Managing and Maintaining Windows 8.1 v13.0
Question 1
You administer desktop computers on your company network.
You want to deploy a WMI file of Windows 8.1 Enterprise to several desktops that have a third-party PCI-X board installed. The hardware vendor provided a device driver to support this board.
You need to customize the image to ensure that the device driver is installed when you deploy the image.
What should you do?
- A. Download and run the imagex.exe tool and specify the /append parameter.
- B. Run the dism.exe tool and specify the /add-driver parameter.
- C. Download and run the drvload.exe tool and specify the path to the driver .inf file.
- D. Run the dism.exe tool and specify the /add-package parameter.
Answer : B
Explanation: After you mount the boot image, use DISM to add optional components to the boot image.
Use DISM to add specific drivers to the boot image, when required. Type the following to add drivers to the boot image, if required: dism.exe /image:C:\WinPEMount /add-driver /driver:< path to driver .inf file >
Reference: How to Customize Windows PE Boot Images to Use in Configuration Manager
Question 2
A company has client computers that run Windows 7. The company plans to migrate all of the client computers to Windows 8.1.
Two custom applications named App1 and App2 are installed on all client computers. A company policy restricts network connectivity when App1 is running. App2 must be run in a centralized environment.
You need to ensure that client computers can run the applications after the migration.
What should you use for each application? (Make only one selection in each column. This question is worth two points.)
Answer : 
Explanation:
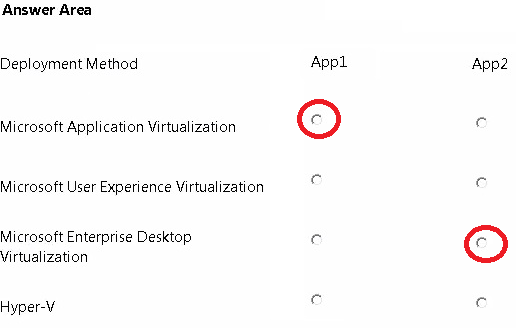
* App1:
Microsoft Application Virtualization (App-V) can make applications available to end user computers without having to install the applications directly on those computers. This is made possible through a process known as sequencing the application , which enables each application to run in its own self-contained virtual environment on the client computer.
The sequenced applications are isolated from each other. This eliminates application conflicts, but the applications can still interact with the client computer.
Question 3
You have several client computers that run Windows 7 Enterprise.
You plan to configure the computers to dual-boot to Windows 8.1 Enterprise by using a native-boot VHD.
You have a VHD file that contains an installation of Windows 8.1 Enterprise,
You need to inject several device drivers into the VHD file.
Which tool should you use?
- A. Bcdedit
- B. Bcdboot
- C. Pkgmgr
- D. Dism
Answer : D
Explanation: Deployment Image Servicing and Management (DISM) is a command-line tool used to service Windows images offline before deployment. You can use it to install, uninstall, configure, and update Windows features, packages, drivers, and international settings. Subsets of the DISM servicing commands are also available for servicing a running operating system.
DISM is installed with Windows 7, and it is also distributed in the Windows OEM
Preinstallation Kit (Windows OPK) and the Windows Automated Installation Kit
(Windows AIK). It can be used to service Windows Vista with Service Pack 1 (SP1),
Windows Server 2008, Windows 7, Windows Server 2008 R2, or Windows PE images. DISM replaces several Windows OPK tools, including PEimg, Intlcfg, and Package
Manager.
http://technet.microsoft.com/en-us/library/dd744256%28v=WS.10%29.aspx
Reference: http://social.technet.microsoft.com/wiki/contents/articles/516.how-to-boot-from- a-vhd.aspx#Add http://technet.microsoft.com/en-us/library/cc749465%28v=WS.10%29.aspx
Package Manager (Pkgmgr.exe) installs, uninstalls, configures, and updates features and packages for Windows Vista. You can install or update Windows Vista feature packages on an offline destination computer by using Package Manager and an unattended installation answer file. http://technet.microsoft.com/en-us/library/hh824874.aspx
BCDboot can update an existing boot environment on the system partition: http://technet.microsoft.com/en-us/library/cc709667%28v=WS.10%29.aspx
BCDEdit is a command-line tool for managing BCD stores. It can be used for a variety of purposes, including creating new stores, modifying existing stores, adding boot menu options, and so on. BCDEdit serves essentially the same purpose as Bootcfg.exe on earlier versions of Window
Question 4
You have a Windows 8.1 computer. You have a 1-terabyte external hard drive.
