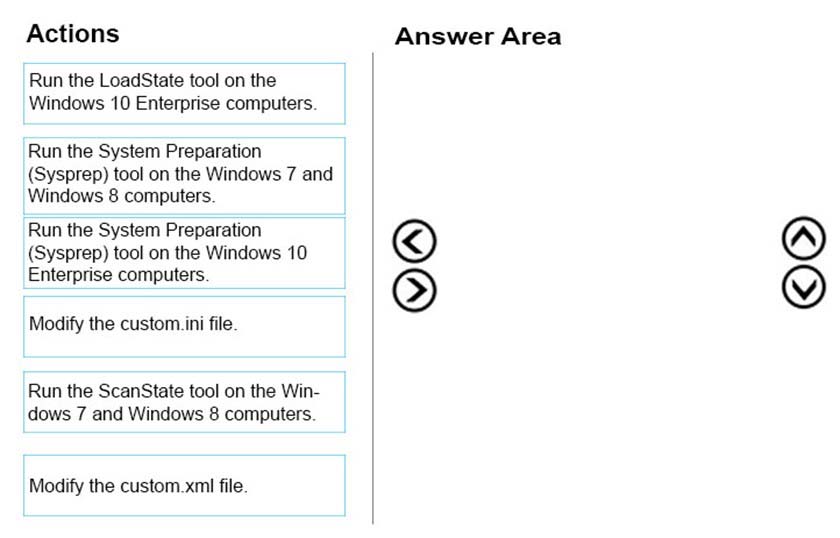
Answer : 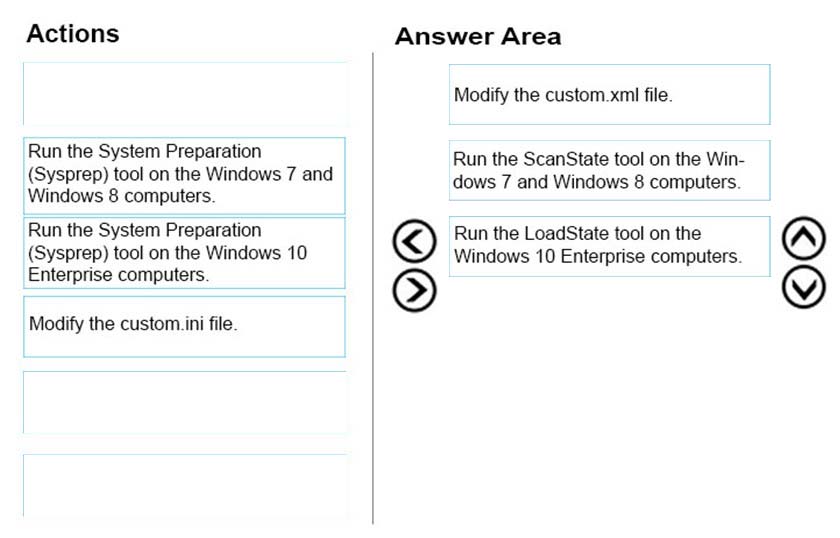
Question 14
You have a computer that runs Windows 10 and has BitLocker Drive Encryption (BitLocker) configured.
You need to change the BitLocker PIN for the drive.
What should you run?
- A. the bitsadmin.exe command
- B. the Enable-BitLocker cmdlet
- C. the Add-BitLockerKeyProtector cmdlet
- D. the Set-PcsvDeviceUserPassword cmdlet
Answer : C
Question 15
You have a computer that runs Windows 10 and has BitLocker Drive Encryption (BitLocker) configured.
You need to change the BitLocker PIN for the drive.
What should you run?
- A. the repair-bde.exe Windows script file
- B. the Enable-BitLocker cmdlet
- C. the bitsadmin.exe command
- D. the manage-bde.exe command D
Answer : Explanation
References:
https://technet.microsoft.com/en-us/library/dd875513(v=ws.10).aspx#BKMK_changepin