You purchase a second 1-terabyte external hard drive.
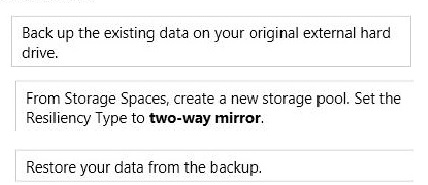
You need to create a fault-tolerant volume that includes both external hard drives. You also need to ensure that additional external hard drives can be added to the volume.
Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
Answer : 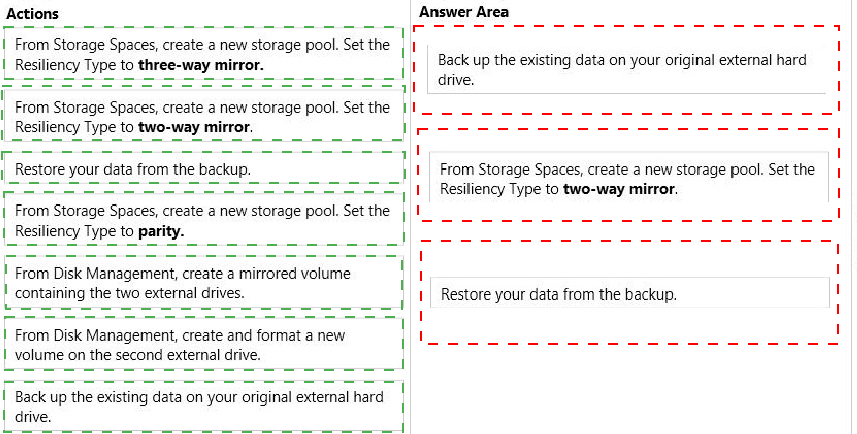
Explanation:
Question 5
Your company has client computers that run either Windows XP or Windows 7.
You plan to deploy Windows 8.1 Enterprise to all of the computers.
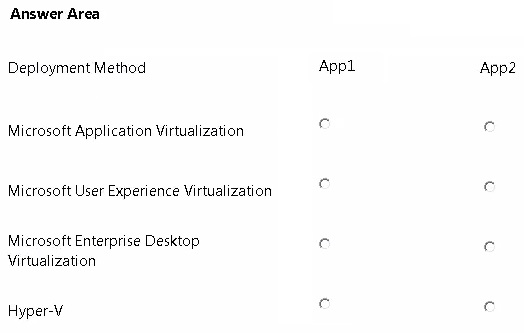
You plan to deploy the applications shown in the following table.
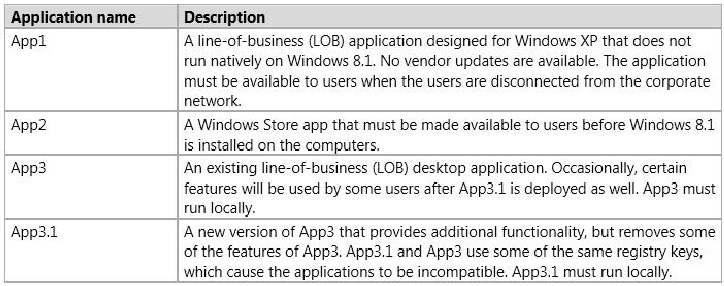
You need to recommend the appropriate technology to deploy each application. Each solution must ensure that the users can access all of the applications. The solution that uses the least amount of system resources must be selected, whenever possible.
Which technology should you recommend for each application? (To answer, select the appropriate technology for each application in the answer area.)

Answer : 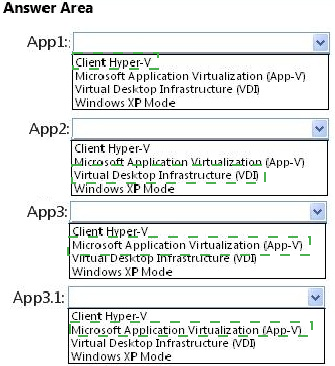
Explanation:
http://technet.microsoft.com/en-us/library/cc783635%28v=ws.10%29.aspx
Question 6
Note: This question is part of a series of questions that use the same or similar answer choices. An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in this series. Information and details provided in a question apply only to that question.
You support Windows 8.1 Enterprise desktop computers and tablets. All of the computers are able to connect to your company network from the Internet by using DirectAccess.
Your company wants to deploy a new application to the tablets. The deployment solution must meet the following requirements:
-> The application is not accessible if a user is working offline.
-> The application is isolated from other applications.
-> The application uses the least amount of disk space.
You need to deploy the new application to the tablets.
What should you do?
- A. Deploy the application as an Application Virtualization (App-V) package. Install the App- V 4.6 client on the tablets.
- B. Deploy the application as a published application on the Remote Desktop server. Create a Remote Desktop connection on the tablets.
- C. Install the application on a local drive on the tablets.
- D. Install the application in a Windows To Go workspace.
- E. Install Hyper-V on tablets. Install the application on a virtual machine.
- F. Publish the application to Windows Store.
- G. Install the application within a separate Windows 8.1 installation in a virtual hard disk (VHD) file. Configure the tablets with dual boot.
- H. Install the application within a separate Windows 8.1 installation in a VHDX file. Configure the tablets with dual boot.
Answer : B
Question 7
You have a Windows 8.1 Enterprise desktop computer.
You add three new 3-terabyte disks.
You need to create a new 9-terabyte volume.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
- A. From Diskpart, run the Convert MBR command.
- B. From Disk Management, bring all disks offline.
- C. From PowerShell, run the Add-PhysicalDisk cmdlet.
- D. From Disk Management, create a new spanned volume.
- E. From Disk Management, convert all of the 3-terabyte disks to GPT.
- F. From PowerShell, run the New-VirtualDisk cmdlet.
Answer : D,E
Explanation: You can build a spanned volume from GPT discs.
A spanned volume is a dynamic volume consisting of disk space on more than one physical disk. If a simple volume is not a system volume or boot volume, you can extend it across additional disks to create a spanned volume, or you can create a spanned volume in unallocated space on a dynamic disk.
You need at least two dynamic disks in addition to the startup disk to create a spanned volume. You can extend a spanned volume onto a maximum of 32 dynamic disks.
Reference: Create a Spanned Volume
https://technet.microsoft.com/sv-se/library/cc772180.aspx
Question 8
You administer laptops that run Windows 8 Enterprise and are members of an Active
Directory domain.
Users travel frequently and access domain resources from inside client networks or from their home network. You want to manage the laptops when they are connected to the company network from the external networks.
You need to ensure that the laptops can be managed and maintained while users are not logged on to the computers.
Which of the following should you recommend?
- A. Remote Assistance
- B. Windows Remote Management (WinRM)
- C. DirectAccess
- D. Remote Desktop
Answer : C
Explanation: Networking and Access Technologies
Reference:
http://technet.microsoft.com/en-us/network/dd420463.aspx
DirectAccess, introduced in the Windows 7 and Windows Server 2008 R2 operating systems, allows remote users to securely access enterprise shares, web sites, and applications without connecting to a virtual private network (VPN). DirectAccess establishes bi-directional connectivity with a user's enterprise network every time a users
DirectAccess-enabled portable computer connects to the Internet, even before the user logs on. Users never have to think about connecting to the enterprise network and IT administrators can manage remote computers outside the office, even when the computers are not connected to the VPN. Forefront Unified Access Gateway (UAG) 2010 extends the benefits of DirectAccess across your infrastructure, enhancing scalability and simplifying deployment and ongoing management.
Question 9
Your company recently purchased 10 new desktop computers for a remote unconnected location. All of the desktop computers have the same hardware configuration.
You install Windows 8 Pro on a reference computer and install a custom driver to support the video adapter.
You want to create an image of the reference desktop that retains the custom driver in the image.
You need to edit the unattended answer file.
Which setting in the unattended answer file should you edit?
- A. Microsoft-Windows-PnPSysprep | PersistAllDeviceInstalls
- B. Microsoft-Windows-PnPSysprep | DoNotCleanUpNonPresentDevices
- C. Microsoft-Windows-PnpCustomizattonNonWinPE | DriverPaths
- D. Microsoft-Windows-Shell-Setup | OEMInformation
Answer : A
Explanation: Microsoft-Windows-PnpSysprep
Reference:
http://technet.microsoft.com/en-us/library/cc766005(v=ws.10).aspx
Explanation:
The Microsoft-Windows-PnpSysprep component specifies whether all Plug and Play information persists during the generalize pass. Typically, during the generalize pass, all device information is removed from the computer.
If the device information is removed during the generalize pass, the next time the computer runs Plug and Play, the devices will be re-initialized. Typically, the next time the computer boots, the specialize pass runs, and Plug and Play runs.
PersistAllDeviceInstalls -
Specifies whether all Plug and Play information persists during the generalize configuration pass.
Question 10
You support Windows 8.1 desktop computers for a company named Contoso, Ltd. The computers are members of the Active Directory domain named contoso.com.
Contoso works with a supplier named Fabrikam, Inc. Each company has a public key infrastructure (PKI), and no public certificate authorities (CAs) are used. The Fabrikam network includes a website that is accessible from the Contoso network. The website requires SSL and mutual authentication.
You need to configure the computers to allow contoso.com domain users to access the website without any warning prompts. You also need to use the fewest certificates possible.
Which certificate or certificates should you use? (To answer, drag the appropriate certificate to the correct certificate store. Each certificate may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
Answer : 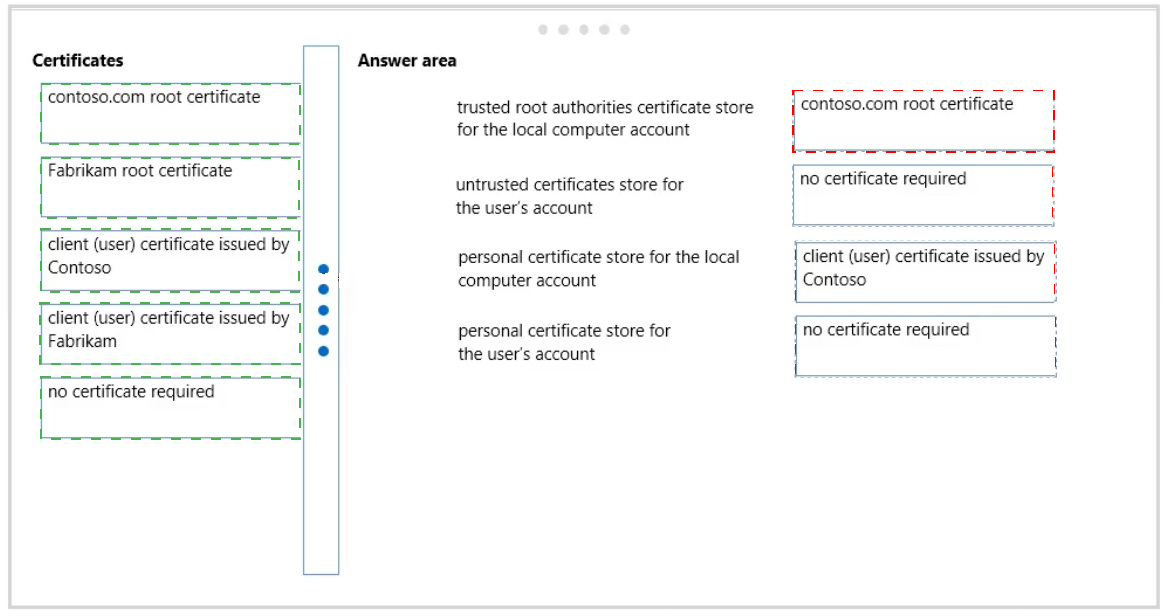
Explanation:
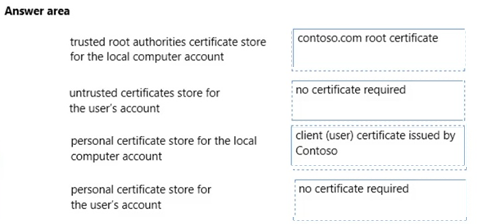
* the contoso.com domain must be trusted.
* a client certificate is needed for domain computers in contoso.com
Question 11
You administer Windows 8.1 Enterprise computers in an Active Directory domain. You have purchased a subscription to Windows Intune.
Company security policy requires that Windows Intune track resolved malware for 15 days, and that a system restore point be created before malware remediation.
You need to meet the requirements specified in the security policy.
What should you do?
- A. Create a new Windows Intune Mobile Security Policy in the Windows Intune Admin Console with the recommended settings.
- B. Connect your Microsoft account to your domain account.
- C. Create and deploy a Windows Firewall policy by using a custom policy.
- D. Create a new Windows Intune Center Settings policy with custom settings.
- E. Create and configure an Endpoint Protection scan.
- F. Create a new Windows Intune Agent Settings policy with the recommended settings.
- G. Create a new Automatic Approval Update policy.
- H. Create a new Windows Intune Agent Settings policy with custom settings.
Answer : E
Explanation: Microsoft Intune can help you to secure your managed computers in a number of ways, including:
* Endpoint Protection Provides real-time protection against malware threats, keeps malware definitions up-to date, and automatically scans computers. Endpoint Protection also provides tools that help you to manage and monitor malware attacks.
* Windows Firewall settings Uses policies that allow you to configure Windows Firewall settings on computers.
* Software updates
Reference: Help secure your computers with Endpoint Protection and Windows Firewall policy for Microsoft Intune
Question 12
You support Windows 8.1 Enterprise desktop computers.
Your company is deploying proprietary devices that will use a signed device driver. The driver is stored on a server share and is updated frequently by the device manufacturer.
You need to configure the desktop computers to automatically install the most recent version of the device driver from the file share when the proprietary device is plugged in to the computer.
What should you do?
- A. Run the dism.exe tool and specify the /Add-Driver parameter,
- B. Run the pnputil.exe and specify the -e parameter.
- C. Modify the DevicePath value in the HKEY_LOCAL_MACHINE/Microsoft/Windows/CurrentVersion registry key.
- D. Run the pnputil.exe tool and specify the -a parameter.
Answer : D
Explanation: Pnputil.exe is a command line utility that you can use to manage the driver store. You can use Pnputil to add driver packages, remove driver packages, and list driver packages that are in the store.
* -a
Specifies to add the identified INF file.
* -e
Specifies to enumerate all third-party INF files.
Example: pnputil.exe -a a:\usbcam\USBCAM.INF
Adds the INF file that is specified by USBCAM.INF
Reference: Pnputil -
Question 13
You support desktop computers and tablets that run Windows 8 Enterprise. All of the computers are able to connect to your company network from the Internet by using
DirectAccess.
Your company wants to deploy a new application to the tablets.
The deployment solution must meet the following requirements:
-> The application is stored locally on the tablets.
-> Access to the application is protected with extra logon credentials, in addition to a standard domain account used by users.
-> The application utilizes the least amount of network bandwidth.
-> The application must maintain access to the current desktop.
You need to deploy the new application to the tablets.
What should you do?
- A. Deploy the application as an Application Virtualization (App-V) package. Install the App- V 4.6 client on the tablets.
- B. Deploy the application as a published application on the Remote Desktop server. Create a Remote Desktop connection on the tablets.
- C. Install the application on a local drive on the tablets.
- D. Install the application in a Windows To Go workspace.
- E. Install Hyper-V on tablets. Install the application on a virtual machine.
- F. Publish the application to Windows Store.
- G. Install the application within a separate Windows 8 installation in a virtual hard disk (VHD) file. Configure the tablets with dual boot.
- H. Install the application within a separate Windows 8 installation in a VHDX file. Configure tablets with dual boot.
Answer : E
Explanation: Client Hyper-V -
Reference:
http://technet.microsoft.com/en-us/library/hh857623.aspx
Question 14
Your company is migrating from Windows 7 to Windows 8.1.
Before you attempt to migrate a client computer named Computer1. Computer1 fails and can no longer start Windows 7.
You need to migrate the user profile from Computer1 to a client computer named
Computer2 that runs Windows 8.1.
Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)
Answer : 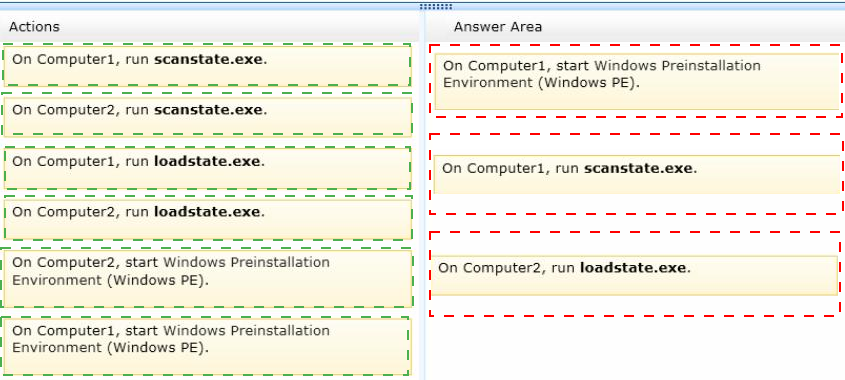
Explanation:
Box 1 -
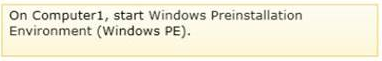
Box 2 -
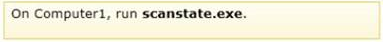
Box 3 -
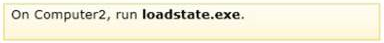
LoadState.exe. The LoadState tool migrates the files and settings, one at a time, from the store to a temporary location on the destination computer. The files are decompressed, and decrypted if necessary, during this process. Next, LoadState transfers the file to the correct location, deletes the temporary copy, and begins migrating the next file.
The ScanState tool scans the source computer, collects the files and settings, and then creates a store. ScanState does not modify the source computer. By default, it compresses the files and stores them as a migration store. ScanState copies files into a temporary location and then into the migration store. http://technet.microsoft.com/en-us/library/dd560755%28v=WS.10%29.aspx http://technet.microsoft.com/en-us/library/bb457090.aspx http://technet.microsoft.com/en-us/library/cc749015%28v=WS.10%29.aspx http://technet.microsoft.com/en-us/library/cc766226%28v=ws.10%29.aspx
Question 15
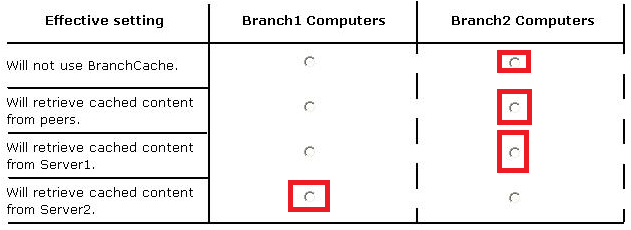
Your company has a main office and two branch offices named Branch1 and Branch2. The main office contains a file server named Server1 that has BranchCache enabled. Branch1 contains a server named Server2 that is configured as a hosted cache server.
All client computers run Windows 8 Enterprise. All of the computers are joined to an Active
Directory domain.
The BranchCache settings of all the computers are configured as shown in the following exhibit. (Click the Exhibit button.)
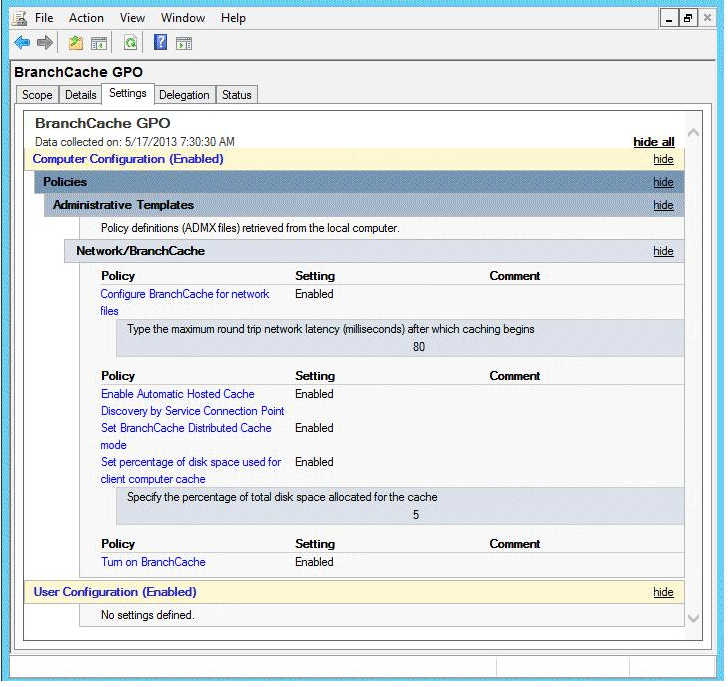
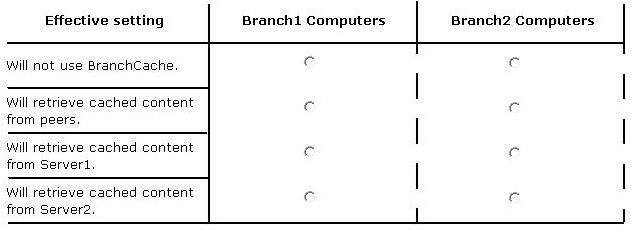
In the table below, identify the effective setting for the client computers in each branch office. Make one selection in each column. Each correct selection is worth one point.
Answer : 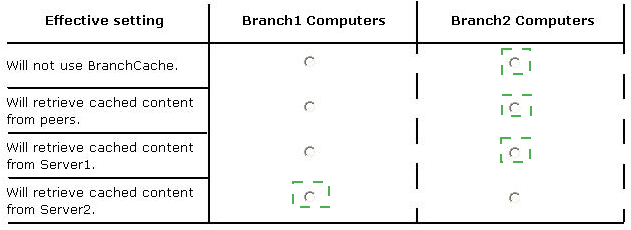
Explanation: